End-to-End Encryption: The Good, the Bad and the Politics
Here’s what you need to know about the debate over end-to-end encryption
Note: This article, which was originally published in 2019, has been updated to include related news & media resources.
It’s that time of the year when we grab our popcorn and witness another chapter in the age-old battle between governments and tech companies. Once again, governments are attacking tech companies for giving criminals a “safe place” for their communication, while the companies say they are protecting privacy.
After Apple and WhatsApp, Facebook is the latest platform to make the headlines in the ongoing encryption debate — end-to-end encryption to be precise. In an open letter addressed to Mark Zuckerberg, co-founder & CEO of Facebook, the governments of the U.S., U.K. and Australia have asked the social networking giant not to proceed with its plans to implement end-to-end encryption across Facebook’s messaging services. And not only that, they’ve also reaffirmed their request for a backdoor in the encryption of messaging services.
But before you form any opinions on this situation, it’s essential to know what end-to-end encryption is and what it does.
Let’s hash it out.
What is End-to-End Encryption? How is it Different from Other Encryption?
How Encryption Works
We’ll get to “end-to-end” encryption in a bit — but before that, let’s first understand what encryption is and what it does.
Consciously or unconsciously, we all send and receive a lot of information when we use the internet through our devices. And some of this information is confidential (passwords, financial information, personal photographs, etc.) and could cause a lot of damage if someone steals or tampers with it. So, how do we make sure that no one does that? Well, this is where encryption comes in.
Encryption is the technique that turns our data into an undecipherable format so that no third party can read or alter it. It’s what keeps us safe in the ocean of the internet.
Here’s an example of a phrase of text that’s been encrypted:
- Plain text: This is a Facebook message.
- Encrypted text: eXP3jH+7giCt1gIg0zHm3j3DPI1xuFRvbhmaKJx/uQQ=
As you can see, there’s no way to figure out what the encrypted text means — unless, of course, you have the private key to decrypt it.
Facebook Messenger Is Already Encrypted — Here’s How It Works
Facebook Messenger already uses encryption — just not end-to-end encryption. “Normal” encryption (a.k.a. link encryption) works like this:
- Sender forms an encrypted connection with Facebook’s servers.
- Sender submits the encrypted message to Facebook’s servers.
- Facebook decrypts the message and stores it on their servers.
- Facebook’s servers form an encrypted connection with the recipient.
- Recipient downloads the message via an encrypted connection.
Note that in this scenario, Facebook controls the encryption/decryption, and Facebook has access to the decrypted message.
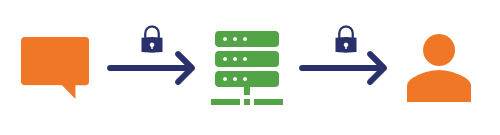
How End-to-End Encryption Works
Now, let’s get to end-to-end encryption. It’s precisely what it sounds like — end-to-end encryption facilitates the type of encrypted communication that only the sender and receiver can read/see. No one in the middle — including Facebook, the government, or another messaging service provider — can read/decrypt messages being sent from one device to another.

In other words, the messages you send are decrypted at the endpoint of the communication — the device you’re sending messages to. The server you’re sending the data through (i.e. Facebook) won’t be able to decrypt or view your messages.
Facebook Can’t See Your Messages When They’re End-to-End Encrypted
The distinction between the two is that while normal or link encryption encrypts the data, the server transmitting information between two devices has the ability to decrypt the encrypted data. End-to-end encryption, on the other hand, uses the server to transmit the data (how else would the data transfer take place?), but it doesn’t allow the server to decrypt the data. Therefore, the server is just a medium that facilitates data transfer of encrypted information. Hence, WhatsApp or any other end-to-end encrypted app won’t be able to read your information (even if they want to).
End-to-End Encryption: The Good
Security professionals and privacy experts largely support the idea of end-to-end encryption because it better protects your data from hackers and other parties who may want spy on you. When you allow the data transmitter (the messaging service provider in this case) to decrypt your messages, you’re leaving a significant potential security hole that could cause problems if the server is compromised, hacked, or surveilled.
If the information is protected end to end, though, there’s no point in intercepting information halfway down the line as it’s in an encrypted format. Thus, it protects the privacy of millions of people and assures them that no one — not even the messaging service itself — could read their private information. For this reason, experts (including organizations such as the Electronic Frontier Foundation (EFF), the Center for Democracy & Technology, and others) are advocating for the use of end-to-end encryption in messaging apps.
End-to-End Encryption: The Bad
The main argument against end-to-end encryption (and in favor of link encryption) is that end-to-end encryption creates a “safe space” for criminals to communicate where there’s no third party who can read and perform security checks on their messages. In other words, the technology that’s supposed to protect the privacy of millions of people and businesses protects the confidentiality of criminals as well.
I’m not saying that I’m in favor of this argument, but it undeniably does hold some water. If the server was able to decrypt the data, we can have a system that would help in catching the bad guys. In the case of end-to-end encryption, this option is gone. I don’t know what other motives they may have, but this is the argument that the governments of the U.S., U.K., and Australia are using to do away with end-to-end encryption.
End-to-End Encryption: The Politics
While the argument made by various governments might make sense to a certain extent, there’s always a question mark regarding their full intentions. Do they care about the crimes that may be hidden because of end-to-end encryption, or are they crying foul in order to serve a bigger agenda: having the power to easily spy on people?
So far, seeing the evidence that’s available to us, both seem likely to be true.
And it’s worth noting here that Edward Snowden, the famous National Security Agency whistle-blower, previously revealed that the intelligence services in the U.K. and U.S. had been intercepting communications through various channels for many years on a mass scale. So, where do you draw the line as far as governments’ interference is concerned? Encryption can be used for good and for bad, but so can surveillance!
An Encryption Backdoor Is Not the Solution
If you’ve been following this entire encryption saga, you must have stumbled across the term “backdoor.”
Basically, a backdoor is a mathematical feature of the encryption key exchange that could decrypt the end-to-end encryption, and no one knows about this except the ones who made it (the messaging service). In popular words, it’s like a secret key. So when, let’s say, a judge orders a warrant to hand over certain information in a decrypted format to the government, the messaging app (or the government agency) could use this “backdoor” to give your decrypted information to the government.
But, again, this comes with a danger — a massive one. What if this powerful tool falls into the wrong hands? If a cybercriminal somehow gets hold of this “secret key,” they could have access to all of your private pictures, messages, etc. and do who knows what with them! And that’s why creating a backdoor could be even more dangerous than concerns about standard encryption.
Why Does Facebook Want to Implement End-to-End Encryption? (Is Facebook Running Away from Its Responsibility?)
Implementing end-to-end encryption would mean that even Facebook itself won’t have access to the information being shared through its messaging service. This seems quite contrary to the business model that Facebook has built around data monetization.
So, why doesn’t Facebook want the data? Does it really care about privacy, or is there something else hiding behind the curtain?
One possible reason why Facebook plans to implement end-to-end encryption is to simply move away from the pressure of law enforcement, court orders, warrants, and controversies. Currently, Facebook uses artificial intelligence (AI) and a team of human moderators to monitor the content and messages sent via its platform. They then report suspicious communication/content to authorities. This content moderation system is the source of a lot of expense, negative news coverage and even lawsuits for Facebook.
With end-to-end encryption in place, this could all go away because Facebook won’t be able to decipher the communication. They can simply say “sorry, we can’t access the content even if we want to.” That could save Facebook a lot of time, money, and hassle.
A Not-So-Final Word
Considering that Facebook has already implemented end-to-end encryption in WhatsApp, the most extensively used messaging service that it owns, it seems likely that end-to-end encryption will be implemented in Facebook’s other services as well. The question is — what happens next? I expect the governments championing the call to eliminate end-to-end encryption to shift gears and attack the tech companies with more ferocity. Further down the road, this never-ending battle could spark into a fire, and ordinary users could be its witnesses or become engulfed in it.
As always, leave any comments or questions below…
Recent Related News
Updated on April 29, 2021





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)







 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown