CAs to Deprecate OU Info from Digital Certificates Starting July 1
The CA/B Forum has decided that CAs no longer need to include organizational unit (OU) information when issuing publicly trusted SSL/TLS digital certificates. Let’s quickly explore what this means for you when ordering SSL/TLS certificates (spoiler alert: it won’t change anything for most users)
There are changes coming down the pike that will make the task of ordering certificates easier a bit easier by eliminating confusion. Traditionally, the certificate ordering process has required requestors (i.e., you) to provide information for the organization unit (OU) field. However, starting Sept. 1, the CA/Browser Forum (CA/B Forum) has decided that this field is no longer necessary and that all publicly trusted certificate authorities (CAs) will no longer include this information in the certificates they issue.
However, some CAs are being proactive and are rolling out these changes ahead of time — starting as early as July 1. But why this change is occurring, and what does it mean for your business?
Let’s hash it out.
What You Need to Know in a Nutshell
Here’s a quick overview of everything you need to know:
- The organizationalUnitName (OU) field information will no longer be included in new, renewed and re-issued SSL/TLS certificates. (This change only affects you if your company used the field for record keeping, differentiating services, or other such activities.)
- Some certificate authorities have decided to roll out their certificate changes prior to the Sept. 1 deadline to avoid any issues:
- Sectigo will remove OU info from their certificates starting July 1. They’ll offer a temporary option for deactivating the OU field on an “account by account basis” by April 1.
- DigiCert will remove the field from their certificates in August. This will occur sometime before the end of the month (they weren’t more specific than that in their information release.)
- The CA/B Forum was concerned that the field could be misused because it’s a free-form field that lacked substantive verification requirements. (I.e., anyone could enter virtually anything they wanted there.)
- The OU field was causing issues by slowing down certificate validation.
- This change doesn’t affect private CA certificate users. (This OU field removal only impacts publicly trusted SSL/TLS certificates.)
If that’s all you were looking for, feel free to move on your way. But if you’re one of our newer readers, or you’re new to the SSL/TLS industry as a whole, no worries. We’ve got you covered and will answer some other related questions that you may have…
What the Heck Is the OU Field?
When you complete a certificate signing request (CSR) as part of the certificate ordering process, there’s traditionally been a free-form field in which you’d enter metadata that you want to store in your certificate. In cPanel, for example, this field is labeled “Company Division” instead.
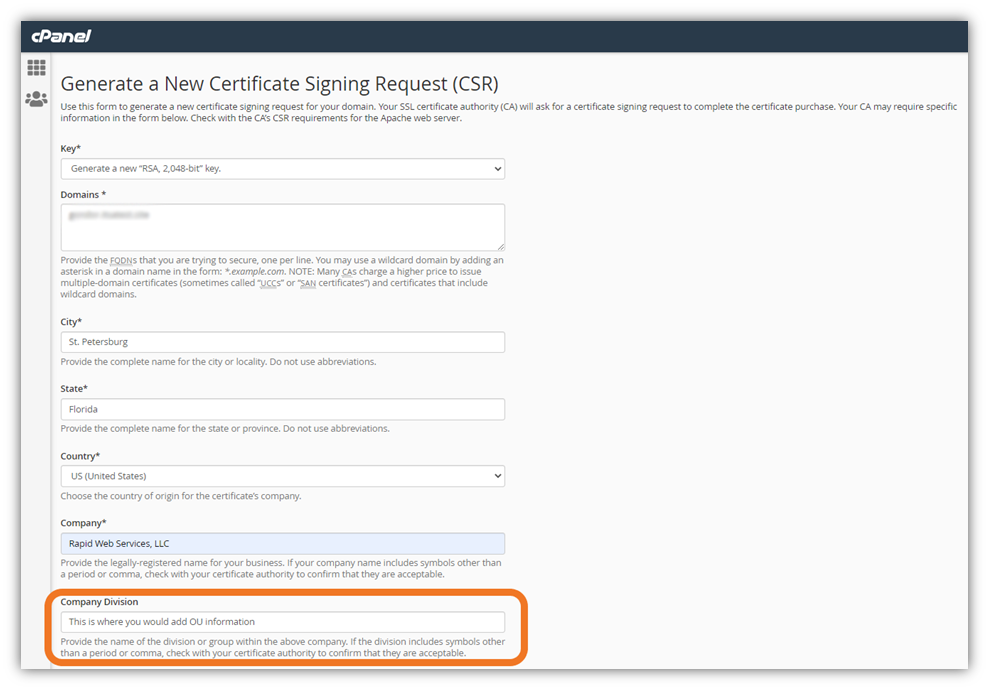
However, many users had no idea what information to input in this field because, frankly, the term is pretty nebulous. Does it mean your department? A website? A trademark? Something else entirely? Yeah, you see why it could be confusing.
Here’s an example of an OU field in the SSL/TLS certificate for Wells Fargo:
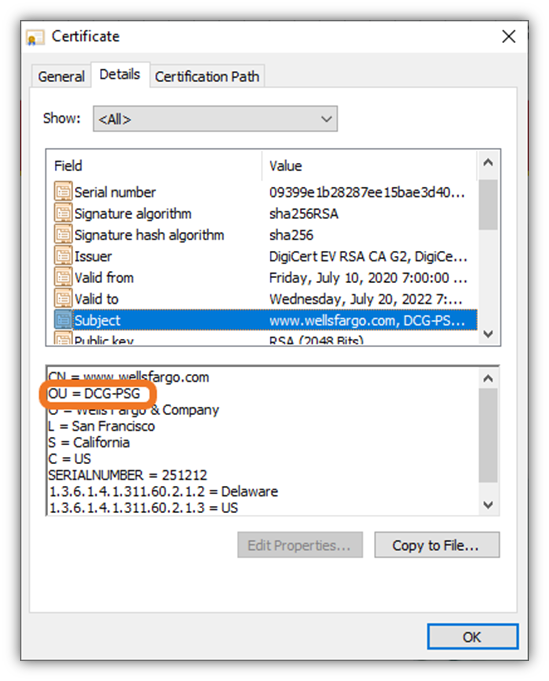
Do you know what the DCG-PSG stands for? We don’t, either (at least, not without turning to Google to see what turns up). And that’s kind of our point. The scope of the OU field’s intended usage is actually pretty limited, and it’s required to not be “misleading.” However, who would check that out and how would the information be verified? When this form is filled out incorrectly, it leads to a litany of issues that bog down validation times for companies ordering certificates. Which brings us to our next talking point…
Why Are CAs Removing the Organizational Unit Field Being Removed?
The quick answer: Because the CA/B Forum told them to do so in their latest release of SSL/TLS Baseline Requirements (1.8.1). The concern was that this field could be intentionally or unintentionally misused and cause validation hang-ups and other issues.
The long answer: Basically, the CA/B Forum is the industry’s voting body of heavy hitters like Google, Apple, DigiCert and Sectigo. Last fall, the Forum’s members discussed via email the use of the OU field and whether it served as a benefit or a hindrance. While some companies used it correctly, the concern was that the field was often used incorrectly and that bad guys could misuse the OU field for bad purposes.
In December 2021, the group voted to deprecate the organizationalUnitName field entirely from certificates. This will take effect starting Sept. 1 (although CAs are implementing the change ahead of schedule on their sites.)
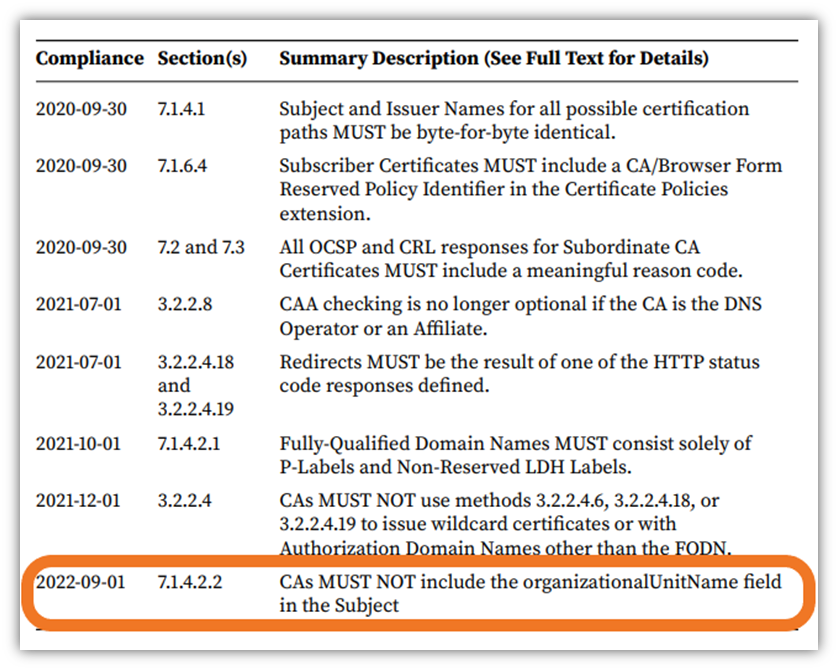
According to Section 7.1.4.2.2:
“Certificate Field: subject:organizationalUnitName (OID: 2.5.4.11) Required/Optional: Deprecated. Prohibited if the subject:organizationName is absent or the certificate is issued on or after September 1, 2022. Contents: The CA SHALL implement a process that prevents an OU attribute from including a name, DBA, tradename, trademark, address, location, or other text that refers to a specific natural person or Legal Entity unless the CA has verified this information in accordance with Section 3.2 and the Certificate also contains subject:organizationName, subject:givenName, pg. 80 subject:surname, subject:localityName, and subject:countryName attributes, also verified in accordance with Section 3.2.2.1.”
To quickly summarize, the idea behind removing the OU field is that it will:
- Eliminate an unnecessary piece of data.
- Mitigate OU-related hiccups in the validation process by eliminating the highly specific field.
- Prevent inaccurate attributions or intentional misuses of company names, trademarks, tradenames, addresses, or other information.
How Will Removing the OU Field Affect My Organization?
Honestly, this change isn’t earth-shattering and isn’t going to affect the overwhelming majority of our readers. This change will likely only affect you if you’ve been doing something custom (like using the OU field to keep track of which employee/department issued a certificate). But seeing as how we like to keep you apprised of changes within the CA/B Forum, we thought it pertinent to let you know about the change that’s occurring ahead of time.
Here’s a quick overview of what removing the OU field will entail for publicly trusted certificates:
- The OU field will be removed from all certificate authorities’ certificate order forms.
- All new or re-issued publicly trusted SSL/TLS certificates will no longer contain OU information.
- Pre-existing SSL/TLS certificates (i.e., those that were ordered prior to the field’s removal) won’t be affected.
Wondering what this means for private CA certificate users? A whole lot of nothing. Basically, this isn’t going to change a darned thing for 99.9% of users.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown