Gartner Says PKI Was a Bigger Challenge in 2023 Than MFA
Gartner reports taking “twice as many calls” about PKI and certificate lifecycle management (CLM) than multi-factor authentication (MFA)-related calls in 2023. Why is interest in PKI growing and why are so many organizations having PKI-related challenges? Let’s take a look…
Erik Wahlström, Vice President and Key Initiative Leader of the Identity and Access Management Team at Gartner, recently shared in a LinkedIn post that organizations are increasingly interested in public key infrastructure (PKI) and managing their digital certificates.
Is this growing interest because more companies are using PKI, or is PKI getting harder? (Hint: It’s both.) So, why are companies having more PKI challenges? As Wahlström alludes, there are many reasons, but here are five categories in particular that we see a lot of challenges in…
Let’s hash it out.
If Your Organization Has Challenges with PKI, You’re Not Alone
Public key infrastructure and X.509 digital certificates aren’t new; the framework and digital certificate standard have been around since the 1980s. Despite this fact, organizations often still struggle. Research from KeyFactor’s The State of Machine Identity Management 2023 report identifies increasing PKI complexity as one of the main causes of their headaches.
See if any of the survey respondents’ revelations from KeyFactor’s data rings a bell regarding how things are within your organization:
- 53% say don’t have the staff and resources to maintain their PKIs effectively
- Nearly three in four say they’re deploying more certificates and keys
- 22% say the lack of executive support is a “serious issue”
Many organizations have historically failed to fully embrace both the benefits and requirements of running an effective PKI. Data from DigiCert’s State of Digital Trust 2024 report shows that one-third of surveyed enterprises are overly confident in their PKI security capabilities and digital trust.
It’s likely that this kind of mindset has led to many of the data breaches and service outages we’ve seen in recent years.
So, why bother with these changes now, after all this time? And what are some of the PKI-related challenges organizations are facing?
5 PKI Challenges That Organizations Are Facing
1. Too Many Certificates Are Spread All Over the Place
SSL Everywhere has led to the broader use of SSL/TLS certificates across the internet. And this is a good thing, after all. Every organization should implement HTTPS across their digital platforms to provide secure, authenticated connections that protect data in transit. This helps to keep their most sensitive data out of bad guys’ hands.
Securing your data in transit helps you meet some of the requirements of various U.S. data privacy laws and other privacy and encryption-related regulations. By adding SSL/TLS (i.e., the transport layer security that turns HTTP into the secure HTTPS protocol) to the equation, you’re bringing public key cryptography and verified digital identities into the fold. These things, combined with a secure protocol, help to support digital trust and give your brand and organization a reputational boost in the eyes of consumers and search engines.
However, the challenge of SSL Everywhere is exactly what the name implies: SSL is in use everywhere. So, this means many more SSL/TLS certificates are in use now than we saw years ago — not to mention other certificate types such as device and user authentication certificates. And every one of those digital certificates and its cryptographic key pairs must be properly managed.
2. Shortening Certificate Lifespans (I.e., Decreasing Certificate Validity Periods)
We’ve heard a lot about shorter certificate lifespans over the past few years. But what are some of the reasons leading to these decreased validity periods?
- Certificate validity was reduced to 398 days a few years ago.
- Cutting-edge organizations are using new short-term certificates (e.g., 7-10 days).
- Some certification authorities are issuing 90-day certificates.
- Google would like to move the industry toward a 90-day max lifespan.
While shortening certificate lifespans sounds potentially beneficial on the surface, it may have the unintended opposite effect. For example, it could result in more certificate outages — about which KeyFactor’s 2023 machine identity report data indicates that 66% of survey respondents report it takes three or more hours to identify and remediate.
Smaller organizations often rely on manual certificate management methods (think Excel spreadsheets). This is “doable” if you only have a handful of certificates to worry about. But what if you’re an enterprise managing hundreds, thousands, or tens of thousands of certificates? Guess again.
If a certificate has already been compromised, the bottom line is that it needs to be revoked immediately. It doesn’t matter if it exists for 90 days or 398 days — it still needs to be revoked right away. And until that happens, your covered systems and apps are at risk. This is where requiring and enforcing strong revocation and certificate management policies and processes is key, along with implementing certificate lifecycle automation, is more important than setting arbitrary certificate validity lifespans.
3. Needing Better Certificate Management and Lifecycle Automation
More certificates + shorter certificate validity periods = a lot more problems for the people managing certificates.
Conversations about PKI security concerns almost always circle back to certificate lifecycle management. Why? Because they go hand in hand. While CLM isn’t everything in cyber security, it is a key (excuse the pun) piece of the puzzle. Generally speaking, certificate lifecycle management boils down to a handful of essential points:
- Knowing where all your certificates are deployed at any given moment,
- Knowing who’s responsible for issuing, monitoring, and managing them,
- Ensuring that your organization only uses valid certificates, and
- Renewing your certificates before they expire or replacing them once revoked.
But if you don’t have a system in place that helps you manage and automate many of these essential (but monotonous) tasks, then your organization is in for a rough ride.
Let’s consider certificate lifecycle management in terms of car maintenance. Managing your certificates is akin to changing the oil in your vehicle’s engine on a regular schedule. When done properly, it’s what helps keep your website, web apps, and services running smoothly and helps to prevent them from seizing.
Not giving your vehicle regular oil changes can result in your engine becoming a gunky, disgusting mess that requires a costly rebuild:
Likewise, not managing the certificates within your IT ecosystem and network(s) can lead to service outages, website downtime, data breaches, and a bunch of other issues that everyone from your board to your customers really won’t like.
4. Having Legacy PKI Systems That Don’t Meet Current Security Needs
Company leaders often look toward implementing the “latest and greatest” technologies within their operations. Historically, however, this mindset often hasn’t extended to the most foundational security mechanisms. For many organizations:
- They often rely on outdated legacy PKI systems and inefficient processes.
- Others lack the resources and know-how to implement PKI security correctly.
- Many try to cut corners to save time and costs. (Gotta meet those deadlines, am I right?)
Needless to say, PKI is a hot mess when not implemented properly. As a result, organizations face increasingly greater challenges and scrutiny from consumers and lawmakers alike. However, there’s a shift in mindset regarding how organizations regard PKI: companies are striving to achieve more mature PKIs.
As part of their modernization efforts, organizations must ensure systems are implemented and configured properly. “Configuration creep,” as Wahlström called it — a term that refers to the gradual sprawl of security misconfigurations that build up within your networks and other IT environments over time — is a big issue; one that’s poised to keep increasing, particularly for legacy systems.
Poor configurations degrade your organization’s overall cyber security posture, creating vulnerabilities that leave it (and its sensitive data) open to attack, exploitation, and compromise.
5. Wanting to Be Prepared For Quantum Computing
Quantum computers that can break modern public key encryption are coming, whether you’re prepared or not. And being crypto-agile is a key element of being prepared for its (eventual) arrival.
Cryptographic agility, or crypto-agility, is the concept of having PKI-based security mechanisms and systems in place that provide visibility and enable cryptographic responsiveness. It’s about knowing:
- What systems and assets you have in place,
- How they’re being used, and
- Whether your organization and PKI are equipped to handle the issues you’ll face within your IT ecosystem.
Being crypto-agile is particularly critical when you consider the impending threat that quantum computers pose. The modern public key cryptographic algorithms we rely on today (e.g., RSA, which uses prime factor-based keys) will be broken a la Shor’s Algorithm. This is why post-quantum cryptography (PQC), or what’s often referred to as quantum-resistant or quantum-safe cryptography, is on the horizon.
Being crypto-agile involves the eventual implementation of PQC hybrid algorithms. As a PKI administrator, your first step is to inventory all of your cryptographic keys and certificates. This way, you know what digital assets you have and where they’re located.
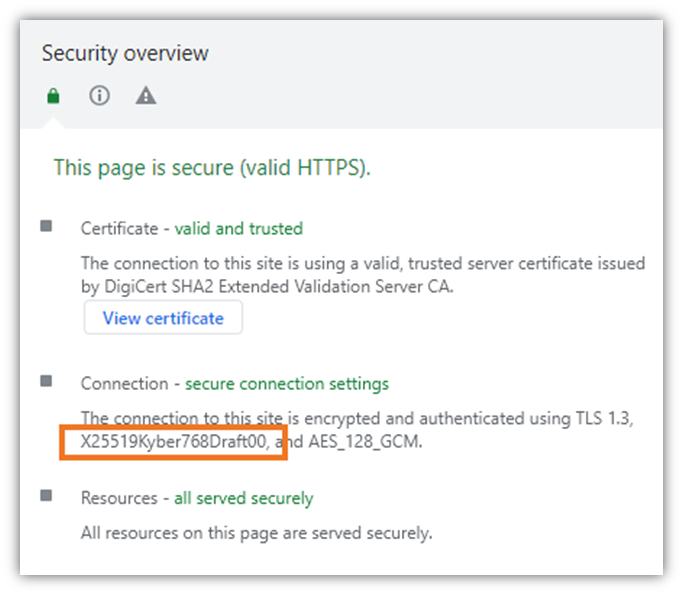
As a user, you can also implement the use of some PQC hybrid algorithms in your browser. Here’s an example of the PQC hybrid algorithm that Google Chrome (browser version 116 or later) employs when users visit The SSL Store’s website:
Final Thoughts
Let’s face it: consumers nowadays are virtually inundated with news about service providers suffering data breaches and certificate-based service outages. They’re seeing what happens when organizations rely on outdated legacy systems, inefficient processes, and insecure practices:
- Sites and services are taken down by organizations’ certificate mismanagement issues more often than by threat actors.
- Security gaps serve as exploits, increasing organizations’ attack surfaces and leaving their data at risk.
- Their data is being compromised due to mismanaged PKI and compromised keys.
All of these factors lead to them losing faith in organizations and other entities that are responsible for securely storing and using their data.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













 (2 votes, average: 3.50 out of 5, rated)
(2 votes, average: 3.50 out of 5, rated)






Be the first to comment