Twitter will deprecate support for TLS 1.0, TLS 1.1 on July 15
All Twitter connections will require TLS 1.2 starting Monday
On Monday, July 15, Twitter will drive another nail into the coffin of TLS 1.0 and TLS 1.1. The social media giant that serves as the world’s comments section will officially require all connections to use TLS 1.2 or higher starting next week.
This move is part of a larger movement to deprecate the outdate versions of the TLS protocol. There are legitimate security concerns associated with TLS 1.0 and TLS 1.1, which is why just about every major player in the tech industry already has – or have announced plans to – deprecate support for them.
So, today we’re going to keep it light and talk about Twitter removing support for TLS 1.0 and TLS 1.1 next week, why TLS 1.0 and TLS 1.1 are on their way out and how many websites are still supporting them.
Let’s hash it out.
Twitter De-platforms TLS 1.0 and TLS 1.1
While Twitter actually announced the upcoming removal of support for TLS 1.0 and TLS 1.1 a month ago on June 11, it kind of flew under the radar until Twitter suffered an outage last night.
As service returned, Twitter was a bit opaque about its cause:
The outage was due to an internal configuration change, which we’re now fixing. Some people may be able to access Twitter again and we’re working to make sure Twitter is available to everyone as quickly as possible.
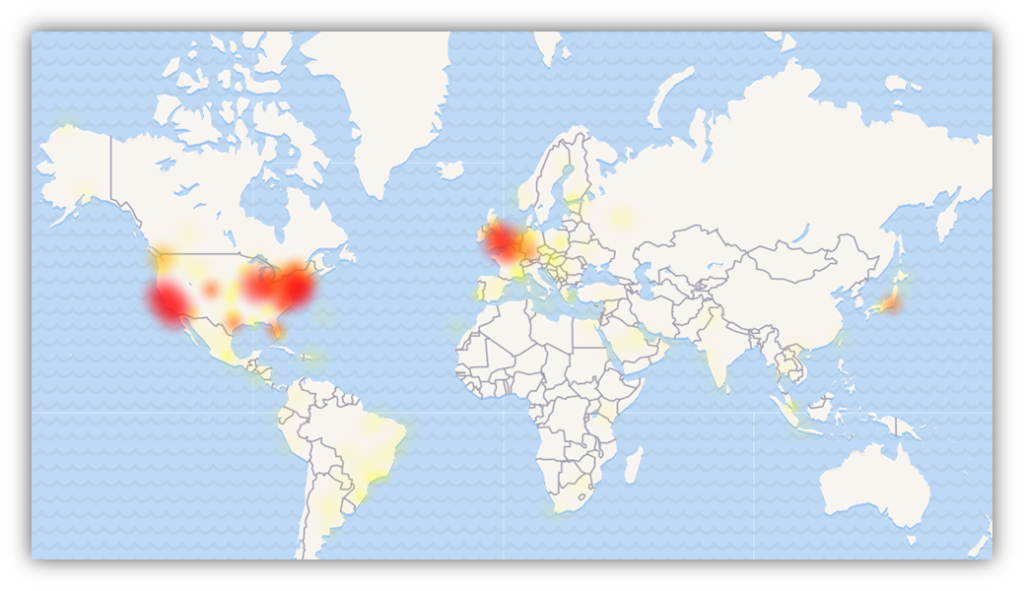
This is totally conjecture on my part, but it’s very possible that the configuration issues may stem from Twitter’s upcoming removal of support for the older TLS protocol versions. Again, that’s little more than an educated guess, but it would line up. We’ll have a better idea if Twitter mysterious pushes back its deprecation date.
Either way, plans to require TLS 1.2 for all connections are already well underway.
Beginning July 25th 2019, all connections to the Twitter API (and all other Twitter domains) will require TLS 1.2. This change will affect all formats and tiers of the API (REST, streaming, and webhooks; standard, premium, enterprise, and Ads and Media APIs), as well as the wider Twitter platform.
This is going to have its biggest impact on APIs that connect to Twitter. If you’ve got a share button or a Twitter feed on your website or blog – that means this could affect you. Generally, a lot of those kinds of web apps and plugins are developed by a third-party – one that hopefully is on top of this – but if you’ve spun up your own are have a lousy provider you might be in for a rough Monday morning.
We recommend reviewing ALL code that connects to the Twitter API, and validating that it uses libraries that support modern, secure encryption standards. Specifically, you must ensure that your code correctly negotiates a TLS 1.2 connection to api.twitter.com and associated domains.
So, if you weren’t already aware – this is your notice: Make sure any connections you’re making with Twitter or its API support TLS 1.2 or they’re going to break on July 15, 2019.
Why is TLS 1.0 and TLS 1.1 being deprecated?

For starters, they are ancient in internet years. SSL (Secure Sockets Layer) 1.0 was the first iteration of SSL/TLS, it was developed by Netscape in 1995 and was never released because of security flaws. 2.0 was released with security flaws that almost immediately necessitated the development of SSL 3.0 in 1996.
TLS was introduced in 1999 as the successor of SSL. SSL 2.0 and SSL 3.0 were officially deprecated in 2011 and 2015 respectively, though and uncomfortable number of websites still support them to this day.
There are some differences between SSL and TLS on a technical level, probably the biggest – at least initially – being the way connections are initiated, either by port or by protocol. But each successive version has made technical improvements over its predecessors so you could make the argument that TLS 1.3 and TLS 1.2 are far more different from one another than SSL 3.0 and TLS 1.0 were. We’re really splitting hairs here though.
TLS 1.0 was released in ’99. TLS 1.1 came along in 2006. 1.1 is actually kind of the redheaded stepchild of the family, it wasn’t as widely adopted – largely owing to the fact TLS 1.2 came two years later in 2008. Last year, after nearly 30 drafts, the IETF finally finished defining TLS 1.3 as RFC 8446.
Here’s how many websites still support the various protocols, per WatchGuard:
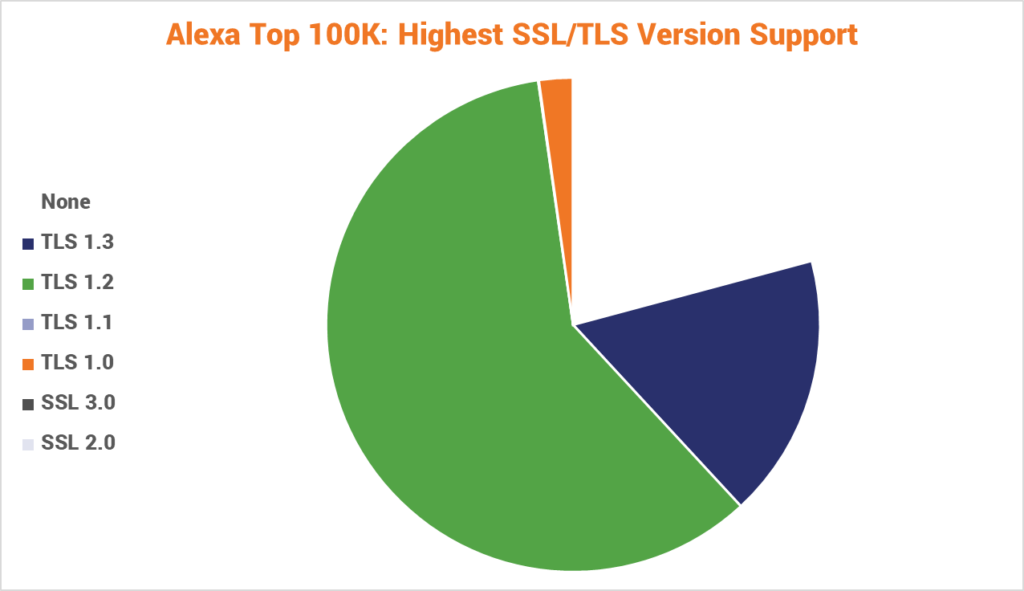
| None | TLS 1.3 | TLS 1.2 | TLS 1.1 | TLS 1.0 | SSL 3.0 | SSL 2.0 |
| 20,911 | 17,345 | 59,830 | 53 | 2,221 | 5 | 0 |
Now let’s talk about what specifically makes continuing to support TLS 1.0 and TLS 1.1 a threat: vulnerabilities with bad acronyms. POODLE. DROWN. BEAST. SSL Stripping attacks. Downgrade Attacks.
Now, if we’re being honest a lot of these exploits are actually fairly complicated to pull off. A lot of times this industry does a poor job distinguishing between an imminent threat and theoretical one. And this industry in particular, which is so obsessed with purity, is especially guilty of that.
But there is a non-zero chance that these vulnerabilities could be exploited.
And the bigger issue websites and applications are about to run into is a lack of support from critical industry players. In a rather unprecedented move, Apple, Microsoft, Mozilla and Google – that four major browser makers – jointly announced plans to deprecate support for TLS 1.0 and TLS 1.1 in January 2020. PCI DSS has already mandated the deprecation of TLS 1.0 and strongly advises deprecating support for TLS 1.1, too.
As more and more industry leaders announce plans to stop supporting everything but TLS 1.2 and TLS 1.3 – it’s going to be harder and harder to justify continuing to support the older versions.
What does this mean for my SSL certificate?
Nothing. SSL/TLS certificates are not contingent upon protocol versions and vice versa. When a new version of the protocol becomes available – or is deprecated – that’s a server-side configuration task. You may need to update certificates if changes to key size requirements or digital signatures are needed, but in general you can upgrade to TLS 1.3 or remove support for older TLS versions without having to update or adjust your certificate usage.
The bigger issue, as stated earlier, will be making server updates and tweaks to the code for any program that uses the Twitter API.
The average Twitter user likely won’t notice any difference unless they’re on an older device or running an outdated version of their OS or browser. This is going to be a change that makes an impact at the organizational level.
So… heads up.
As always, leave any comments or questions below…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown