A brief overview of PKI (Private Key Infrastructure) and why your certificate is trusted.
One of the most common questions we field is in relation to the “Chain of Trust.” If you’ve ever had any questions about roots, intermediates or how SSL certificates are chained, you’re discussing the Chain of Trust. This article will serve to explain how certificate chaining works and how a browser determines that your certificate can be trusted.
What is the Chain of Trust?
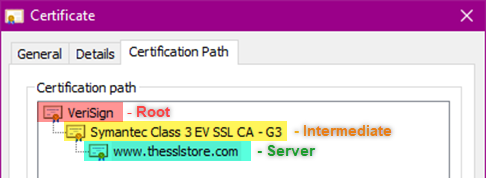
The Chain of Trust refers to your SSL certificate and how it is linked back to a trusted Certificate Authority. In order for an SSL certificate to be trusted it has to be traceable back to the trust root it was signed off of, meaning all certificates in the chain – server, intermediate, and root, need to be properly trusted. There are 3 parts to the chain of trust:
Root Certificate – A root certificate is a digital certificate that belongs to the issuing Certificate Authority. It comes pre-downloaded in most browsers and is stored in what is called a “trust store.” The root certificates are closely guarded by the Certificate Authorities.
Intermediate Certificate – Intermediate certificates branch off of root certificates like branches off of trees. They act as middle-men between the protected root certificates and the server certificates issued out to the public. There will always be at least one intermediate certificate in a chain, but there can be more than one.
Server Certificate – The server certificate is the one issued to the specific domain the user is needing coverage for,
How does the Chain of Trust work?
When you install your SSL certificate, you’ll also be sent an intermediate root certificate or bundle. When a browser downloads your website’s SSL certificate upon arriving at your homepage, it begins chaining that certificate back to its root. It will begin by following the chain to the intermediate that has been installed, from there it continues to tracing backwards until it arrives at a trusted root certificate. If the certificate is valid and can be chained back to a trusted root, it will be trusted. If it can’t be chained back to a trusted root, the browser will issue a warning about the certificate.
Troubleshooting Chain of Trust Issues
You will occasionally receive errors regarding your certificate’s Chain of Trust if something has been configured incorrectly. Here are some things to consider if you receive an error relating to your trust chain.
- Was your SSL certificate issued by a trusted CA? If not, your SSL certificate will not be trusted by browsers.This would also be an issue if you self-signed your certificate.
- Did you install your intermediates properly? While some browsers will try to fill in any gaps in the certificate chain, you don’t want to leave things to chance. Make sure that you successfully install all intermediate certificates at the time you install your SSL certificate.
- Is your server configured correctly? Just because you’ve installed your SSL certificate and any accompanying intermediates doesn’t mean you’ve configured your server properly. If you’re having trouble with the installation of your certificate, our installation team would he happy to assist.
As always, if you have any questions about the Chain of Trust feel free to contact our Customer Experience Department!