The Dirty Dozen: The 12 Most Costly Phishing Attack Examples
The list of the top phishing attacks and BEC scams and what made them so successful
Note: This article, which was originally published in 2019, has been updated to include related news & media resources.
Phishing is one of the most vicious and dangerous threats to your businesses — regardless of whether you’re a large corporation, a small business, or something in-between. The most successful phishing attack examples often involve a combination of different social engineering tactics and can involve the impersonation of CEOS or company executives, government organizations, charities, vendors, and business partners.
At some level, everyone is susceptible to phishing scams because they prey on an individual’s personal judgment, insecurities, or (in some cases) incompetence. Whether you’re a c-level executive, a celebrity, or an employee at a small business, these attacks are designed to use a variety of deceptive tactics to try to influence, manipulate, or outright trick you into performing a particular task. The goal could be to gain access to vital systems or to get you to make large wire transfers to fraudulent accounts.
Falling for business email compromise schemes that involve phishing and email spoofing are among the most costly mistakes companies around the globe make. How costly? We were wondering the same. That’s why we’ve taken the time to identify the top 12 phishing attack examples.
How did these scams occur? More importantly, what can we learn from each of these notable phishing attack examples?
Let’s hash it out.
The 12 Most Costly Phishing Attack Examples to Date (Ranked from Highest to Lowest Cost)
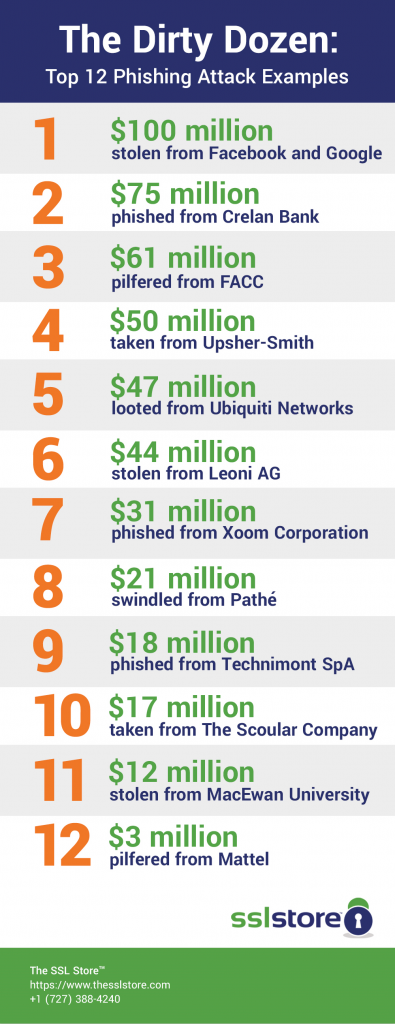
- $100 million — Facebook and Google
- $75 million — Crelan Bank
- $61 million — FACC
- $50 million — Upsher-Smith Laboratories
- $47 million — Ubiquiti Networks
- $44 million — Leoni AG
- $31 million — Xoom Corporation
- $21 million — Pathé
- $18 million — Tecnimont SpA
- $17 million — The Scoular Company
- $11.8 million — MacEwan University
- $3 million — Mattel
Breaking Down the Top 12 Most Costly Phishing Attack Examples

1. Facebook and Google
Facebook and Google, together, were scammed out of more than $100 million between 2013 and 2015 through an elaborate fake invoice scam. Yeah, that’s an insane amount of money to lose due to what ultimately boils down to an avoidable mistake. A Lithuanian hacker was able to accomplish this feat by sending each company a series of fake invoices while impersonating a large Asian-based manufacturer they used as a vendor.
2. Crelan Bank
Crelan Bank in Belgium lost $75.8 million (approximately €70 million) in a CEO fraud attack that was reportedly discovered during an internal audit. The identities of the attackers are still unknown, but the bank has implemented new security measures to prevent the attack from happening again.

3. FACC
FACC, an Austrian aerospace parts maker, lost $61 million (approximately €54 million) in a CEO fraud scam. A hacker posed as the CEO and sent a phishing email to an entry-level accounting employee who transferred funds to an account for a fake project. This kind of situation underscores the importance of having comprehensive and regular cyber security awareness training for employees. This case is a landmark in another way — the company is suing their former CEO and CFO for not doing enough to protect the company from millions in losses. In the ongoing case, the company has alleged that the two leaders “failed to set up adequate internal controls and to meet their obligations of collegial cooperation and supervision.”
4. Upsher-Smith Laboratories
Upsher-Smith Laboratories, a U.S. drug company, was swindled out of more than $50 million over the course of three weeks in 2014. The phishers, impersonating the company’s CEO, sent phishing emails to the company’s accounts payable coordinator that instructed them to make nine fraudulent wire transfers. Though they were able to recall one wire, which dropped their loss to $39 million (plus interest), they still initially transferred more than $50 million, which is why they rank fourth on our list.

5. Ubiquiti Networks
Ubiquiti Networks, a U.S. computer networking company, faced an unusual situation: The company was unaware that it had been taken for $46.7 million — nearly 10% of the company’s cash position — through CEO fraud emails and was notified of the activity by the FBI, which had been watching the company’s Hong Kong unit’s bank account.
According to the company’s quarterly financial report:
“The incident involved employee impersonation and fraudulent requests from an outside entity targeting the Company’s finance department. This fraud resulted in transfers of funds aggregating $46.7 million held by a Company subsidiary incorporated in Hong Kong to other overseas accounts held by third parties.”
6. Leoni AG
Leoni AG, a leading manufacturer of wire and cables, was scammed out of €40 million (approximately $44 million) when a finance employee in the company’s Romania office was targeted by a phishing email claiming to be from the company’s senior German executives. This situation is another one of those phishing attack examples that demonstrates the importance of training employees to identify phishing emails.
7. Xoom Corporation
Xoom Corporation, a leading electronic funds transfer provider, found itself in the crosshairs of a BEC scam that cost them nearly $31 million. In Q4 2014, the company reported a “$30.8 million business e-mail compromise (“BEC”) fraud loss” when communications involving employee impersonation and conveying fraudulent requests targeted the company’s finance department.
8. Pathé
Pathé, a European cinema chain, was scammed out of more than $21 million (approximately €19 million) when two top-level executives were targeted in an email scam. Over nearly a month, the hacker got them to transfer multiple payments while impersonating the company’s CEO. The company ultimately ended up terminating the CEO over the incident.
9. Tecnimont SpA
Tecnimont SpA, an Italian engineering, construction and procurement company, was defrauded $18.6 million through an elaborate BEC scheme. This phishing attack example involved cybercriminals sending emails to the company’s India executives and the scheduling of fake conference calls to discuss a confidential acquisition in China.
10. The Scoular Company
The Scoular Company, a commodities trading firm, was scammed out of more than $17 million in an elaborate spearphishing scam. Phishers, pretending to be the company’s CEO, sent emails to the company’s controller, instructing them to wire funds while referencing the company’s real accounting firm (though the contact information they provided was fake — the email address was from a Russian server and the Skype phone number was registered using an IP address in Israel).

11. MacEwan University
MacEwan University, an educational institution in Canada, was bilked out of nearly $11.8 million in 2017 when phishers imitated Edmonton construction companies and sent out fake invoices as part of a massive scam. The cybercriminals went as far as to create multiple websites for more than 12 construction companies in the area to collect from the real businesses’ business partners. The good news for MacEwan is that they were able to recover 92% ($10.9 million) of their stolen funds in the end.
12. Mattel
Mattel, the manufacturer that sells Barbie and other kids toys, was scammed out of $3 million through CEO fraud in 2015. However, luck was on Barbie’s side in that the phishers performed their attack the day before a bank holiday. This gave Mattel executives time to get international police and the FBI involved and, ultimately, recover their stolen funds within days of the transfer. Unlike some of the other companies on our list of phishing attack examples, Mattel enjoyed a happy ending to what could have been a very ugly cyber security story.
What Makes BEC Phishing Scams So Successful
Business email compromise and phishing scams are on the rise. The Internet Crime Complaint Center (IC3) reports “a 136% increase in identified global exposed losses” relating to BEC/email account compromise scams between December 2016 and May 2018.
What makes phishing scams so successful? They aren’t technology focused. Hackers are targeting people — they’re counting on employees responding in a frenzy to urgent emails that appear to come from their executives or vendors. “I need you to transfer $X to X account as soon as possible to avoid an important deal falling through!”
These attacks act on the idea that the employees they target aren’t likely to question an email that comes from their boss’s boss (or boss’s boss’s boss, and so on) or to double-check and verify information when they’re being told to rush. It’s not about targeting vulnerabilities in networks or security defenses; it’s about targeting you and your colleagues as people who make mistakes.
What We Can Learn from These Companies’ Phishing Scam Experiences
There is a common trait among these 12 corporate phishing attack examples: Many of the employees who received the messages simply complied with the fraudulent email requests without first verifying that the requests were valid. In the cases where the employees did try to verify whether they should perform the task, most simply responded to the fraudulent email or called the attacker(s) using the fake contact information provided in the email.
Require Verification Through Other Official Channels

If the employees in any of these situations had reached out through other official channels or methods — such as using known phone numbers from their company’s phone directory to call the person directly, contacting their assistant, or even just walk down the hall to speak with the alleged requester face to face — they could have avoided losing millions of dollars in fraud. Unfortunately, the true cost of phishing attacks often does not end with the money that was stolen — other costs include loss of revenue due to damage to the company’s image and reputation.
This concept goes hand-in-hand with our next recommendation, which would make it mandatory to follow set processes before making any financial transfers.
Implement New Processes to Increase Cyber Defenses
Another way these companies could have avoided falling prey to phishing attacks is if they had account verification and safeguard processes in place. This could entail requiring employees to follow set processes (such as performing account verification, requiring secondary and/or tertiary signatures by other personnel, and requiring phone verification, etc.) before making any transfers over a set amount — for example, $10,000. Sure, this may seem a bit inconvenient for your accounting and finance department initially, but a little inconvenience sure beats losing millions of dollars to cybercriminals.
Implement Employee Cyber Awareness Training

In addition to having the appropriate policies in place, offering comprehensive cyber security awareness training for employees likely would have prevented many of these phishing attack examples from occurring. This form of education regularly trains employees to identify and appropriately respond to phishing emails (which, in most cases, means not engaging with the email itself, informing the IT administrator, and deleting or quarantining the email). It also contributes to strengthening your organization’s “human firewall.”
Cyber security awareness training can be offered face to face or online, and periodic phishing testing should be performed to determine the success of the training or to identify areas to focus on in future trainings.
Use Email Signing Certificates
The final method of protection we’ll mention that could have prevented any (or all) of these phishing attack examples is the use of email signing certificates. Email signing certificates enable executives and other employees to digitally “sign” their emails so their recipients can easily verify that they are who they say they are. These certificates, which are issued by industry-trusted certificate authorities (CA), use an S/MIME protocol (secure/multipurpose internet mail extension) to digitally sign emails. By making the use of email signing certificates mandatory across the board, it means that if someone in the finance or accounting department receives an email that appears to come from the CEO, they can easily verify the identity of the email sender.
An added bonus is that these certificates can also be used to send secure emails using asymmetric encryption. This enables you to send an encrypted email to a recipient who has the matching private key, which protects the integrity of your data while it’s at rest and sitting in your recipient’s inbox by ensuring that no one but the intended recipient can open it. Since many email service providers use SSL/TLS to protect emails while they’re in transit, this means that you’ll be able to enjoy both data in transit and data at rest protection.
Final Thoughts
There are new business email compromise and phishing attack examples taking place at companies around the world. What this list shows is that no company is too big to fall prey to tried-and-true phishing scams. While it’s important to secure your devices and IT infrastructure to eliminate vulnerabilities, it’s just as important to also strengthen your “human firewall” through training and identity verification methods.
If you know of any noteworthy attacks that should be included on our top phishing attack examples list in the future, be sure to mention them in the comments below.
Recent Related News
Updated on April 29, 2021





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown