A Look at U.S. Business Email Compromise Statistics (2024)
Data from the FBI Internet Crime Complaint Center (IC3) indicates that reported business email compromise scam losses are up nearly 58% since 2020. See where your state stands regarding the costs of these email channel scams…
A business email compromise (BEC) attack will turn your average day into a scorching dumpster fire. BEC is a devastating technique that can result in everything from system compromises and data breaches to financial losses and reputational ruination.
For this report, we’re focusing on the financial consequences — i.e., reported financial losses — this type of attack creates for businesses and individuals in the United States.
Explore the latest business email compromise statistics data from the FBI’s Internet Crime Complaint Center (IC3). The Internet Crime Report 2023 includes BEC statistics from 2023 and comparison data looking back over the last five years.
Let’s hash it out.
A Quick Review of What Business Email Compromise Scams Entail

The FBI categorizes business email compromise attacks as email-based defrauding scams that:
- target individuals and businesses alike, and
- typically involve using either compromised email accounts or closely spoofed accounts.
In many cases, bad guys use this approach to request fraudulent fund transfers. However, other BEC scenarios involve bad guys requesting fraudulent bank account changes and trying to get their hands on sensitive data.
“But wait,” you may say, “I thought that email account compromise (EAC) attacks are those that involve bad guys taking over legitimate email accounts. Isn’t that the case?”
Yes, you would be right. However, BEC scams also typically involve bad guys compromising legitimate email accounts (often by using social engineering) to get the targets to do their bidding. And since there’s so much overlap between the two terms, the FBI tends to lump BEC and EAC incidents together into the same category, using the terms synonymously.
Business email compromise attacks, totaling $2,946,830,270 in reported losses in 2023 alone, represent the second-costliest category of reported cyber crimes for the year. BEC attacks follow only investment scams in the year’s rankings, which jumped 38% to top $4.57 billion in reported losses in 2023.
A Five-Year Comparison of BEC Losses (2019-2023)
Before diving into individual states’ data, let’s first look at the generally upward trend regarding business email compromise scams that have been reported to the IC3 and other law enforcement agencies over the past five years.
| 2023 | 2022 | 2021 | 2020 | 2019 | |
| BEC Losses By Victims | $2,946,830,270 | $2,742,354,049 | $2,395,953,296 | $1,866,642,107 | $1,776,549,688 |
| # of Complaints By Victims | 21,489 | 21,832 | 19,954 | 19,369 | 23,775 |
Keep in mind that these numbers reflect only reported losses. This is important to recognize because the FBI says that cyber crimes are largely underreported. Furthermore, the data also includes reported incidents from the American public who reside outside the U.S. and its territories as well.
Business email compromise complaint losses have increased by more than 65% since 2019. However, individual complaint reports have decreased by more than 9% in that same period. This means that the average cost per complaint has increased from $74,723 in 2019 to $137,132.03 in 2023. So, fewer people and organizations are being scammed out of larger amounts per incident.
Business Email Compromise Complaints By State (Plus Washington D.C.) in 2023
Alright, you’ve waited long enough — it’s time to dive into the individual states’ data. For this section, we have three bits of data:
- Total Reported Losses: This category refers to the total amount of reported financial losses by victims in either 2022 or 2023.
- Number of Victims: This number refers to the individual complainants who reported losses due to BEC attacks.
- Average Loss Per Victim: This refers to the average financial losses sustained by complainants who were victimized in BEC scams.
The business email compromise statistics included in this report were calculated based on data published in the FBI IC3’s 2021, 2022, and 2023 Internet Crime Reports. We also used the FBI IC3’s State Report tool, which breaks down all types of reported crime typos data by state.
| Total Reported Losses (2023) | Number of Victims (2023) | Average Losses Per Victim (2023) | Total Reported Losses (2022) | YOY Changes in Total Reported Losses (%) | |
| Alabama | $26,955,606 | 195 | $138,233.87 | $19,629,224 | +37% |
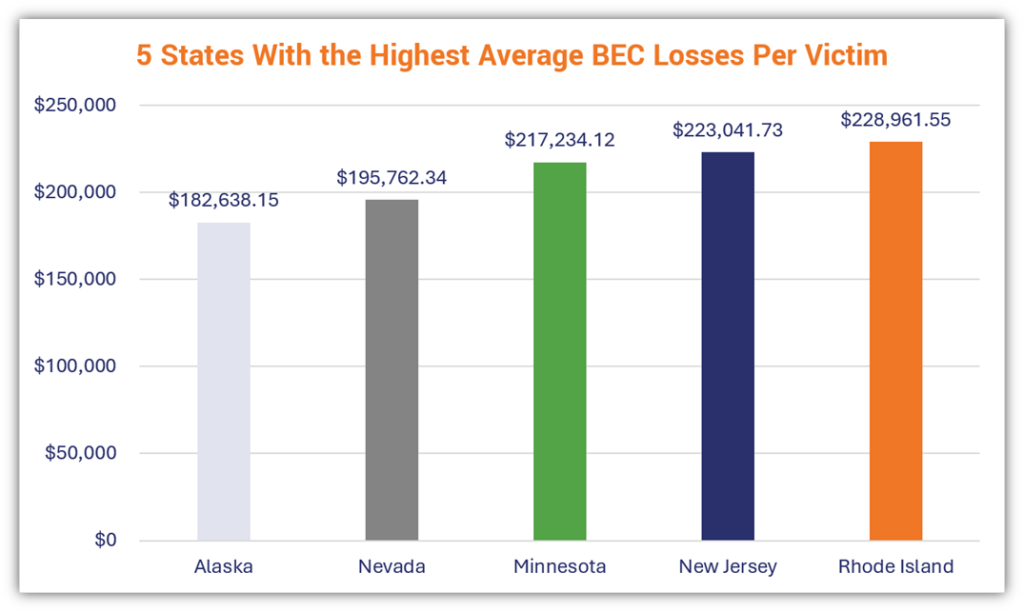
| Alaska | $12,236,756 | 67 | $182,638.15 | $2,987,862 | +310% |
| Arizona | $76,850,493 | 545 | $141,010.08 | $48,491,959 | +59% |
| Arkansas | $15,284,456 | 128 | $119,409.81 | $22,788,271 | -33% |
| California | $412,112,793 | 3,161 | $130,374.18 | $439,425,357 | -6% |
| Colorado | $57,512,670 | 495 | $116.187.21 | $53,961,108 | +7% |
| Connecticut | $38,103,346 | 276 | $138,055.60 | $35,746,379 | +7% |
| Delaware | $9,618,579 | 61 | $157,681.62 | $8,419,097 | +14% |
| District of Columbia | $18,970,376 | 149 | $127,317.96 | $15,279,911 | +24% |
| Florida | $193,828,560 | 1,711 | $113,283.787 | $180,889,707 | +7% |
| Georgia | $88,204,126 | 598 | $147,498.54 | $113,588,916 | -22% |
| Hawaii | $2,841,044 | 73 | $38,918.41 | $4,443,071 | -36% |
| Idaho | $17,412,873 | 99 | $175,887.61 | $12,531,126 | +40% |
| Illinois | $94,174,031 | 773 | $121,829.28 | $83,883,493 | +12% |
| Indiana | $55,751,807 | 326 | $171,017.81 | $22,483,945 | +148% |
| Iowa | $10,906,708 | 161 | $67,743.53 | $16,716,697 | -35% |
| Kansas | $19,761,290 | 143 | $138,190.84 | $21,789,894 | -9% |
| Kentucky | $20,269,246 | 164 | $123,592.96 | $13,641,891 | +49% |
| Louisiana | $17,565,708 | 167 | $105,183.88 | $18,467,023 | -5% |
| Maine | $4,516,013 | 54 | $83,629.87 | $5,347,402 | -16% |
| Maryland | $55,021,852 | 412 | $133,548.18 | $43,217,922 | +27% |
| Massachusetts | $65,960,320 | 501 | $131,657.33 | $72,232,592 | -9% |
| Michigan | $50,623,006 | 561 | $90,237.09 | $68,721,629 | -26% |
| Minnesota | $69,732,152 | 321 | $217,234.12 | $24,935,817 | +180% |
| Mississippi | $7,399,653 | 71 | $104,220.46 | $14,672,094 | -50% |
| Missouri | $30,188,586 | 339 | $89,051.88 | $49,116,067 | -39% |
| Montana | $3,891,985 | 83 | $46,891.39 | $7,148,037 | -46% |
| Nebraska | $10,538,005 | 105 | $100,361.95 | $5,359,750 | +97% |
| Nevada | $46,004,149 | 235 | $195,762.34 | $27,786,876 | +66% |
| New Hampshire | $6,995,141 | 106 | $65,991.90 | $2,593,546 | +170% |
| New Jersey | $140,070,206 | 628 | $223,041.73 | $62,949,746 | +123% |
| New Mexico | $3,775,992 | 83 | $45,493.88 | $6,881,044 | -45% |
| New York | $216,249,339 | 1324 | $163,330.32 | $216,192,152 | +.03% |
| North Carolina | $69,988,104 | 596 | $117,429.70 | $52,718,983 | +33% |
| North Dakota | $4,692,621 | 46 | $102,013.50 | $2,720,709 | +72% |
| Ohio | $59,124,423 | 565 | $104,645.00 | $55,234,618 | +7% |
| Oklahoma | $22,651,833 | 208 | $108,903.03 | $31,445,399 | -28% |
| Oregon | $22,817,664 | 301 | $75,806.19 | $30,108,808 | -24% |
| Pennsylvania | $96,052,798 | 731 | $131,399.18 | $92,550,017 | +4% |
| Rhode Island | $14,195,616 | 62 | $228,961.55 | $8,992,082 | +58% |
| South Carolina | $30,639,826 | 384 | $79,791.21 | $46,858,072 | -35% |
| South Dakota | $5,142,217 | 40 | $128,555.42 | $2,532,512 | +103% |
| Tennessee | $49,883,412 | 368 | $135,552.75 | $46,637,795 | +7% |
| Texas | $294,849,405 | 1,917 | $153,807.72 | $260,206,398 | +13% |
| Utah | $38,595,361 | 224 | $171,300.72 | $26,231,307 | +47% |
| Vermont | $1,207,190 | 41 | $29,443.66 | $6,755,695 | -82% |
| Virginia | $63,282,523 | 600 | $105,470.87 | $56,360,110 | +12% |
| Washington | $54,603,486 | 552 | $98,919.36 | $43,920,897 | +24% |
| West Virginia | $3,687,868 | 41 | $89,948.00 | $4,268,151 | -14% |
| Wisconsin | $30,437,803 | 279 | $109,096.07 | $47,023,205 | -35% |
| Wyoming | $2,302,076 | 46 | $50,045.13 | $2,509,854 | -8% |
As far as business email compromise statistics go for 2023, this brings the total to $2,763,481,093 in reported losses for 21,116 complainants in the 50 U.S. states and Washington D.C. (i.e., the District of Columbia). Again, just as a reminder, this BEC statistic doesn’t include victims outside those 50 states and Washington D.C., so just keep that in mind.
Wondering which states faced the highest average reported losses by victim? Wonder no more:
Other U.S. Territories Also Faced BEC Scams in 2023
In its calculations, the IC3’s researchers also lumped in data from several U.S. territories. The data also counts toward that overarching $2.9 billion dollars in reported losses from BEC scams in 2023:
- American Samoa: 1 victim reported $271,000 in losses.
- Guam: 5 victims reported $76,567 in total losses (an average of $15,313.40 per victim)
- Northern Mariana Islands: (The report shows no victims reported losses, but it was still included in the list of covered territories)
- Puerto Rico: 42 victims reported $4,532,407 in total losses (an average of $107,914.45 per victim)
- U.S. Minor Outlying Islands: 5 victims reported $178,228 in total losses (an average of $35,645.60 per victim)
- U.S. Virgin Islands: 7 victims reported $2,137,025 in total losses (an average of $305,289.29 per victim)
3 Steps to Avoid Becoming a Business Email Compromise Scam Victim
Don’t want your organization to be included in the IC3’s future business email compromise statistics? We don’t blame you — that should be every company’s goal. Here are some of the ways to avoid suffering the same fate:
1. Educate Your Employees to Increase Their Cyber Awareness and Hygiene
Virtually every organization’s first line of defense is its “human firewall.” If your employees fail to recognize scam tactics or don’t practice good cyber security hygiene (e.g., following password security best practices), then you’re likely to find yourself making bad headlines.
- Teach your employees how to recognize BEC threats and spoof messages.
- Remind them to scrutinize any requests to see if they make sense. (Think critically by asking questions like “who is requesting the funds?” and “why are they requesting the transfer?)
- Provide real-world examples of BEC and phishing emails.
- Implement simulated phishing and BEC attacks to gauge your employees’ levels of awareness and ability to put into action what they’ve learned.
- Instruct them on how to set up secure passwords.
- Provide employees with access to a password management system and instruct them on how to use it securely.
You can use the results of simulated tests to make improvements to future training sessions and materials.
2. Implement Additional Layers of Security to Your Accounts
There are plenty of ways to increase the security of your accounts beyond educating your employees. There are various security tools and resources you can implement:
- PKI-based email authentication: This approach uses digital certificates (called S/MIME certificates) and public key cryptography to add cryptographic digital signatures to your emails. As an added bonus, these certificates also enable you to send encrypted emails to other S/MIME users who send you their public keys. (The easiest way to do this is to have them send a digitally signed email to you.)
- Multi-factor authentication (MFA) or single-sign on (SSO): Using one of these identity verification mechanisms makes it more challenging for bad guys to gain access to your legitimate accounts.
- DNS records for your email domain. Setting up a sender policy framework (SPF), domain keys identified mail (DKIM), and domain message authentication reporting and conformance (DMARC) records can help prevent unauthorized users from sending messages from your domain. It also gives servers reporting instructions regarding fraudulent messages they receive so you’re aware of potentially malicious activities from your domain.
- Use verified mark certificates to brand your mail. Together, VMCs and brand indicators for message identification (BIMI) enable you to display your verified brand logo in recipients’ inboxes so there’s no question about whether your emails are authentic.
You can also use log- and network-monitoring tools to keep an eye on your traffic and what IP addresses people are using to sign into your organization’s accounts.
3. Implement & Enforce Request Verification Procedures
Create documented procedures that employees must follow before they can transfer funds or respond to requests for sensitive information. A few examples of what some of these processes may look like include the following:
- Verify the emailer’s identity via an official channel. Teach employees to call the alleged employee or vendor who reached out using an official company telephone number. If the supposed caller works in the same building, instruct employees to go speak with the person face to face. Either method is a way to verify the person is authentic and not an imposter. Never use a phone number or email address provided by the person who reached out to you.
- Requiring employees to verify the request using a call-back method. Instruct employees to get authorization for any wire transfers, gift card purchases, or requests for sensitive data. Set up a specific internal phone number for employees to call for authorization.
- Teach employees to ask questions when receiving phone or video calls. We’ve talked about the dangers of generative AI technologies and how bad guys are video and audio deepfakes to carry out fraudulent wire transfer requests. Some threat actors use emails to request phone calls or video meetings where they use AI deepfakes. One way to help avoid falling for these scams is to ask questions to see if the caller responds. If they ignore your inquiries or talk over you without any acknowledgment that you’ve said something, that’s a big red flag.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)



















Be the first to comment