Java Ransomware (Literally): Not Even Your Coffee Maker Is Safe
The Proliferation of IoT Devices is Brewing New Security Vulnerabilities in the Most Unlikely Places
Your alarm goes off and you crawl out of bed, just like every other day. Still groggy and half-awake, all you can think about is the sweet salvation that is your morning cup of joe. You slowly will yourself over to the coffee maker. As you get closer a hint of yesterday’s brew pleasantly fills your nose. You’re so close, all that’s left to do is push the power button and start brewing.
The screen illuminates, everything is ready to go, and then you see this:

No, you aren’t still sleeping, and this isn’t some kind of weird dystopian nightmare. Unfortunately you’ve become yet another victim of ransomware, this time from the most unlikely of sources.
The number of “smart” devices in our homes is increasing rapidly, and with it comes more opportunities for hackers to infiltrate our lives. The Internet of Things (IoT) allows these machines to communicate with the cloud via some sort of connectivity, providing a great number of benefits to the end user such as automatic adjustments, alerts/notifications, and data gathering. But that connectivity can be a double-edge sword, giving third parties a direct route into your home or business.
Words can’t espresso the dangers of these vulnerabilities. Crippling your coffee maker or fridge would certainly be annoying, but what if the same thing happened to your automobile as you’re driving down the highway at 80 mph? Proper security measures for IoT devices is critical. As Mike Nelson, DigiCert’s VP of IoT Security explains:
“Connectivity is growing into every corner of our lives. This connectivity presents new risks that people and businesses aren’t used to thinking about. A rule of thumb for cybersecurity is that any device that connects to something will eventually be hacked.”
Mike Nelson, VP of IoT Security, DigiCert
So how did hackers manage to gain access to a coffee maker in the first place? How could it have been prevented? And what lessons can we learn as a result?
Let’s hash it out.
For Whom the Bean Tolls
It all started with a coffee maker from the company Smarter (we’ll see very soon just how ironic that name is). Security issues with their products were first discovered back in 2015. The London-based security firm Pen Test Partners discovered that they were able to recover the Wi-Fi encryption key used in version 1 of the Smarter iKettle.
Later, they found more issues in both the iKettle version 2 and a previous version of the Smarter coffee maker (pictured below).

It turns out there was no firmware signing and no protected area inside the chipset of the devices. Nelson elaborates on the possible consequences:
“Not signing firmware updates and storing security credentials in unprotected memory is giving away the keys to your kingdom. This opens the potential for a hacker to embed malware in your update package, and to masquerade as a trusted actor in your ecosystem with no limitation of what they could do.”
Mike Nelson, VP of IoT Security, DigiCert
Researchers were able to do just that with the appliances, ultimately reverse engineering the device protocol to allow for remote control.
In 2018, Smarter released updated versions of both the iKettle and the coffee maker which used a new chipset to fix the vulnerability. However, Smarter never issued any kind of alert and didn’t publicly warn customers about the problem, despite many of the older versions still being in use today.
Kettle Down, It’s Just an Experiment
Martin Hron, a researcher at security firm Avast, was curious as to what exactly he could achieve by exploiting the vulnerability. He set out to reverse engineer one of the older-version coffee makers as a thought experiment. He spent a mere week at work on it, yet was able to achieve quite a bit.
Hron figured out a way to turn on the burner, spin the grinder, dispense water, and display messages on the LED screen, all while playing an extremely annoying beeping sound in the background non-stop. You can see his handywork in action here:
What’s even scarier is that this is a type of “out-of-the-box” vulnerability. It didn’t require any kind of special configuration or physical modification.
There’s a Latte of Dangers With Smart Devices
Upon plugging in the Smarter coffee maker, Hron discovered that it acted as a Wi-Fi access point with the intention of communicating with a smartphone app. The problem? It used an unsecured connection. Without any encryption, he had no problem learning how the phone app controlled the coffee maker. And since there was no authentication either, he came to the conclusion that a rogue app would be able to do the same thing.
He was limited by the small selection of commands initially available though, so he went a step further and started looking into how exactly the coffee maker got firmware updates. In a not-so-shocking (or in this case, scalding) turn of events, he found that they were received with no encryption, no authentication, and no code signing.
With this knowledge in hand, he was able to pull the latest firmware version from the Android app and reverse engineer it. He used IDA, an analyzer, debugger, and disassembler that’s commonly used for that purpose. What he discovered was that the firmware was in plain-text, human-readable strings that were ultimately uploaded directly into the FLASH memory of the coffee maker.
Grinding Out New Firmware
The next step was to open up the coffee machine and determine what CPU the coffee maker was using. That way, he’d be able to transform the binary code of the firmware into the base assembly language that that could communicate directly with the coffee maker. You can see the disassembled insides of the machine below (courtesy of his own blog post on the subject):
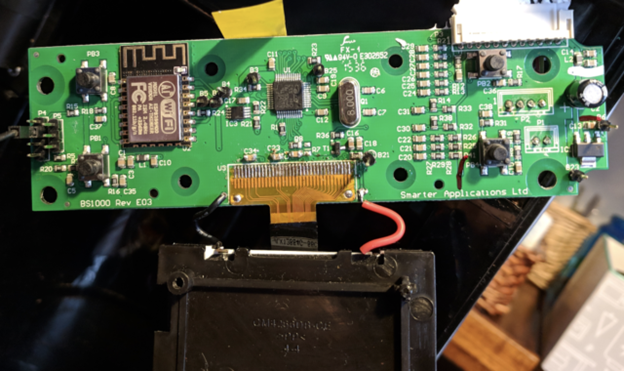
Hron was on the home stretch. He knew exactly how to manipulate the most important functions, such as checking if a carafe is on the burner, sounding a beep, and installing updates. From there, he wrote a python script which imitated the update process. He played around with a few ideas, including mining cryptocurrency, but found that the CPU speed of 8MHz made that impractical.
So, he switched to ransomware instead. By taking advantage of some unused memory space, he was able to add a few lines of code that displayed the ransom message. Hron said that they “thought this would be enough to freak any user out and make it a very stressful experience. The only thing the user can do at that point is unplug the coffee maker from the power socket.” I would certainly be “freaked out” if I saw this displayed:

The Gritty Details
The Wi-Fi connection was originally able to be made because the machine uses an ad-hoc SSID until it can be connected to a home network. After that, it goes away. A hacker could work around this if they knew that the coffee maker was on a particular network by sending a deauthorization packet that would lead to it getting disconnected. Then, the device would go back to broadcasting the ad-hoc SSID that’s vulnerable to malicious firmware updates. One could even go a step further by sending that same deauthorization packet to every Wi-Fi network in range, then wait and see if any ad-hoc SSID’s appear.
That’s only the tip of the possible iceberg, however. Hron believes that with more work, one could make the coffee maker attack other devices on the same network. Which means your computer, router, cell phone, and other devices could be at risk.
The map below shows the nearly 570 Smarter coffee makers that aren’t using the “smart” features (which actually makes them easier to hack):
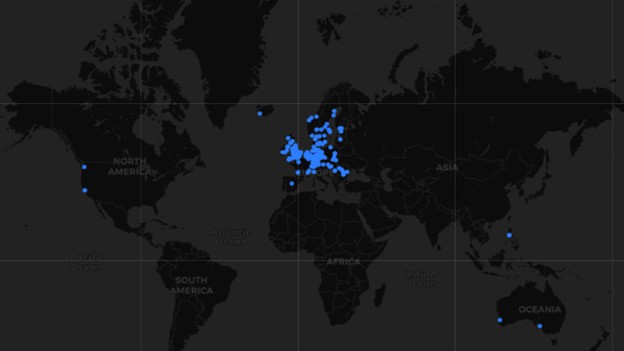
This is a very small subset of one version of one device from one brand. Think how many other devices exist in the wild that aren’t full secured: things like TV’s, appliances, security cameras, lightbulbs, doorbells, etc. The number could easily be in the millions.
Avoiding a Case of Déja-Brew
The worst part is that this particular model of coffee maker is no longer eligible for firmware updates. If you happen to own it, there’s literally nothing you can do to patch the vulnerability discovered by Hron. It’s one of the most concerning aspects of modern IoT devices. Take your fridge for example. Most people will own theirs for a decade or more. Can we really expect vendors to provide software support over a span of 10-15+ years?
If manufacturers don’t do things right the first time, then we’ll be on track to fill our homes with vulnerable, abandoned devices that can be exploited to create data leaks, ransomware attacks, network breaches, and more. There are other ways that end users can protect themselves, such as using a virtual LAN and a separate, isolated SSID for example. But do you really think your aunt or grandpa are going to be savy enough to do that? After all, we buy “smart” devices to make things easier, not complicate our lives further. Nelson agrees, feeling that:
“Consumers have the right to assume the security and safety of products they buy off the shelf. There are certainly things consumers can do to improve security, but manufacturers have the ultimate responsibility to build ‘secure by design’ products and make it easy for consumers to implement security best practices like multi-factor authentication and good password management.”
Mike Nelson, VP of IoT Security, DigiCert
It goes to show just how important encryption and authentication are to IoT security. They must be implemented in every device at every stage, from chip production to end-of-life. Authentication is especially important, as it only allows trusted devices to connect to the network. Certificates do this in a scalable and elegant way that doesn’t require user interaction (unlike, say, passwords or hardware authentication). They also provide integrity out-of-the-box via code signing, preventing malware from running and protecting over-the-air updates throughout the device’s lifetime.
IoT Security Platforms Mocha Life Easier (Like DigiCert®’s IoT Trust Manager)
Certificate Authorities already have products that are geared towards IoT devices, such as DigiCert®’s IoT Trust Manager, which is continuously being developed and improved as IoT technology evolves. The DigiCert® IoT Trust Manager is built on DigiCert ONE, a new PKI management platform, and takes a modern approach to securing IoT networks via:
- Flexible deployment: DigiCert® Iot Trust Manager utilizes containerized architecture to enable hosted, private and public cloud, on-prem, in-country and hybrid deployments (so you can enjoy all managed PKI benefits no matter how you deploy it).
- Fast deployment: With their Docker configured, customers can have DigiCert® IoT Trust Manager and DigiCert One up and running in less than one hour, rather than taking 4-6 weeks, as legacy PKI management solutions require.
- Metadata: Manufacturers can import all device identity and other deployment information into DigiCert® IoT Trust Manager to track details about each device, in conjunction with the certificate issued to the device.
- Full device lifecycle authentication: DigiCert® IoT Trust Manager provides full device lifecycle authentication, encryption, and integrity by embedding a certificate into the silicon or microchip and tracking it through the device lifetime. This provides full end-to-end security from manufacturing through end-of-life.
Solutions like these make effective IoT security both easier and more effective, allowing for manageable scalability as more and more of our devices become “smart.” In the end however, it’s up to manufacturers to actually adopt these measures to ensure that consumers stay protected.
Don’t Leave Your IoT Devices Exposed
Want to know more about the challenges facing IoT devices and how DigiCert®’s IoT Device Manager can help you overcome them? Grab our FREE IoT PKI Security Basics Kit now.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown