15 Brute Force Attack Prevention Techniques You Should Know
Whether it’s understanding how to stop a brute force attack on your server or how to prevent brute force attacks in general, there are several key things you can do to protect your business. Here’s what to know…
It’s no secret that bad guys love bad passwords. And I don’t mean bad like passwords that contain naughty words — I mean passwords that are so easy to guess that my young niece could figure them out with minimal effort. Reusing old passwords or “tweaking” old passwords (which 70% of users admit to doing) is also an issue. These types of insecure passwords make easy targets for brute force attacks. This is why brute force attack prevention should be a priority for your cyber security initiatives.
Brute force attacks are account hacking attempts that involve everything from cybercriminals guessing random or common passwords to capitalizing on leaked or stolen legitimate user credentials. These cyber attacks are no laughing matter. Bad guys often use scripts or bots to target the login pages on many sites and web apps, but these attacks also have other malicious uses as well.
Losses to businesses from these events vary in terms of direct and indirect costs. The United Kingdom’s Information Commissioner’s Office (ICO) reports that Cathay Pacific (an international airline) suffered a brute force attack in 2018 that resulted in a £500,000 non-compliance fine due to insufficient security measures. Understanding how to stop a brute force attack on your server can help prevent your company from making similar headlines.
So, is there a one-size-fits-all solution for how to prevent brute force attacks? Not really. Brute force attack prevention typically boils down to a layered security approach coupled with a handful of tried-and-true tactics. Much like other types of cyber attack prevention methods, it’s about eliminating as many vulnerabilities as possible in your cyber defenses and making yourself a tougher target than the guy next to you.
In this article, we’ll cover several common brute force attack prevention techniques. We’ll also walk you through how to stop a brute force attack on a server.
Let’s hash it out.
How to Prevent Brute Force Attacks (15 Brute Force Attack Prevention Techniques)
To effectively stop brute force attacks from affecting your IT systems and customers, you first need to really understand what a brute force attack is. Since we’ve already written an article talking about what a brute force attack is and how different types of brute force attacks work, we figure we can just give you a quick overview before moving on to talking about the various brute force attack prevention techniques.
A brute force attack is both a category and specific method of cyber attack that’s typically used to gain unauthorized access to accounts. Many brute force attacks fall within the category of password attacks, but they’re also useful for trying to guess API, SSH and cryptographic keys and find hidden web pages. When used as a password attack method, it targets your authentication systems by pelting its login forms with password and username guesses until it finds a matching combination.
It’s no secret that bad guys want to gain unauthorized access to your organization’s secure resources and sensitive data. As such, admin and privileged user accounts are particularly attractive targets because their accounts have greater access than others.
With all of this in mind, let’s break down 15 brute force attack prevention techniques. These prevention methods will be categorized into six distinct categories to help make the content easy to follow.
Implement Strict Access Controls & Set Up Other Authentication Protections
The general idea of access controls and access management is to ensure that only authorized, authenticated users can access your secure resources. This counts as everything from your network and web apps to other IT systems and data. In a basic sense, access management boils down to knowing:
- If someone has the approval or permissions to access those resources (authorization), and
- If the person requesting access is, in fact, who they claim to be (authentication).
This combination of authorization and authentication is critical to identity and access management (IAM) and your organization’s ability to develop a zero-trust architecture.
Understanding how to use access controls effectively and keep bad guys from finding your login pages is essential to understanding how to prevent brute force attacks from being successful. These practices and processes also help to limit exposure in the event that a brute force attack is successful.
This brings us to the first brute force attack prevention technique on our list…
1. Require Use of Strong, Unique Passwords — Or, Better, Passphrases
Require users to create unique passphrases in lieu of traditional passwords. For example, Goldfish%MirrorHarp+Sickle is a lot easier to remember than 3Ln`GW@09h*QaAwn$!. The FBI recommends using unique passphrases that are at least 15 characters long and contain multiple words. The idea is that passwords that are long and consist of random words/phrases are more secure and easier for people to remember than random gibberish. (So, you’ll be less likely to write them down or reuse them to secure multiple accounts.)
We specify unique password/passphrases because users typically like to choose the easiest route when it comes to creating account secrets. This often results in users either creating crappy (insecure) passwords or re-using passwords across multiple accounts.
Knowing this, it’s crucial for businesses to set strong password security requirements and create a password policy that you enforce. Check out NIST’s Digital Identity Guidelines (SP 800-63B) for additional guidance when creating password-related policies.
2. Set Account Restrictions So Only the Users Who Need Access Have Access to Key Systems
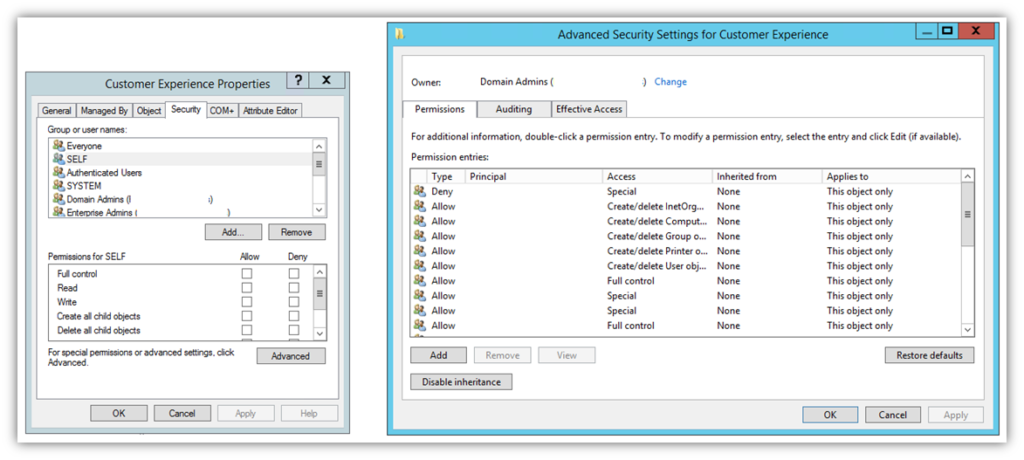
This process often involves setting roles and permissions for users within your active directory (AD) or other access management systems to limit exposure in the event that an employee’s account becomes compromised.
This process can also include setting remote access restrictions relating to remote desktop protocol (RDP) in particular. RDP is a common target for brute force attacks. Edgescan’s 2021 Vulnerability Statistics Report shares that RDP exposures increased significantly in 2020:
“Remote desktop (RDP) and Secure Shell (SSH) exposures increased by 40%, likely due to the increase in remote working due to Covid-19. RDP (and similar services) are easy and commonly used avenues for brute force or credential stuffing attacks, against weak user credentials.”
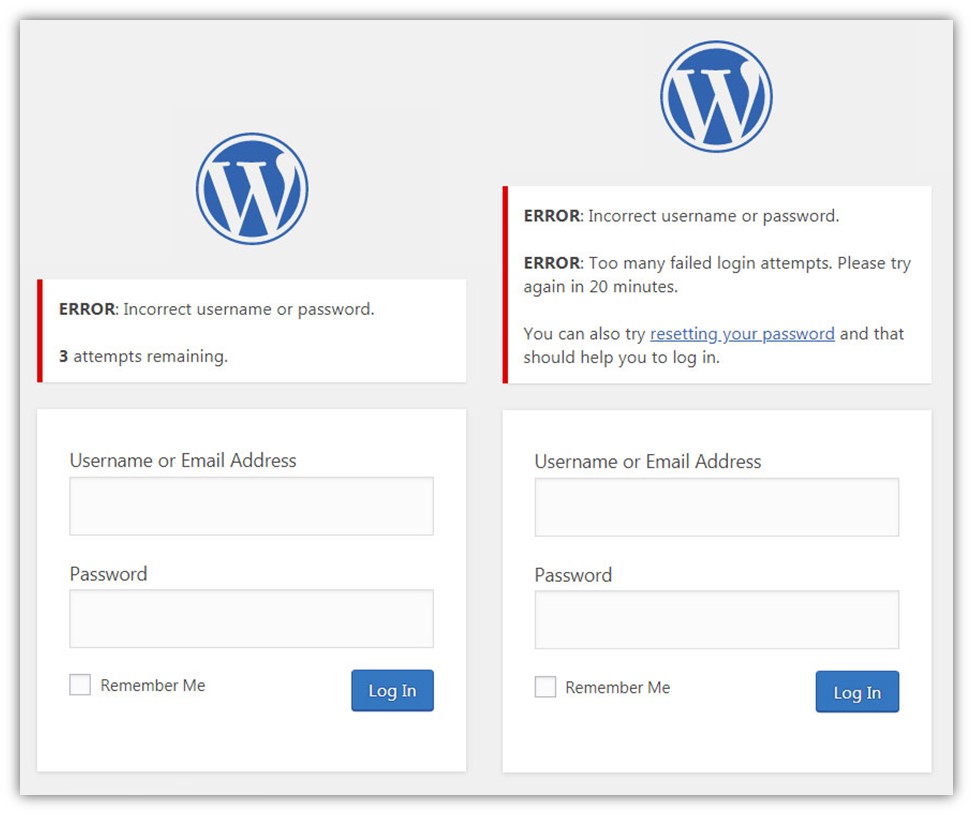
3. Set a Limit for How Many Failed Login Attempts Can Occur Within a Certain Period
A couple of big red flags that you’ll see with brute force attacks is a single IP attempting to log in to multiple accounts, or multiple IPs attempt to log in to a single user account. You can combat these issues by using rate limits and access use policy:
- Setting and enforcing rate limits is a great way to limit the traffic on your web app, network or server. In this context, you can configure your resources to only allow a specified number of failed user login attempts within a set time period.
- With an account use policy, you can set accounts to lock out users after so many failed attempts.
Secure Your Login Pages and Other Web Apps Using These Protection Measures
It’s no secret that the login pages on sites and web apps are the primary targets in most brute force attacks. Data from Verizon’s 2021 Data Breach Investigations Report (DBIR) shows that 89% of data breaches targeting web apps involved the use of brute force or stolen credentials.
This is why you must take extra care to fortify these defenses to the best of your ability. Here are a few of the ways you can do this:
4. Employ CAPTCHA as Part of Your Login Page Requirements
You know that dreaded “Click here to prove you’re not a bot” challenge box you have to click on many websites? That’s CAPTCHA, which stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.” (Yeah, I know, that’s way more letters than just C-A-P-T-C-H-A but I didn’t name it…)
These tools come in many varieties, some of which may require you to calculate simple mathematical equations, identify elements in photographs, or solve word problems. But I’ll be honest: Whenever I’ve had to solve CAPTCHA in recent months, my mind always goes to this humorous video:
Regardless of how annoying (and frustrating) this site security feature may be at times, it does have some value. CAPTCHA can be useful in preventing account takeovers, fraudulent purchases, and other use cases. The idea behind a CAPTCHA as an effective security tool is that it requires correct answers almost 100% of the time. The idea is that this should be a task that’s easy for humans but incredibly difficult for machines.
You can use a tool like reCAPTCHA on your website to prevent most bots from being able to pummel your login forms. Google even has an enterprise version that enables you to use it for site-wide coverage and an API to integrate the tool into mobile applications.
5. Use an Allowlist to Limit Access to Specific Pages
Allowlists (AKA whitelists) are a great way to limit to ensure that only select users, IP addresses, or domains can access your pages, web apps, emails, applications, and other systems. For example, using an allowlist enables you to specify which IP addresses can access your login pages. Any access attempts made by IP addresses other than those you’ve included on that list will be blocked automatically.
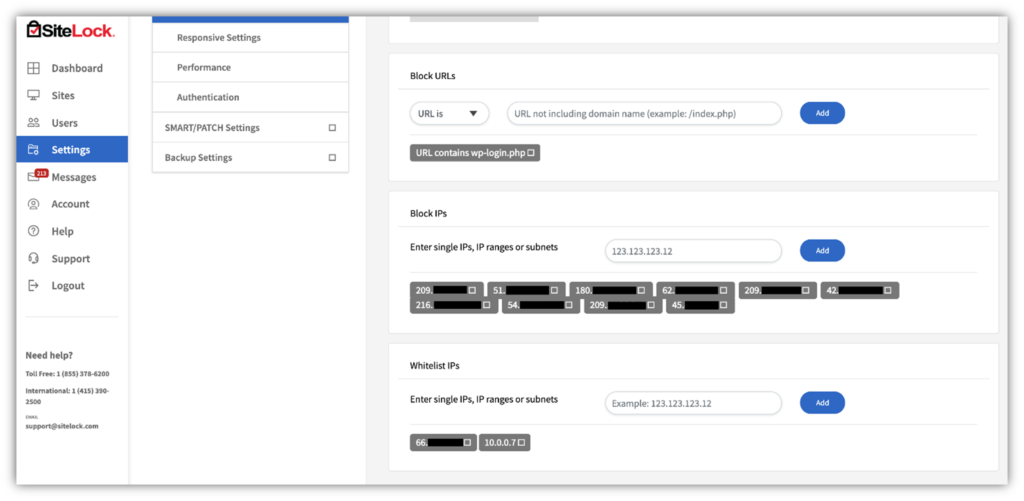
Why not use a blocklist (AKA blacklists) instead? Well, you can. It’s just that you’d have to know which IP addresses to block ahead of time. And it becomes even more complicated if attackers are using proxy IP addresses because it makes their traffic look like it’s coming from IP addresses that are different than their own.
However, using a blocklist can be an effective security measure in some cases, such as if:
- You observe many failed login attempts or unusual traffic originating from IP addresses in specific geographic areas, and
- You know none of your legitimate users will access your pages from those geographic areas.
Obviously, this won’t help you so much if an attacker is just cycling through lists of proxy IPs or using some types of automated systems. But some of the contributors at OWASP have a potential solution for that issue that involves using changing site response behaviors by generating unique failed login error messages. (Click on the link in the previous sentence to learn more about all of that.)
6. Change the URLs of Your Login Pages
While using something like example.com/blog/login.php makes these pages easy for your team to remember, it also makes them easy for hackers to guess and automated tools and bots to target with brute force attacks. But if you use a unique URL for these critical pages — say, example.com/blog/w00t-login-here.php instead, then you make your authentication pages a lot harder for bad guys to find.
We had to do this ourselves here at Hashed Out earlier this year. Why? Because some schmuck(s) repeatedly tried to force their way into our blog dashboard. This is one of the ways we chose to shut down their brute force attacks. It’s not a foolproof method, but at a minimum it reduces the server load caused by lazy brute forcers.
Create Layers of Security to Strengthen Your Network and Server Security Defenses
This next section focuses on site-related brute force attack prevention techniques. The idea here is that you want to use multiple layers of cyber defenses to protect your organization. This includes various network security tools that help you monitor and block unusual traffic.
One of the most important ways to protect your IT environment from brute force attacks is to keep all of your software, firmware, add-ons and extensions patched and updated. Cybercriminals love to exploit vulnerabilities to gain access to related or connected systems. However, you can take some other steps to ensure your devices, sites, and networks are operating with the strongest defenses.
7. Adopt Network Security and Threat Detection Tools
A web application firewall (WAF) is a great tool that can help you to detect and thwart credential stuffing attacks. However, it’s not perfect and can be ineffective against botnet brute force attacks that involve multiple attackers using unique IP addresses. This is why you should be using other types of protection as well.
Intrusion detection systems (IDS) help you to identify and report network security incidents and vulnerability exploits — but they do have limitations. You can’t use IDS to prevent or respond to these issues — that requires another related set of tools. Security information and event management (SIEM) software is a great way to identify, analyze and respond to threats in real time. SIEM helps you catch brute force attacks in action so you can do what needs to be done to rain on the bad guys’ parades.
However, we understand that these tools — and the experts needed to operate them effectively — can be pretty pricy for smaller in-house operations. This is where using a managed security service provider may be a good option.
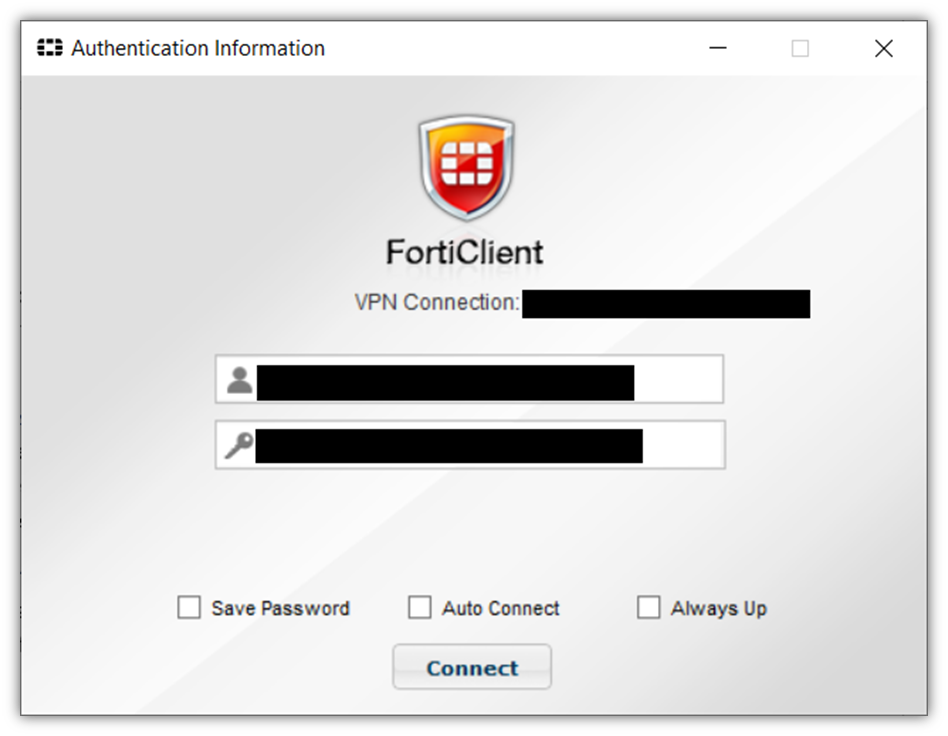
8. Require Employees to Use Secure, Encrypted Connections
If you’ve been reading Hashed Out for a while, you know that encryption is essential to cybersecurity. We typically talk about it in terms of securing website connections via HTTPS through SSL/TLS certificates. However, virtual private networks (VPNs) are also useful tools — particularly when you have employees and admins working remotely.
If you require VPN use for remote access — and have a VPN gateway set up to keep remote VPN traffic separate from your local network — it can help to prevent the RDP-focused brute force attacks we mentioned earlier.
9. Manually Change Your Default Ports to Hide Your Connections
Bad guys like easy targets because they spend less time and energy to achieve a decent ROI. By changing your connections to default to different ports, you’re basically hiding your connections from them — or, at the very least, you’re making those connections significantly harder for bad guys to find.
Use Secure Password Storage Methods & Implementations
Figuring out the best way to store passwords is critical for your organization’s security from user and admin perspectives. Here are a few of the ways that you and your employees can help keep your passwords secure.
10. Use a Password Manager
NordPass data shows the average person juggles between 70 and 80 passwords. If your users have issues remembering their passwords or require many password resets, then this section is for you.
Password managers are a great option for users who want to generate and store complex passwords. These tools allow you to store all of your complex passwords and long passphrases in a way that requires you only to remember your master password to access or use. It really doesn’t get much easier than that.
11. Only Store SALTED Password Hashes On Your Servers
Storing plaintext passwords on public-facing servers is a big security issue and is something companies actively try to avoid doing. Instead, organizations typically store users’ password hashes on their servers instead because using password digests an easy way to verify their password entries on the back end during authentication without having to know their plaintext passwords. (This still isn’t secure enough and requires an additional step that involves a salt — and we’ll tell you why in a moment.)
When users log in to their accounts, the passwords they type are run through a one-way pseudorandom function (i.e., a hash). Then, their resulting hash values are checked against their organizations’ list of stored hash digests on the back end. If the results match, then the organization knows the user entered the correct password. If not, then the authentication fails and returns an error response to the user.
But a mistake that companies do make is opting to store encrypted passwords or unsalted password hashes on their public-facing servers. Even if plaintext passwords are encrypted or are simply hashed (unsalted), they’re still at risk. If you accidentally misconfigure the database or an authorized user’s credentials get compromised via an SQL injection attack, that encrypted or hashed data could become leaked or stolen.
- If bad guys get their hands on your decryption key, then your encrypted data is no longer secure. They can use that key to decrypt your customers’ password data and see the plaintext values.
- Although hash digests are too costly (both in time and resources) for cybercriminals to reverse, bad guys have another card up their sleeves. They can use password cracking techniques (i.e., rainbow table attacks) to try to match unsalted password hashes to lists of known password hashes. This process can help them map back to the original password.
This is why the best course of action is to only store salted password hashes instead. A salt is a unique, random value. When you add a salt to your password, it means you’re adding a unique, random integer to the end of each password prior to hashing it. This results in the generation of a unique hash value. So, even if two individual users use identical passwords, the unique salt values alter the hash inputs individually so the resulting password hashes are unique.
Here’s an example of how this process looks from our article on password security:

… Or, Better Still, Adopt Passwordless Authentication for Your Business

Another way to eliminate the risk of brute force attacks is by eliminating passwords altogether. Passwordless authentication allows your employees to identify themselves and authenticate to access your secure resources. Some methods of passwordless authentication include:
12. Require the Use of Multi-Factor Authentication
Traditional multi-factor authentication (MFA) typically offers three categories of identifying factors to choose from for authentication:
- something you know (like a password or PIN),
- something you have (like a key fob, token, or CAC), and
- something you are (biometrics such as a facial scan or fingerprint).
Traditionally, the “something you know” factor is almost always a password. But in passwordless MFA, a password is replaced with an alternate (ideally more secure) different factor. Some types of MFA even include other verification factors like somewhere you are (geolocation data) and something you do (behavioral patterns that are observed and logged using AI).
13. Adopt PKI-Based Authentication Certificate-Based Authentication
As we’ve discovered, users often don’t use passwords that are secure enough to make them a viable stand-alone security measure. And since many MFA methods use passwords as one of the first authentication factors, this doesn’t always mitigate the issue. This is why some companies use alternative authentication methods instead that rely on public key encryption.
Certificate-Based Authentication
Certificate-based authentication is another method of passwordless authentication we’ve talked about before. It allows a user to authenticate automatically because of a digital certificate and cryptographic key that’s stored on their device. The user’s identity is tied to that certificate, so when implemented with proper access controls, the user can access any sites, web apps or other IT systems their user profile has permissions for from that device.
When they open their web browser, the server or application they’re connecting to requests that client certificate as an additional component of the traditional connection process. This digital certificate allows the user on that device to access resources without ever having to remember or type in a password.
When paired with a trusted platform module (TPM), this authentication method becomes even more secure. This tamper-resistant security hardware helps you to ensure that no one can steal or alter the user’s cryptographic keys.
SSH Key-Based Authentication
This authentication option really is a bit more niche as it applies typically to admin-type accounts and not general users. (Admins commonly use SSH for remote system access and management for networks and other IT systems.) But, still, it’s something worth mentioning in this type of article.
SSH authentication typically involves a user manually entering their login credentials or using an SSH key to authenticate automatically. Since we’re talking about passwordless authentication methods in this section, the first method doesn’t really apply. A key-based authentication method is more secure because SSH keys are brute force attack resistant (provided you take the appropriate steps to keep your keys secure and properly manage them).
To learn more about SSH keys and explore some SSH key management best practices, be sure to check out our related article that addresses that topic.
Secure Your Human Firewall By Making Employees Tougher Targets
I’ve said this before, but your employees and other users can either be your organization’s greatest defense or its biggest weakness when it comes to security. The difference lies in their cyber awareness and their ability to apply what they know in real-life situations.
This is where cyber awareness and phishing training can help.
14. Provide Mandatory Cyber Awareness Training

This should be a no-brainer, but since many companies still don’t offer some type of cyber awareness training, it’s worth mentioning. Cyber awareness training is an invaluable tool that helps users learn about real-world threats and how to respond to them. Your training sessions should cover everything from common phishing scams and social engineering tactics to what your employees should do if they encounter something suspicious or unusual.
One important note: be sure to use real examples in your training. Honestly, examples of phishing emails shouldn’t be hard to come by — just take a look at your email junk and trash folders. But sharing real-world examples of phishing emails and screenshots of fake websites found in the wild can make the difference between adequate training materials and really great ones.
But in addition to holding face-to-face or online training sessions, you can take employee training a step further with testing. This leads us to our next point…
15. Carry out Cyber Attack and Phishing Tests or Simulations
An easy way to gauge the effectiveness of your cyber awareness and phishing training is to set up tests. This method helps you to see what training has been effective and identify areas where employees are struggling to apply their knowledge.
One such example is to send fake spam emails to your employees (without their knowledge) to see who:
- Opens any of the emails,
- Clicks on any of the messages’ links, or
- Reports the messages as spam.
You can use all of this data to figure out what areas of knowledge may be lacking to provide additional training. It also may help you identify new areas of opportunity for future training sessions or modules.
Final Thoughts on Brute Force Attack Prevention
Brute force attacks aren’t new and they’re certainly not going anywhere anytime soon. The truth is that cyber threats are continually changing, and your organization’s defenses must evolve to meet them head on.
Cybercriminals know that no technology is 100% secure and they continually try to find new ways to circumvent your organization’s security measures. This is why every company must actively take steps to update and improve their cyber defenses to counteract these malicious efforts. We hope some of these brute force attack prevention techniques help guide you on the road to making your organization more secure.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown