Executing a Man-in-the-Middle Attack in just 15 Minutes
Getting in the middle of a connection – aka MITM – is trivially easy
Note: This article, which was originally published in 2018, has been updated to include related news & media resources.
One of the things the SSL/TLS industry fails worst at is explaining the viability of, and threat posed by Man-in-the-Middle (MITM) attacks. I know this because I have seen it first-hand and possibly even contributed to the problem at points (I do write other things besides just Hashed Out).
Obviously, you know that a Man-in-the-Middle attack occurs when a third-party places itself in the middle of a connection. And so that it can be easily understood, it’s usually presented in the simplest iteration possible—usually in the context of a public WiFi network.
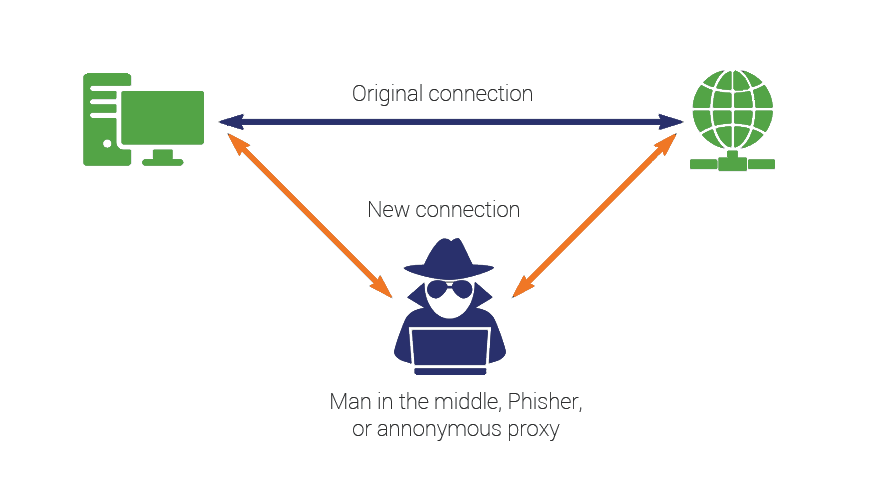
But there’s a lot more to Man-in-the-Middle attacks, including just how easy it actually is to pull one off.
So today we’re going to unmask the Man-in-the-Middle, this article will be a precursor to a future white paper by that same name. We’ll talk about what a MITM is, how they actually occur and then we’ll connect the dots and point out just how important HTTPS is in defending against this.
Let’s hash it out.
Before we get to the Man-in-the-Middle, let’s talk about internet connections
One of the most misunderstood things about the internet in general is the nature of connections. Ross Thomas actually wrote an entire article about connections and routing that I recommend checking out, but for now let me give the abridged version.
When you ask the average internet user to draw you a map of their connection to a website, it’s typically going to be point A to point B—their computer to the website itself. Some people might include a point for their modem/router or their ISP, but beyond that it’s not going to be a very complicated map.
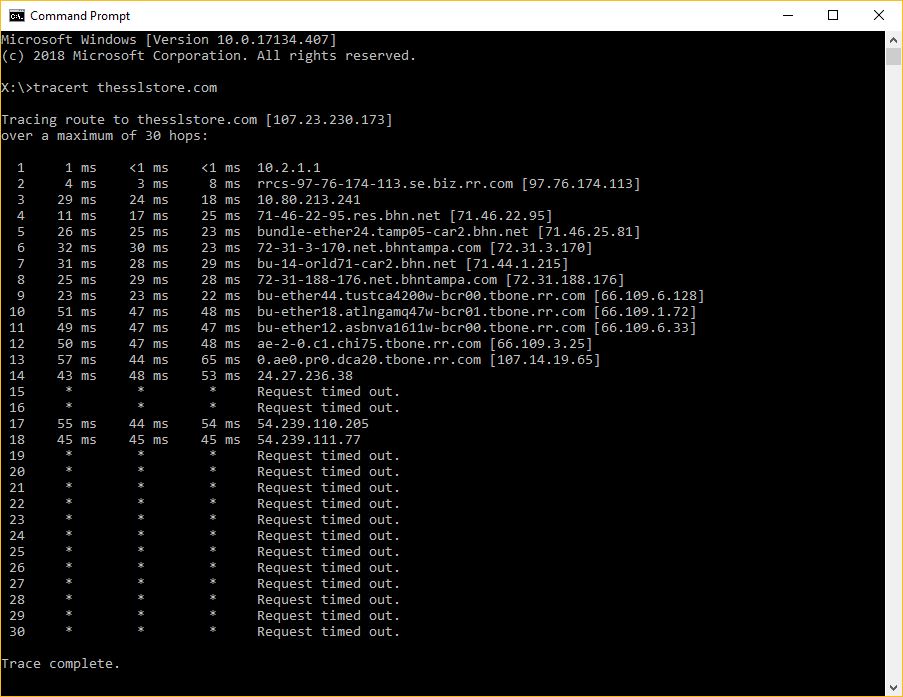
In reality though, it IS a complicated map. Let’s use our website to illustrate this point a little bit better. Every operating system has a built-in function called “traceroute” or some variation thereof.
This tool can be accessed on Windows simply by opening the command prompt and typing:
tracert thesslstore.com
Doing this will show you part of the route your connection traveled on the way to its destination – up to 30 hops or gateways. Each one of those IP addresses is a device that your connection is being routed through.
When you enter a URL into your address bar your browser sends a DNS request. DNS or Domain Name Servers are like the internet’s phone book. They show your browser the IP address associated with the given URL and help find the quickest path there.
As you can see, your connection is not nearly as simple as point A to point B or even point C or D. Your connection passes through dozens of gateways, often taking different routes each time. Here’s an illustration from a Harvard course of the path an email would have to travel from a scientist’s computer in Ghana to a researcher’s in Mongolia.
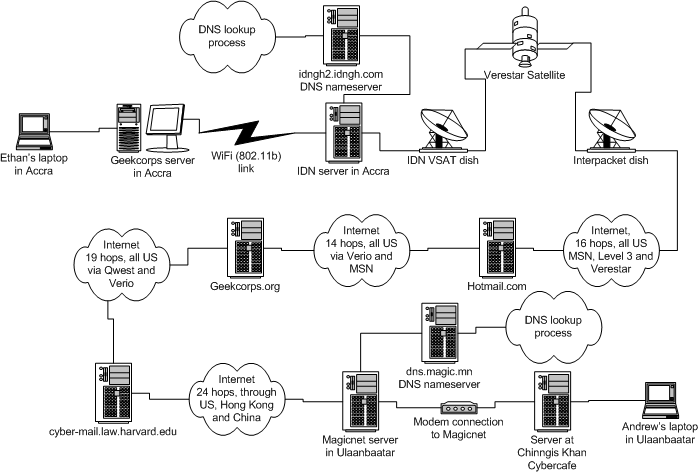
All told, that’s at least 73 hops. And here’s the thing: not all of those gateways are secure. In fact, most aren’t. Have you ever changed the ID and password on your router? Or any of your IoT devices for that matter? No? You’re not in the minority – less than 5% of people do. And hackers and criminals know this. Not only does this make these devices ripe for Man-in-the-Middle attacks, this is also how botnets get created.
What do you picture when I use the word, “Hacker?”
Before we go any further, a couple of disclaimers. First of all, admittedly this article has a bit of a grey/black hat feel. I’m not going to give blow-by-blow instructions on how to do the things I’m about to describe because that feels a little bit irresponsible. My intention is to give you a reference point for discussing the realities of MITM and why HTTPS is so very critical.
Second, just to underscore how easy this is I’d like to point out that I learned all of this in about 15 minutes using nothing but Google. This is readily-accessible information and well within the abilities of even a novice computer user.
We have this image of hackers thanks to TV and movies:
But, contrary to their depiction in popular culture, most hackers aren’t really like that. If they’re wearing a hoodie at all, it’s definitely not obscuring their face as they type command prompts in a poorly-lit room. In fact, many hackers even have lights and windows in their offices and apartments.
The point is this: hacking really isn’t as difficult or sophisticated as it’s made to look—nor is there a dress code. It’s a lot more common than people realize. There’s a very low barrier to entry.
SHODAN, a Google search and a Packet Sniffer
SHODAN stands for Sentient Hyper-Optimised Data Access Network. It is a search engine that can locate pretty much any device that’s connected to the internet. It pulls banners from these devices. A banner, in this context, is basically a snippet of information relating to the device itself. SHODAN port scans the internet and returns information on any device that hasn’t been specifically secured.
We’re talking about stuff like IP addresses, device names, manufacturers, firmware versions, etc.
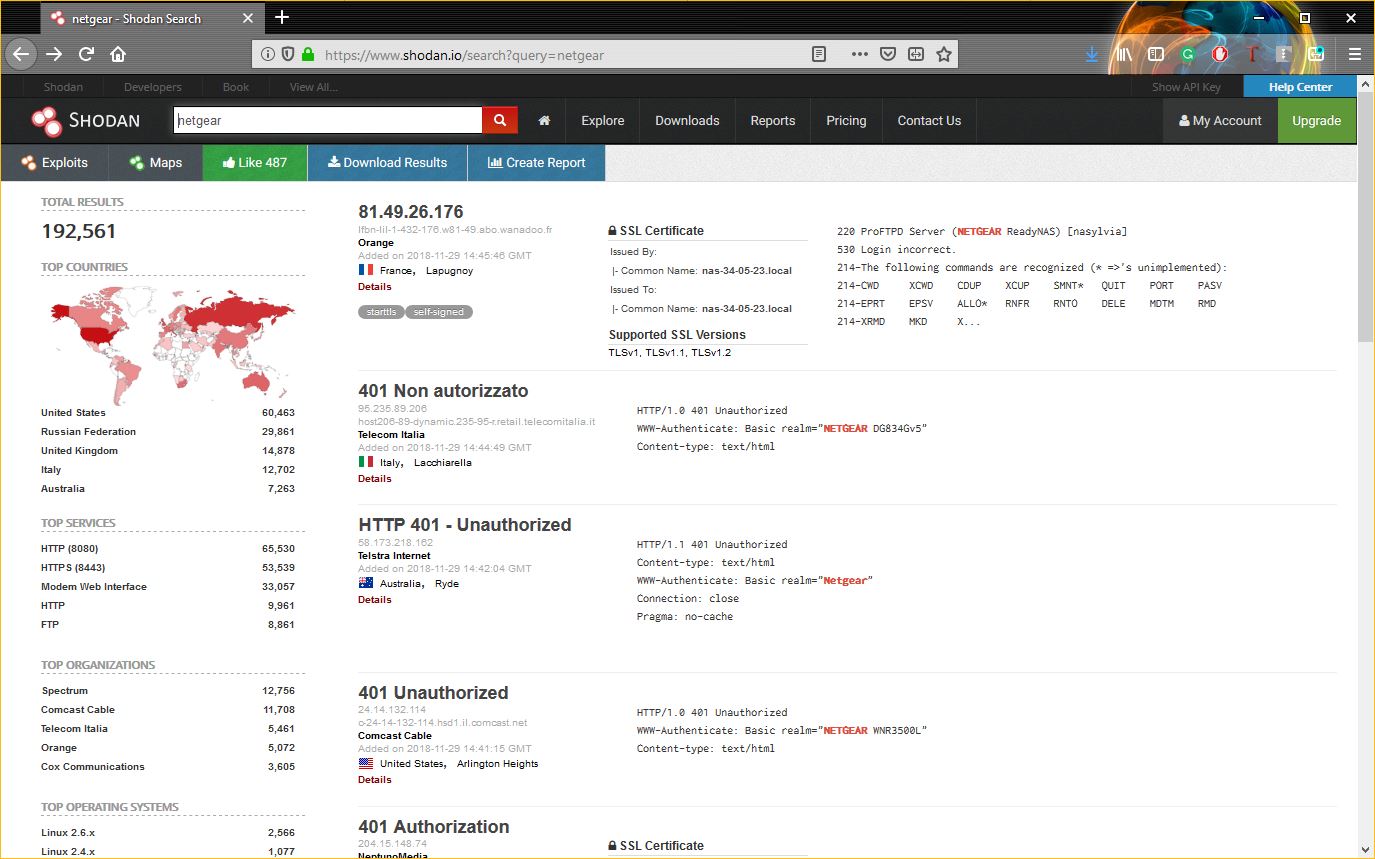
SHODAN is kind of terrifying when you consider all the ways it can be misused. With the right commands you can narrow your search down to specific locations, going as granular as GPS coordinates. You can also search for specific devices if you have their IP addresses. And as we just covered, running a traceroute on a popular website is a great way to get a list of IP addresses from gateway devices.
So, now we have the means to track down specific devices and we can look for high volume MITM targets, many of which are unsecured and still using default settings.
The beauty of the internet is that you can typically find out what those default settings are, specifically the admin ID and password, with only the cunning use of Google. After all, you can figure out the make and model of the device from the banner, so finding the default info will be no problem.
In the example above I made a simple search for NetGear routers. A quick Google search for its default ID/password yields the requisite information in the snippet – I don’t even have to click one of the results.
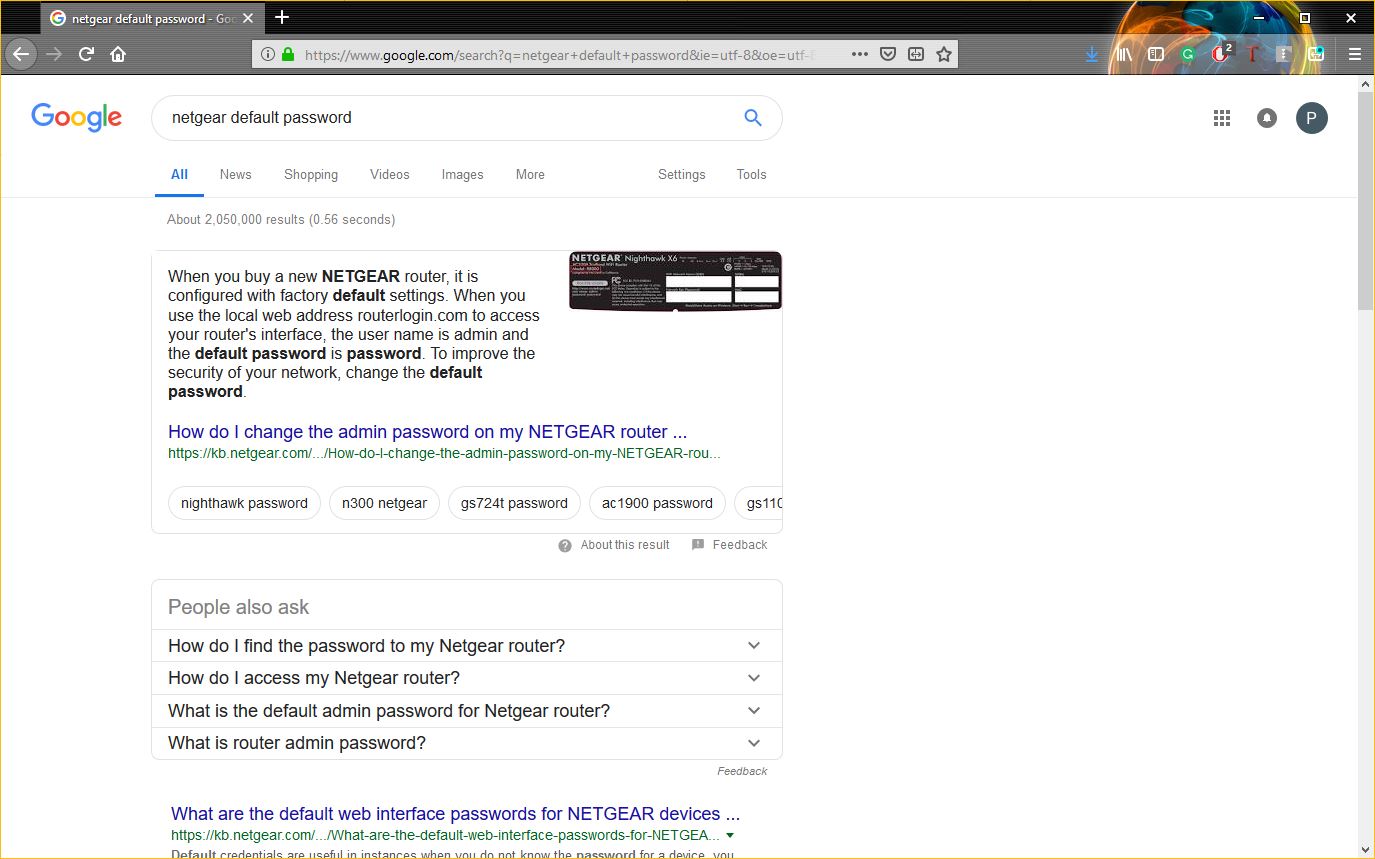
With that information in hand, we can gain unauthorized access to any unsecured version of a NetGear device and perform our Man-in-the-Middle attack.
Now let’s talk about packet sniffers. Data being sent across the internet is not sent in some steady stream. It’s not like a hose where the data just flows onward. The information being exchanged is encoded and broken down into packets of data that are then transmitted. A packet sniffer inspects those packets of data. Or rather, it can if that data is not encrypted.
Packet sniffers are readily available on the internet, a quick search on GitHub yields over 900 results.
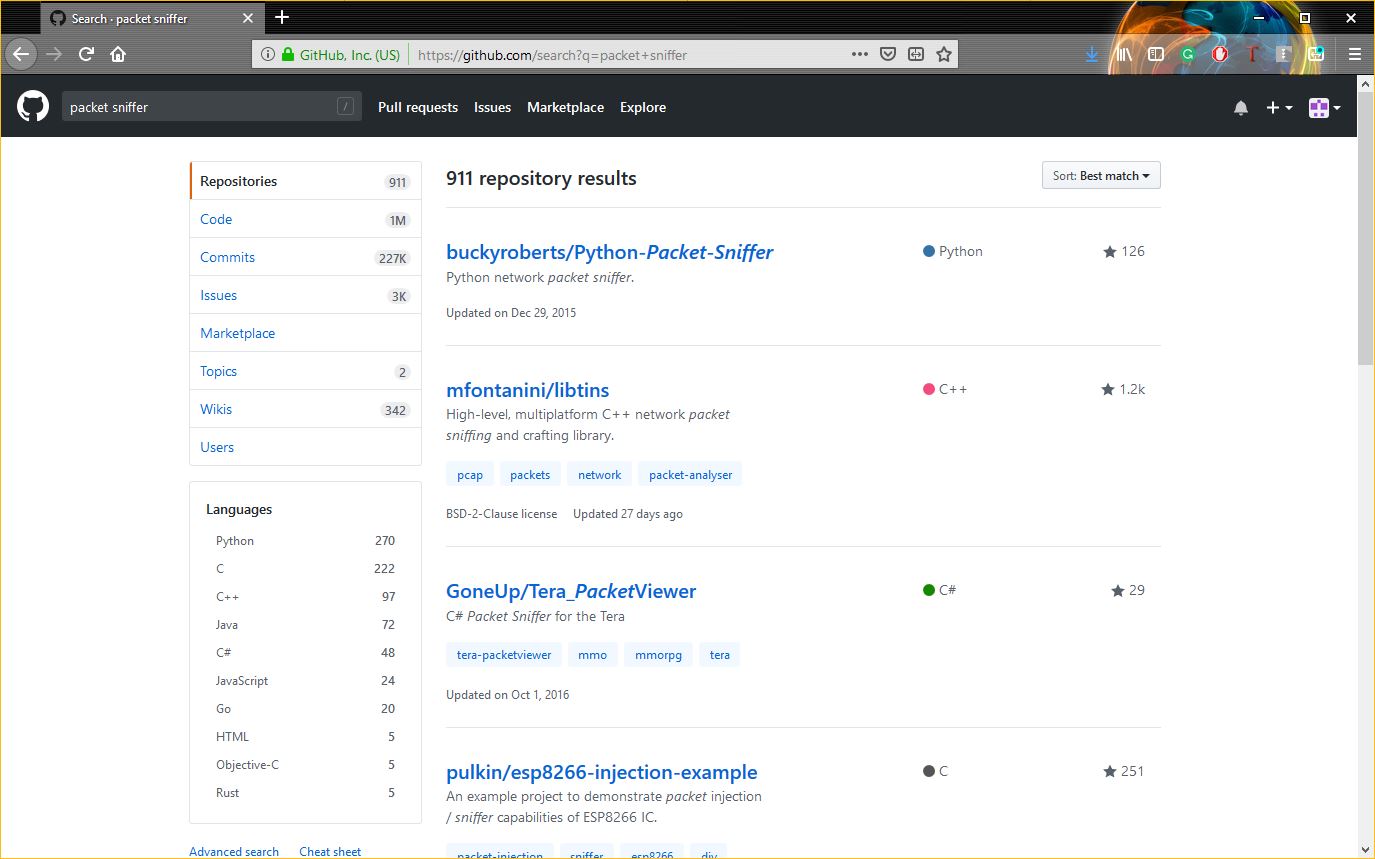
Not every packet sniffer is going to work nicely with every device, but again, with Google at our disposal finding the right fit won’t be difficult.
We actually have a couple options, we can find a packet sniffer that will integrate right into the device we’re hacking with minimal configuration on our part, or if we want to really go for broke we can slap some new firmware on the device and really build out some additional functionality.
 Now let’s tie this together. After an attacker has found an unsecured device, pulled its banner and found the default login credentials needed to access it, all they have to do is install a packet sniffer (or really any kind of malware they wanted) and they can begin to eavesdrop on any information that passes through that gateway. Or worse.
Now let’s tie this together. After an attacker has found an unsecured device, pulled its banner and found the default login credentials needed to access it, all they have to do is install a packet sniffer (or really any kind of malware they wanted) and they can begin to eavesdrop on any information that passes through that gateway. Or worse.
Hypothetically, using this information and these techniques, you could create your own botnet out of unsecured devices on your office network and then use them to overload your IT admin’s inbox with calendar invites to secure them all.
Trust me, IT guys love jokes like that.
HTTPS vs. MITM
We’ve just covered how a Man-in-the-Middle attack is executed, now let’s talk about what harm it can cause. In the example we just gave you – its most innocuous iteration – the data being passed through this gateway via HTTP is being read and any sensitive information like financial details or personal data can be harvested.
It only increases in severity from there. Remember, Man-in-the-Middle or MITM is a general term that refers to a means, not necessarily an end. Once a connection has been intercepted, you can do anything from simple spying to content injection.
The only surefire way to prevent a MITM is with SSL/TLS encryption and HTTPS, which encrypts data as it passes through each gateway on the way to its intended destination. When data is encrypted, it can still be intercepted but it’s essentially useless as it’s unreadable.
This is one of the biggest opportunity areas for the SSL/TLS industry because we are failing miserably in how we explain this. While it matters that the parties on either end of the connection trust one another, there’s a lot more surface to cover than just that. There are dozens of gateways between end points, and you cannot trust that each one of those is secure.
The stakes are much higher than we’re making them see. Because it’s trivially easy to access a lot of these gateways and set up a packet sniffer – or worse.
As always, leave any comments or questions below…
Recent Related News
Updated on April 29, 2021






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)







 (4 votes, average: 3.25 out of 5, rated)
(4 votes, average: 3.25 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown