What Is a Device Certificate? Device Certificates Explained
Device certificates make it possible to do everything from authenticating devices to securing their communications and data as it transmits across the internet. Here’s what to know about what these devices are and how using them can benefit your business
Electronic devices have become staples of our everyday personal and professional lives. If you’re like many people, you might have an Alexa in your home or a smart thermostat in your office. And there’s a reason why they’re so popular — smart devices are attributed to helping companies streamline processes, increase productivity, better serve customers, and reduce costs.
Now, we’re not here to sell you on the benefits of these devices. However, we want to point out that the use of connected devices has steadily been increasing over the last decade. IDC estimates that an average of 152,200 IoT devices will connect each minute by 2025. That’s a lot of devices — let’s do the math. Considering that there are 1,440 minutes in a day and 525,600 minutes in the average year, that means they’re estimating:
- 219,168,000 devices will connect a day by 2025, or
- 115,194,700,800,000 — more than 115 trillion — devices will connect each year!
If your organization chooses to say yes to IoT, you also need to be aware of what you need to do to secure those devices. This is where device certificates come into play. But what is a device certificate? And how do these certificates certificates benefit your organization’s security and authentication capabilities?
Let’s hash it out.
What Is a Device Certificate? Defining Device Certificates
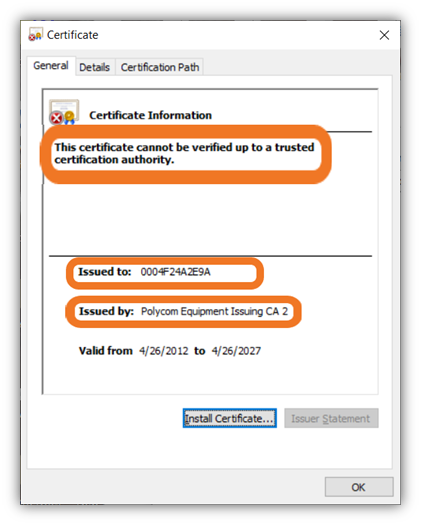
A device certificate is a type of digital certificate that enables mutual authentication and secure connections between two devices (i.e., machine-to-machine, or M2M communications). This is done through the use of public key infrastructure, or PKI for short. This is why they’re also sometimes known as PKI device certificates.
A device certificate is typically issued by an organization’s internal certificate authority, or what’s known as a private CA. While we’re not going to get into the nitty-gritty differences of public vs private CAs, we’ll give you a quick overview.
- A public certificate authority is a separate trusted third party that issues publicly trusted certificates that you buy.
- A private CA, on the other hand, is internal to your organization (meaning, you issue your own certificates for use on your network).
Now, let’s quickly compare a client authentication certificate that’s been issued by a public CA versus a device certificate that’s been issued by a private CA:
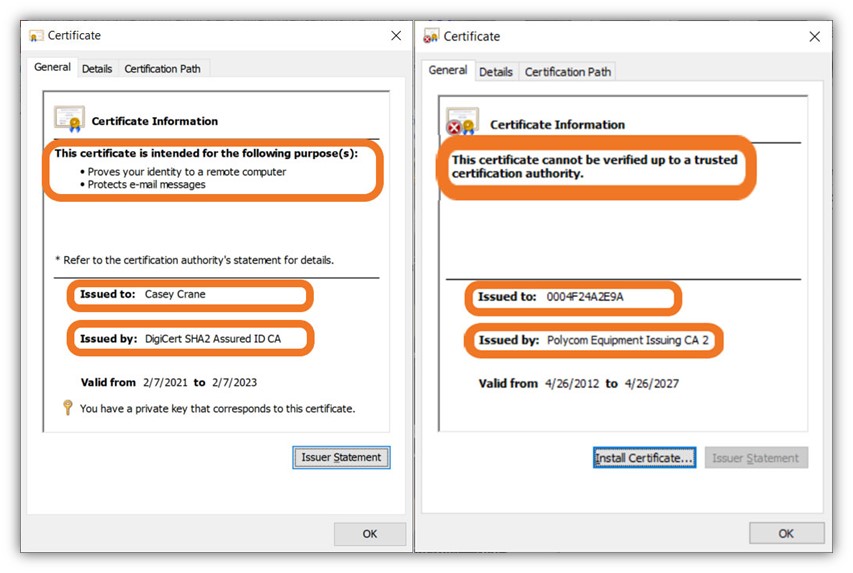
In a nutshell, device certificates enable the following:
- Secure authentication through the use of verified organizational identity,
- Device identity via the common name registered on the certificate,
- Data security through the use of encryption, and
- Data integrity through cryptographic signatures and hashing.
Typically, these digital certificates enable authorized devices to connect to your internet network or other devices and applications on your network. The idea here is that the certificate itself serves as a form of digital identity for the device. Much like how a passport helps you prove your identity at the airport, a device certificate enables other devices to verify that the device that’s trying to connect with them is legitimate.
Each certificate comes with a set of cryptographic keys, which helps create those secure communications. One key encrypts the data while the other decrypts it — what this does is ensure that only the intended recipients (the two communicating devices) can access the plaintext data. This helps to prevent unauthorized users from seeing something they shouldn’t.
What Organizations and Industries Typically Use Device Certificates?
Device certificates are irreplaceable tools that help both device manufacturers and deploying enterprises secure their devices. As such, these certificates have uses across virtually all industries and environments, including:
- Manufacturing facilities,
- Healthcare facilities,
- Corporate offices,
- Airports, and
- Retail stores.
Regardless of your industry, these PKI digital certificates can help you secure many types of devices. Examples of two common use cases include:
- IoT device manufacturers can secure their devices before shipping them out the door.
- Deploying organizations (i.e., companies that use these devices within their environments) can use these certificates to secure the devices on their networks.
Unfortunately, many IoT device manufacturers don’t bother securing their devices before shipping them out to customers. This means that as a user (i.e., an organization or enterprise that’s using these devices within your environment), you need to take the initiative to do it yourself.
Examples of Devices These Certificates Help You to Protect
Let’s quickly explore some examples of the types of devices that device certificates protect:
- IoT devices — Examples of these devices include smart CCTV cameras, manufacturing robots, medical devices, and smart monitors and sensors.
- Mobile devices — This is pretty self-explanatory and mainly includes smartphones and tablets (including enterprise and BYOD devices).
- Other hardware devices — This category includes many types of devices, including network appliances (such as gateways and perimeter firewalls).
Server Certificates vs Device Certificates = One-Way vs Two-Way Authentication
When people talk about digital certificates, there’s sometimes a misunderstanding that all digital certificates are the same or that they do the same things. But much like how Apple enthusiasts feel about their devices in the lifelong Apple vs Windows debate, not all certificates are the same and serve different purposes.
Let’s consider a traditional SSL/TLS certificate, or what’s known as a website security certificate. If you use an SSL/TLS certificate on your website (meaning that the certificate is installed on your server), you’re enabling your server to identify itself to customers’ web browsers. This allows the server to establish a secure, encrypted connection between your customers’ clients and your server. This process is known as one-way authentication because only the server is identifying itself to the client — not vice versa.
(Note: The authentication process occurs in what’s known as an SSL/TLS handshake, which is a VERY technical topic that we’re not going to get into right now. Be sure to check out our other article on the topic to learn more about what the SSL/TLS handshake is and how it works.)
Now, let’s consider the role of a device certificate. This certificate lives on the users’ devices, not your server. So, what they do is allow their clients to authenticate to your web server during the SSL/TLS handshake. It’s similar to how client authentication certificates enable authorized users (such as your employees) to connect to web apps or secure drives on your internal network. However, these certificates are used on autonomous devices.
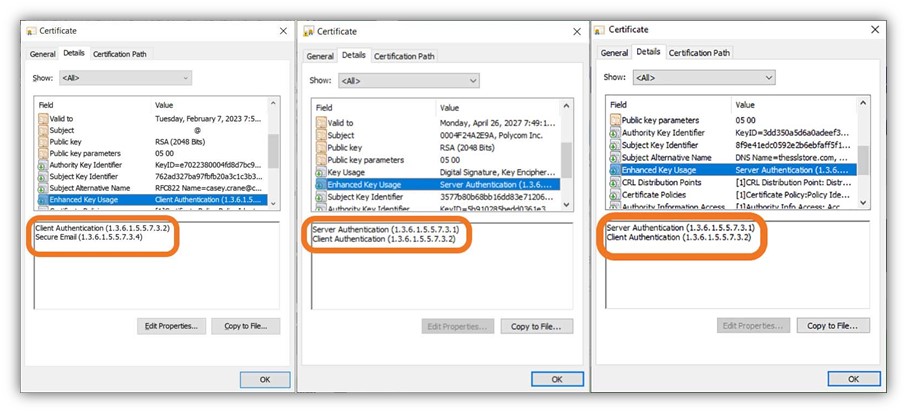
Let’s consider the enhanced key usage (EKU) data of these three types of certificates:
Now, let’s compare this to the key usage data for the three types of certificates:
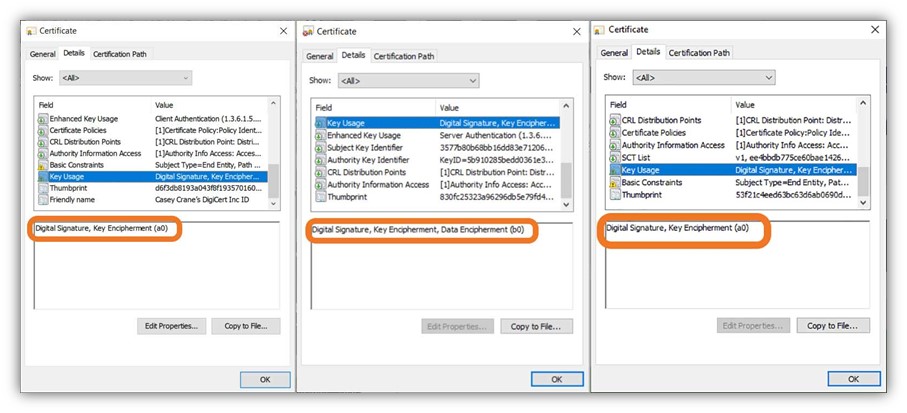
All of this is to say: device certificate authentication = two-way secure authentication.
How Device Certificates Help Secure Your Business and Data
Now that we know what device certificates are and how they work (in a general sense), let’s explore some of their uses and applications for organizations:
- Enable secure authentication between devices. Enable your organizations’ devices to communicate securely with your servers and other devices while mitigating the risks of man-in-the-middle attacks.
- Secure your devices against attackers. Device certificates help to protect your organizations’ devices (and the data they contain) by enabling them to communicate securely with your servers. This helps to protect them against man-in-the-middle attackers and helps to prevent them from becoming botnet zombies.
- Help you scale your device security. Ramping up security can be challenging for any business — but it’s especially true for large organizations and enterprises. These companies often have devices connected to multiple networks and geographic regions.
- Help you achieve zero trust. Device certificates bring your organization closer to creating a zero-trust security environment.
Where Do You Get a Device PKI Certificate?
Since a device certificate is something your company uses within its internal environment and network, you’ll issue it through your private CA. This isn’t something you can buy from a public CA like you would an SSL/TLS certificate or an email signing certificate. There are two main ways to do this:
- Build and manage your own private CA using a quick solution such as OpenSSL or Microsoft CA.
- You can work with a managed PKI (mPKI) provider to handle these processes.
But, regardless of whichever method you choose, there is one final point we need to emphasize here…
Device Certificates Must Be Properly Managed to Be Useful (Final Thoughts)
While there are obviously many financial and operational benefits of using device certificates, these digital certificates won’t do you any good if they’re not properly managed. Part of this entails knowing where your certificates are and when they must be replaced.
Much like everything else in life, nothing lasts forever. All digital certificates are issued with expiration dates. They can also be deployed across centralized and decentralized environments, making them harder to keep tabs on without the right tool(s) at your disposal.
Proper device certificate management entails knowing the following:
- When and how (i.e., using what processes and procedures) device certificates are issued,
- What devices you have on your network(s) and within your IT environments,
- Whether those devices are protected with PKI digital certificates,
- When those certificates are set to expire, and
- Who is responsible for managing those certificates’ lifecycles.
If you’re looking for a great PKI management tool for your device certificates, contact our PKI sales team for help identifying the best solution for your needs.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown