Polymorphic Malware and Metamorphic Malware: What You Need to Know
Everything you need to know about this adaptive and prolific cyber threat.
Note: This article, which was originally published in 2019, has been updated to include related news & media resources.
Imagine a virus or malicious entity that can adapt and change over time. This shapeshifter camouflages itself by changing its “genetic makeup,” if you will — it’s code — to hide itself from those who seek to destroy it. Unfortunately, this scenario is not just something you have to dream up. While it may sound like something from a science fiction novel, polymorphic malware is all too real in the world of IT security. And, it also isn’t a new development — this mutating form of malware has actually been around since at least the ‘80s with the creation of malware named 1260.
Polymorphic Malware Is Everywhere
Polymorphic malware is more common than most people realize. In fact, recent research from Webroot showed that “more than 94% of all malicious executables we encounter are polymorphic.” Webroot acknowledges that there has been a dramatic increase in the prevalence of malware and potentially unwanted applications (PUAs). However, many people may not know that much about polymorphic malware — or, at least, don’t talk about it as much as they should.
We wish we could say that polymorphic malware is a one-of-a-kind thing, but it’s not. It has an even more unattractive and unpleasant relative who is harder to find, let alone evict. Metamorphic malware can evade more conventional detection methods than polymorphic malware because of its greater complexity and transformative capabilities. We’ll talk more about this later.
We know — the idea of having to deal with self-adapting malware in addition to all of the other cyber threats your company faces each day is almost enough to ruin your morning cup of coffee. Almost. However, no matter whether you work for a major corporation, a small to midsize business, or a government organization, mutating malware is a threat that needs to be addressed.
But what do we really know about this adaptive malware? In this article, we’ll discuss the similarities and differences of polymorphic malware vs metamorphic malware, examples of polymorphic malware, and speak with some industry experts about what you can do to protect your organization against it.
Let’s hash it out.
What is Polymorphic Malware?
Have you ever seen a chameleon change its colors to blend in with the background? One minute, it’s bright green; the next, it’s virtually invisible — just part of the dirt and rocks! This is a prime example of polymorphism. In cybersecurity, however, the term polymorphism has a less positive connotation. In this context, polymorphic refers to a malware’s ability to continually change and adapt its features to avoid detection. Polymorphic malware pairs a mutation engine with self-propagating code to continually change its “appearance,” and it uses encryption (or other methods) to hide its code.
As you’ve guessed, this ability to change is not so great for you when you are the intended target of a malware-based cyber attack. And, in addition to constantly evolving, polymorphic malware is also ever-increasing in number. Ana Tone, Team Leader Protection Labs for the security solutions provider Avira, says that:
“Polymorphic malware is an increasing prevalent threat in the last years, being easier for malware authors to take an existing malicious code and with less effort to change the object packaging through polymorphism and create new versions of the malware.”
How Does It Work?
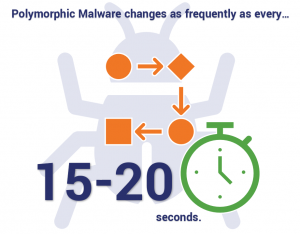
Polymorphic malware exists in many forms — Digital Guardian identifies some of these types of malware as viruses, bots, trojans, worms, and keyloggers. Regardless of the type, what makes this malware so effective is its complexity and speed. Polymorphic malware uses polymorphic code to changes rapidly — as frequently as every 15-20 seconds! Because many anti-malware vendors use traditional signature-based detection methods to detect and block malicious code, it means that by the time they identify the new signature, the malware has already evolved into something new. As a result, most security solutions simply can’t keep up with or aren’t able to detect these threats.
Polymorphic malware takes advantage of employee ignorance and unrecognized zero day vulnerabilities to wreak havoc. If an employee clicks on an attachment in a phishing email or provides information via a phishing website, they open your entire network, company, and sensitive data to attack. And when the threat is continually evolving, it’s harder to identify let alone eliminate.
Choosing not to educate your employees or patch known vulnerabilities leaves your company a sitting duck. Microsoft recently released a patch for a critical remote code execution vulnerability that existed in Remote Desktop Services in select Windows operating systems. This patch aims to prevent potential widespread attacks that could be exploited by adaptive malware and other threats. Imagine what hackers could have done if Microsoft didn’t recognize — or chose to ignore — this vulnerability… We may have been seeing news headlines in the coming months declaring widespread data breaches or ransomware attacks.
Polymorphic Malware vs Metamorphic Malware
We briefly touched on the conversation about polymorphic malware vs metamorphic malware a little bit earlier. People often think that polymorphic malware and metamorphic malware are the same — and on the surface, they are: They are adaptive and mutating software that hackers use to infiltrate and steal information while avoiding detection. And, both polymorphic and metamorphic malware aim to circumvent traditional anti-malware solutions. However, though their goals are the same, the way each type of malware reaches them differs.
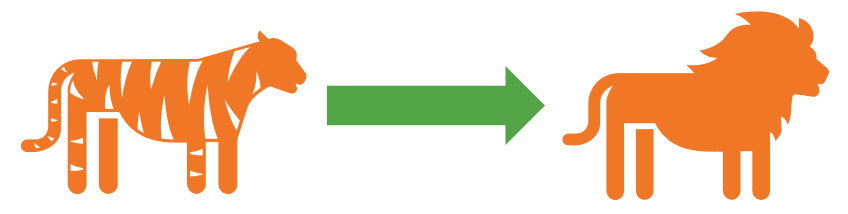
One of the things that differentiates metamorphic from polymorphic malware is that it completely re-writes its code so that each newly propagated version of itself no longer matches its previous iteration. This differs from polymorphic malware, which alters part of its code but retains one part of its code that remains the same (making it a bit easier to identify than metamorphic malware). To put it simply, polymorphic malware is a leopard that changes its spots; metamorphic malware is a tiger that becomes a lion.
According to a presentation from WetStone, a division of Allen Corporation, the metamorphic structure looks like this:
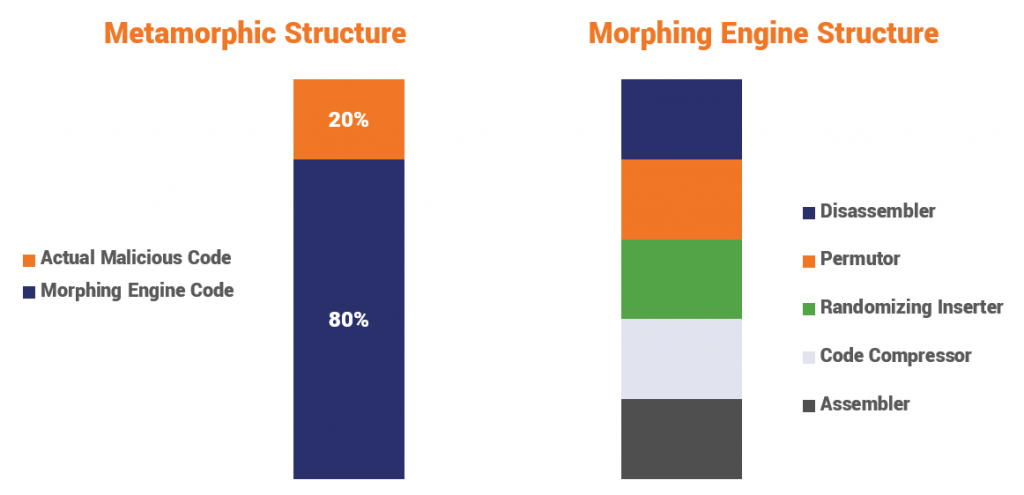
Although both types of malware are difficult to write — even a small error can result in significant issues that may prevent it from functioning — metamorphic malware is more difficult to develop than polymorphic malware because its creator may use multiple transformation techniques. These methods can include “register renaming, code permutation, code expansion, code shrinking and garbage code insertion.”
The Rise of Polymorphic and Metamorphic Malware
There’s no doubt that adaptive malware has been steadily increasing in recent years. Travis Smith, principal security researcher at Tripwire, says there are several reasons why these forms of malware are becoming more common:
“I believe the reason we’ve seen a rise in this type of malware is because it is proven to be able to bypass endpoint security solutions who are too heavily focused on signatures. While these are less common these days, there has been renewed interest in sharing threat intelligence in the security community over the last 5 years. The easiest method to share this information is via file hashes. If a piece of malware changes its file hash with each infection, the effectiveness of defenders sharing threat intelligence about that piece of malware will drop drastically.”
Marcus Chung, CEO of BoldCloud, an award-winning cybersecurity advisory firm, blames three main factors:
“1) ROI — The number of recent successful attacks or corporate data breaches have shown that targeted or “specialized malware threats” are more effective and thus provide a better ROI and revenue generator for these advanced malware developers.
2) Artificial Intelligence (AI) advancements – Access to advanced artificial intelligence technologies and machine learning tools is now widespread and the costs of developing or adapting these technologies to create malicious programs has drastically decreased.
3) Cat & Mouse Defenses – As the current generation of advanced security technologies have upped their game to detect many more types of polymorphic and other malware threats, the well-funded multi-billion dollar Malware industry developers have done the same to defend their revenue generating malware cash cows.”
Common Types of Polymorphic Malware and Polymorphic Viruses
Much like other forms of malware, polymorphic varieties can be divided into multiple families. Some of the most commonly seen types include:
- CryptoLocker — This insidious ransomware virus encrypts files on devices and shared networks. It gains access to systems through a variety of vectors, including downloads, file sharing sites, and email.
- CryptXXX — This form of ransomware used the Angler Exploit Kit (EK), once considered the leading EK, would encrypt files and steal passwords.
- VirLock — Thought to be the first polymorphic ransomware, this virus locked down victims’ screens while also infecting their existing files.
- WannaCry — This ransomware, which resembles the CryptXX trojan, is a cryptoworm that takes advantage of an EternalBlue exploit, an unpatched vulnerability on old Windows operating systems.
An Example of Polymorphic Malware at Work
Back in 2007, an infamous spam email known as Storm Worm was sent containing the subject line “230 dead as storm batters Europe.” This pernicious malware infection, which contained a backdoor trojan, wasn’t initially recognized because of its limited detectability. As soon as a user opened the email’s attachment, the malware deployed and executed the trojan to turn their device into a bot. What made this malware particularly difficult to detect was the fact that the worm’s file binder would alter itself every 10 to 30 minutes. The alterations mean that the malware would undergo multiple permutations before any security experts would have a chance to identify the first version of the malware.

How to Defend Against Polymorphic and Metamorphic Malware
Simply put, the fight against mutating malware is a race between hackers and cybersecurity experts. Each side is doing their best to stay ahead of the other — the first by trying to come up with new and more inventive (and invasive) threats; the other by trying to create new detection capabilities and response methods. It’s a good ol’ fashion arms race in the cyber world. The good news, however, is that these threats are not unstoppable. We’ll now turn to industry experts to get some ideas about what can be done to identify and mitigate the damage caused by polymorphic malware.
Brian Gill, co-founder of Gillware, a data recovery and digital forensics company, says there are several things you can do to protect your business, devices, and information technology against polymorphic malware:
“In order to be the most effective, you should take a multi-layer approach which ideally would combine people, processes, and technology. Begin by making sure any software you use is up to date. A lot of software creators provide security updates for when vulnerabilities are discovered. If you’re using outdated software, you run the risk of opening the door for malware threats. You should also never click on suspicious links or attachments. Recognizing how to identify these malicious properties should be part of employee training and can go a long way in bolstering your defenses. Additionally, passwords should be regularly updated using multi-factor authentication when possible. Lastly, take advantage of behavior-based detection tools. These tools are more advanced than your traditional antivirus solutions. Things like endpoint detection and response can actually narrow down threats in real time, prior to your information being compromised.”
Many of these points are supported by Tone, who reiterates the importance of combining technologies that provide real-time protections and having processes in place to ensure that all software applications are kept up to date.
Polymorphic malware poses the biggest threat to businesses who rely solely on signature-based solutions as their main line of defense. To address this, Smith recommends the following:
“By following basic and foundational controls, most malware will be stopped before it has a chance to execute. Businesses should focus less on signatures or individual tools, instead defenders should focus their energy on the tactics, techniques, and procedures adversaries will use against them. Using a model such as MITRE’s ATT&CK is a great starting point for businesses who are concerned with increasing their security posture.”
What else can you do to detect these threats?
- Use anti spam and anti phishing email protections that help to identify and quarantine malicious emails.
- Implement heuristic analysis mechanisms that scan for certain shared components of different threats.
- Use emulation and virtualization tools that better understand a file’s behavior in a virtual environment.
- Tighten employee access control methods to sensitive and essential systems.
Related: Secure Your Website with a Comodo SSL Certificate.
Final thoughts
Keeping your customer and company data secure from all threats should be a major priority. Although accomplishing this with a continually changing enemy can be a challenging, as we’ve discussed, it’s not impossible.
To rehash, there are a few things you can do to increase detection of polymorphic malware and prevent it from gaining access to your system:
- Implement layers of defense in the form of firewalls, antivirus and anti-malware solutions.
- Provide comprehensive employee education, training, and testing to prevent employees from engaging with malicious emails and phishing emails.
- Use machine-learning and behavior-based detection methods rather than traditional signature-based techniques.
- Having processes in place to keep all of your protection and detection applications and systems patched and up to date.
- Use good password management practices; require employees to change their passwords regularly.
- Limit employee access to minimize damage if an account becomes compromised.
What are your thoughts? If you have any questions or comments, be sure to share them below.
Recent Related News
Updated on March 25, 2021





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown