How Improving Your Cyber Security Posture Benefits Your Bottom Line
Your security posture and company’s profitability are more closely linked than you may realize
Admit it: Growing and protecting your company’s bottom line is a top priority. While many business professionals feign their organization’s mission or value statement as their ultimate driving force, often time, most value-centric priorities take a back seat to the almighty dollar. Why shouldn’t it? After all, money helps to keep the lights on, employees working, and the corporate machine chugging along. But what if something was to cause that well-oiled machine to come to a grinding halt? That’s precisely what can happen to companies that lack or have a poor cyber security posture.
Security posture refers to the strength of your overall cyber security defense. This is important because cyber security threats are ever increasing, and cyber attacks are considered the third greatest global threat, according to the World Economic Forum (WEF). At the risk of repeating ourselves by restating what we’ve said in many articles: Every business needs to be prepared because it’s not if but rather when cyber security attacks will strike. A 2018 Deloitte survey of 1,100 U.S. executives indicates that more than 90% of their companies have faced a cyber security challenge, and nearly one-third experienced a cyber security breach within the past two years. Increasing your organization’s cyber security posture helps to help your business block most cyber security attacks and avoid the costs associated with them.
Let’s hash it out.
The financial impact of cybercrime and other related costs
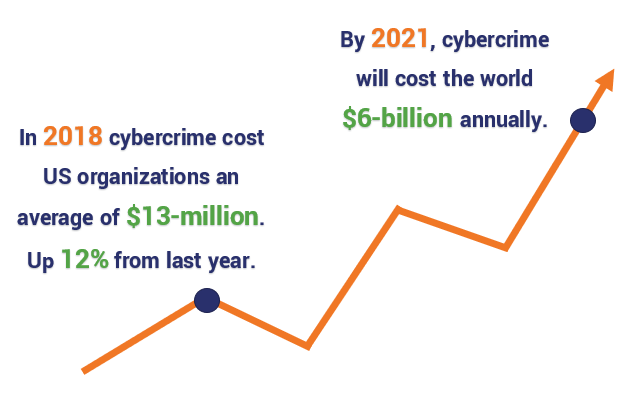
Accenture reports that cybercrime cost individual U.S. organizations an average of $13 million in 2018, an increase of 12% over the previous year. The costs of cyber attacks and data breaches are anticipated to increase over the next few years. Cybersecurity Ventures estimates that cybercrime damages will cost the global community $6 trillion annually by 2021.
Calculating the cost of cybercrime isn’t as straightforward a task as one might think. Many factors can contribute to cybercrime costs, including (but certainly not limited to):
- Lost, stolen, or destroyed data;
- Purchasing a decryption tool (paying a ransom) in response to a ransomware attack;
- Theft of intellectual property;
- Stolen funds;
- Downtime during a cyber attack and the following disruption to business operations following an attack;
- The impact to brand image/reputation;
- Loss of customer and investor trust;
- Forensic investigation costs;
- Legal costs;
- Restoration costs; and
- Fines for not meeting regulatory compliance requirements (such as Payment Card Industry [PCI], Health Insurance Portability and Accountability Act [HIPAA], and the European Union’s General Data Protection Regulation [GDPR]).
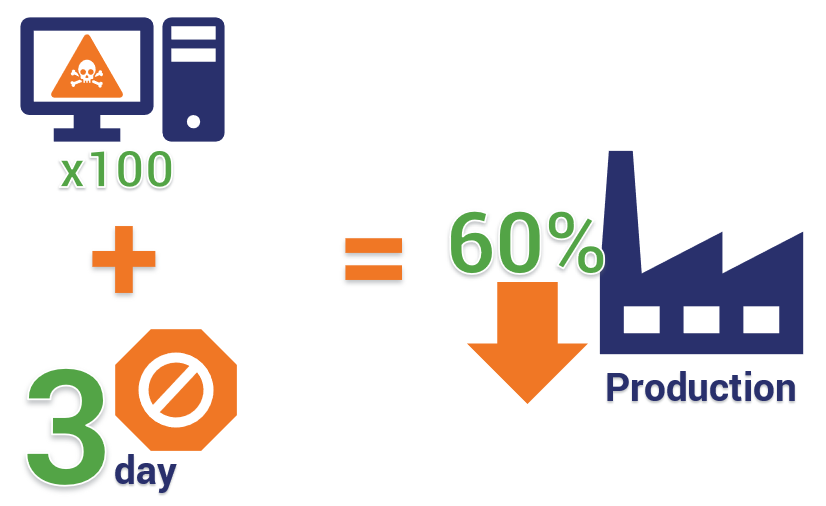
A recent example of how a cyber attack can affect business operations involves the Hoya Corporation, a Japanese optical products manufacturer with manufacturing plants in Thailand. At the end of February 2019, the company was targeted by a malware attack that infected about 100 computers, resulting in a three-day partial shutdown of its Thailand production operations and invoice operations in Japan. This reduced factory output by approximately 60%. In an official statement, the company reported that the computers were “infected with ID and password stealing viruses.”
Luckily for Hoya, their cyber posture was not as bad as other companies that have been victimized by malware attacks — while they were unable to prevent the initial phase of the attack (the spread of the malware), they did prevent the second phase’s “cryptojacking” attack, which intended to use the computers for cryptocurrency mining. As a bonus, Hoya also reported that no data leak was detected.
With the growing prevalence of cyber security attacks, there is a variation of a Warren Buffet quote floating around the internet that comes to mind that someone has altered to fit cyber security:
“It takes 20 years to build a reputation and five minutes (of cyber incident) to ruin it.” Though Buffett may not have added those extra words in the parentheses, the statement still rings true. One cyber attack, data breach, or data disclosure can destroy your business by ruining its reputation, image, and standing in the industry and community. The story of the now-defunct code hosting service Code Spaces is a prime example of such a situation. After they sustained a cyber attack, their company was forced to shut down permanently. Thankfully, in the case of Hoya Corporation, they were able to prevent the main attack before losing thousands — or even millions — of dollars in cryptocurrency or invaluable client data.
How your cyber posture can help protect your bottom line
A PricewaterhouseCoopers (PwC) survey of 3,000 business leaders from more than 80 territories reports “businesses of all sizes are ill-prepared to protect themselves and their customers.” If your company is like any of these businesses, enhancing your cyber security posture by increasing your cyber resilience is the most obvious way to reduce your risk of becoming a victim of successful cyber security attacks. This, in turn, helps to protect and improve your business’s bottom line by avoiding the resulting costs of attacks and data breaches.
Increasing your cyber security defense strength can help you:

- Reduce costs by leveraging technology and industry best practices;
- Adhere to GDPR, HIPAA, and PCI regulatory compliance requirements; and
- Avoid potentially avoid hundreds of thousands of dollars (or even millions) in fines and penalties. PCI noncompliance can even result in a possible suspension of your company’s ability to process card payments.
Here are some of the ways you can strengthen your cyber security posture to protect your bottom line:
Enhancing your cyber posture: Create barriers for cybercriminals
In IT security, the most basic way to ward off cyber attacks is the use of firewalls, antivirus, and antimalware platforms. These first-line-of-defense tools provide a barrier between your network and external networks and threats. The idea here is to make it more difficult for attackers to break into and move through your network so you have more time to identify any threat and respond. The more walls you throw up, the more time a hacker has to spend getting through your defenses — this makes their efforts less profitable and you appear like less of an appealing target.
Firewalls vary by type, purpose and application; they can be hardware, software, or both. Some involve packet filtering and stateful inspection while others aim to prevent application-layer attacks and offer threat detection and remediation. But don’t stop at just implementing firewalls. While effective in combination with antivirus and antimalware solutions at repelling many threats, they cannot protect you from everything — this is why it’s imperative to have other protections in place.
Implementing password security measures

Another method of protection is requiring frequently-changing and secure passwords of your employees and customers. This is particular important considering the results of SailPoint’s 2018 survey, which shows that 75% of surveyed employees report reusing passwords across multiple accounts, and 56% use the same password for both personal and work accounts. Flimsy password security is the Achilles’ heel of your IT security: No matter how seemingly impenetrable your cyber security defense “fortress” may be, all it takes it one employee to leave the main door unbarred for a hacker to walk right in.
Protecting email
Email is a huge vulnerability for many businesses. According to Cofense, 91% of cyber security attacks start with a spear-phishing email. Some of the ways to address these concerns is to implement email security and anti phishing solutions such as the use of email and document signing certificates. These security certs help employees digitally sign and encrypt emails and sign sensitive or confidential documents for electronic communications. These cyber protections help to authenticate email senders, prevent email and document tampering, certify documents, and are compliant with many industry standards. Email certificates enable employees to verify whether an email they receive from their boss or a colleague was, in fact, sent by them and is not a case of phishing or CEO fraud. Furthermore, sending encrypted emails protects sensitive or confidential information from being “read” by eavesdroppers and man-in-the-middle (MitM) attackers.
Enhancing your cyber posture: Test your network for vulnerabilities
Two of the most effective ways to check for weaknesses in your cyber security posture are the use of vulnerability assessments and penetration testing (also known as pen tests). A vulnerability assessment helps to identify, analyze, and prioritize any existing vulnerabilities in your systems, applications, and IT infrastructure. This differs from a pen test, which is when a cyber security expert (often a “white hat” hacker, or the “good guy” for all intents and purposes) runs attacks against your systems to test their defenses to find and exploit their vulnerabilities. The goal is to find any weaknesses in your defenses before a “black hat” hacker (the “bad guy”) does.
Enhancing your cyber posture: Increase visibility to monitor and identify threats

Knowing what is going on within your network is an essential factor in strengthening your cyber posture. External actors can hack their way through your defenses or simply walk through the front door when employees unwittingly provide their credentials and personal information (think phishing). Regardless of how they gain access, you must be able to recognize their activities quickly enough to prevent them from proceeding any further and mitigate the damage they cause. This requires increasing visibility into your network, traffic, and infrastructure through network monitoring and protection tools such as intrusion detection systems (IDSs) and intrusion prevention systems (IPSs), security incident and event management (SIEM) systems, and the establishment of a cyber security operation center (either in-house or external).
During the malware attack on Hoya, the company’s officials reported that a network server overload was noticed, which led them to investigate — and ultimately stop — the hacker’s attack from progressing to phase two. This likely involved the use of a cyber security operations center team monitoring their network, operating system, firewall, IDS activities, and endpoint devices. An effective CSOC uses SIEM tools and IDSs to monitor and identify threats.
However, even the best IDSs can’t protect against data disclosure that can occur due to phishing emails. That’s why it’s important to also implement other methods of protection and prevention that focus on your employees.
Enhancing your cyber posture: Increase employee security with training and policies

Eighty-three percent of surveyed global information security professionals reported experienced phishing attacks in 2018, according to data from ProofPoint. As dire as this statistic may be, the good news is that there are things you can do to prevent phishing and cyber attacks from being successful and reduce your company’s potential losses. One of these methods is to implement cyber security awareness training and regularly test your employees to ensure they understand and can apply their cyber security knowledge to real-life scenarios. This could include quarterly, bi-annual, or annual training and phishing tests to identify areas in which employees lack knowledge to improve future training methods.
Other methods include:
- Using email protection and anti phishing solutions,
- Implementing and enforcing computer use policies, and
- Limiting access to databases, client records, and other sensitive systems to only those employees whose jobs necessitate access through a policy of least privilege (POLP).
Enhancing your cyber posture: Increase cyber security capabilities with third-party services
Earlier, we mentioned the idea of a cyber security operation center, which is a security-as-a-service product that is used to monitor, identify threats, and respond to security attacks. However, not all companies have the capacity or budget to implement an in-house CSOC. This is why it’s beneficial to use a third-party SaaS solution to augment your existing defenses with a team of IT security experts who provide 24/7 security monitoring. Partnering with a third-party security-as-a-service provider is a cost-effective way of gaining the benefits of an in-house CSOC without having to pay the hefty price tag that often accompanies hiring an entire team of in-house IT security pros. (One such example of a CSOC is CWatch Web by Comodo.)
How to make your cyber posture work in favor of growing your company’s bank account
So far, we’ve discussed many of the benefits of cyber security in terms of how it helps to reduce the costs that could from cyber attacks. But, how can you capitalize on the advantages of cyber security posture strength to increase your business’s profitability? It often boils down to making your customers feel more comfortable and confident.

According to a report by Capgemini’s Digital Transformation Institute, 77% of consumers rank cyber security as the third most important factor when choosing a primary retailer and their products. The report states that customers are more satisfied and “approximately 40% of consumers would be willing to increase their online spend 20% or more if their primary retailer gave them certain assurances which built their trust.” This goes to show that implementing cyber security best practices not only helps to improve your site’s security and reduce cybercrime-related costs, but it can potentially increase your profitability. However, there is more to it than simply implementing cyber security methods to increase your security posture — the key to driving business (and its resulting profit) is creating a perception of security.
How to profit from your security posture: Talk about your cyber security efforts and initiatives

We already covered some of these concerns in the previous section about how to protect your bottom line by mitigating costs relating to cyber security attacks and cybercrime. What we didn’t mention was the idea of communicating your efforts to the public, your customers, and investors alike. As the Capgemini survey shows, consumers care about the security of their data and want to know that you’re doing everything within your power to protect it.
According to an article by Consumer Goods Technology (CGT), improving your bottom line as a retail businesses is intricately tied to data privacy and security:
“Cyber security represents a lucrative opportunity for retailers to improve customer satisfaction and drive online spending,” added Tim Bridges, Capgemini’s global sector lead for consumer products, retail and distribution. “Only retailers that are able to efficiently align their cyber security measures with customer expectations will be able to impact top line revenue.”
What all of this means is that you need to be able to address consumer privacy concerns with clear messaging about how their information may be used and what you are doing to protect their data. Your ability to articulate this information is a significant factor in influencing and building consumer trust.
How to profit from your security posture: Increase accessibility and security across all platforms
Make your company and services more accessible and secure across all channels — your website, email, call center, social channels, brick-and-mortar point of sale (POS) systems. etc. Consumers want to shop how, when, and where it is most convenient for them. This means using cyber security technologies and best practices that encrypt customer data to keep it from falling into the wrong hands.

Using SSL/TLS (secure sockets layer and transport layer security) certificates on your website is a great way to increase your security and grow customer trust. SSL/TLS certificates — which are essentially the same thing (minus some technical differences) — are used to authenticate a website, domain, or organization and create an encrypted connection while displaying corresponding security indicators (padlock, green bar, etc.) on a user’s web browser. Many SSL certificates also offer site seals that you can display on your web pages to increase consumer confidence in your website and brand.
Visual safety indicators play a significant role in creating a perception of security, which can contribute to increasing your overall profitability. According to research from the Baymard Institute:
“In prior research we have documented how users have little understanding of the actual technical security of web pages and instead mainly rely on what their gut feeling is telling them. It’s therefore recommended that you add visual clues – such as borders, background colors, and site seals – to your online payment forms to increase the perceived security of the sensitive fields in the form in order to make your users feel more comfortable when handing over their credit card information.”
How to profit from your security posture: Get your IT systems & business up and running ASAP
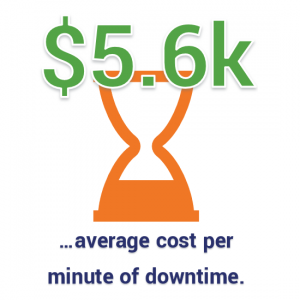
According to Gartner, the average cost of downtime is $5,600 per minute, which equates to $336,000 per hour. Realistically, many companies can absorb the cost of a few minutes of downtime without it making much of an impact. However, imagine if that downtime lasted an average of 14 hours — which is what KnowBe4 report indicated was the average downtime for 500 surveyed companies from 50 countries. That substantial amount of downtime (which would cost more than $4.7 million) would significantly reduce your revenue (not to mention your bottom line). For many small to midsize businesses (SMBs), this type of damage will force them to close their doors within six months.
According to IBM, downtime not only affects your business operations, it also reduces your company’s competitive advantage:
“Today, digital business channels represent a greater market share and can drive revenue generation. Apart from revenue and productivity losses, customers do not tolerate downtime. They will quickly abandon a business and use a competitive firm to meet their needs.”
With proper planning, you can reduce the downtime your business could experience from cyber attacks and outages by using data backup methods and disaster recovery plans. Having an up-to-date incident response plan, IT disaster plan, and business continuity plan (BCP) (as well as regularly testing your plans and data backups) helps to ensure that you have the people, resources, and processes in place to immediately begin getting your IT systems — and, ultimately, your business — up and running ASAP after an emergency.
How to profit from your security posture: Increase your competitive advantage through customer confidence, trust, and loyalty
One of the most critical ways your cyber security posture benefits your profitability comes in the form of increasing consumer confidence and trust. According to a survey by The Harris Poll for IBM, data security is a primary concern for global consumers: “75 percent will not buy a product from a company – no matter how great the products are – if they don’t trust the company to protect their data.” This means that consumers who perceive your site as secure are more likely to do business with your company — giving you a competitive advantage over other businesses.

Openly communicating about your investment in IT security defenses and protections, as well as using SSL/TLS certificates that offer web browser security indicators and email security certificates that authenticate your employees, helps to inspire customer trust and lead to improved customer retention and loyalty. For online retailers, this can result in higher conversions and means that customers are less likely to abandon their virtual shopping carts.
How to profit from your security posture: Boost your SEO rankings with SSL/TLS certificates
Did you know that you can boost your search engine optimization (SEO) rankings by up to 5% on Google simply by installing SSL/TLS certificates on your server? Converting your website(s) to HTTPS (hypertext transfer protocol secure) communicates that you have authenticated your domain(s), subdomain(s), and business with the proper certificate authorities. Google looks at this in a highly favorable light and has integrated SSL/TLS as one of the ranking signals in its search results ranking algorithm.
In summary
While providing a strong security posture is important for your business from an IT security perspective, it’s easy to see how it’s also imperative from the financial perspective of your business as well. Increasing your cyber security stance — and communicating how you have done so — helps to increase customer trust and confidence, which translates to increased business and revenue. This change of mindset provides your business with a strategic new approach to increasing profitability and not just reducing costs.
What other ways do you think that increasing your cyber security posture benefits your bottom line?
As always, be sure to share your thoughts or ask questions in the comments section below.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown