What Is a Hardware Security Module? HSMs Explained
Hardware security modules are specialized computing devices designed to securely store and use cryptographic keys. Let’s break down what HSMs are, how they work, and why they’re so important to public key infrastructure
Demand for hardware security modules (HSMs) is booming. Data from Entrust’s 2021 Global Encryption Trends Study shows that HSM usage has been steadily increasing over the last eight years, increasing from 26% in fiscal year 2012 to 49% in 2020. According to data from 360 Market Updates, the HSM market is expected to reach $2.75 billion by the end of 2026.
What is an HSM and what does it do? Why are so many companies using HSMs? And what are the practical uses for HSMs in enterprise environments?
Let’s hash it out.
What Is a Hardware Security Module (HSM)? An HSM Definition & Explanation
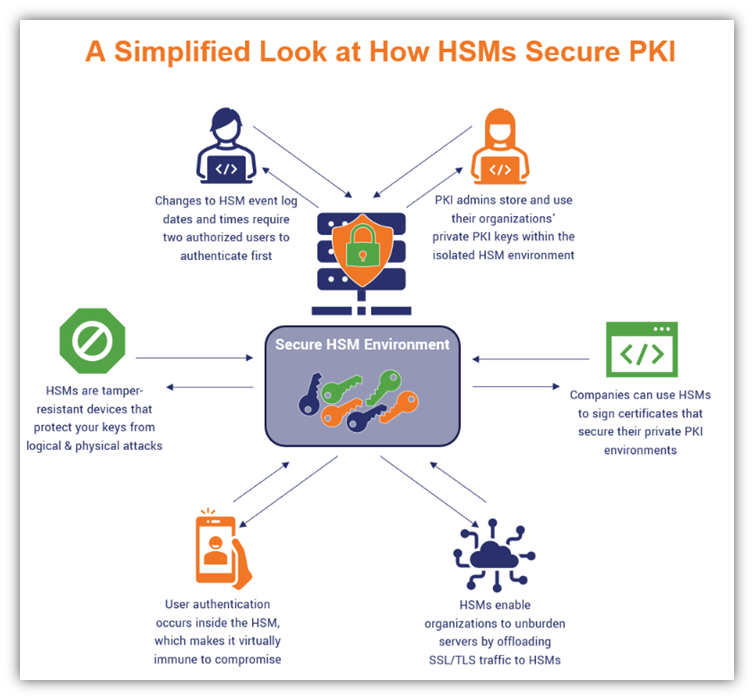
Encrypted data isn’t secure if the keys you use to encrypt it are exposed — this is where HSMs can save the day. Hardware security modules (HSMs) are tamper- and intrusion-resistant hardware components that organizations use to protect and store their cryptographic keys while still making them available for use by authorized users. Their purpose is to control access and limit risk to your company’s sensitive private keys.
HSMs enable your employees to use of your organization’s private keys without needing direct access to them. Basically, your software (for example, hosted on a web server) can execute cryptographic functions and authentication without loading a copy of your private key into memory on your web server (where it could be vulnerable to attack). The cryptographic functions are all done within the confines of an HSM’s secure environment. Performing these operations within this secure little bubble keeps your sensitive data from becoming compromised by keeping the private keys hidden away in a secure location.
To better understand this concept, think of an HSM like a vending machine. A vending machine stores drinks and food items within an isolated internal environment. It’s designed to accept user inputs (i.e., your item selections) and generate outputs (i.e., pop out a tasty snack), and you can’t access the inside of the vending machine or alter its functions.
Similarly, an HSM accepts user inputs and generates outputs (such as signed certificates or software) without users (or applications) seeing, accessing, or altering your cryptographic keys. That’s because its functions are executed within the confines of its secure environment, and no key can be wholly exported, extracted or removed from an HSM in a readable format. So, like a vending machine, you can use it to get your desired output but you can’t see or access the internal workings of the device and all of its individual components that made it possible.
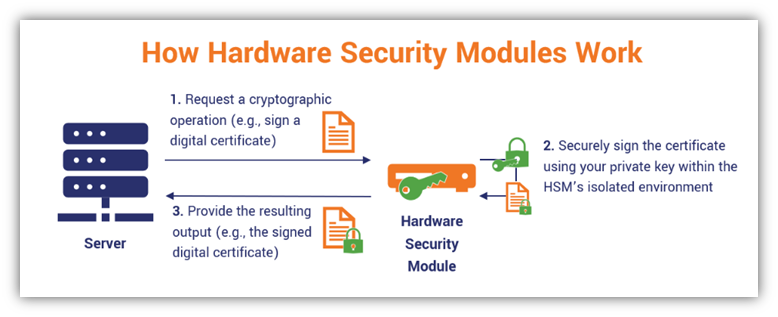
Here’s a quick overview of how hardware security modules work:
How Using an HSM Can Help Your Business
You may be wondering why you need to use a hardware security module at all. I mean, why should you go through the hassle and cost of setting up an HSM when you can simply use your web server’s built-in functionalities?
Well, for one thing, an HSM provides significantly more secure key storage than what you’d get from using a traditional web server. When companies use their web servers to run many applications, this can result in vulnerabilities that cybercriminals can exploit. HSMs are devices with limited usages and attack vectors. This is why:
- Public certificate authorities and registration authorities use these devices to create, store and manage their sensitive keypairs. (Note: They generally store the root CA offline to keep it as secure as possible.)
- Companies with private PKIs use these devices to use and store the keys they use to sign their PKI certificates, software code and documents.
Using an HSM helps you secure your private code signing keys and avoid exposure issues like what HashiCorp faced earlier this year. On April 22, HashiCorp informed customers that the GPG private key they use to sign official product downloads and updates was exposed as the result of a third-party (Codecov) security incident.
Basically, the crux of the situation is that an unauthorized user exploited a vulnerability that gave them the ability to export sensitive data from Codecov’s continuous integration (CI) environments. HashiCorp’s CI environment — which housed the company’s GPG private key and other “sensitive secrets” among — were among those exposed CI environments. If HashiCorp stored their key in a secure HSM instead of the CI, then it wouldn’t have been exposed.
How HSMs Improve IT and Data Security
There are also many other purposes and uses that HSMs serve in terms of PKI and general cybersecurity. You can use an HSM to:
- Store and protect all of your cryptographic keys throughout their lifecycles. HSMs are generally standalone network-connected devices that are separate from your servers. This helps to keep your keys secure through all lifecycle stages — from generation all the way through their eventual destruction or revocation.
- Generate the most cryptographically strong keys for your PKI. HSMs have built-in true random number generators (TRNGs) that provide randomness and unpredictability.
- Protect the security of your keys through “zeroization.” Because HSMs are tamper-resistant devices (both for logical and physical attacks), they’re built to erase or destroy all stored cryptographic data to prevent compromise.
- Secure your organization’s cryptographic operations and services. Restricting these functions (such as signing PKI certificates, applications and documents) to occur only within the secure, stand-alone environment of the HSM helps to prevent key exposure.
- Improve server performance via load balancing. HSM devices are stripped-down, standalone devices that can take on the responsibility of performing operations that otherwise bog down your servers. Some HSMs are equipped to act as web traffic accelerators by offloading cryptographic operations.
- Protect your keys from insecure extractions that can lead to compromise. “Wrap” or encrypt your encryption keys to prevent them from being extracted in plaintext format.
- Secure the keys for your development, testing and production environments. An HSM protects the private PKI keys used by the software and systems relating to your internal production and testing environments so these systems can use them without needing direct access to them. (Note: use a separate HSM for each environment to avoid data security risks — never use the same HSM across multiple environments).
- Ensure compliance with data security regulations and simplify audit processes. HSMs are typically validated hardware components that ensure compliance because they meet specific industry standards. They also provide tamper-resistant logs that inform you about:
- what cryptographic operations they’re used to perform,
- when these operations were carried out, and
- who was responsible for authorizing those operations.
Here’s a breakdown of the top 10 HSM use cases in 2021, according to data from Entrust and the Ponemon Institute:

Hardware Security Module Options: Physical Devices vs Cloud-Based HSMs
Having options for secure cryptographic storage is important for all businesses, particularly as their needs evolve with the growth of their operations. The good news is that HSMs vary in terms of both their physical sizes and applications. Some HSMs are small plug-in cards or USB devices while others are large external devices and appliances that companies store on premises within secure locations.
Hardware security modules can be very cost-prohibitive for many businesses. A 2018 article in SecurityToday.com says that the cost of deploying a single HSM can range upwards of $40,000 — and that price doesn’t include other related costs such as additional hardware, support, and maintenance. So, doing everything yourself may not be a viable option.
But just because your company can’t afford to buy one or more of these devices outright doesn’t mean that you can’t still enjoy the advantages of using HSMs. Some vendors (such as Thales and Amazon Web Services) now offer cloud-based HSM products and services.
There are a few different options when it comes to using cloud HSMs:
- Rent a dedicated physical HSM appliance that gets stored in your off-site data center.
- Pay for access to the functionalities of an HSM vendor’s device or appliance.
- Pay for access to a virtual environment within a vendor’s shared HSM.
The idea here is rather than having to buy an expensive physical appliance that you need to protect on site, you can instead “rent” a dedicated physical appliance or pay for access to the functionalities of one controlled by a third-party vendor for less cost.
As you can imagine, there are advantages and disadvantages to each approach, but you’re ultimately the one who needs to decide which approach is best for your organization or business. Just be sure to carefully read the service level agreement (SLA) to ensure they’re what you need.
Of course, there is a way you can have your cake and eat it, too — meaning that you can use an HSM without having to buy or rent one. This is possible when you partner with a managed PKI (mPKI) service provider. For example, DigiCert is an mPKI provider whose platform was built using an HSM. When you use their platform, you can capitalize on their secure HSM on the backend without having to buy or rent this expensive hardware.
Hardware Security Modules vs Trusted Platform Modules: Are HSMs & TPMs the Same?
If you think that an HSM sounds a lot like a trusted platform module, or TPM, there are a couple good reasons.
- Both HSMs and TPMS are tamper-resistant hardware components, and
- Both devices are examples of hardware roots of trust that protect the services and cryptographic tools that global consumers and businesses use daily.
But are these two devices the same? No. TPMs are device-specific components within individual devices whereas HSMs are external devices with wider applications at handling operations relating to many or all devices and applications across an organization’s network.
TPMs are basically computer chips that physically attach to individual devices’ motherboards to secure their PKI keys while keeping them separate from the devices’ CPU memory. They help to ensure device integrity and provide an isolated environment for the device’s cryptographic operations.
HSMs, on the other hand, are hardware devices that aren’t limited to individual machines. They’re intended for use at-scale by applications and servers across your organization.
To learn more about what trusted platform modules are and how they work, be sure to check out our other article relating to that specific topic.
Who Uses HSMs and Why Are They Important to Your Organization’s Digital Security?
The National Institute of Standards and Technology (NIST) Special Publication “Recommendation for Key Management: Part 2 — Best Practices for Key Management Organizations” (SP-800-57 part 2, rev 1) describes hardware security modules as critical key management components. They’re part of the physical infrastructure that makes secure key storage and cryptographic operations possible.
HSMS are used by organizations across virtually all industries, some of which include:
- Certificate authorities (public and private CAs),
- Government and public sector organizations,
- Cloud service providers and vendors,
- Banks, credit card companies and other financial institutions,
- Blockchain platforms and entities,
- Automotive manufacturers,
- Entertainment service providers, and
- IoT device developers and manufacturers.
That’s quite a spread in terms of industries, am I right? This variation is, in part, due to the fact that hardware security modules come in two main varieties (which we’ll explore momentarily) for organizations’ various usages.
What HSMs Do: HSM Use Cases & Applications Within Organizational Environments
Hardware security modules are typically used for securely storing cryptographic keys and payment-related information. However, their uses span the gamut in terms of current and future applications. Here are some of the ways you’ll currently find HSMs in use globally:
- Securing digital identities for passport-related systems,
- Protecting root CA keys (for public and private CAs),
- Verifying user identity information,
- Enabling cryptographic operations at scale within organizational environments.
- Securing root keys in blockchain signatures.
- Creating strong credentials for connected technologies across various industries (automobiles, manufacturing, medical devices, and gaming consoles).
- Protecting digital watermark properties for streaming services.
The Two Types of Hardware Security Modules: General Purpose and Payment
When we talk about HSMs here at Hashed Out, we’re typically talking about general purpose HSMs. However, it’s important to note that this isn’t the only category of HSMs — Thales Group describes a second category of HSM devices as “Payment HSMs.” Now that we know what HSMs are and some of their applications, let’s explore the two types of HSMs a bit more in depth.
General Purpose Hardware Security Modules
General purpose HSMs are those that all types of organizations use as part of their organization’s overall cyber security. These are like the devices we described in the “What Is a Hardware Security Module (HSM)?” section near the beginning of the article.
These devices typically use vendor-neutral APIs to facilitate communication and cryptographic services for your applications. That’s because general purpose HSMs rely on the public key cryptography standards #11 (PKCS#11), which are a group of standards that outline how applications and HSMs can interact and communicate for cryptographic operations. (This enabled interoperability between applications and devices from various manufacturers.)
They also must meet geographic or industry security validation and trustworthiness requirements and standards such as:
- FIPS 140-2 validation requirements. U.S. federal agencies must use devices that meet FIPS 140-2 (ideally level 3 as a minimum) validation requirements.
- Common Criteria (CC) for Information Technology Security Evaluation. The Common Criteria are among the most widely recognized standards for IT security products worldwide.
- eIDAS Protection Profile EN 419 221-5. These regulation trustworthiness requirements are based on Common Criteria and are required for many government entities throughout the European Union.
- HIPAA Security Rule. The Technical Safeguards include encryption as an “addressable” implementation specification for organizations that handle covered data. Although HSMs aren’t specifically mentioned, they’re the most secure way to protect the private keys that encryption and decryption processes require.
Payment Hardware Security Modules
As you can probably guess from the name, this second category of HSMs focus on the payment industry and are more specialized. Like general purpose HSMs, payment HSMs are also tamper-resistant hardware components that enable businesses to store and protecting keys and data. However, these keys relate to financial applications and transactions and do jobs such as storing customer PINs
Payment HSMs are designed to meet many different standards and use various interfaces. They also require different protocols and certifications from their general purpose HSM counterparts, some of which include the Payment Card Industry PTS Hardware Security Module (PCI PTS HSM) Modular Security Requirements and FIPS 140-2 validation requirements (level 3 or higher), and various regional security requirements.
For the purpose of this article, we’re primarily focusing on general purpose HSM functionalities, so we’re not going to get into the nitty-gritty of payment HSMs here. However, we’ve put together a quick side-by-side comparison table to help you better understand the differences between the two types of hardware security modules:
| Type of HSM | General Purpose HSMs | Payment HSMs |
| Industries | Government and Public Sector, Cyber Security, Entertainment Services, | Banking and Financial Institutions |
| HSM Formats/Types | Dedicated physical hardware devices and appliances, or cloud-based access to a vendors’ physical devices or virtual functionalities | Dedicated physical hardware devices and appliances |
| Compliance Requirements and Standards (Depending on the Specific Device) | FIPS 140-2 (level 3 or higher), Common Criteria (ISO/IEC 15408), and EN 419 221-5 | PCI HSM, FIPS 140-2 (level 3 or higher), ANSI, ICO and various regional and payment card industry vendors’ specific security requirements |
| API Support Specifications | PKCS#11, CAPI/CNG, JCA/JCE | Non-standardized APIs |
5 Practicalities to Keep In Mind When Using HSMs to Secure Your PKI
We touched on some of the uses of general purpose HSMs within organizational environments. Now, let’s explore some practical applications.
1. Incorporate HSMs Into Your Private PKI on Day One
A hardware security module provides the foundational security and trust your PKI needs. This is why it should be part of your organization’s public key infrastructure from the get-go and not just added later on. (Technically, you can add an HSM to your private PKI architecture later — however, it does require a lot of extra work and configurations that you can avoid by making the device part of your initial PKI.)
- Storing your keys in software on your server leaves those sensitive assets at risk of exposure and compromise.
- Using an HSM at the beginning creates a secure record that makes your PKI auditable.
- Incorporating PKI from the start gives your private CA scalability that benefits your growing organization.
2. Make Your Authentication Artifacts and Processes More Secure
HSMs allow you to store your organization’s cryptographic keys and create the PKI certificates that are necessary to enable user, device and software authentication. Furthermore, the authentication processes themselves can occur within the HSM’s internal environment. This keeps the keys secure by not requiring them to be accessed directly, copied or moved.
3. Improve Server Performance Through Cryptographic Offloading
You can use your hardware security module for cryptographic offloading (such as for SSL/TLS). The purpose of SSL/TLS offloading is to ease the burden on your web server that stems from encrypting and decrypting traffic by shifting those functions to another device (such as a load balancer).
If you opt to store your private keys in an HSM instead of your web server, you can shift the cryptographic functions relating to that traffic to your HSM.
4. Encrypt Extractable Encryption Keys for Greater Security
The Open Web Application Security Project’s (OWASP) Key Management Cheat Sheet specifies that if you choose to secure your cryptographic keys offline or in devices such as HSMs, you should encrypt them using key encryption keys, or KEKs.
5. Use a MPKI Solution or Service That Has Its Own HSM
If you want to avoid the costs and responsibilities associated with in-house management of an HSM for your private PKI, then choose an mPKI provider whose platform was built using an HSM. Doing this enables your authorized users to use your organization’s HSM-stored keys remotely without accessing or touching the keys. For example, users can sign EV code signing certificates without the necessary risk of keeping individual tokens on hand that could get lost or stolen.
Final Thoughts: For HSMs to Be Effective, You Have to Keep Them Secure
While HSMs are great security tools, they require you to take steps to keep them (and the keys the contain) secure. This includes physical security measures as well as digital access.
The first aspect entails keeping your hardware security modules stored in secure physical locations (such as a secure data center or server room). Your HSM should never be stored in an open or insecure location where unauthorized individuals can access it.
HSMs require strong access controls, policies and processes to keep your cryptographic keys secure and ensure that only authorized users can use it. This way, no unauthorized employees or nefarious external parties (i.e., cybercriminals) can use your cryptographic keys against you to digitally sign data, applications, or certificates.
Also be sure to monitor your HSM event logs. This way, you know who tries to access or use your cryptographic keys and how they used them.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown