Chrome 66 Launched: Millions of SSL Certificates Potentially Distrusted
Chrome 66 launched with security at its focal point
Google has just rolled out the stable release of Chrome 66 across all major platforms, and it’s fair to say that not everyone is going to like it. That’s because Google has dealt its first blow to websites that are currently protected by Symantec, and its subsidiary certificate authorities. Any Symantec, GeoTrust, RapidSSL and Thawte SSL certifcates that were issued before June 2016 are now distrusted by Chrome 66. Any certificates that have been issued between June 2016 and December 2017 will need to be reissued before October 23, 2018.
This is what Chrome’s warning looks like:
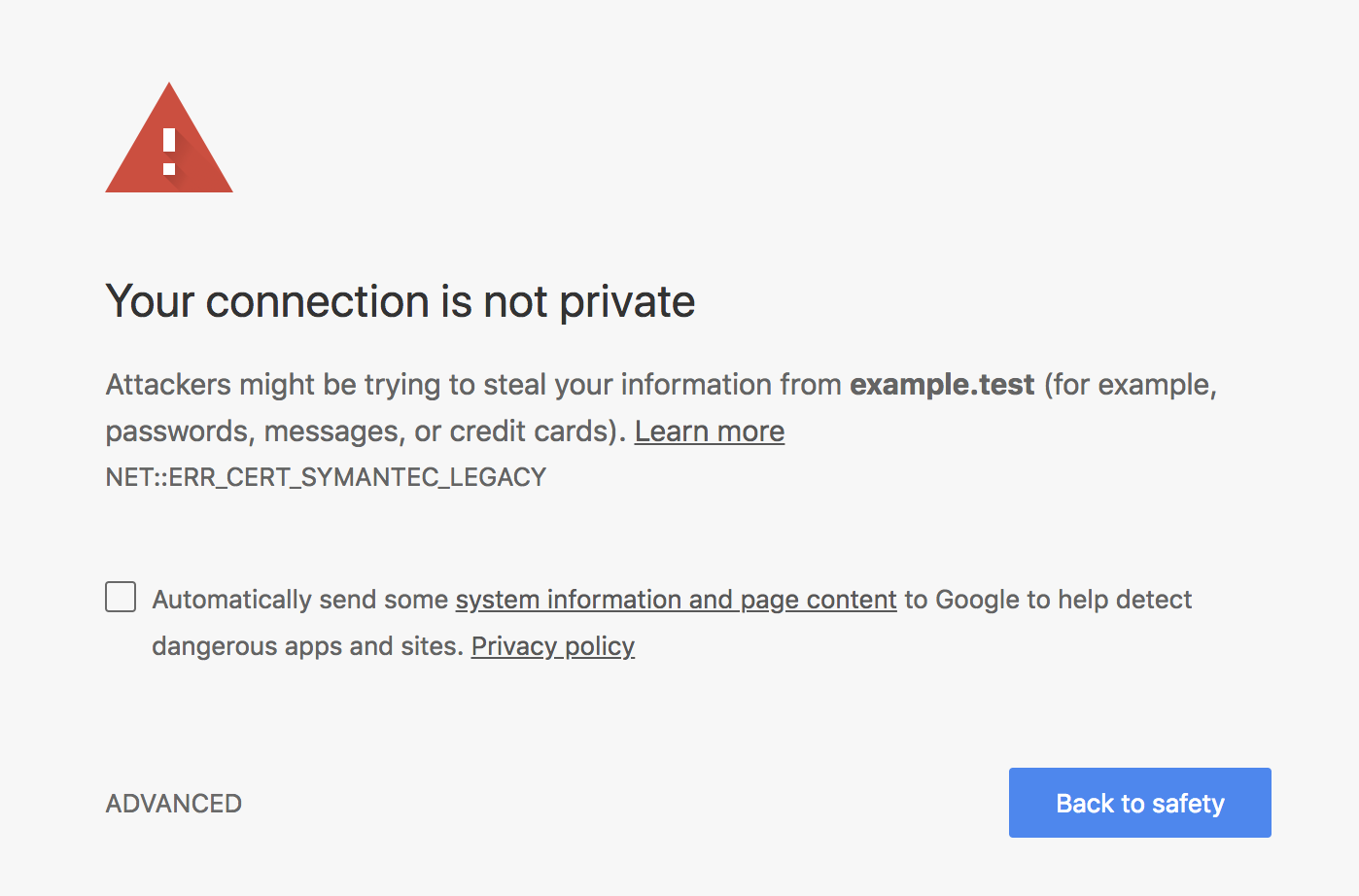
Google distrusting Symantec SSL certificates has been an ongoing situation dating back to 2016. It was (and still is) a part of its long-term plan to distrust all Symantec SSL/TLS certificates issued off Symantec’s now-distrusted PKI. Whether or not this was an overreaction on Google’s part is now a moot point. Any site that is getting penalized needs to re-issue their certificates (for free) from DigiCert, which acquired Symantec’s CA business, immediately.
Administrators of distrusted websites have likely received numerous reminders. We know this because our parent company, as an SSL certificate provider, has sent hundreds of thousands of these notifications. But we realize that a lot of website owners are busy running their sites and these things can fall by the wayside. While the Symantec-Google distrust has been a huge deal in this industry, it hasn’t made major waves outside of it. That means there will be plenty of site owners surprised by this.
If you’re one of them, we suggest you re-issue your cert ASAP. If you don’t know how to do it, here’s someone you can talk to.
New Features in Chrome 66
The distrust of Symantec certificates is likely to hog the limelight (as it should) as far as Chrome 66 is concerned. But there are two noteworthy introductions that we can’t afford to overlook. One of them is the automatic audio silencing of auto-play videos. I love this move as I no longer have to go searching through 30-35 open tabs (a rookie number for many of you out there) looking for the noisy culprit. Google had planned to introduce this feature in Chrome 64, and I was looking forward to it. But for whatever reason, it got delayed. But, as the great Greek philosopher Empedocles often said: better late than never.
Another substantial improvement that is being rolled out is Site Isolation. If you follow our blog, you’d know that Google introduced this feature in Chrome 63. However, it wasn’t enabled by default. Now, in Chrome 66, this feature has become a default setting. Right now, this has been rolled out on a trial basis and will only be available to a limited number of users. If everything goes smoothly, every user will be able to get their hands on it.
Site Isolation facilitates separate processes for separate sites. In other words, each open website’s content is treated as a different process. This results in better performance and enhanced security. The performance is improved as entire browser won’t freeze if one of the tabs crashes (phew!). As far as security is concerned, Site Isolation thwarts Code Infusion attacks as it doesn’t let one page to talk with the other. As a result, the hackers can’t infuse malicious code in Chrome’s Sandbox process. The only downfall of Site Isolation is that it may increase Chrome’s memory usage by 10-20 percent. Trust me; it’s worth it.
With Chrome 66, you’ll be able to export your saved passwords to other browsers. Apart from this, Chrome 66 also incorporates a whopping 62 security fixes. If you still haven’t received the Chrome 66 update, don’t worry, as it is being rolled out in phases. By the end of the week, it should be available everywhere.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown