PayPal Phishing Certificates Far More Prevalent Than Previously Thought
Over 14,000 SSL Certificates issued to PayPal phishing sites.
Earlier this month I discussed the use of Let’s Encrypt certificates on PayPal phishing sites. In that article I asked Let’s Encrypt to stop issuing certificates containing the term “PayPal” because of the high likelihood they would be used for phishing.
That requested stemmed from the fact that PayPal is a high value target and that Let’s Encrypt had already issued nearly 1,000 certificates containing the term “PayPal,” more than 99% of which were intended for phishing sites.
With expanded research, we found our previous claim was a major underestimate. Let’s Encrypt has actually issued 15,270 “PayPal” certificates. This reveals the previously unknown extent of the Let’s Encrypt phishing phenomenon.
The Let’s Encrypt Phishing Connection
One of the primary fears voiced by critics of Let’s Encrypt – a fear that predates the Certificate Authority’s launch – was that the service would become the go-to CA for phishers because its SSL certificates were free. Let’s Encrypt also has an unconventional stance on the role of the CA, arguing that it was not the CA’s job to stop malicious sites from using its certificates. This meant that phishers and malware distributors were free to use Let’s Encrypt without any risk of being banned or having their certificate revoked.
Despite the concerns of many around the industry, Let’s Encrypt’s stance is in full compliance with industry standards. Regardless, that policy in combination with offering free certificates does create a very attractive environment for phishers.
In my previous article I said Let’s Encrypt had issued 988 certificates containing the word “PayPal” – for example, paypal.com.secure-alert.net. Typically, CAs would not issue certificates like this due to the likelihood they will be used to aid criminal activity.
Of those 988, 99.5% of the certificates were being used (or had been used) for phishing. While this proved that there was wide-spread abuse, it was not at the scale many had expected when Let’s Encrypt was first announced.
We now have new data that captures the full extent of the “PayPal” certificates that have been issued by Let’s Encrypt. This new data comes from crt.sh – a search engine for certificate transparency logs – and reveals that the service has been significantly more popular with phishers than previously reported.
Between January 1st, 2016 and March 6th, 2017, Let’s Encrypt has issued a total of 15,270 SSL certificates containing the word “PayPal.”
This figure is more than ten times larger than previous estimates that have been published. The vast majority of this issuance has occurred since November – since then Let’s Encrypt has issued nearly 100 “PayPal” certificates per day.
Based on a random sample, 96.7% of these certificates were intended for use on phishing sites.
The internet is currently moving from HTTP to HTTPS, spurred by a number of initiatives to “encrypt everything.” Encrypting everything includes the bad sites, and the widespread use of HTTPS on malicious sites has been a concern for some.
For many years, the security industry as a whole incorrectly taught users to associate HTTPS and the green padlock with a “safe” site. This is a bad generalization, which may lead users to believe a phishing site is real if it is using SSL.
In addition, Chrome’s new UI displays “Secure” next to every site with a valid SSL certificate and HTTPS configuration. What’s the chance that a user misconstrues the meaning of this and sees a phishing site as legitimate?
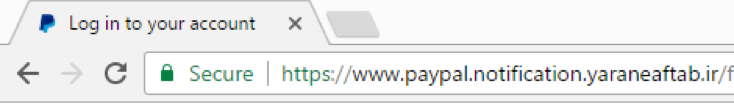
While our research has focused on PayPal phishing, there are many other targets out there including Bank of America, Apple IDs, and Google. Let’s Encrypt has issued thousands more of these certificates.
This new data clearly shows that use of HTTPS on phishing sites is significantly higher than previously thought.
The Data
This section expands on our data and methodology.
Our Source
Let’s Encrypt submits all of the certificates it issues into certificate transparency logs, a mechanism designed to increase public transparency into the activities of CAs. The logs also act as an excellent source for researchers who want to analyze a CA and the SSL certificate ecosystem.
Not all CAs log their certificates, as this is currently an optional practice (though not for long). Because Let’s Encrypt voluntarily logs, it allows us to get very accurate data about its issuance activity.
Last week we reported Let’s Encrypt had issued 988 “PayPal” certificates. That figure came from the methodology used by previous works. Upon further research, we found that method was limited in scope and was capturing only a small portion of the population.
Our new figure of 15,270 certificates comes from crt.sh, a Certificate Transparency search engine operated by Comodo. That is the total number of certificates issued by Let’s Encrypt that contain the word “PayPal” somewhere in the certificate’s identities (either a Common Name or a SAN) between March 25th, 2016 and March 6th, 2017 (our search covers all of 2016, but no matching certificates were issued until March). This is a sub-string search that includes all hostnames containing “PayPal” anywhere within the name.
Such a complete search is not possible through crt.sh’s website because of the scale of the query. Rob Stradling, who developed crt.sh, queried the database directly and provided me with this data upon request.
To compare Let’s Encrypt to other CAs, we ran the same search for the same date range for other CAs included in crt.sh’s database. During the same time period, all other CAs combined issued 461 “PayPal” certificates that were potentially used for phishing sites. This number excludes results that could be confidently ruled out as legitimate sites and services operated by PayPal.
Because many CAs do not participate in certificate transparency, their certificates only appear in a log if a third-party decides to log them. Thus it is likely some “PayPal” certificates issued by other CAs have not been logged and therefore not counted. However, I believe the number is fairly accurate, and even if we are very generous with our margin of error, all other CAs combined represent less than 1/10th of Let’s Encrypt’s volume of PayPal phishing certificates. This shows that the use of SSL certificates on PayPal phishing sites is directly tied to Let’s Encrypt’s entry into the market.
Rate of Issuance
It took phishers some time to adopt Let’s Encrypt as their CA of choice. Our search covered all certificates issued between January 1st 2016 and March 6th, 2017.
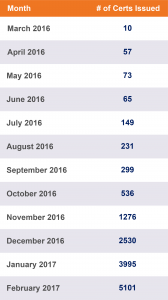 Let’s Encrypt has been issuing certificates since late 2015, when they were in a public beta. However, the first Let’s Encrypt phishing certificate for Paypal was not issued until March 25th, 2016. On the right is a per month breakdown.
Let’s Encrypt has been issuing certificates since late 2015, when they were in a public beta. However, the first Let’s Encrypt phishing certificate for Paypal was not issued until March 25th, 2016. On the right is a per month breakdown.
The number of PayPal certificates increased substantially in November 2016. There does not appear to be any specific cause for the increase. It may simply be that it took some time for word to spread amongst the phishing communities and for technical expertise to be developed.
The various initiatives encouraging HTTPS are likely to appeal to phishers as well. There are a number of performance benefits (such as HTTP/2) only available to sites using HTTPS. In addition, sites using valid SSL certificates are given trusted UI indicators by browsers (the padlock icon in all browsers, the “Secure” label in Chrome) which make a phishing site look more legitimate.
In November, more than 1,000 “PayPal” certificates were issued for the first time. That number doubled in the following month and has increased month over month since then. February of this year has seen the highest issuance yet, with more than 5,000 certificates.
Since November, when the amount of activity significantly increased, more than 100 “PayPal” certificates have been issued per day, on average.
Based on the data available so far, this month (March 2017) will be the first full-month decline since June of 2016.
Prevalence of Phishing
We estimate that 96.7% of the 15,270 certificates were (or are) used for phishing (that’s 14,766 certificates). Most phishing sites are quickly reported to their web hosts and detected by services such as Safe Browsing and subsequently taken offline. Once flagged as dangerous, a phishing site becomes useless. The majority of the sites are not currently conducting any activity.
To determine the ratio of phishing sites vs. legitimate ones, we took a random sample of 1000 certificates and reviewed them by hand. For the vast majority of certificates, the hostname made the purpose of the site clear. We avoided false positives by labeling sites as “legitimate” when we were unsure, and visited the sites when necessary.
In our previously reported data we performed the same check on all the certificates. In that group of 988, only 4 of the sites were legitimate, giving us a phishing rate of 99.6%.
In our new sample we found a phishing rate of 96.7%.
Both cases show that nearly all “PayPal” certificates being issued by Let’s Encrypt are intended for phishing, and legitimate users make up only a single-digit share.
Conclusion
Assuming that current trends continue, Let’s Encrypt will issue 20,000 additional “PayPal” certificates by the end of this year.
Let’s Encrypt takes a hands-off approach when it comes to moderating issuance and revoking certificates because it does not fit with its goal of encrypting every website.
We do believe there are valid reasons for that approach, but question its indiscriminate application. After publishing our previous article we had a great discussion with the community on our website and on social media. There were many good rebuttals to my request that Let’s Encrypt blacklist “PayPal”, and we now think there are other viable solutions to this problem and other end-goals to pursue.
Our main goal in publishing these expanded figures is to show how popular the use of SSL is on phishing sites. If Let’s Encrypt will issue upwards of 35,000 “PayPal” certificates by the end of 2017, there are likely tens of thousands more targeting other popular sites and services. The security community, and internet users at large, should be aware of the extent of this activity.
The security community has previous speculated about the use of SSL on malicious sites. We hope this data serves as early proof that there is widespread use, at least in the subcategory of phishing. Future studies of phishing should consider the potential benefits and appearance of legitimacy granted to phishing sites using HTTPS instead of HTTP.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown