Password Security: What Your Organization Needs to Know
Verizon’s 2020 DBIR report indicates that more than 80% of hacking-related breaches involved brute force or lost/stolen credentials — here’s what to know to strengthen your password security
Password security is a must for everyone — businesses, organizations, and private individuals alike. Yes, I know — I can already hear the “duh” resounding in your head. But the reason we’re taking the time to write an entire article that’s dedicated to password security is because:
- Not enough people take password security seriously. You probably can think of a few people who match this description off the top of your head.
- Many people don’t know what constitutes a strong password. There are a lot of different guidelines regarding what’s a good password versus a bad password. We’re going to clarify that for you.
- There is more to effective password security than just creating strong passwords. Yes, it’s true. Using strong passwords is only one part of the equation. But there are several other important considerations and things you need to do to increase your organization’s password security effectiveness.
So, what is password security? What do strong and weak passwords look like? What are the risks associated with not having strong password security for your organization? And what other considerations are there for password security aside from creating strong passwords?
We’ll answer these questions and also go over some quick password security tips as well at the end (for those of you who don’t want to read the entire article).
Let’s hash it out.
What Is Password Security?
Password security is the combination of policies, processes, and technologies that make passwords and authentication methods more secure. It’s all about knowing how to protect passwords. A password itself is a type of memorized secret authenticator. Basically, it’s something that only you should know that allows you to authenticate yourself to third parties. Other examples of authenticators include cryptographic devices, one-time passwords or PINs, and key access cards.
But what constitutes strong password security? For a password to be considered secure, it means that it must:
- Prevent unauthorized users from gaining access to protected systems, information, and data.
- Have sufficient complexity so that it’s impractical for someone else to guess or crack.
- Be memorable enough for you not to forget (after all, what good is a password if you have to reset it continuously?) or use a password manager (which, of course, has its own risks).
- Be something that you keep secret and don’t share with anyone else.
- Must be stored securely and in a way that prevents compromise.
Although passwords weren’t introduced until the 1960s, passwords have become central to account security and overall cybersecurity for organizations and users alike. But password security accounts for more than just the password itself. It also must speak to the policies, procedures, technologies, and training that protect those passwords and the access they provide. For example:
- Creating and implementing a computer use policy and/or a BYOD policy that indicates what accounts may be accessed on which devices, requires the use of a VPN when working remotely or connecting to public Wi-Fi, etc.
- Creating and enforcing a password policy that addresses specific password creation, storage, and maintenance requirements.
- Providing training and guidance to employees to help them understand the importance of creating a secure password and following password management best practices.
Why Is Password Security Important?

Human error is a big issue, and as long as companies employ humans, that issue isn’t going away any time soon. Users are human, and humans make mistakes. (No matter what your mom told you growing up, no one is perfect.) And data from an IDC report underscores that concern.
Data from an IDC report shows that nearly two-thirds (62%) of their IT- and non-IT 2019 survey respondents indicate that user errors are the leading cyber threat to their businesses. And those employees who posed the greatest level of concern were your everyday, run-of-the-mill users — not the executives or those with any unique or special access privileges.
If users can’t remember their passwords, this results in them having to reset their passwords. The estimated costs that are associated with resetting passwords are significant at scale. Forrester Research shared years ago that the costs associated with an individual password reset come to about $70. Now, multiply that by the number of requested password resets your IT team receives per year.
Sure, you can potentially reduce costs by automating the password reset process. But you’ll still run into the issues of users creating simple passwords and sharing passwords.
What are some other key considerations when it comes to the importance of password security?
Regulatory Compliance Concerns
Compliance is an area that should be on the radar of all applicable organizations. There are multiple regulations and regulatory bodies requiring organizations to meet specific standards for identity authentication and data protection. There are also other organizations that set standards and provide guidance that companies and other organizations can follow. These include:
- The National Institute of Standards and Technologies (NIST) — a set of standards/guidelines that don’t require compliance.
- Payment Card Industry Data Security Standards (PCI DSS) — regulations that require compliance.
- General Data Protection Regulation (GDPR) — legislation that requires compliance.
Non-compliance issues can have lots of effects on a business or organization, ranging from operational impacts to financial ones. Let’s quickly go over some of these considerations.
NIST
Okay, although NIST’s guidelines are requirements for U.S. federal government-affiliated agencies and entities, they provide great recommendations and standards for other organizations to follow as well when it comes to securely storing password-related data. (No compliance required for non-fed agencies.)
Let’s consider the identity guidelines NIST published in their special publication SP 800-63B Digital Identity Guidelines. In section 5.1.1.2, which is on the topic of protecting and storing memorized secret verifiers (i.e., passwords), they recommend allowing users to paste passwords. The practice of password pasting was perceived to be a bad thing but many in the cybersecurity community viewed it as a good thing because it encouraged users to use longer passwords that are harder to remember. (Whereas if you disable password pasting, people are more likely to use shorter passwords that are easier to type.)
In that same section, NIST also shares the following guidance regarding how passwords are stored:
“Verifiers SHALL store memorized secrets in a form that is resistant to offline attacks. Memorized secrets SHALL be salted and hashed using a suitable one-way key derivation function. Key derivation functions take a password, a salt, and a cost factor as inputs then generate a password hash. Their purpose is to make each password guessing trial by an attacker who has obtained a password hash file expensive and therefore the cost of a guessing attack high or prohibitive.”
A hash is a one-way cryptographic function that’s essentially irreversible. By adding a unique salt to a password prior to hashing it, what you accomplish is creating a completely unique hash value for every password — even if users are using the same password.
Let’s say you have two users using the same password SpockR0ck$KirksSocks. (Note: don’t actually use this as your password. I’m just giving you an example here!) If you were to hash that password for user one, then you’d wind up with an identical hash digest (hash value) for user two. The way to ensure that doesn’t happen is to add a salt, which is a random and unique value. For example, a salt could be something like uSEt3hF0rceHaRRy.
Let’s take a look at how the process works for adding a salt to your password prior to hashing it in the following infographic:

So, the key takeaway here is that salting a password prior to hashing it makes cracking the password hash too costly (i.e., impractical) for cybercriminals to achieve at scale. So, this means that hash tables and rainbow table attacks don’t work on salted passwords.
Cool, good to know. And we’ll speak more to hashing and salting a little later in this article. But for now, let’s continue on with our list of compliance-related considerations.
PCI DSS
Let’s consider the Payment Card Industry Data Security Standard, or what’s known as PCI DSS. This regulation is outlined by the PCI Security Standards Council, the founding members of which include the five major credit card companies (VISA, Mastercard, American Express, Discover, and JCB International). If your organization accepts online credit card payments or handles payment card-related data, then heads up — this is for you.
PCI DSS has a total of 12 requirements that organizations and businesses that handle this type of data must adhere to. And PCI DSS compliance applies to any businesses globally that handle this type of data — it’s not just applicable to U.S. companies.
If your organization is non-compliant with any of the PCI data security requirements, then you could face significant fees. However, those fees won’t come from the council itself — instead, they’ll be imposed by the card companies themselves. And we’re not talking chump change here, either. PCI non-compliance can result in fines ranging from $5,000 to all the way up to $100,000 per month — and each individual credit card company could impose those penalties. So, the overall total may actually be higher!
A $5,000 penalty for a large corporation might seem like very little, but it could make or break small businesses. However, the specific amount of a penalty depends on a few key factors, including your organization’s size and the severity of your non-compliance. So, a large corporation would face much larger penalties than mom-and-pop businesses that are non-compliant.
Wondering why we’re talking about payment card-related data in an article on password security? Here’s why. PCI DSS requirement 8 focuses on identity and authentication. As you can imagine, this section speaks to password security.
The most recent version of the data security standard (version 3.2.1) says that the effectiveness of passwords boils down to an authentication system’s design and implementation. In particular, “how frequently password attempts can be made by an attacker, and the security methods to protect user passwords at the point of entry, during transmission, and while in storage.”
The Payment Card Industry Data Security Standard (PCI DSS) 8.2.1. says the following:
“Using strong cryptography, render all authentication credentials (such as passwords/phrases) unreadable during transmission and storage on all system components.”
This speaks to the importance of using cryptographic processes to secure data and following password storage best practices. Of course, we’ll speak more to that a bit later.
GDPR
Alright, let’s jump across the pond for a few moments and take a look at the European Union’s General Data Protection Regulation.
Passwords aren’t specifically mentioned in the GDPR. But something that is mentioned for data processors in GDPR article 28 is that they need to demonstrate “appropriate technical and organisational measures in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject.” Likewise, article 25 specifies that the controller (the person who decides what data is processed and how) must also implement such safeguards so as to protect the rights of the data subject.
So, to translate, this statement means that organizations involved in the processing of personal data of covered individuals must have certain security measures in place to protect the data they handle. Of course, implementing strong password policies and procedures would be a no-brainer for inclusion in “appropriate technical and organizational measures.” After all, using strong and unique passwords is considered a cybersecurity industry best practice.
Non-compliance with GDPR’s requirements may result in hefty administrative fines. For example, infringements of such provisions could result in “fines up to 10 000 000 EUR, or in the case of an undertaking, up to 2 % of the total worldwide annual turnover of the preceding financial year, whichever is higher.”
Other Cost Considerations
We mentioned earlier that insecure passwords and poor password management practices are associated with higher risks of phishing attacks and data breaches. Let’s just give you a few quick examples of what we meant by that:
- The adjusted average cost of BEC/EAC surpasses $1.7 billion. The FBI’s Internet Crime Complaint Center (IC3) shared in their 2019 report that the estimated average adjusted costs relating to business email compromise/email account compromise is $1,776,549,688. To put that in perspective, that’s more than the $1.5 billion in estimated costs that NOAA attributes to Tropical Storm Eta (a storm that affected residents in multiple states in the southeastern U.S.) in November 2020. Please, do yourself a favor and implement email security best practices within your organization now.
- The average cost of a data breach in the U.S. is $8.64 million. IBM and the Ponemon Institute reported in their 2020 Cost of a Data Breach Report that the U.S. leads the rest of the world in terms of having the highest average costs stemming from data breaches. Definitely not the kind of “leading” we like to do here! Considering we already mentioned that 80% of hacking-related breaches involved brute force or lost/stolen credentials (courtesy of Verizon’s 2020 DBIR report), it’s easy to recognize that poor password security is an obvious contributing factor that leads to those steep costs.
- The compromise of Twitter’s top verified user accounts in July 2020 was linked to credential compromise. A Twitter employee was the target of a social engineering attack that led to their credentials being used to target and compromise 130 verified accounts (including those owned by icons like Elon Musk, Barack Obama, Joe Biden, and Bill Gates). The goal? To scam users with fake promises of Bitcoin. New York State’s Department of Financial Services (NY DFSS) estimates losses to victims as the result of this scam are $118,000 in Bitcoin.
Examples of Weak Passwords
It’s true that bad passwords come in all shapes and sizes. But many of them tend to include a few common ingredients: commonly used words, typing patterns, common names (kids, significant others, etc.), dates of significance (such as birth dates and anniversaries), etc.
So, what are the most commonly used passwords? Here’s a list of the world’s 10 most commonly used passwords, according to CyberNews:
- 123456
- 123456789
- qwerty
- password
- 12345
- qwerty123
- 1q2w3e
- 12345678
- 111111
- 1234567890
How not only pitiful but utterly terrifying is that list? It would maybe be a little understandable if this group was a list of passwords created by preschoolers. But this list is of the 10 most common passwords for users worldwide! (And, no doubt, the preschoolers’ passwords would likely be more creative.)
So, why are people using such basic and easy-to-guess passwords? Frankly, it boils down to people allowing convenience to outweigh security. It’s a lot easier to remember a password like “123456” than it is to remember a more complex password like “X89*2nkc_1m74WeF.” But this is where making longer passphrases can be really useful. I’m sure you’d agree that creating and remembering a unique lengthy passphrase like “SunshineFLOWERSBuildGreatScents” is a lot easier than remembering “X89*2nkc_1m74WeF” while still being more secure than “123456.”
This is why using lengthy passphrases is the best of both worlds: it offers greater complexity that thwarts cybercriminals while still being easy enough for forgetful users to remember.
5 Components of Strong Password Security
What are some of the key considerations of strong passwords that can help you avoid falling prey to password cracking attacks?
1. Password Length & Complexity
Common knowledge indicates that passwords should be minimum of 12 characters, use uppercase and lowercase letters, and have some random numbers and special symbols thrown into the mix. But the long-accepted wisdom that complex passwords are more secure comes with an important little caveat: A complex password isn’t useful if you can’t remember it.
Of course, one option is to use a password manager. But there is risk associated with that depending on how well those password management organizations protect those passwords. You’re essentially putting all of your eggs in one basket, which is fine so long as the organizations take the proper steps to protect your password data. (For example, password managers shouldn’t store any of your password data on their servers (only password hashes) and all of your other data you share with them should be encrypted anyhow.)
But if password management companies don’t do what they’re supposed to do on their end in terms of providing strong password security, it leaves your passwords — and you — at risk.
This is where the idea of passphrases comes into play. The FBI’s resource Protected Voices recommends the use of passphrases over traditional passwords. Here, the emphasis is on the length of passphrases that you’ll remember instead of focusing more on the complexity of passwords you’re virtually guaranteed to forget. They’ve even taken to Twitter to address the issue of password length over complexity.
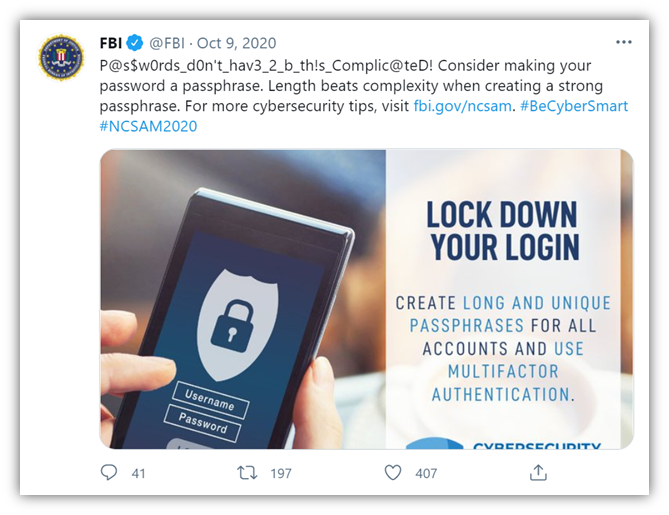
But what makes passphrases complicated enough that they’re impractical for cybercriminals to crack?
- They need to contain multiple words (ideally, at least four).
- The words should be uncommon (you can look up the most commonly used words on Oxford 3000 and 5000).
- Avoid “l33t” spellings of words (those are easy for cyberriminals to figure out by replacing letters with common numbers and symbols, like “H0use” instead of “House” or “G@m3r” instead of “Gamer”).
Check out this great video from the YouTube channel Computerphile that talks about password complexity and length:
2. Require Users to Create Unique Passwords for Every Account
People love doing what’s easy and reusing the same password over and over again is precisely that. As you know, though, recycling passwords is an obvious password security faux pas. But don’t just tell people that they need to use unique passwords — actually make them do it by implementing unique password requirements.
If a user tries to create a new password that has X% of the same alphanumeric characters, both in the same order or in reverse, block the credential change from occurring. Also, make it part of your password security policy that users must create unique passwords for every account and never share them with anyone else.
3. Keep Passwords Secure
You can also recommend using an approved password manager to help them keep all of their passwords secure. The advantage of using a password manager is that:
- It allows you to have as complex a set of passwords as you want for all of your accounts, but
- You only have to remember a single password — or what’s known as the master password.
Some people choose to keep password books. While this is better than using insecure or easy-to-guess passwords, it’s only good if you have a way to keep that book secure. (Otherwise, it’s still a major vulnerability.) This means that you want to keep is securely locked up when not in use, and you probably won’t want to bring it with you if you spend a lot of time on-the-go. Heaven forbid you forget it or accidentally leave it somewhere!
4. Using Common Password Lists to Your Advantage
Okay, so knowing that there are lists of compromised passwords available on the internet and the dark web (both for purchase and for free) really sucks. But the good news is that you can turn a negative into a positive by using those lists in a way that improves your organization’s password security.
You can use these lists as blacklists that your users cannot use when creating or updating their account passwords. It can also help you prevent password spraying attacks from being successful by preventing users from using passwords that can be found on common password lists or breached password lists.
5. Implementing Secure Password Storage Best Practices
A critical bit of knowledge is that you should never, under any circumstances, save passwords in plaintext format. Not only is it a bad practice but it also leaves you vulnerable to cyber attacks.
With this in mind, a password security best practice is to add a unique salt to each password prior to hashing it. This way, every hash value is truly unique even if separate users are using the same password. And, again, salting your hash — I mean, before you hash — is an effective way to prevent brute force attacks and rainbow table attacks.
There’s an Alternative to Traditional Password Security…
Okay, so there are a lot of things that go into having strong password security. But what if you could take one thing out of the equation that makes password security easy for users and more manageable for your IT security team? This is where passwordless security (i.e., passwordless authentication) comes into play.
Passwordless authentication is exactly what the name implies: it’s security without the use of passwords. Choosing to implement passwordless security for your organization is more liberating than going commando for kilt wearers — it makes things easy-breezy for users but doesn’t leave you at risk of accidental exposure. (We’re talking about password exposure, of course — get your mind out of the gutter.)
Now, there are a few ways you can go about rolling out passwordless authentication. One option is to use multi-factor authentication (MFA). The other is known as certificate-based authentication or PKI-based authentication.
Multi-Factor Authentication (MFA)
Multi-factor authentication offers advantages for businesses who want to make their authentication measures more secure. This type of mechanism requires you to provide two or more types of information:
- Something you know (such as a password or PIN).
- Something you have (this could be a smartphone app, a CAC card, a key or token).
- Something you are (a biometric such as a fingerprint, retinal scan, facial scan or even a voice sample).
However, it’s not bulletproof in terms of withstanding many attack methods that bad guys love to use. It’s better than using nothing, right? Eh, that may be true. But the FBI warns that cybercriminals use social engineering and technical methods to circumvent MFA protections.
But what other passwordless security options are there? One of the most effective ways to secure your account without the use of a traditional password is through the use of public key infrastructure. This is known as certificate-based authentication or PKI-based authentication.
Certificate-Based Authentication
PKI-based authentication methods are more secure than traditional MFA methods. Public key infrastructure is the foundation of internet security; it’s the framework of cryptographic technologies, systems, processes and policies that make secure communications possible via an incredibly insecure channel (i.e., the internet).
Certificate-based device authentication uses PKI digital certificates in conjunction with trusted platform modules (TPMs). The way it works is that you install a digital certificate that onto a user’s machine that ties the identity of an organization or individual to that device. This provides client authentication by having your device authenticate itself to the server without you ever having to type in a password.
The advantages of PKI-based passwordless authentication include:
- Users no longer have to create or memorize difficult passwords. Because the certificates are what authenticate users, no passwords are required.
- You don’t have to worry about improper password hash storage. Don’t want to deal with the hassle and risks associated with storing password hashes on servers? Then don’t — eliminate the risk by doing away with passwords altogether.
- Not falling prey to phishing and other credential attacks. If you’re using certificate-based authentication, you don’t have to worry about someone phishing your employees’ login credentials and passwords because they don’t have them anymore.
TL;DR: 6 Password Security Tips You Can Implement Now
As you’ve learned, password security isn’t a one-size-fits-all approach. And there are a lot of moving parts when it comes to making password-based authentication more secure. But here are a few quick tips you can use to make your password security more effective:
- Don’t share your login information with other users. This is password rule #1. Your password is your password and should never be shared with anyone else. Even if you carefully craft a strong password, it doesn’t mean that your password will remain secure if you share it with someone.
- Never recycle old passwords or use the same password across multiple accounts. A common mistake that most users make is reusing passwords on an account or across multiple accounts. The danger here is that if that password becomes compromised due to a data breach, phishing attack, or another factor, it means that any other account using that password would be at risk of compromise.
- Use lengthy passphrases instead of overly complex (and hard-to-remember) passwords. We already talked about this earlier. But to quickly recap, a lengthy passphrase is easier for users to remember than a complex password. This makes a password more effective for users who don’t rely on password managers.
- Block users from using passwords that you can find on breach lists. For the love of all that’s good in this world, stop users from using credentials that can be found on public data breach lists!
- Ensure that your organization properly stores its password hashes. There is never, ever a reason to store passwords in plaintext format. Only password hashes should be stored, and even then, those hashes should be salted prior to being hashed. This will not only make passwords resistant to brute force attacks but it makes them resistant to rainbow table attacks.
- Get rid of cumbersome and risky passwords altogether. Why leave yourself at risk when you have another more secure method of authentication (PKI-based authentication) at your disposal?





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (6 votes, average: 4.33 out of 5)
(6 votes, average: 4.33 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown