Rainbow Tables: A Path to Password Gold for Cybercriminals
While most articles on passwords focus on the user side of security, we’re going to flip the script with a look at rainbow tables. We’ll break down what they are, how they work, & how to mitigate this password security threat
Although they sound like furniture items for a certain 80s animated heroine, rainbow tables are a lot more serious than their cheerful name would imply. They’re both a threat for businesses that digitally store password hashes and an advantage to researchers and law enforcement for different reasons. Rainbow table attacks are a way for cybercriminals to use cryptanalysis to efficiently crack password hashes in password files or databases they’ve found or stolen.
But what are rainbow tables and why should you care about them? We’ll break down what a rainbow table is, how it works, and why rainbow table attacks are an issue even for businesses that hash their stored passwords. Then we’ll share with you the “kryptonite” of rainbow tables that can help you mitigate this threat.
Let’s hash it out.
What we’re hashing out…
- While most articles on passwords focus on the user side of security, we’re going to flip the script with a look at rainbow tables. We’ll break down what they are, how they work, & how to mitigate this password security threat
- What Is a Rainbow Table?
- How a Rainbow Table Attack Works (A General Overview)
- A Look at the History of Rainbow Tables
- What Is Hashing?
- Advantages of Using Rainbow Tables for Password Cracking
- How to Protect Your Stored Passwords from Cybercriminals
- Wrap Up on Rainbow Tables & Ways to Mitigate Rainbow Table Attacks
What Is a Rainbow Table?
Okay, rainbow tables make a highly complex topic to write about, so bear with me here while I try to break it down into the simplest terms possible. There are a lot of misconceptions about what rainbow tables are (and aren’t) online. They’re essentially powerful resources that enable password-breaking attempts known as rainbow table attacks.
In the most basic sense, rainbow tables are a way for cybercriminals to crack unsalted, hashed passwords via rapid cryptanalysis. (A salt is a random, unique number that you apply to a plaintext password prior to hashing and storing it to make the password more secure. But don’t worry, we’ll talk salting later in the article.) They’re large lookup database tables that can be used in cryptographic attacks known as rainbow table attacks. Each table consists of pre-computed password-hash combinations that help to uncover the plaintext version of passwords from their hashes. If this sounds like a hash table, hold on to that thought. It’s similar in the sense that it’s a password-cracking method, but it’s not the same thing.
Now, to create these password-hash combos for the rainbow tables, you first have to calculate a lot of pre-computed password-hash “chains.” These chains, which are constant in length, are created through the use of two specific functions that alternate with each section of the chain:
- One-way hash functions (which are, essentially, irreversible mathematical processes that map plaintext data to hash outputs of fixed lengths — we’ll talk more in depth about hash functions later in the article), and
- Hash reduction functions (which reduce hashes to plaintext data).
These sequential chains connect and build upon each other to form longer chains. However, the only things that may be retained are the starting point and endpoint of each chain (i.e., the first and last entry of each chain, or the password and the matching hash value). So, a chain would look something like this:
A basic illustration of how a rainbow chain looks. It consists of alternating segments of passwords, hash functions, hash values, and reduction functions. However, to create a rainbow table, you keep only the first and last values of the chain and discard the rest of the data. To crack a password hash value using a rainbow table attack, you then rebuild the intermediate data that was discarded that leads up to the hash in question.
You calculate the chain but you only retain the first and last values. Now, mind you, there could be thousands or potentially even millions of pairs that are linked in these chains. But, again you’re only saving the first and last entry of the chain. Everything else in between gets tossed like last week’s leftovers.
How Is Saving Only Part of The Work Beneficial?
Wait, if you only keep the first and last entry and delete everything in the middle, doesn’t that make the table useless? Nope — quite the contrary. It’s all about how you organize the data that makes the difference. A 2005 (ISC)2 article by Philippe Oechslin, the creator of the rainbow table, explains this a little more:
“With rainbow tables, you have to calculate the hash of all passwords, but you only store a very small fraction of them, say one in ten thousands. The trick is to organize the passwords and hashes in such an order that with the data you choose to store, you can recreate all the passwords and hashes quickly with the order of ten thousand hash operations. You thus reduce the amount of memory and increase the time of cracking, hence, time-memory trade-off.”
This storage of the first and last password and hash combination is what actually creates your rainbow table. So, you have to go through the process of creating all of the chains and organizing them so that you save just the first and last entries of each one in the table. You can rebuild the chains when you need to, which gives you back all of the missing info you’d tossed. But what this does is save you in terms of both operational time and storage.
The longer the chains are, the smaller your table is but the slower your lookup speed is, too. Likewise, the shorter the chains are, the bigger the table and the faster your lookup is as well. So, this means that if you double the size of your rainbow tables, you could quadruple your cracking speed. This is the basic concept behind the time-memory trade-off.
According to Oechslin’s 2005 article:
“For the trade-off to work, the hashes and passwords have to be organized in chains. To achieve this, you need to define a reduction function that maps a hash into a password. You can choose any function you want as long as it takes a hash as an input and generates a password as its output. Starting from a password, you can now generate a hash from the password with the hash function, and then generate a new password from this hash with the reduction function. Start over until you have a chain of ten thousand passwords and hashes.”
We’ll jump more into how rainbow tables work momentarily. But first, let’s talk about what they do and why they’re so useful for the good guys and bad guys alike.
Breaking Down What Rainbow Tables Do
Rainbow tables are useful for cybercriminals who want to crack complex passwords by using their hashes. Other methods — such as using dictionary (brute-force) attacks and hash tables — may be more useful for trying to crack more simple passwords. But they’re also significantly more time- and resource-intensive.
I reached out to Oechslin directly via email in December 2020 to ask him to share his insight about what rainbow tables are and what they do. Oechslin is the founder of Objectif Sécurité, an IT security consulting company in Switzerland. This is how he described rainbow tables in layman’s terms:
“Rainbow table[s] make it possible to do all the hard work of password cracking in advance and to store the results in a smart and compact table structure. The day you need to crack a password, you can take the rainbow tables that you (or somebody else) prepared and greatly accelerate the cracking.”
So, cybercriminals can use these tables to compare pre-computed hashes against those stored in organizations’ storage documents of password hashes (such as their system password files) that they have access to. If successful, they can use these hashes to reverse-map a password hash to gain access to the plaintext (readable) version of the original password.
So, rainbow tables are basically massive lookup tables that can crack complex passwords significantly faster than using traditional password cracking methods.
Loosely speaking, it’s kind of like how you likely learned basic multiplication in school (before Common Core Math Standards was even a twinkle in the eyes of legislators). Remember multiplication tables? You likely used one of those tables of pre-calculated values to learn how to calculate and memorize answers for basic multiplication equations. This way, you could simply recall 8×12 in your head without having to go through all of the intermediate calculations (8×2, 8×3, 8×4… and so on) in your head first.
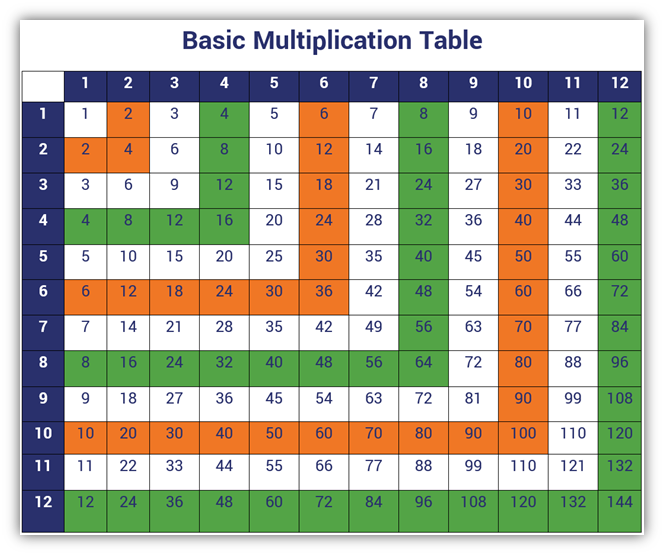
But unlike the above table, which has all of the possible combinations saved, rainbow tables would only require you to store an incredibly small percentage of them — like 10 in 100,000. This is because you’d only store the first and last passwords of each chain and throw out the rest of the chain’s data.
In some cases, cybercriminals may use multiple rainbow tables. They can do this simultaneously or use the tables sequentially (the advantage here being that sequential rainbow tables are faster).
Rainbow Tables vs Hash Tables
Now, something that tends to catch a lot of people off-kilter when they’re researching rainbow tables is the concept of hash tables. Rainbow tables are often confused with hash tables because, yes, they both involve hashing. While similar, they’re not synonymous concepts — the former is significantly more complex than the latter, and they’re used for different functions.
- Hash table — A hash table is a table that contains every possible hash that can be generated from possible passwords matching specific parameters (length, composition of characters, numbers, etc.) that are hashed via a specific hashing algorithm. This method of exhaustive search is highly time- and resource-consuming. It would take a massive amount of space to store a table with the hash value for every possible eight-character password, for example.
- Rainbow table — One or more tables of pre-computed plaintexts and matching hash values that require fewer table entries and hash calculations. Rainbow tables only store the first and last values of chain data, requiring less storage. To crack a password hash this way, you regenerate the chain data that leads up to the hash value. Therefore, rainbow cracking is faster and less resource-intensive than brute force attacks, taking only seconds or minutes to crack passwords that would otherwise take significantly more time.
So, when would you use one over the other and why? Hash tables are great very simple passwords. (For example, you might use a hash table to scan a database for passwords that match one of the top 10,000 most commonly used passwords. Rainbow tables, on the other hand, are great for trying to crack the hashes of tougher or more complex passwords.
Do Companies Often Store Passwords in the Clear?
Thankfully, no. Unfortunately, some do, and this can lead to a lot of problems (including identify theft and financial fraud) down the road. However, when sites allow people to save their passwords, typically what they’re really doing is storing the hash digests of those passwords. In that case, plaintext passwords aren’t:
- Uploaded to any databases, and
- Viewable to employees or hackers (because the hashing occurs on the backend and generates the hash digest).
Windows, for example, doesn’t store plaintext passwords in the operating system (OS) and active directory (AD). They store password hashes instead that have historically been created using one of two hashes:
- LM Hash (LanManager hash) — The older and more insecure hashing algorithm that’s vulnerable to password cracking techniques.
- NTLM Hash (NT LanManager hash) — The newer hashing algorithm that’s more resistant to password cracking techniques (but still not infallible).
Microsoft suggests disabling the storage of LM password hashes in Windows OS and server OSes. Check out this LM password hash storage prevention article from Microsoft for more on that. Spoiler alert: Microsoft’s use of LM hashes is what led to Oechslin developing rainbow tables. But we’ll talk more about all of that later in the article.
How Cybercriminals Gain Access to Password Hash Lists
You see, organizations frequently allow users to store their passwords — or, more accurately, their password hash digests — on their servers. Heck, maybe your business is one of them. The idea here is that because the passwords are cryptographically hashed — meaning that the plaintext is mapped to ciphertext of a specific length to make them unreadable — that they’re secure. But as you’ll soon learn, not everything is always so straightforward.
But how in the world would someone gain access to your list of password hashes? There are many different ways:
- You forget (or neglect) to secure your database with a password when you upload it.
- Cybercriminals could exploit vulnerabilities to gain access to your Active Directory (AD). Once in there, they can search for and extract your password hashes to create a list that they can apply password cracking techniques to.
- They can trick or manipulate users through phishing attacks to gain access to systems they’re authorized to access.
But regardless of how they get their hands on your list of hashed passwords, what we’re going to focus on here is what they do with that data once they have access to it.
If a cybercriminal manages to get their hands on your organization’s list of stored password hash digests, they could use brute force attacks or rainbow table attacks to try to crack ‘em. For the latter option, they can compare the stored list of hashes against their pre-computed rainbow table(s) to see if any matches turn up and then re-calculate the chains that lead to the password. This rapidly speeds up the password cracking process.
Why Are They Called Rainbow Tables?
“Rainbow tables” seems like an odd choice for the name of such a powerful tool, right? It’s really not once you get the idea behind it.
If you map out a rainbow table and use different colors to illustrate the different reduction functions, it’ll visually create a rainbow-like appearance. Oechslin’s original research paper displayed rainbow tables in black-and-white. However, when he presented his research at a 2003 conference, he chose to use different colors to represent different reduction functions to illustrate the meaning. This coloring method results in a rainbow-like display as shown below:
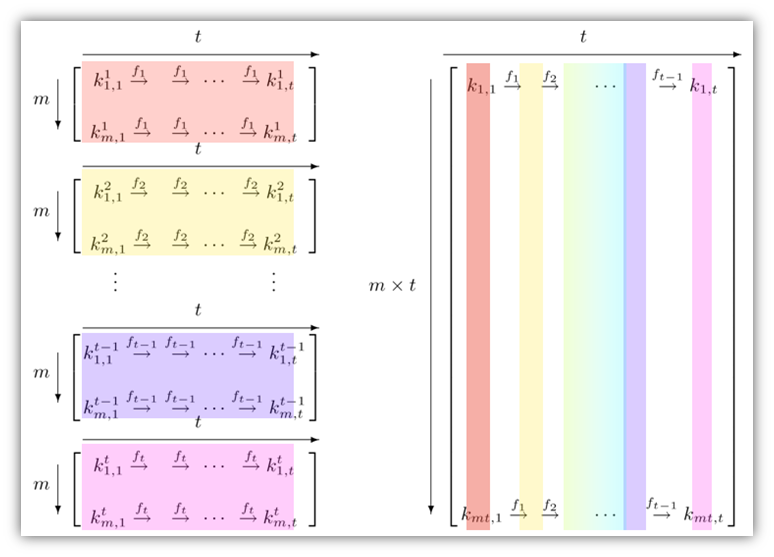
Again, if that was clear as mud — don’t worry. I’m going to break it all down for you more here in a moment. Just note that there will be some overlap between the different sections of this article, but some explanations are required to make sure that everyone is on the same page while reading this regardless of their tech-savviness.
Rainbow Table Attacks vs Brute Force Attacks
Rainbow table attacks are sometimes compared to dictionary or brute force attacks. However, they differ from brute force attacks not only in terms of efficiency but also in how their processes work in general.
Brute Force Attacks
A brute force attack is the traditional way of cracking passwords. It’s all about trying every possible permutation of a password — which can involve changing standard characters out for numbers, letters, special characters, etc. — and hashing each one individually to create an exhaustive list. Then, the attacker can then compare it to an existing list of hashes that the attacker wants to crack.
But brute-force attacks at scale are slow — prohibitively so. This type of attack takes not only a lot of time but also a massive amount of resources as well since you’re having to run through every possible permutation until you find the right combination.
Rainbow Table Attacks
You’ve already learned what rainbow tables are. But how does it work when you actually want to crack a password hash digest using your handy table (or tables)? Since you can’t calculate a hash in reverse, you instead start by calculating a chain from the hash. The idea here is that you use the rainbow table to see if any passwords that result match the ones in your table. If so, and more specifically if they’re the end of a chain, then you can calculate the chain from the beginning until you reach the desired password.
In general, rainbow tables are useful for trying to crack password hashes in the files that they already have access to. Dictionary and brute force attacks, on the other hand, are often used to gain access to the systems that house those password storage files. This process involves inputting lists of pre-guessed or stolen passwords or random letter, character, and number combinations into the web apps and seeing if any find a match.
How a Rainbow Table Attack Works (A General Overview)
Rainbow table attacks, in a nutshell, involve two specific processes on the part of the cybercriminal:
- They need to create (or download) a rainbow table — a really, really big file or database of pre-computed password-hash pairs. This involves creating all of the chains we talked about earlier to come up with the first and last values and then dump the intermediaries.
- They need to use the table to crack password hashes. This involves finding hash values in the rainbow table and recalculating the chains (and the plaintext passwords) that lead up to the hashes.
Rainbow tables are useful to cybersecurity researchers and cybercriminals alike. That’s because the former use them as a means to check security and standards effectiveness, whereas the latter use them for exploitation.
An Example of a Rainbow Tables in Action
Let’s quickly take a look at a demo of password cracking using a tool known as Ophcrack. (Oeschlin shared this link and suggested I try it out.) It’s a password cracker that was based on the concept of rainbow tables and cracks NT and LM hashes for Windows. The site says it has a 96.7%-99.9% success rate overall.
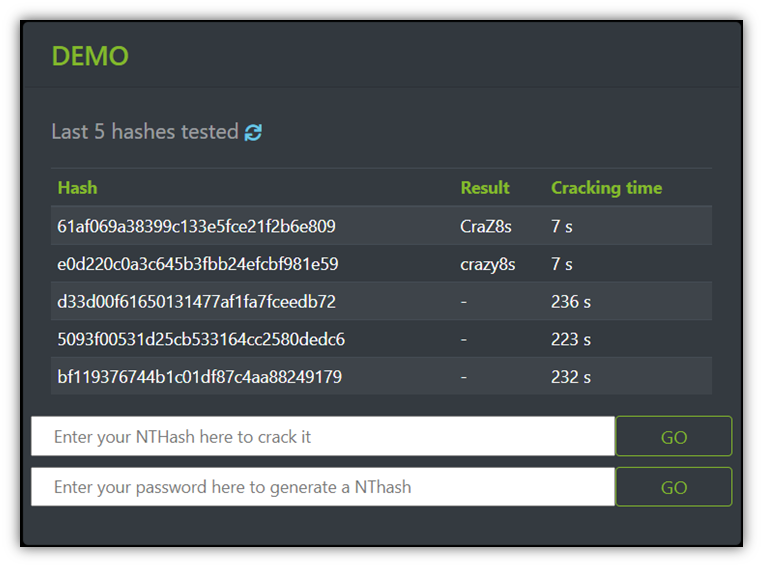
Let’s say we want to try to use Ophcrack to crack the password “crazy8s.” For the password “crazy8s,” the NTHash generator created a password hash of “e0d220c0a3c645b3fbb24efcbf981e59.” This hash digest took only seven seconds to crack using the Ophcrack password cracker. Likewise, for the password “CraZ8s,” only took seven seconds to crack as well.
Because this password was a relatively short password that used only alphanumeric characters, Ophcrack was able to easily crack it using its pre-computed rainbow tables that were set with specific parameters. If you used a longer password with special characters, on the other hand, a hacker might not be able to crack that password using this tool.
Considering that Nordpass reports the world’s most commonly used passwords in 2020 were all alphanumeric simpletons like “123456” and “senha,” then using rainbow tables to ferret out the passwords of a hash would be a cinch for virtually any cybercriminal who knows how to use one. For fun, we took the third most common password, picture1, and ran it through the Ophcrack demo. It took a grand total of 12 seconds to calculate:
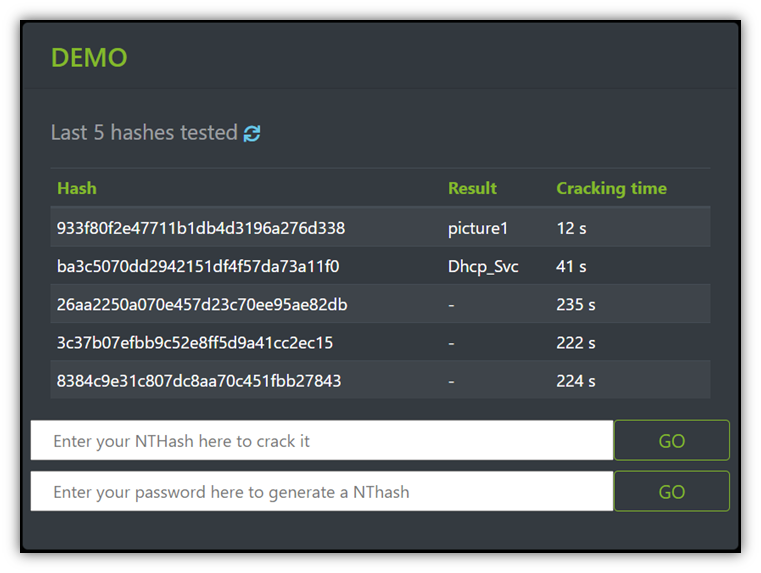
To the 371,435 users that NordPass reports as using that incredibly insecure password… You really need to put some thought and effort into creating more secure passwords that are resistant to rainbow tables and other password cracking attacks. (Try creating long and nonsensical passphrases instead — something like “Sm0keeyEyes^DontHE@R” that will afford you greater security… and no, I don’t mean to use that exact phrase. Come up with a unique one for yourself!)
Why Rainbow Attacks Are Successful Against Lists of Password Hash Values
Rainbow tables are useful for identifying matching reduced hashes in password systems that rely on weak or fast hashing algorithms (I’ll explain more about hash functions in a bit). Rainbow table attacks help cybercriminals crack hashed passwords by performing cryptanalysis with incredible speed and efficiency by relying on precomputed values.
Furthermore, while cybercriminals can opt to create their own rainbow tables, they can also choose to download precomputed tables via the internet.
A Look at the History of Rainbow Tables
Okay, these tables sound like a real nightmare for website owners and businesses. But how in the world did these things come about in the first place? We’ll need to look back several decades to paint a complete picture.
Rainbow tables were created by Oechslin back in the early 2000s. He coined the phrases “rainbow tables” and “rainbow chains” in his research paper “Making a Faster Cryptanalytic Time-Memory Trade-Off.” Oechslin’s paper reports that his creation was based on an earlier algorithm by cryptologist Martin Hellman (from the duo Diffie-Hellman) in 1980 and a variant by Ronald Rivest around 1982.
Remember the memory-time trade-off we mentioned earlier? Well, Hellman figured out a way to “trade memory” in exchange for attack time, speeding up exhaustive search-based cryptanalysis attacks. A couple of years later, Rivest’s variant introduced the concept of distinguished points, which achieved faster cryptanalysis by reducing the number of table look-ups required but used chains of inconsistent lengths.
The issue with both previous methods was twofold:
- They were resource-heavy and time-consuming processes, and
- When two chains in a single table would collide, they’d merge.
Oechslin came up with a faster solution for precomputed data generation and table look-up vehicle to serve as an alternative to Rivest’s distinguished points. According to Oechslin’s paper:
“Our optimization has the same property as the use of the distinguished points, namely that it reduces the number of table look-ups by a factor which is equal to the length of the chains. For an equivalent success rate our method reduces the number of calculations needed for cryptanalysis by a factor of two against the original method and by an even more important factor (12 in our experiment) against distinguished points.”
Furthermore, Oechslin’s paper explains that each point of a rainbow chain would use its own successive reduction function, starting with 1 and ending with t-1.
“Thus if two chains collide, they merge only if the collision appears at the same position in both chains. If the collision does not appear at the same position, both chains will continue with a different reduction function and will thus not merge.”
Why Oechslin Created Rainbow Tables
The goal of Oechslin’s experimental research was to crack the Microsoft Windows LanManager password hashes (LN Hashes) that all versions of the operating system relied upon for backward compatibility. (I told you we’d come back to this eventually.) He compared the cryptanalysis time of the classical tables (Hellman’s and Rivest’s versions) and his rainbow tables to see:
- Which method would be faster, and
- Which method would require fewer hash calculations and false alarms (which requires more processing power).
Spoiler alert: Oechslin’s rainbow table method was “about 7 times faster than the original method” in terms of cryptanalysis and had fewer false alarms. His experiment also achieved a 99.9% success rate.
Of course, generating a massive table (or set of tables) with all possible hash computations would be absurdly large. We’re talking one or more terabytes in size. So, what Oechslin did was develop a way to store less data from generated password-hash combinations and perform fewer hash calculations while using fewer resources and less time. This made his process faster and more efficient than traditional brute-force attacks. What can I say? Sometimes less really is more!
To fully understand what a rainbow table is, you also must understand what hashing is. So, if you’re already familiar with hashing, you can skip this part. But if you’re not, let’s take a few moments to break down what hashing is and how it works.
What Is Hashing?
When people think of “hashing,” there are usually a few things that come to mind. One line of thought involves a certain green pointy-leafed plant. (Hey, I’m not judging.) Another involves a tasty breakfast item that consists of a mix of beef and potato. (Also not judging that, either — heck, that stuff is delicious.) But in cryptography, hashing has a very different meaning.
In cryptography, hashing is what allows you to index and organize data more easily. It’s also a way to map data, regardless of size, to a specific length output using an algorithm. Basically, a hash is a one-way cryptographic function that validates the integrity of the data it’s applied to (meaning that it enables you to know if something’s been modified) and serves as a check-sum. This differs from encryption algorithms, which are considered two-way functions.
Hashes are often called one-way functions because they’re so challenging and impractical (though not impossible if, say, you had unlimited resources and were immortal) to reverse engineer. The reality is that it’s simply impractical for people to do because of the sheer number of resources and time the process would require. Examples of common or well-known hash algorithms include:
- SHA-1, SHA-2 (and its variants SHA-256 and SHA-512), and SHA 3 (SHA stands for secure hash algorithm, by the way)
- MD5
- TIGER
- CRC32
How Hashing Works in Password Security
So, when we talk about a hashed password, we mean that a password has had a one-way hash function applied to it. This process converts an imput of plaintext of any size into nonsensical gibberish output of a fixed length. Basically, you can change a password like “Password123” to a hash value (which is also known as a hash digest) such as “42F749ADE7F9E195BF475F37A44CAFCB.”
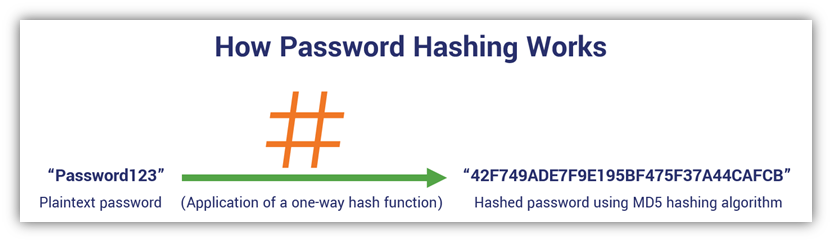
The reason you’d want to do this is because information and data are, by default, transmitted and stored in plaintext on servers and databases. This is incredibly insecure because it means that virtually anyone can access and read that data. And if this occurs with passwords — which has been the case time and again — it means that hackers could use or sell that information to commit crimes or to sell it to other cybercriminals. So, the way to prevent this is to use cryptographic methods to protect the data. This includes the use of salting, which is that random number that we mentioned earlier and will discuss more in depth momentarily.
Advantages of Using Rainbow Tables for Password Cracking
So, if you’re wondering what the benefit or advantage is of using a rainbow cracking for passwords, it’s about saving time and using fewer resources. For example, in the second edition of “11th Hour CISSP Study Guide,” authors Eric Conrad, Seth Misenar and Joshua Feldman describe the advantage of using rainbow tables as the following:
“Rainbow tables greatly speed up many types of password cracking attacks, often taking minutes to crack where other methods (such as dictionary, hybrid, and brute-force password cracking attempts) may take much longer.”
Another advantage of rainbow tables over classical tables is that their structure makes it so that:
- They have fewer false alarms than methods involving distinguished points, and
- Two chains can collide within a table without merging in many cases.
False alarms mean that you may find a chain’s matching endpoint generate more work and waste resources. Basically, it has you using your resources to try to find a matching endpoint that may not be in the table.
Chains with distinguished points that collide in a single table will end up merging. However, with columns in Oechslin’s rainbow tables, because they use separate reduction functions in each column, they’re less likely to merge. That’s because they’d need to have matching keys in identical positions within both chains for that merger to occur.
It’s clear why rainbow tables are useful for cybercriminals. But what other sorts of uses do rainbow tables have? Frankly, they have uses for both cybersecurity researchers and law enforcement. Cybersec researchers who want to identify weaknesses relating to password security processes, policies, and standards may be able to benefit from the use of rainbow tables.
And, according to Oechslin:
“Law enforcement is an example where rainbow tables are used by the good guys. They also serve as a reminder that you should always use best practices for hashing passwords. It is unfortunate that Microsoft has still not learned that lesson.”
So, now that you know what a rainbow table is, how do you make hashed passwords more secure? The answer lies in something known as salting. (Yes, we’re finally going to talk about salting now.)
How to Protect Your Stored Passwords from Cybercriminals
When it comes to password security for hashed passwords, there’s an important term to know that we mentioned but haven’t yet talked about — salting. In cryptography, a salt is a random, unique value. So, when you’re talking about salting, you’re referring to a technique that involves adding a random value to the end of a password.
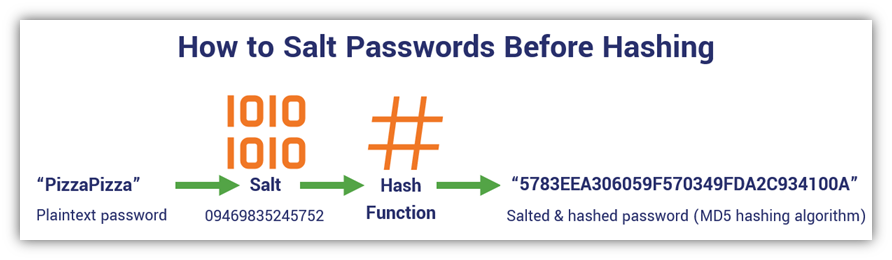
Not sure what I mean? Okay, let’s dive into this a little more with an example. Let’s say that a stored password that you wish to secure is PizzaPizza. (Yes, I know, that’s a sorry excuse for a password. But let’s just roll with it here for the sake of this example.)
When you add a salt to the end of the password — which, again, a salt is a random value such as 09469835245752 — it makes the password look something like this: PizzaPizza09469835245752.
Using the example from earlier, here’s what the process looks like when you apply salt to a password before applying a hashing algorithm:
Why You Should Salt Your Hashed Passwords
But why would someone want to salt their hashes? Because it makes them taste better. Just kidding. No, the long and the short of it is that salting makes stored passwords more secure and resistant to rainbow table attacks.
I’ll defer to Oechslin himself about the advantage of salting before hashing:
“Salting adds an unpredictable part to the password hashes. It is thus not possible to create rainbow tables in advance. If you have to generate them each time you want to crack a password, it defeats the purpose and is not faster than a simple brute force attack.”
So, by integrating salting prior to performing the hashing process, you’re creating a new and unique hash value for every password you store. This means that the hash value that will result from hashing a salted password would be different from the hash that you’d get from hashing an unsalted password. So, precomputation — the whole driving force behind using rainbow tables — then essentially gets thrown out the window because the bad guy would have to create hashes to every possible permutation of the salt values.
Another benefit is that even if multiple users have the same password, their passwords will have different hash values because they’d have different salts applied to them. (Note: this is why it’s important to apply a unique salt to each password, rather than using a site-wide salt value.) So, even if five people were using the same password of PizzaPizza, their hash values would be unique because a different salt value was applied to the password prior to hashing and storing in each case.
Guessing Salted & Hashed Passwords Is Resource Intensive
But can’t someone just guess the salt? As you just learned, a cybercriminal would need to create a precomputed table of values to reflect every possible salt value. And depending on the size of the salt used (64 bits, 128 bits, 256 bits, etc.), the number of calculations that would involve would be enormous and impractical to create, manage, or use.
So, what salting your hashed passwords does, in the most basic sense, is offer greater password security. In a more technical sense, salting the original password masks the true unsalted password (and its hash) by changing the original input. And because salts are supposed to be random unique values for each application, salting stored passwords makes hashed password tables essentially useless to cybercriminals.
That’s a win-win for you and your customers. (Not so much for cybercriminals, but why should we do anything to make their efforts easier?)
What Else You Can Do to Secure Your Passwords: Use Slow Hash Algorithms
Aside from salting before hashing, is there anything else you can do to try to make your passwords more secure? The answer lies in your choice of password hashing algorithm, Oechslin says — the slower the better.
“Other than salting the hashes, you should also make sure that your hash function is slow. Linux and MacOS make thousands of iterations of the basic hash function. This is not noticeable when you log in to you[r] machine, but [it] makes cracking thousands of times slower.
Modern hash functions are also memory hard. To be computed efficiently, they need a lot of memory. This slows down cracking attempts using graphic cards and other specialized hardware that have hundreds of processing cores but do not have hundreds of times the memory of a standard computer.”
Hash algorithms that are designed to be deliberately slow are time, money, and computer resource guzzlers. This makes trying to crack password hashes that use these algorithms both inefficient and cost-prohibitive for cybercriminals. This differs from traditional hash functions that we use for other purposes, like encrypting website connections. In those situations, we want hash algorithms to be reasonably fast while still being effective.
So, what sorts of hash algorithms should be considered? The hash algorithms that the Open Web Application Security Project (OWASP) recommends for password storage include:
- Argon algorithms (such as Argon2id).
- Bcrypt — This algorithm incorporates salting into its process.
- Password-Based Key Derivation Function 2 (PBKDF2) — This one is recommended by NIST.
Wrap Up on Rainbow Tables & Ways to Mitigate Rainbow Table Attacks
That was a lot of technical info to take in. But I hope this article has provided you with a better understanding of what rainbow tables are, how they work, and what you can do to secure your organization’s stored password hashes against rainbow table attacks. Just remember that password security is a continually changing practice. There’s no perfect way to prevent or thwart every type of password cracking attempt. Password security it’s all about just following recommended best practices and trying to at least keep up with cybercriminals (if not staying one step ahead).





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (4 votes, average: 4.25 out of 5)
(4 votes, average: 4.25 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown