A Look at 30 Key Cyber Crime Statistics [2023 Data Update]
We all know that cybercrime is on the rise. But there’s a lot more we can learn from cybercrime statistics — here are 30 cybercrime stats and practical takeaways from industry research.
Cyber crimes have been steadily increasing for several years now. We saw the skyrocketing rates during the COVID-19 pandemic, and while some types of cyber crimes have decreased in the aftermath, others have decided to shoot for the moon.
We’ve seen some big cyber crimes that have made headlines so far this year:
- U.S. Marshals Service’s computer network was offline for 10 weeks due to a ransomware attack. According to The Washington Post, the network of the Technical Operations Group (TOG), a secret branch within the agency, was targeted in the attack on Feb. 17. The agency refused to pay the ransom and had to take its systems offline. Most of the agency’s critical tools were restored within 30 days of discovering the incident. A 350 GB database allegedly containing documents and files from the Marshals Service hack was listed for sale for $150,000 in March.
- Caesars Entertainment paid a $15 million ransom in September to avoid the attacker(s) leaking sensitive customer data online. According to the casino-hotel chain’s U.S. Security and Exchange Commission (SEC) filing, the ransomware attack resulted from a social engineering attack that targeted an outsourced IT support vendor used by Caesars.
- The European Telecommunications Standards Institute (ETSI) suffered a cyber attack and subsequent data breach. The European standards organization announced the breach on Sept. 27, stating that a vulnerability exploit led to the exfiltration of a database containing information of online users. The undisclosed vulnerability has since been fixed, and ETSI has taken additional steps to strengthen its IT security procedures.
In this article, we’ll look under the hood at what constitutes cyber crime and go over the most notable cyber crime statistics trends for 2023. We’ll also dive into some of the trends and stats that experts are pointing to for 2024 and the next few years to come.
Let’s hash it out.
Cyber Crime Statistics: A Look at the Costs of Cyber Attacks, Incidents and Breaches
In the Verizon 2023 Data Breach Investigations Report (DBIR), reports that 95% of data breaches are financially driven. This was from a total of 16,312 analyzed security incidents, including 5,199 confirmed data breaches.
With this in mind, let’s look at some of the most telling cybercrime statistics when it comes to their financial consequences.
1. Cyber Crimes to Cost German Businesses €206 Billion ($224 Billion) in 2023
For the third year in a row, the German digital associate Bitkom reports damages in excess of €200 billion based on its survey of 1,000 companies. Of the respondents, 75% reported suffering digital attacks within the previous 12 months, and more than half (52%) indicated that cyber attacks threatened their businesses’ existence.
Bitkom, which is comprised of more than 2,200 companies in the digital economy, released a statement on Sept. 1 sharing that these costs were the result of a combination of different factors, including:
- Theft of data and IT equipment
- Digital surveillance, espionage, and sabotage
- Industrial surveillance, espionage, and sabotage
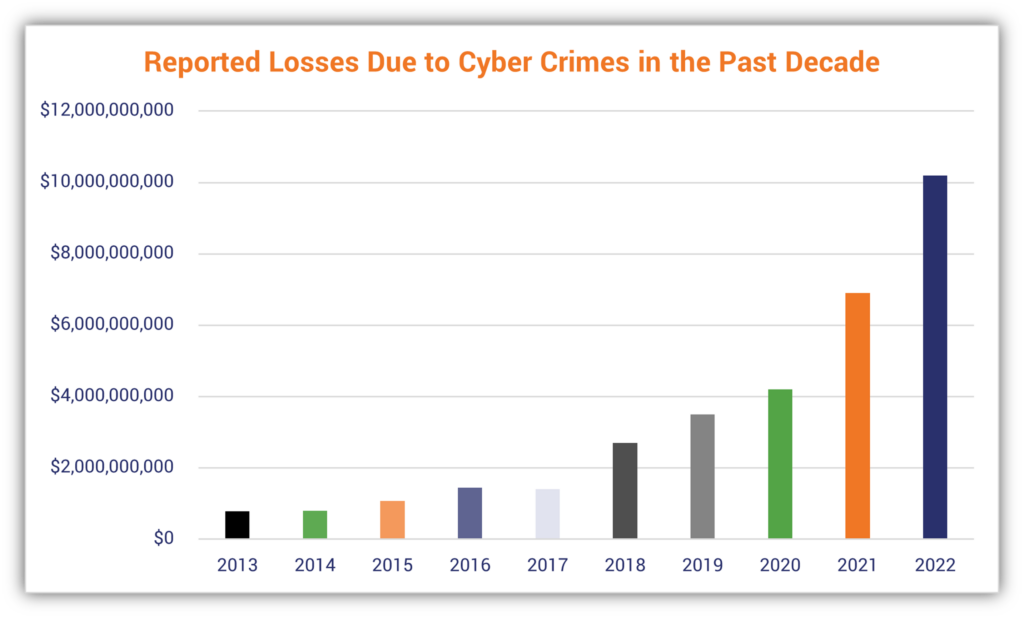
2. Cybercrime Losses Surpass $10.2 Billion in 2022
The FBI’s Internet Crime Complaint Center (IC3) reports that although cybercrime reports decreased 5% to 800,944 in 2022, the potential losses from those reported crimes exceeded $10.2 billion for the year. That’s more than double the total losses reported in 2020.
3. $9.48 Million Is the Average Resulting Cost of a Data Breach in the United States
IBM’s Cost of a Data Breach 2023 report shows that the price tag associated with these devastating situations isn’t for the faint of heart. In its report, IBM showed that the U.S.’s average cost of a data breach is $9.48 million, which is up a bit from the 2022 reported average of $9.44 million. These costs include everything from detection and escalation to post-breach responses and business losses.
So, how does the U.S. compare globally? The average cost of a data breach for businesses globally topped $4.45 million. That’s up 2.4% from $4.35 million last year (2022) and marks an increase of 15.3% over the $3.86 million IBM reported in 2020. However, the geographic region that took the hardest hit in terms of year-over-year growth in data breach costs in this year’s report was the Midde East. The average cost of which jumped more than 8% over the previous year.
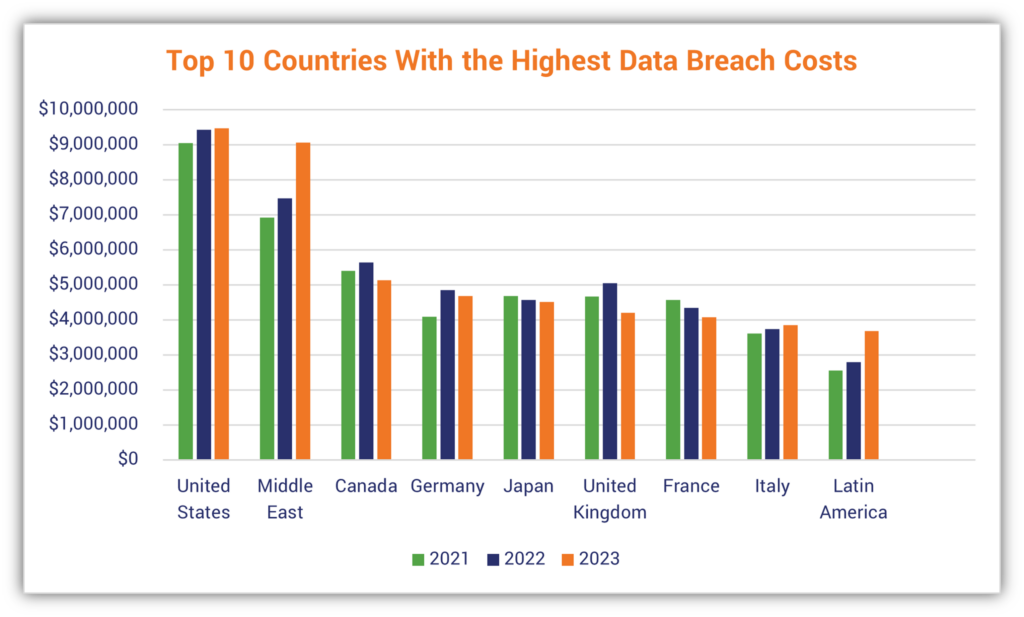
Maybe the U.S. can learn a thing or two from their sister “across the pond,” as it appears the United Kingdom is doing something right. In 2022, the U.K.’s average cost of a data breach was $5.05 million; that’s dropped more than 16% to an average of $4.21 million in 2023.
4. Data Breach Costs Are Up 21.4% For Businesses With 500-1,000 Employees
Although the cost of a data breach has decreased for organizations with 5,000 or more employees, smaller businesses aren’t so lucky. IBM’s 2023 Cost of a Data Breach report shows that they’re the ones taking the biggest hits when it comes to rising data breach costs. The estimated costs rose 21.4% for organizations with 500-1,000 employees and 13.4% for companies with fewer than 500 employees.
5. $675 Is the Average Cost of an Individual Healthcare Record
U.S. healthcare records come with heavy price tags — in this case, $675 per healthcare record, according to the 2023 ForgeRock Identity Breach Report. But what makes these records so valuable for cybercriminals? They contain a wealth of information that can be used, bartered, or sold.
This is particularly true for two critical pieces of information: victims’ social security numbers and dates of birth. These types of data are evergreen, meaning that they can be stored by cybercriminals — potentially for years — and then be used later by bad guys.
In many cases, all the bad guys have to do is wait out the (measly) credit monitoring subscriptions that the breached company will inevitably offer to affected users as compensation for their privacy being breached. Then they can run amok and use that personal data as they please — likely, without the victim realizing it until it’s too late.
Cyber Crime Statistics: A Look at the Profitability of Cybercrimes
Next on our list of cyber crime statistics, we’ll explore how much cyber crimes pay.
6. Organizations Paid $449.1 Million in Ransomware Cryptocurrency Extortions in 1H 2023
Chainalysis reports that annual ransomware cryptocurrency crimes are on the rise in 2023 and are expected to soar past 2022’s reported amounts. As of the end of June 2023, cryptocurrency-based ransomware revenue had reached a horrifying $450 million in just the first half of the year.
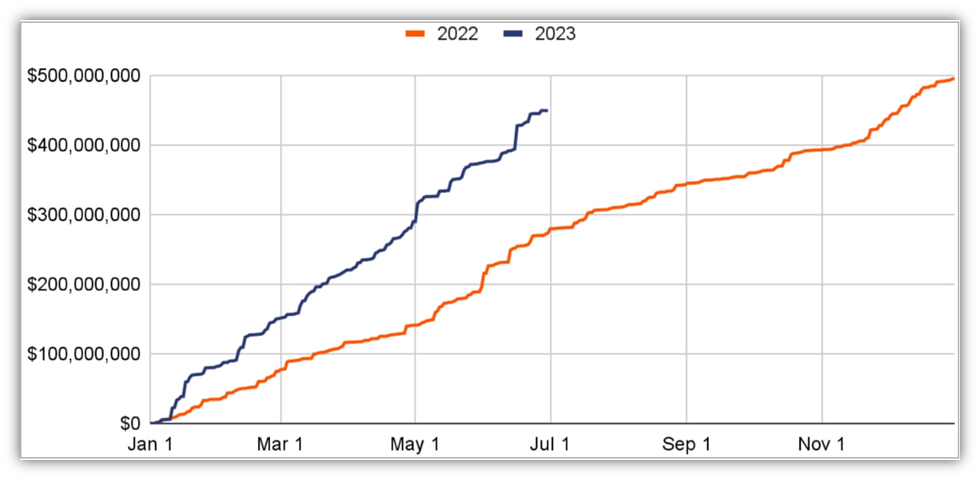
If this rate continues for the rest of the year, it means that attackers are on track to extort nearly a total of $900 million from victims in 2023. This is significantly more than the $500 million in ransomware revenues in 2022 but isn’t quite reaching the gut-wrenching highs (or lows, depending on how you look at it) of 2021, which topped $939 million.
7. Qilin Enables Their Ransomware-as-a-Service Customers to Pocket Up to 85% of Ransom Payments
Based on the numbers above, as you can imagine, Ransomware-as-a-Service (RaaS) can be a lucrative business for cybercriminals. Researchers at the cybersecurity firm Group-IB infiltrated a RaaS group called Qilin, which uses a Rust-based ransomware and customizes their attack strategies to maximize success. They discovered that the group’s ransom amounts typically range from $50,000 to $800,000.
Of course, the higher the amount a cybercriminal can get a victim to pay, the larger the payout is for the RaaS user:
- For ransom payments totaling less than $3 million, they’d allow their customers (called affiliates) to keep 80% of the pot.
- For ransom payments totaling more than $3 million, the affiliates’ earnings increase to 85%. So, on a $5 million ransom, their share is $4.25 million.
Kaspersky reports that ransomware families represent 58% of the malware-as-a-service related incidents its Digital Footprint Intelligence team has observed over the past seven years.
8. Robin Banks Charges Upwards of $300 Per Month for a Single Phishing Kit
Phishing-a-a-service (PhaaS) is another lucrative venture, both for the person rendering the services and for the customer who pays for them. The same can be said with those who create and use phishing kits. Robin Banks is one such example, as IronNet researchers have shared. These phishing kits allow social engineers to impersonate legitimate banks, other financial institutions, and even major companies like Google or T-Mobile to trick or manipulate people out of their money or credentials.
CNBC reports that one California small business owner, Chris Mullenaux, was scammed out of $120,000 by cybercriminals who used a phishing kit to impersonate Chase’s fraud department. Of course, Mullenaux is just one example of someone who was tricked or manipulated into paying out. There are likely many others whose losses haven’t been reported, and many of those victims’ phishing stories can be downright heartbreaking.
9. Cyber Crime Job Listings Offer Promises of Monthly Salaries Ranging Upwards of $20,000
Research from Kaspersky shows that cybercriminals are looking for people to work as developers, analysts, reverse engineers, or other related roles. Some job roles offer full-time or flextime work, and may even offer other tempting benefits such as paid time off (PTO) or sick leave.
Yes, you read that correctly. Cybercrime groups are headhunting and placing job listings to attract candidates, and they’re offering salaries, bonuses, and benefits that would compete with jobs at major IT companies.
If you’re reading this and thinking of tendering your resignation to go take up a life of cybercrime and make some big bucks, think again. Although they’re promised astronomical salaries, what the people who take these jobs earn is often on par with other jobs that fall within the legal realm, as stated in the report:
“Many are drawn by expectations of easy money and large financial gain. Most times, this is only an illusion. Salaries offered on the dark web are seldom significantly higher than those you can earn legally. Moreover, the level of compensation depends on your experience, talent, and willingness to invest your energy into work.”
Not to mention, you’ll face a litany of risks and would be breaking God knows how many laws… So, it’s better to just stick with a legal job and do the daily grind.
And remember, as Shakespeare wrote in The Merchant of Venice: “All that glisters is not gold.”
Cyber Crime Statistics: How Often Are These Attacks Happening (and Who Are They Affecting)?
Let’s dive into some of these cybercrime statistics to see who is being affected by cybercrimes and how often these crimes are being committed.
10. 91 People Are Victimized By Cyber Crimes Every Hour
Surfshark reports that between 2001 and 2021, the number of cyber crime victims has increased from an estimated 6 victims per hour to more than 90 in that same period. However, it’s important to point out that the number would likely be based on reported cybercrimes — that doesn’t account for cybercrimes that go unreported or undiscovered.
Of course, I wish there was more information pertaining to how they came to these conclusions, as there’s little to no information provided as to their methodology.
11. Successful Business Email Compromise Attacks Occur Nearly Every Second

The FBI’s 2022 Internet Crime Report reports that 21,832 reported BEC attacks resulted in $2.7 billion in losses in 2022. That’s the equivalent of an average of $7,397,260 per day, $308,219 every hour, or $5,136.98 per minute.
Based on the number of reports filed, our calculations show that this equates to one successful BEC attack every second. But since many BEC attacks go unreported to IC3 and other law enforcement for various reasons (shame, guilt, fear, etc.), this number is likely significantly higher.
12. The FBI IC3 Reports That 6 SIM Swapping Attacks Occur Every Day (At Least)
Imagine that you’re at work one day and, suddenly, your phone shows that it’s no longer connected to your provider’s cellular network. This is the reality for SIM swapping attack victims, many of whom suffer devastating losses as a result. The research from the FBI IC3’s Internet Crime Report for 2022 shows that 2,026 SIM swap attacks were reported in 2022. (Who knows how many more have gone unreported?)
SIM swapping is a tactic used by cybercriminals to fraudulently gain access to a target’s phone service by porting the SIM card data to a device in the criminals’ possession. Once they have control of your phone number, any accounts with multi-factor authentication (MFA) associated with that number will be vulnerable.
13. 91% of Organizations Report Experiencing One or More Cyber Incidents or Breaches
Data from Deloitte’s report 2023 Global Future of Cyber Survey 2023 shows that the number of organizations suffering at least one cyber incident or breach is high. Deloitte’s calculation shows that the number of organizations that fit within this category has increased 3% over compared to what was reported in its 2021 report. But who are these survey respondents? More than 1,000 c-suite executives and their direct reports in organizations with 1,000+ employees and $500 million in annual revenue — that’s nearly double the number of organizations surveyed for the 2021 report.
Now, let’s pause for a moment and remember an important point. What makes this number even more jarring is that it just represents the number of organizations that admit to having a cyber incident or breach. How many more won’t admit it, or worse, aren’t even aware that they’ve had an issue?
14. 36% of Americans Report Being Victimized in One or More Cybercrimes
One in three Americans have been the victims of a cyber crime, according to the joint Annual Cybersecurity Attitudes and Behaviors Report 2023 by the National Cybersecurity Alliance and CybSafe. It makes sense why 61% of U.S. survey respondents are apprehensive of becoming cybercrime victims. And data from the report shows they’re not alone in having these concerns:
“These fears of falling victim to cybercrime are felt worldwide as there was a 7% increase in the overall number of people who felt they may become victims of cybercrime compared to last year. The survey also found that half of the participants across the nations surveyed thought they were potential targets for cybercriminals, underscoring the necessity for continued efforts to bolster cybersecurity measures.”
15. 2,025 U.S. Schools, Colleges and Universities Faced Ransomware Attacks in 2022
In 2022, 89 education sector organizations and school districts were impacted by ransomware, according to Emsisoft’s The State of Ransomware in the US: Report and Statistics 2022. In that period, 44 colleges and universities and 1,981 schools were impacted. Compare this to 2021, when 88 education sector organizations and school districts (totaling 26 colleges and universities and 1,043 individual schools).
Lincoln College, a 157-year-old historically black college, was forced to close its doors permanently in May 2022. According to a post on its website home page, the decision was made due to a combination of financial and enrollment issues stemming from the COVID-19 pandemic and a December 2021 ransomware attack. The attack blocked school officials from accessing systems and records for several months.
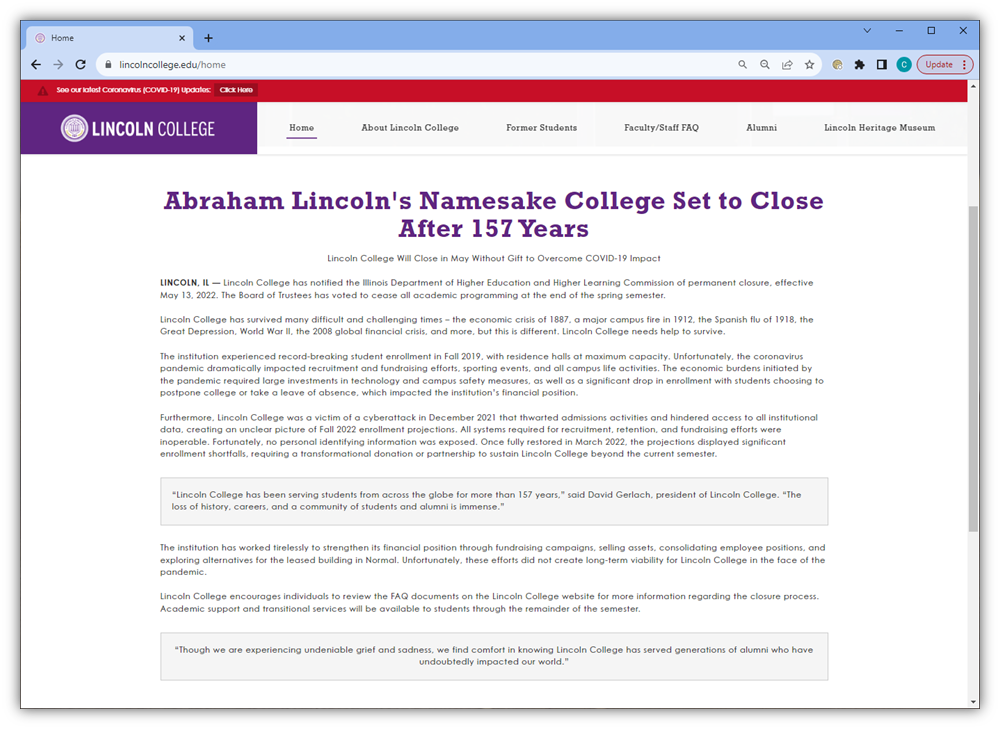
Despite paying $100,000 to recover the blocked data, the school’s needs were too great and it was forced to shutter at the end of the spring semester.
Cyber Crime Statistics: WhoDunnit? A Look at Who’s Responsible For These Cyber Incidents & Breaches
We’ve seen a whole lot of big numbers being thrown around in the last three sections. But who is responsible for many of these attacks and breaches? This section of cybercrime stats will dive into looking at the threat actors and other participants (both witting and unwitting).
16. People Are the Biggest Factor in 74% of Data Breaches
Verizon’s 2023 DBIR data shows that 74% of the data breaches they studied involved a human element. This includes a combination of external threat actors (i.e., non-employees) and internal threat actors through a variety of methods (use of stolen or compromised credentials, error, privilege misuse, or social engineering).
So, while you can take steps to improve your cyber defenses and harden your “human firewall,” there will always be risks that you can’t account for or control because of human nature.
17. 83% of Data Breaches Involved External Threat Actors
Unsurprisingly, the overwhelming majority of data breaches Verizon’s researchers analyzed for the 2023 Data Breach Investigations Report involved third-party malicious actors. This means that of the 5,199 analyzed data breaches that took place between Nov. 1, 2021 and Oct. 31, 2022, more than 4,315 of them involved external bad guys. Ugh.
This is a stark contrast to the 19% of internal threat actors the company’s research team identified, who account for not just intentional harm but “oopses” as well. This percentage is up slightly when compared to last year’s report (Verizon’s 2022 Data Breach Investigations Report), which indicated that internal threats accounted for 18% of incidents.
18. Nation-State Threats on Critical Infrastructure Increased to 40% in 2022
Microsoft’s Digital Defense Report 2022 provides data showing the threat of nation-state actors is growing. Their attacks have been largely focused on key critical infrastructure industries, including communications infrastructure, financial services, information technology (IT), and transportation systems.
In particular, IT service providers are exceptionally attractive targets for cyber crimes. Just think about the level of trust and access they have to have in their roles. As such, bad guys love to use them as a conduit through which to gain access to their downstream clients.
Research from Capterra shows that 61% of businesses have been impacted by software supply chain attacks in the past 12 months.
Between 2018 and 2022, Microsoft reports that it has delivered 67,000 nation state notifications (NSNs) to customers, informing them of nation state-related cyber threat activities.
Cyber Crime Statistics: Breaking Down How Attackers Do What They Do
Now that we have a pretty good idea of who is responsible for many cybercrimes and how much these cybercrimes wind up costing everyone, it’s time to move on to our next cybercrime stats category relating to how these attacks often occur.
19. Attacks and Breaches Targeting Third Parties Increase by Triple Digits
Although targeting one company to attack another isn’t a new cyber attack tactic, it’s one that cybercriminals love to employ because it often achieves great results. According to ForgeRock’s 2023 Identity Breach report, third-party breaches caused by stolen sensitive data rose 136% in 2022.
A couple of examples of businesses being targeted through third parties such as vendors or contractors include:
- MOVEit — Thousands of companies were affected by third-party breaches as the result of a zero-day exploit in MOVEit, a third-party vendor’s enterprise file transfer tool. Calling it “the biggest data theft of 2023,” The Verge reports that 2,000+ organizations (mostly in the U.S.) and the data of more than 62 million people have been affected.
- OpenSea API — The non-fungible token (NFT) marketplace was the target of a third-party breach incident in June 2022. The incident, which followed a phishing incident a few months earlier, involved an employee at a third-party email vendor misusing their access to steal email contact list.
20. 49% of Data Breaches Involve Stolen Credentials
Verizon’s 2023 DBIR shows that nearly half of the data breaches the company analyzed involved the use of stolen credentials. According to the report: “Credentials have really gained ground over the past five years, as the Use of stolen credentials became the most popular entry point for breaches.”
We get it. Why should bad guys want to bust their humps trying to break in the back when they can just walk through the front door instead? That’s, essentially, what they’re doing when they get their hands on one of your employees’ stolen credentials.
This threat increases when you look at web app-related attacks in particular. Verizon reports that 86% of the web application attacks they analyzed involved the use of compromised credentials.
21. 71% of Security Leaders Were the Targets of Account Takeovers
Email-based attacks can have a devastating effect on your business. According to Tessian’s State of Email Security 2022 report, 7 in 10 cyber security leaders fell prey to advanced email attacks in 2022, resulting in their credentials being compromised. Once an account has been taken over, it can be used as a platform to launch additional attacks against others and carry out additional cyber crimes. For example, an attacker can use access to your email to:
- Send phishing emails to your coworkers and direct reports
- Distribute fake invoices to customers
- Trick coworkers into sending sensitive data or sending wire transfers
- Use the credentials to access and compromise other accounts
22. The Publication of Hardcoded Secrets in GitHub Increases 67%
GitGuardian’s report The State of Secrets Sprawl 2023 paints an ugly picture when it comes to secrets management and security. The company’s latest report shows that 10 million secrets (3 million unique secrets) were published on GitHub in 2022 compared to 2021. How about the number of scanned commits? A whopping 1.027 billion between 2021 and 2022 alone.
The report indicates that one in 10 GitHub authors exposed a secret on the platform. That’s 1.35 million of the 13.3 million distinct authors who publish on the site. So, who’s the biggest offenders when it comes to these secret sprawl gaffs? India, China, and the good ol’ U.S. rank #1-3, respectively.
23. 80% of External Software Exploits Were Publicly Known But Not Mitigated
Contrary to popular belief, bad guys often aren’t trying to reinvent the wheel or discover zero-day exploits. Instead, they’re often exploiting previously disclosed attacks. Research from Arctic Wolf Labs’ State of Cybersecurity 2023 Trends report shows that in 2022, four of the five external software exploits bad guys used had been published the year before.
24. At least 75% of Ransomware Attacks and Breaches Stem From Attack Surface Exposures
Vulnerable IT environments were to blame in three-of-four ransomware attacks that PaloAlto’s Unit 42 Incident Response (IR) team handled in 2022. This is according to data from the 2023 Unit 43 Ransomware and Extortion Report.
Any guesses as to one of the most common methods of exploitation? Expired digital certificates. Yup, companies didn’t properly manage their X.509 digital certificates and found themselves paying the price.
25. Double Extortion Ransomware Attacks Increased Nearly 500% in 2021
Traditional ransomware attacks involve bad guys encrypting a target’s sensitive data and holding it ransom in exchange for payment. However, research from CipherTrace shows that many cyber attacks have upped their game and are using double extortion; in these attacks, they exfiltrate the data and threaten to publish it if the victim doesn’t pay.
What are some examples of ransomware groups that are readily embracing the double-extortion model?
- AvosLocker — This ransomware group runs a ransomware-as-a-service (RaaS) model and threatens to either publish or auction off the data online where either the victim organization or other threat actors can purchase it.
- Karakurt — This group doesn’t deny the victimized company access to their data or systems; rather, this group steals sensitive data and threatens to publish or auction it if they don’t receive payment.
- LockBit — Another RaaS, this group usually encrypts the target’s data and exfiltrates it for further exploitation. They’re known to post data of organizations that don’t play ball (i.e., pay the ransom demand) or sell the stolen data via auctions.
26. Ransomware Can Encrypt Data in as Little as 4 Minutes, 9 Seconds
Splunk, a cloud services and security solutions company, ran an experiment to measure ransomware encryption speeds. They ran a series of tests using hundreds of ransomware variants from 10 ransomware families on a test sample of 98,561 documents and files totaling 53 GB.
According to the report:
“After running all one hundred ransomware samples, we determined the total time to encrypt (TTE) varied from four minutes to three and a half hours with a median speed of 42 minutes. This narrow timeline provides a limited window for organizations to effectively respond before encryption is complete.”
Which one came in first? LockBit. Its fastest sample run clocked in at 4:09, maxing out at 396 encryptions per second; its median duration was 5:50 seconds.
| Family | Median Duration |
| LockBit | 5 minutes, 50 seconds |
| Babuk | 6 minutes, 34 seconds |
| Avaddon | 13 minutes, 15 seconds |
| Ryuk | 14 minutes, 30 seconds |
| Revil | 24 minutes, 16 seconds |
| BlackMatter | 43 minutes, three seconds |
| Darkside | 44 minutes, 52 seconds |
| Conti | 59 minutes, 34 seconds |
| Maze | 1 hour, 54 minutes, 33 seconds |
| Mespinoza (PYSA) | 1 hour, 54 minutes, 54 seconds |
| Average of the median | 42 minutes, 52 seconds |
27. Attackers’ Reliance on Cryptojacking Attacks Increased 36% in 2022
Research from SonicWall’s 2023 Cyber Threat Report shows that volume of cryptojacking increased from 78 million in 2021 to 105.9 million in 2022, with the heaviest-hitting month being December 2021. Cryptojacking is a method of cyber attack that uses devices to steal cryptocurrency.
Cyber Crime Statistics: How Organizations Respond to Attacks, Incidents & Breaches
Reading these types of cybercrime statistics is enough to make you want to reach for an antacid. But there is one glimmer of positive news that comes out of all of these nasty cyber incidents and breaches…
In July, the SEC adopted rules requiring registrants to “disclose material cybersecurity incidents they experience and to disclose on an annal basis material information regarding their cybersecurity risk management, strategy, and governance.” It’s also adopted similar rules that apply to foreign private issuers, requiring them to make “comparable disclosures.”
But what has the landscape been like previously regarding cyber incidents and breaches? How have businesses historically responded to these situations in the past year or two?
28. 72% of Respondents Admit to Not Disclosing Data Breaches
Yes, you read that right — Arctic Wolfe’s 2023 cybersecurity trends report states that seven in 10 organizations report choosing not to disclose a data breach to their customers or even their insurance providers. Why? The majority (38%) say it’s because they feared the reputational harm it would cause.
But what are some of the other reasons why businesses and other organizations would withhold that type of information?
- They’re not required by their governing laws or regulations.
- Employees worried about how it would personally impact their standing within their organization and future career opportunities.
- They wanted to avoid risking insurance policy changes.
29. 83% of Companies Victimized By Ransomware Admit to Paying Ransom Demands (At Least Once)
Oh, boy. Data from ExtraHop and Wakefield Research’s 2023 Global Cyber Confidence Index report shows that 4 in 5 organizations have paid a ransom one or more times. That number jumps to 87% when you specifically look at U.S. organizations and decreases to 76% when looking at U.K. organizations. This data is based on a survey of 950 IT decision makes in the U.S., Europe, and Asia-Pacific region.
Companies are increasingly making ransomware payments despite:
- U.S. federal agencies like the FBI advising organizations and businesses to not pay ransomware demands.
- Industry data showing that 80% of companies that choose to make ransom payments are often targeted a second time — and nearly half were reattacked by the same cybercriminals!
- The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) warning that it may impose civil penalties in response to ransom payments being made to parties subject to U.S. sanctions.
Palo Alto Unit 42 shares in its 2023 report that ransom demands in 2022 ran upwards of $50 million (per incident) and ransom payments that were made were as high as $7 million.
30. 57% of Breached Organizations Pass Those Rising Costs Along to Consumers
According to IBM’s 2023 Cost of a Data Breach report, the majority of organizations that suffer one or more data breaches report increasing the prices of their products and services as a result. Although this is down slightly over last year’s report, when 60% of organizations reported raising prices, it still sucks for when you consider the addition of growing inflation and other cost factors affecting customers and consumers.
Final Thoughts on Cybercrime Statistics in 2022
Congrats on making it the whole way through this article — we know it’s a lot to unpack. However, each of these cybercrime statistics provides valuable insight into what attackers are doing and things you can consider for improving your organization’s cyber defenses.
The truth is that no matter what you do, there’s always going to be a cybercriminal who is trying to find ways to outsmart and outmaneuver you. The best thing you can hope for is to take steps to make your organization and data as secure as possible by:
- Implementing strong cyber security policies and procedures,
- Properly managing your public key infrastructure (PKI) and digital certificates,
- Ensuring you have the right people (equipped with the right skills and knowledge) and tools in place,
- Dedicating the money and resources to securing your network, devices and applications, and
- Using encryption to keep your data secure both in rest and in transit.
This article has been updated in 2023 to reflect new industry data and cybercrime statistics. It was previously written by Casey Crane in 2021.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)




![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-698x419.jpg)








5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown