This is what happens when your SSL certificate expires
What happens when your SSL certificate expires? This.
One of the most common questions we get asked is some variation on “what happens when your SSL certificate expires?” or “what happens if you don’t renew your SSL certificates on time?”

The answer is death. Swift ignominious death. Ever wonder what happened to Jeeves? Now you know. On the death certificate his cause of death just reads: “certificate expiry.”
That was a dark day for the internet…
Ok, so maybe that’s a little bit hyperbolic (and patently untrue – everyone knows it was Google’s wetwork). But certificate expiration can have some serious consequences.
So, today we’re going to talk about what happens when your SSL certificate expires, we’ll toss out some infamous examples of certificate expiration and we’ll even go into how to avoid accidentally letting your SSL certificates expire in the first place.
Let’s hash it out.
What Happens When Your SSL Certificate Expires?
Let’s start by answering the question we posed at the outset and then we’ll delve into some of the minutiae. SSL certificates facilitate the encryption of data in transit. By installing an SSL certificate on your website’s server, it allows you to host it over HTTPS and create secure, encrypted connections between your site and its visitors. This safeguards communication. SSL also authenticates the server.
SSL certificates are not valid forever though. They expire. There is an industry forum, the Certificate Authority/Browser Forum, that serves as a de facto regulatory body for the SSL/TLS industry. The CAB Forum legislates the baseline requirements that Certificate Authorities must follow to issue trusted SSL certificates. Those requirements dictate that SSL certificates may have a lifespan of no longer than 27 months (two years + you can carry over up to three months when you renew with time remaining on your previous certificate).
That means that every website needs to renew or replace its SSL certificate at least once every two years. So, what happens when your SSL certificate expires? It makes your sight nigh unreachable.
When a user’s browser arrives at your website it checks for the validity of the SSL certificate within milliseconds (it’s part of the SSL handshake). If the certificate is expired, it issues a warning like this:
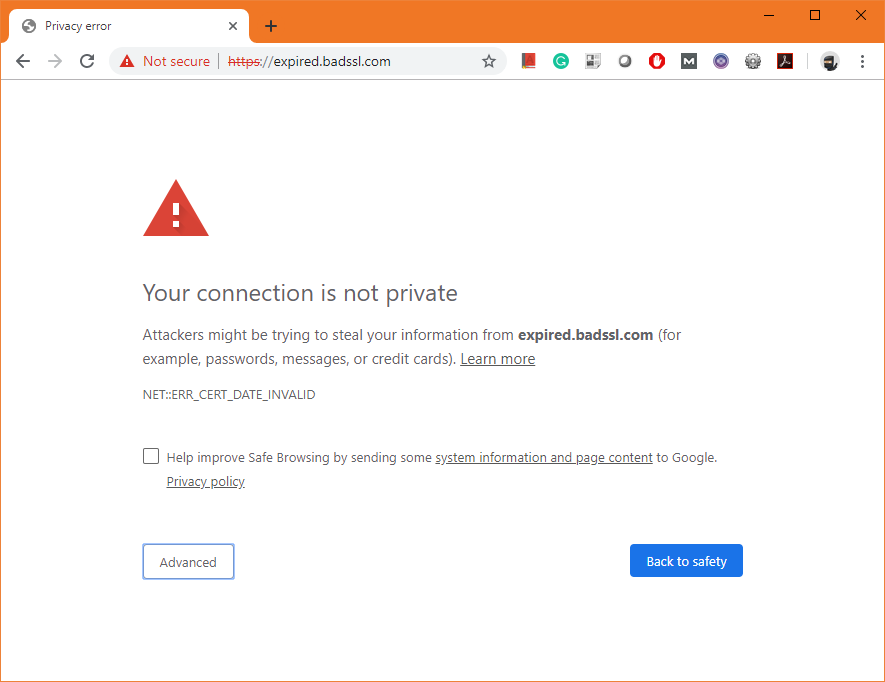
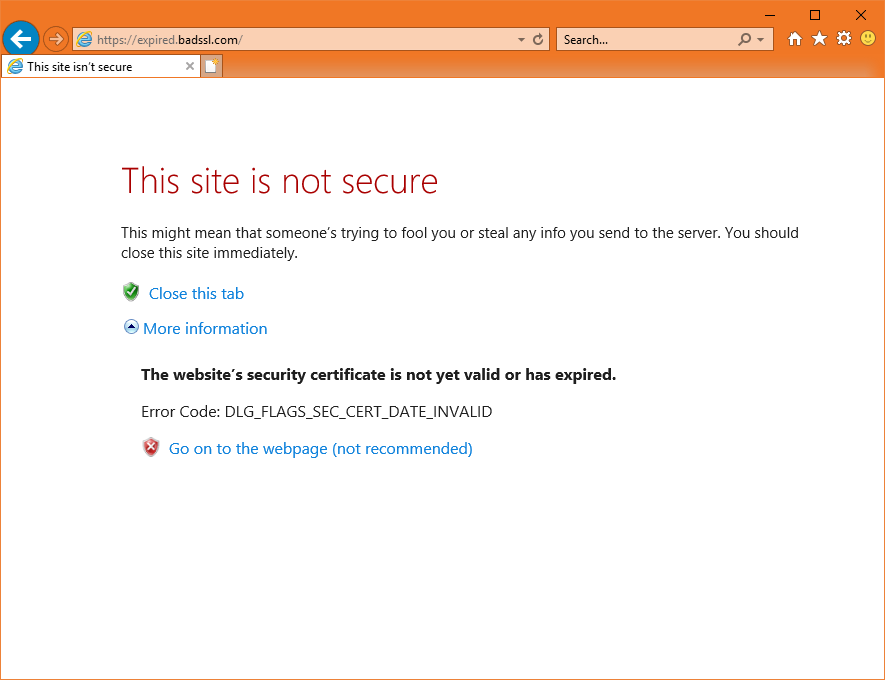
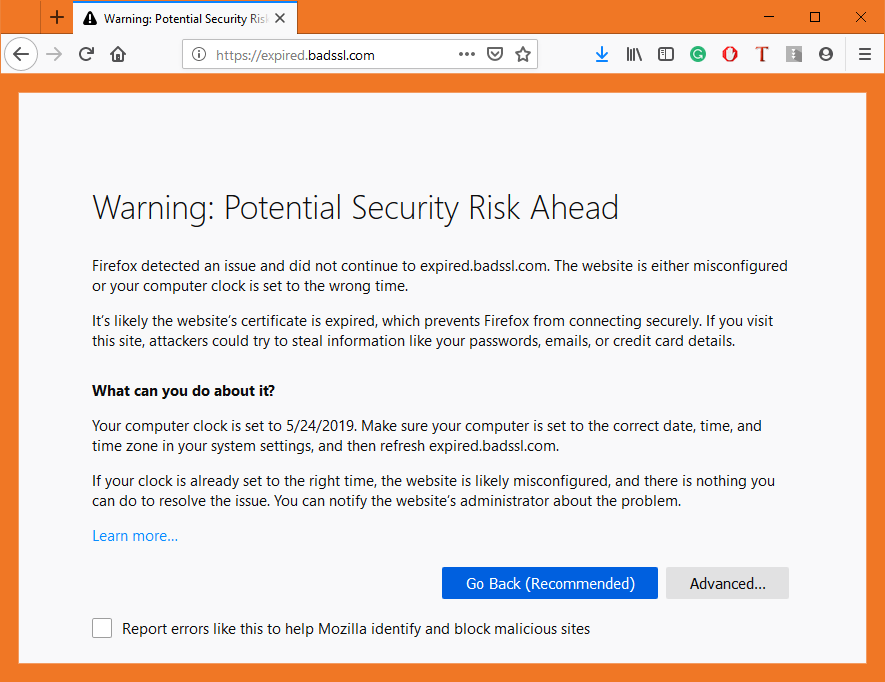
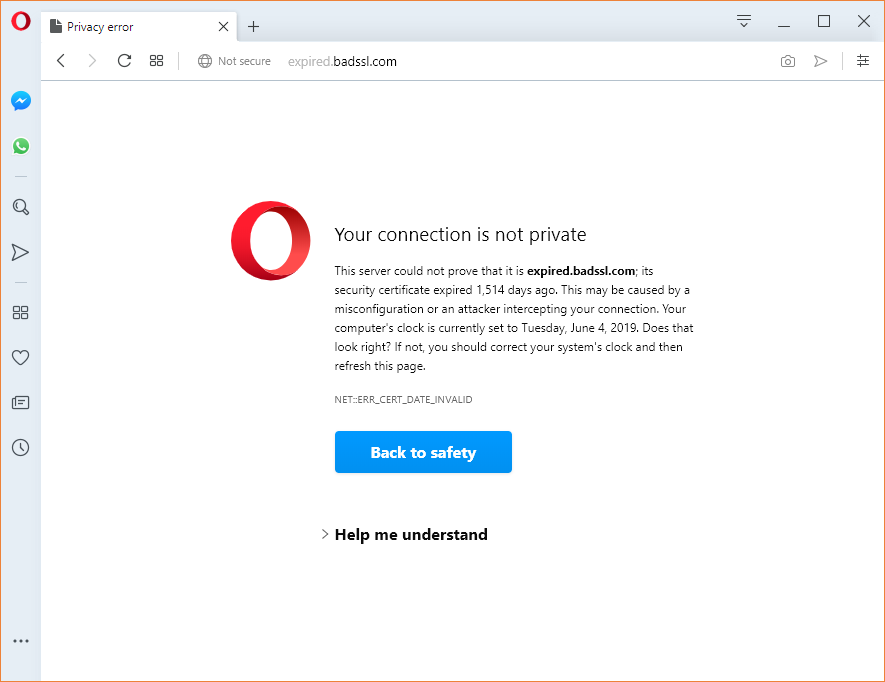
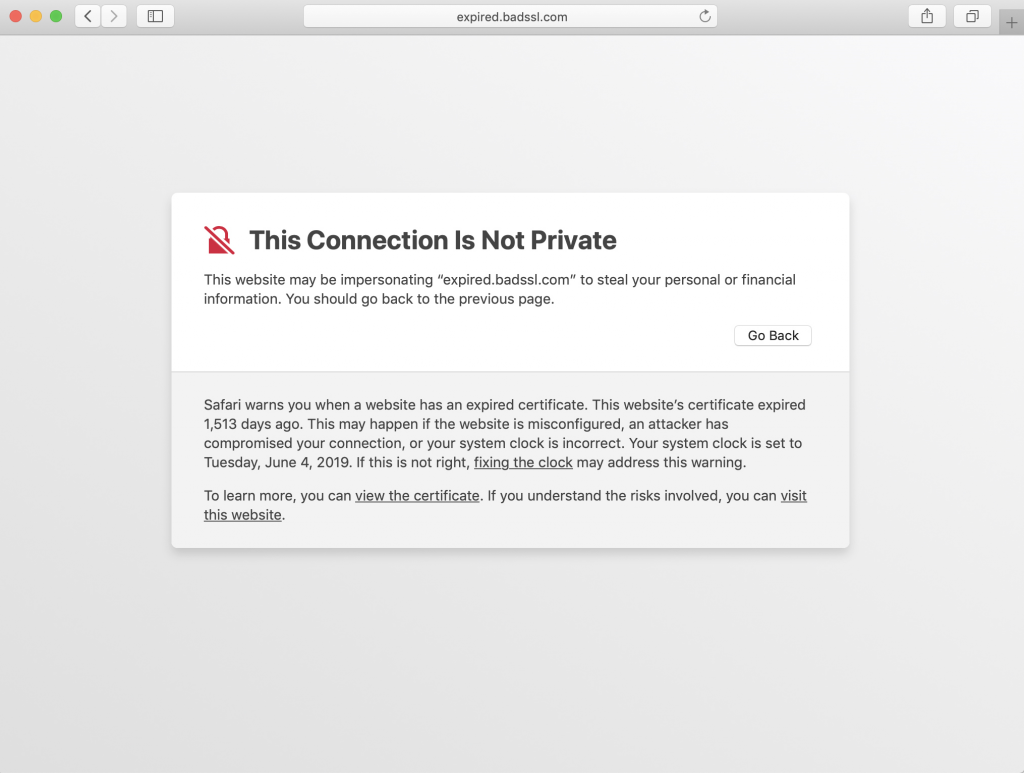
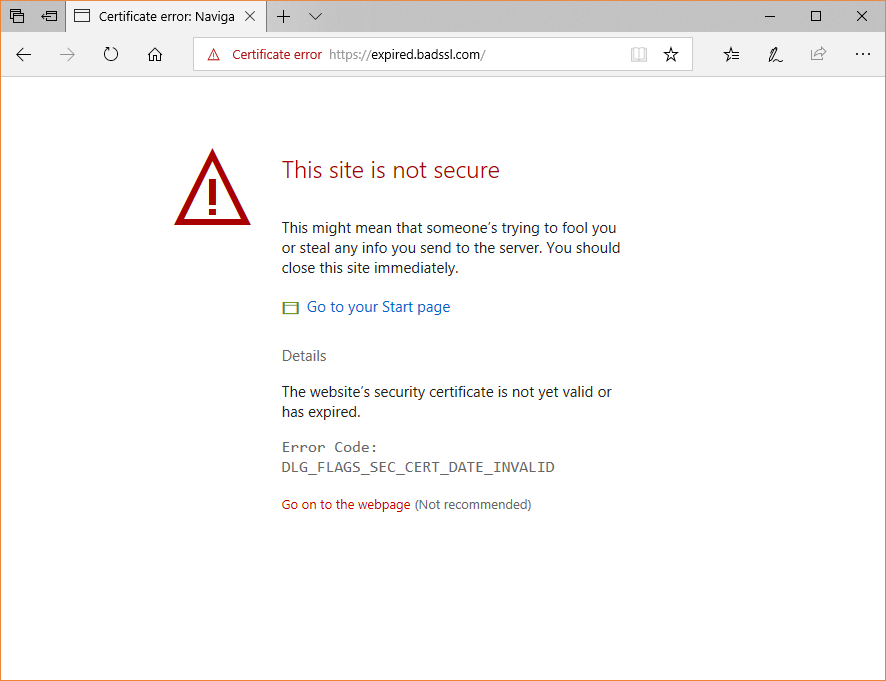
You don’t need me to tell you that this message is essentially a death warrant for your site’s traffic, sales– whatever metric or KPI you value. While most browsers do offer an option to click through the warning, almost nobody does it. The average internet user may not know a ton about cybersecurity, but they know two things: computers are expensive and malware messes up computers. So, if their browser tells them a website isn’t safe, or in this case that their connection isn’t secure, they are probably going to listen.
Wouldn’t you?
Certificate Expiration by the Numbers

Why Do SSL Certificates Expire?
This is a topic we’ve discussed quite a bit in the past, but here’s a quick rundown. As we mentioned earlier, SSL certificates help facilitate two things: encryption and authentication. The latter is the bigger culprit for certificate expiry.
All SSL certificates authenticate something, even domain validation certificates authenticate a server. As with any form of authentication, you occasionally need to re-validate the information you’re using in order to make sure it’s accurate.
That’s especially true on the internet. Things change all the time. Websites change hands. Companies are bought and sold. And SSL/TLS is based on a trust model that can be undermined by that. So it’s important for Certificate Authorities that are issuing trusted certificates to ensure that the information they’re using to authenticate servers and organizations is as up-to-date and accurate as possible.

Let’s look at a practical example. Circuit City was an electronics and appliance retailer that went out of business about a decade ago. Now, imagine for a moment that SSL certificates didn’t expire. Circuit City’s assets have all been sold off or jettisoned, what if someone grabs the certificate and the domain it was issued for. Now they’re free to do whatever they want with that domain (until the certificate is revoked, but that’s a completely separate mess) and everyone’s browser would see this site as the legitimate article. Someone that didn’t realize the company was now defunct could easily be duped. After all, the certificate is legitimate.
That can’t happen. If anything, expect certificate lifespans to get shorter. And believe it or not – we often hear critics claim certificate expiry is a racket for the Certificate Authorities – CAs aren’t the one driving shorter validity. The browsers are.
At one point, SSL certificates could be issued for as long as five years. Then it was knocked down to three. Then last year it was down to two—which was a compromise because the original Google proposal was for one year. In the future certificate validity may be as short as 3-6 months. Let’s Encrypt issues 3 month certificates right now.
Related: Secure Your Domain & Sub-Domains with a RapidSSL Wildcard Certificate.
Authentication isn’t the only culprit for certificate expiry though. Having shorter certificate validity periods also makes it easier for the industry to roll out changes more quickly. For instance, a few years ago the SSL/TLS industry deprecated the use of SHA-1 as a hashing algorithm. As anyone that has ever ordered an SSL certificate knows, you pick the hashing algorithm during generation. With three year validity, in some cases you may have to wait as long as 39 months after the deadline before the certificate expires and SHA-1 is deprecated by that website.
Short validity periods fix this. If we were to phase out SHA-2 in favor of SHA-3 (don’t worry, that’s not coming anytime soon) you could set a cutoff date for issuing SHA-2 certificates and within 27 (or 15 if it’s reduced to one year) months, SHA-2 would be completely deprecated.

High Profile SSL Certificate Expirations
If you do accidentally forget to renew on time and let your SSL certificate expire, you can take some solace in knowing that you are not alone. Below, we’re going to keep a running list of high-profile SSL expirations:
LinkedIn let’s one of its SSL/TLS certificates expire… again!
For the second time in two years LinkedIn suffered outages in the US and UK following the expiration of one of its SSL certificates. This time the expiration affected a link shortener, lnkd.in, which rendered the site unreachable to anyone that clicked one of the shortened links (they’re typically found on social media). Link shorteners basically act like proxies, the shortened link connects with the link shortening server, gets inspected, and then gets passed along to the intended destination. And here’s the thing, this didn’t just affect LinkedIn, anyone sharing content through the site has their link shortened. Here’s an example of one of our posts with its URL shortened.

This is a perfect example of how an expired certificate doesn’t just harm your organization, it can also harm your customers and partners, too.
US Government shutdown causes dozens of SSL certificate expirations
To round out 2018 and kick-start 2019, the two political parties that govern the United States decided to play a game of shutdown chicken that ended up causing the expiration of over 130 government SSL certificates, rendering dozens of sites completely unreachable. As part of a Department of Homeland Security directive from 2015, all government websites are supposed to be on the HSTS preload list. HSTS is a security header that forces browsers to make secure connections. It’s a great idea, the only downside is if anything ever happens to your SSL/TLS certificate, your website breaks. And by breaks I mean it becomes completely unreachable. That’s a problem when it happens to government organizations like the Department of Justice, the US Court of Appeals or NASA.
Ericsson lets certificate expire, 32 million people lose cellular service
In December of 2018, millions of people in the UK were without cellular coverage following the expiration of a digital certificate associated with Ericsson’s network. Ericsson, which is a Swedish cellular company, manufactures myriad back-end equipment for the world’s cellular networks. Thanks to an expired digital certificate in a version of Ericsson’s management software that is widely used by European telecommunications companies millions of cellular users experienced downtime.The outages initially affected software used by O2 and its parent company, Telefonica, but eventually the outages showed up downstream, too.
Equifax misses a breach for 76 days because of an expired certificate
Equifax would have discovered the 2017 attack that compromised millions of peoples’ personal information a lot sooner if not for an expired digital certificate. For ten months, following the expiration of the certificate, Equifax couldn’t inspect the traffic running through its own network. That, in turn, caused it to miss the high-profile breach for 76 days, until the certificate was finally replaced and inspection resumed.
Cisco lets one of its SSL certificates expire
In the first half of 2018, Cisco had an issue that superseded regular SSL certificate expiration—Cisco had a root expire. As we discussed a few days ago, Roots certificates are an integral part of the SSL/TLS trust model. Seated at the top of the proverbial tree, Root certificates are used to sign and issue intermediates and end user SSL certificates. In this case, the root was attached to one of Cisco’s VPNs, meaning every certificate it issued to end users could have potentially become invalid, too. Fortunately, that doesn’t appear to have happened, users were just blocked from generating new end points.

The issue was resolved in APEC-EM Release 1.6.3.
Pokemon Go lets its SSL certificate expire
Niantic seems to be having a bit of a resurgence with Pokemon Go, but back in January of 2018 the game was running into game-breaking bugs and a litany of other problems—one of which was the expiration of one its SSL certificates. The outage was short, lasting just about half an hour, but it was more egg on Niantic’s face at the time.
Fortunately, things seem to be going a lot better for the company lately.
The UK Conservative Party lets its SSL Certificate Expire
The Tories, as they’re known in the UK, don’t have a great reputation when it comes to encryption, in general. Former home secretary Amber Rudd and soon to be ex-Prime Minister Theresa May have both publicly criticized encryption despite clearly not understanding very much about it. So it was ironic, then, on January 8, 2018 when the Tories’ website went down following the expiration of its SSL certificate.
Or maybe you could say it Brexpired.
LinkedIn lets its SSL Certificate Expire
At the beginning of December 2017, LinkedIn allowed one of its SSL certificates to expire. It knocked out LinkedIn sites in the US, UK and Canada. As the VP of Venafi, Kevin Bocek said at the time:
“LinkedIn’s blunder demonstrates why keeping in control of certificates is so important. While LinkedIn will have thousands of certificates to keep track of, outages like yesterday’s show that it only takes one expiry to cause problems. To stay in control, organizations should look to automate the discovery, management and replacement of every single certificate on its network.”
LinkedIn quickly fixed the problem with a DigiCert Organization Validated SSL certificate.
Time Warner lets its Mail Server’s SSL certificate expire
In early 2017 Time Warner compounded the boneheaded oversight that let its email server’s SSL certificate expire by offering its customers some equally boneheaded advice on remedying the situation:
“…going into your email settings and disabling SSL will stop the pop-up message and re-enable the webmail fetch.”
This is terrible on so many levels. Let’s start with the fact that this is awful advice. Don’t ever disable SSL. Ever. Second, it’s incumbent upon the company that lets its SSL certificate expire to replace it in short order. It’s not the customers’ job to change their settings to compensate for that company’s negligence. Third, who the hell is still using Time Warner as an email service?
How to Avoid Letting Your SSL Certificate Expire
Enterprise businesses have a different set of problems when it comes to certificate management. Whereas Small and Medium Sized Businesses (SMBs) may just have one, or a handful of certificates, Enterprise companies have sprawling networks, myriad connected devices and just a lot more surface to cover in general. At the enterprise level, allowing an SSL certificate to expire is usually the result of oversight, not incompetence.

The best way to avoid this issue, at any level – from enterprise to the smallest mom-and-pops operation – is automation. That may sound a bit abstract, but automation has never been easier now that the ACME protocol has been published as a standard by the IETF. We covered this a few days ago, proper configuration of the ACME protocol lets you set it and forget it.
The ACME protocol works by installing a client on your server that will act as an agent for the website(s) hosted on it. Following a process where the agent proves it’s authorized to act on behalf of the designated websites, it can be configured to contact the Certificate Authority of your choice at regular intervals to replace and renew SSL certificates. Originally, only Let’s Encrypt supported this. But each day more and more CAs are adding their own support, with major players like Sectigo and DigiCert leading the way.
ACME isn’t the only choice for automation, other certificate management platforms like Venafi’s can also be set up to automate all stages of the certificate lifecycle, including those oh-so-important renewals.
We’ve got over a decade’s worth of experience helping organizations of all sizes tackle these challenges. Here’s some more actionable advice on avoiding certificate expiry in the event you’re not automating:
- Whatever CA or SSL service you got your SSL certificates from will send you expiration notifications at set intervals starting at 90 days out. Make sure that you set these reminders to be sent to a distribution list and not just a single individual. The Point-of-Contact you used when getting the certificate issued may not be there by the time it expires. Maybe they moved on, got promoted or just drank a little too much at the office Christmas party and got canned—whatever the case you need to make sure the notifications are reaching the right people.
- Identify the proper channels to escalate reminders as the expiry date approaches. For instance, at 90 days out you might just want to have the notification sent to your distribution list. At 60 days send it to your distro list, and to your system admin. At 30 days you send it to both the list and the system admin, and now your IT Manager gets looped in, too. Keep escalating all the way to the CIO or CISO if needed.
- Find a good certificate management platform. One of the biggest challenges facing enterprise businesses is visibility. You can’t replace expiring certificates if you can’t see them. We try to stay vendor agnostic, but DigiCert, Sectigo and Venafi all have tremendous platforms that can help enterprises see and manage digital certificates across their entire infrastructure. Also, make sure you log in regularly so you can stay apprised of when you have renewals coming up.
- Decide on what CA(s) you want to work with and then set up CAA records to restrict who can issue for your domains. This will help to eliminate the possibility of new rogue certificates being issued. The more you can consolidate your PKI into a single platform, the better off you’ll be.
- Speaking of rogue certificates, find a good scanning tool and then use it regularly to find and track rogue certificates by checking the various CT logs.
So, that’s what happens when your SSL certificate expires
Forgetting to renew or replace an expiring SSL certificate can happen to anyone. But there are a lot of tools available to help minimize the risk that poses. The key, as we’ve discussed, is either automation, or at least having visibility and good lines of communication so you can get out ahead of upcoming expirations.
Check out our 3 steps for how to fix your security certificate once it has expired to learn more.
Unfortunately, this problem isn’t going anywhere – even with the rise of automation – the sheer volume of digital certificates being issued to new websites, IoT devices and end points means somewhere, someplace, there’s always going to be one expiring.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (7 votes, average: 3.29 out of 5, rated)
(7 votes, average: 3.29 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown