Sectigo acquires Icon Labs, becomes first CA to offer End-to-End IoT Security Solution
Sectigo’s new IoT platform now seamlessly hardens devices with embedded tools and a secure boot
Sectigo (formerly Comodo CA) has acquired Icon Labs, a security company specializing in IoT security solutions. The acquisition was announced yesterday via press release and on its blog.
The move is consistent with a larger trend – Certificate Authorities beginning to provide PKI-based IoT security solutions to manufacturers. And quite frankly, this is a much-needed reaction to the glaring lack of security that has traditionally plagued IoT devices.
Perhaps unsurprisingly in our haste to connect every conceivable device to the internet – security took a back seat. And now it turns out that all those unsecured household and industrial devices are a perfect addition to botnets and can be harnessed to do evil. Or, just made to mine cryptocurrency.
Regardless, IoT security has never been more important than it is in 2019. So, today we’re going to talk about what exactly it is that PKI is securing with regard to the IoT and we’ll discuss why Sectigo’s acquisition of Icon Labs bodes well for the future
Let’s hash it out.
Sectigo Expands its IoT Security Platform
For customers of both Sectigo and Icon Labs this move will add a slew of additional security features to the services you were already enjoying. Icon Labs customers will now have access to “purpose-built IoT issuance” from the world’s leading CA. Sectigo IoT customers will now be able to further harden their devices with embedded tools and a multi-stage secure boot.
“Icon Labs has been growing and addressing this challenge by securing the device market for more than two decades. For the first time, embedded security technology is combined with device authentication and identity management to provide customers with a complete IoT security platform that solves many of the challenges presented by the rising number of threats,” said Bill Holtz, CEO, Sectigo.
The acquisition makes Sectigo the first CA to offer end-to-end security for IoT devices – from manufacture through the end of its lifecycle. Now customers will be able to secure the device itself as opposed to just securing network perimeters.
The Sectigo IoT Security Platform now boasts:
- Multi-Stage Secure Boot – Ensures software integrity from the moment the device is powered on. Developers can now use Code Signing certificates to digitally sign boot loaders, microkernels, operating systems, supplication code and data to ensure software integrity. Secure audit logs are also kept for boot processing and other related services.
- Embedded Firewall – Filters provide deep packet inspection capabilities for industrial protocols.
- TPM Integration – Trusted Platform Modules are used for secure certificate and key storage.
- Secure Remote Updates and Alerts – Firmware and software updates are further secured, offering authentication, integrity checks and the ability to issue alerts in the event that an update fails.
- On-premise CA – In addition to a Sectigo cloud-based CA, you can now leverage and on-site CA to perform critical functions like issuance, registration renewals/revocations.
“By joining Sectigo, Icon Labs is contributing to a powerful advancement in connected device security. We are securing IoT devices and the convergence of traditional IT systems and Operational Technology (OT); that is, the hardware and software that detects or causes changes in physical processes through direct monitoring and/or control of physical devices,” said Alan Grau, Founder of Icon Labs.
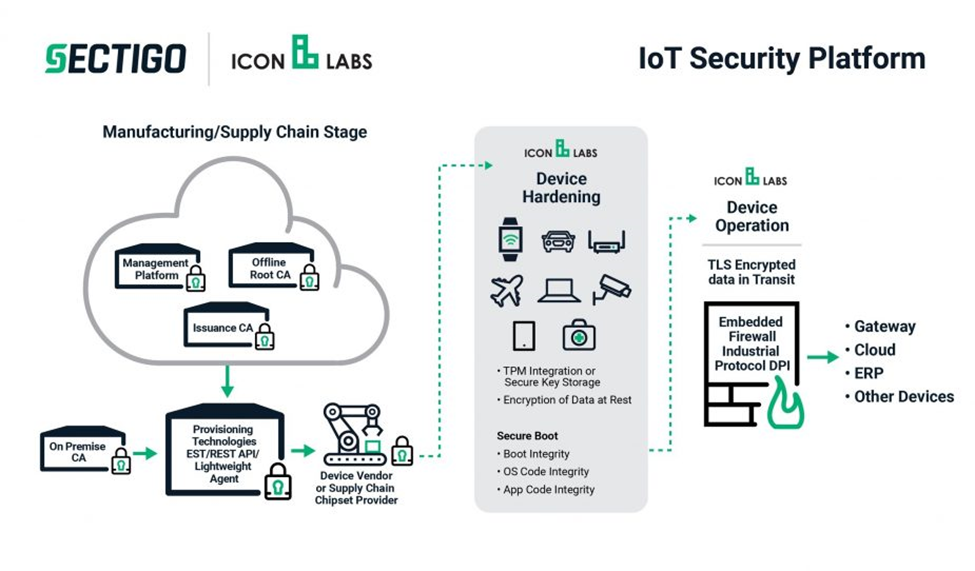
What exactly are we securing with IoT devices?
Sectigo’s IoT Security platform is now capable of securing just about every attack vector facing IoT devices, from attacks that occur while the device is booting, to attacks that may occur while the device is connected to a network, to attacks that occur during the update cycle.
“Icon Labs adds an important set of products and core competencies to the Sectigo technology suite. Sectigo will continue to provide existing Icon Labs customers with the full set of offerings they’re accustomed to. Additionally, we are proud to make the acquired technology products available to the full set of Sectigo enterprise customers for their device security needs,” writes Sectigo Senior Fellow, Tim Callan.
Icon Labs’ ability to harden devices by securing all stages of the boot process and embedding tools like firewalls shuts down attack vectors that Sectigo previously couldn’t address. And vice versa.
So, how does PKI better secure the IoT?
For starters, it provides a much-needed mechanism for authentication. We rarely talk about SSL/TLS client certificates, the ones that individual users can use to authenticate themselves. That’s because from a retail perspective there’s not much of a use for client certificates. It’s just an added layer of complexity.
But at the corporate level, especially with organizations that allow employees to bring their own devices, it’s important to be able to authenticate the device and possibly even its is user. The business sector isn’t really the one pushing the IoT numbers up to an estimated 75-billion by 2025 though. That’s largely on account of the industrial sector where OEMs or Original Equipment Manufacturers make connected components that go into larger systems and machines. A mistake in the business sector could lead to a breach or some kind of financial harm but there are rarely physical stakes. Not so with industrial components. Over the past few years we’ve seen a couple of attempts to attack a Saudi chemical company, which would have resulted in loss of life were it not for a failsafe that shut down the whole plant. Power grids in the Ukraine have been attacked. And then, of course, there was the Stuxnet virus that overloaded Iranian nuclear centrifuges.
IoT devices have become a major target and authentication is a great way to help avoid compromise.
But authentication is far from the only thing PKI can do to secure the IoT. That’s because client and server certificates aren’t the only kind of PKI certificate. You can also use Code Signing certificates to better secure updates and patches. By digitally signing your updates before pushing them to the connected devices they’re intended for, it allows the device to verify the integrity and legitimacy of the code. This prevents anyone from pushing an unsanctioned update, even if they manage to compromise the update server.
Finally, there’s the simple issue of encrypting any data that’s transmitted via TLS. In many contexts the information being shared by this device is highly sensitive, so transmitting it insecurely invites disaster. Ensuring that every device has a certificate and can connect securely effectively encrypts all data while its in transit and prevents Man-in-the-Middle attacks and just eavesdropping, in general.
And, as we covered, with Icon Labs’ technology now undergirding its IoT Security Platform, Sectigo can further secure connected devices with embedded tools and improved boot security. Toss in the inclusion of its recent Zero-Touch deployment feature and Sectigo is really starting 2019 off with a bang.
As always, leave any comments or questions below…

Sectigo IoT Security
The world’s first end-to-end security for the IoT.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown