Baptists & Bootleggers: Consensus on Eliminating the Secure DV SSL Indicator
Sometimes the internet creates strange bedfellows.
In 1982, an Economist at Clemson University named Bruce Yandle concocted an economic theory that he articulated using the old tale of the Baptists and the Bootleggers.
As the anecdote goes, both the Baptists and the Bootleggers agreed that the bars and liquor stores should be closed on Sunday. The Baptists were teetotalers and wanted them closed to get a break from the demon drink. The bootleggers wanted them closed so they could sell their wares.
The outcome, says Yandle, is “durable regulation that will stick around as long as the Baptists and the Bootleggers have a common objective.”
Keep that theory in mind because it’s never been more applicable to the SSL industry than in the current debate over Browser UI and how it displays for DV SSL certificates.
That occurred to me this morning, following this interaction:
I want to abolish security indicators, you want to sell them. That we “agree” on abolishing DV indicators is more a coincidence than any kind of agreement on the issue.
— hanno (@hanno) December 6, 2017
Granted, I don’t think the Certificate Authorities and resellers that are “trying to sell” SSL certificates are as nefarious as bootleggers. But certainly, some in the industry do seem to feel that way.
Regardless, I think by this point we can all agree the Secure DV SSL indicator needs to go. It’s creating more problems than its solving. And while discussions of a uniform UI and EV treatment remain, there seems to be a consensus on DV.
There are two main factors behind why the DV UI is failing. The first is the rapid proliferation of DV SSL certificates. The second is Google’s change to its UI itself.
Starting at the beginning of the year, Google began marking websites with DV or OV SSL certificates “Secure,” and it is slowly beginning to mark HTTP sites “Not Secure.” Though Google tested for different UIs, the one it ultimately decided on was the “Secure”/”Not Secure” binary. As pretty much everyone throughout the industry knows, users don’t have much of an idea what the old visual indicators meant and this was an attempt to simplify things for them.
Unfortunately, it went the other way. People mistook “Secure” for safe and acted accordingly.
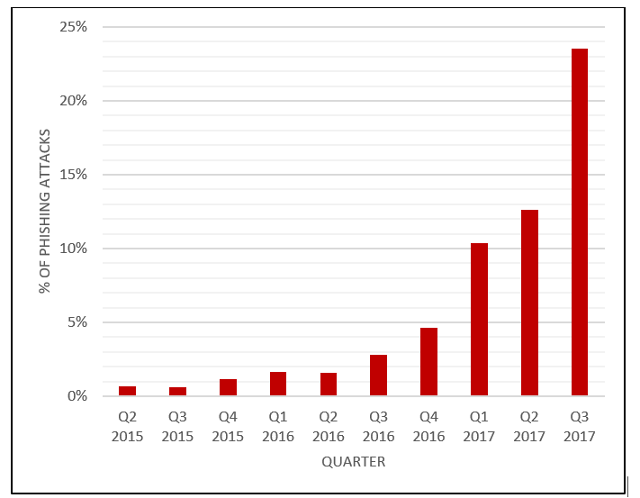
Phishing is now at an all time high. According to one threat report, phishing is up 74% in Q3 2017. There are 1.4 million new phishing sites created each month, on average. And according to a PhishLab report issued yesterday, a quarter of all phishing is now done via HTTPS.
It’s being done using DV certs, too. Here’s a look at the last 30 days, 99.5% of the HTTPS phishing sites sampled were DV.
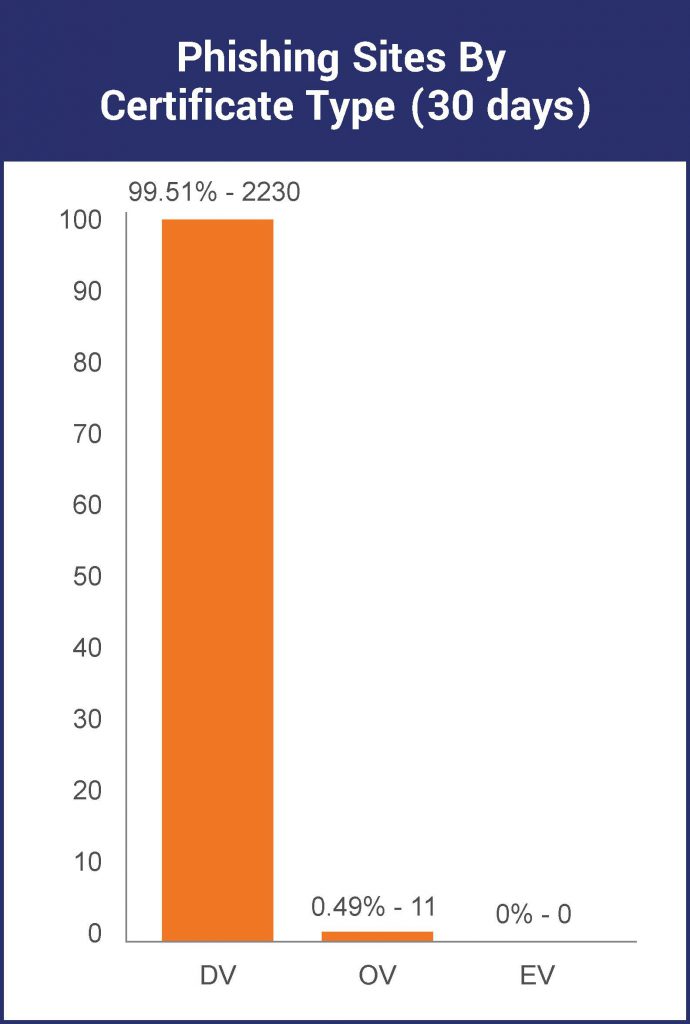
And that makes a lot of sense. It’s easy to get a DV SSL certificate nowadays. There are free CAs, DV certs come bundled as part of hosting packages now and there are even programs with commercial CAs where you can get a DV SSL certificate without paying a cent.
We think this is great. The problem is: if Domain Validated SSL is the new default, why is it getting such a strong indicator?
Now, from all of thus data, there’s no way you could prove a causal link between Google’s UI and this decided uptick in HTTPS phishing. But there is DEFINITELY a correlation. Keep in mind, the chart below is from last Spring, that line would be at the top of the graph now.
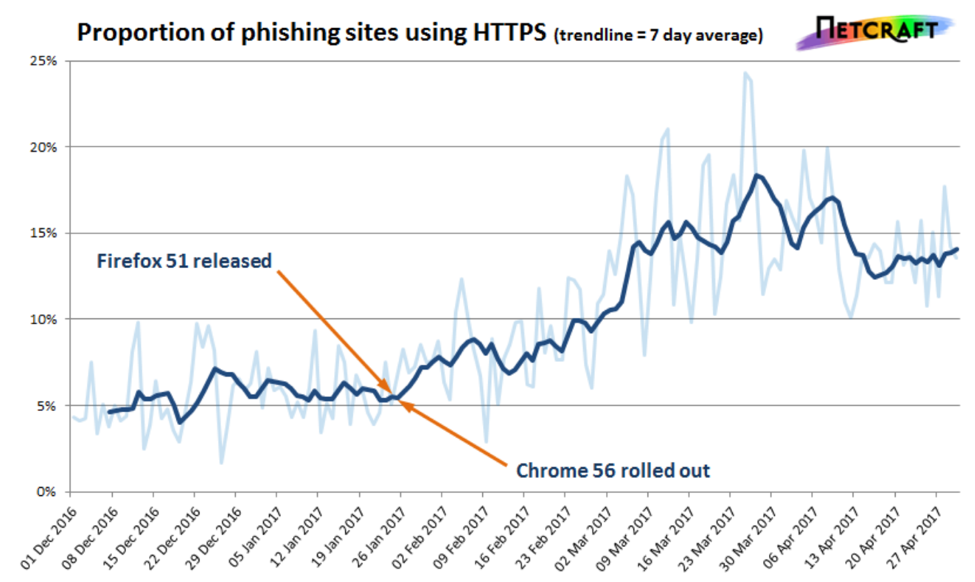
My understanding of Google’s ultimate plan was that it wants to eliminate the Secure DV SSL indicator once enough of the internet has migrated to HTTPS. And that probably seemed like the ideal way to do it at the time.
Things have changed. The current UI makes phishing websites with SSL certificates – which is now about one in four sites – more effective.
The Secure DV SSL indicator needs to go.
When even the Baptists and the Bootleggers can agree on that—you know it’s time.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown