What You Need to Know About S/MIME
Here’s how S/MIME email signing certificates and encryption increase email security
When was the last time you sent a handwritten message? If you’re like most Americans, it has likely been a while (except maybe for sending the occasional holiday or birthday card). That’s because email has become such an integral part of our personal and professional lives. According to research from The Radicati Group, Inc., the number of business and consumer emails sent and received per day is forecast to surpass 392 billion by the end of 2026. This is up from the 333+ billion emails sent/received in 2022 alone.
However, although emails are widely used, they are not always safe nor secure. In fact, Verizon reports that 92% of malware is delivered via email. Unfortunately, traditional email client filters can’t identify all spam or phishing emails and sometimes allow them to slip through their defenses to users’ inboxes. Another second area of concern is that spoofing is undeniably easy to accomplish through simple PHP code — meaning that someone could send an email so that appears to come from another sender. A third significant concern is that most emails are sent in plaintext, meaning that the content can be “read” by unintended third parties.
How S/MIME Addresses Security Vulnerabilities in Email
With these concerns in mind, companies that handle sensitive or confidential information via email need to have protections in place to encrypt that data when it is sent to a web server from a web browser or email platform (or vice versa). One country, Denmark, is now even mandating that email encryption be used for messages containing sensitive types of personal information. According to the government’s official statement (translated from Danish):
“… the Data Protection Authority has decided to sharpen its practice with regard to the transmission of confidential and sensitive personal data by e-mail in the private sector. In the future, it will thus be the Data Inspectorate’s opinion that it will normally be an appropriate security measure – for both public and private actors – to use encryption when transmitting confidential and sensitive personal data with e-mail via the Internet.”
For some, the go-to solution for this challenge has been the use of S/MIME certificates, or what are known as email signing certificates. What is there to know about S/MIME? In reality, a lot.
Let’s hash it out.
What is S/MIME?
If you’re wondering “what is S MIME,” then you’ve come to the right place. This acronym, which stands for “secure multipurpose internet mail extension” or “secure/multipurpose internet mail extension,” refers to an email signing protocol that is used to increase email security. The way that S/MIME certs work is that they enable users to 1) prove the actual sender of an email through a timestamped digital signature, and 2) encrypt and decrypt the content of their emails, and 3) facilitate secure document sharing across networks by ensuring file integrity. This means that these certificates also double as document signing certificates in some cases by signing and encrypting files before they are sent via email.
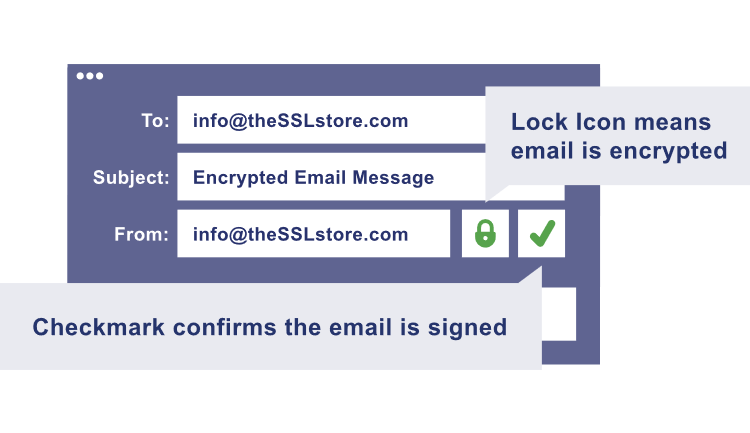
But how do you know that your emails are secure? As shown in the accompanying graphic, you’ll see a security indicator in the form of a lock icon that communicates when an email is encrypted and secure, and a checkmark that verifies if the email was digitally signed.
Think back to the mention about hand-written letters at the beginning of the article. If you’ve written a letter, signed it, and sent it to a friend or loved one, they’re likely to recognize your handwriting and trust that it’s you without you having to deliver the letter personally. This is the same concept as S/MIME, which uses a public key encryption to automatically encrypt and decrypt email content and attachments and uses a timestamped digital signature that shows you are who you say you are.
The way the digital signature works is as follows:
- A digital signature is generated using a private key and authenticated using a public key.
- The public key is sent with the S/MIME protected email — this verifies your identity when the recipient opens the email
- Your private key applies your unique digital signature to each email and repeats the process.
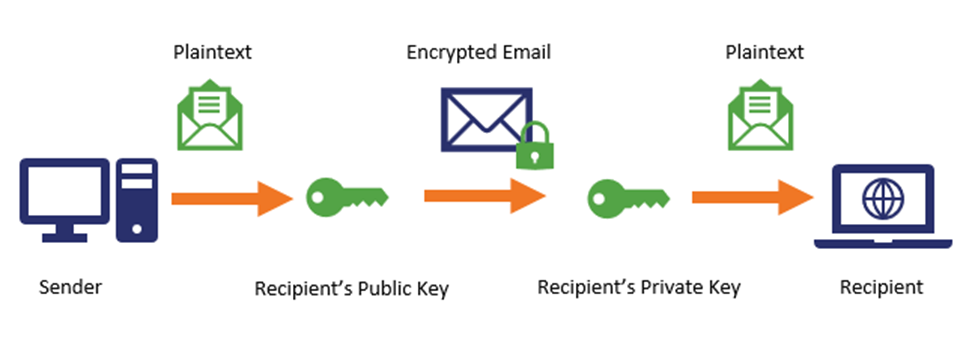
The second component of S/MIME (encryption) entails that your email data — MIME data — is encrypted before it transmits from point A to point B (to/from a web server and email client).

This encryption is done using a public key and the content of the message is then decrypted using the recipient’s corresponding private key. This at-rest and in-transit data protection helps prevent the messages from being “read” by people other than the intended recipients by keeping the emails secure until the intended recipient with the private key decrypts it.
S/MIME is one of three main types of encryption that are relevant to email:
- Secure/multipurpose internet mail extension
- Transport Layer Security (TLS)
- Pretty Good Privacy (PGP)
Will discuss the other two more in a bit.
S/MIME Support
While reading all of this, you may be wondering “does my email client support S/MIME?”
Some of the popular desktop and mobile email clients that support S/MIME include:
- Apple Mail
- CipherMail (for Android mobile devices)
- Gmail (G Suite Enterprise and G Suite for Education)
- IBM Notes
- iPhone iOS Mail
- MailMate
- Microsoft Outlook and Outlook on the Web (formerly Outlook Web App)
- Mozilla Thunderbird
Although S/MIME is supported by many email clients, it has not been widely implemented. Historically, it has been used by primarily by highly confidential government types and technology geeks because it was too cumbersome to for general users to implement. Part of this is due to the fact that both the sender and the recipient need to have S/MIME certificates to encrypt and decrypt one another’s messages using public and private keys. However, S/MIME adoption is increasing due to automated tools for implementing and managing the certificates, and the pros of using S/MIME outweigh the cons in that S/MIME protects your in-transit and at-rest data. This helps your organization:
- Mitigate susceptibility to man-in-the-middle (MitM) attacks;
- Prevent email spoofing;
- Prevent business email compromise (BEC) scams by preventing attackers from reading your email content; and
- Comply with regulatory compliance concerns that are outlined by General Data Protection Regulation (GDPR), Payment Card Industry (PCI) standards, Healthcare Insurance Portability and Accountability Act (HIPAA), and the U.S. Department of Defense’s Defense Acquisition Regulation Systems (DFARS).
S/MIME Validation Levels
Do you know that there are different validation levels or “classes” of certificates? Yeah, it’s a bit of a Wild West out there with no one accepted industry standard accepted by all certificate authorities (CAs). What you see from CA to CA varies and is based on their proprietary judgment.
Depending on the email security needs of your organization, here is how some levels of validation for S/MIME certificates can look:
- Email validation — This process requires a valid email address and domain verification.
- Individual validation — This process aims to identify you individually as an employee. This requires your government-issued identification card (such as a driver’s license) and a valid company email address to issue an email signing certificate with your name on it.
- Organization validation — This process aims to verify that an organization is valid. It involves a phone call to your organization’s representative and verification of the existence of the organization, as well as its email domain, to issue a cert that indicates the name of the company. In this way, the process of getting an organizational validation S/MIME certificate is reminiscent of an organizational validation (OV) SSL certificate.
What Other Types of Encryption Are Used For Email?
While S/MIME is the main focus of this article, I’d be remiss to not mention that there are other types of email encryption available on the market.
TLS
Transport layer security encryption is useful in many applications for protecting data as it moves from server to server. In the form of TLS certificates, this encryption method is often used for securing content shared between an end user’s web browser and a website’s server through an encrypted channel. Similarly, for email, TLS is used to create an encrypted communication tunnel through which emails are sent. However, an issue with using TLS alone for email encryption is that it does not protect at-rest data, meaning that any emails you have sitting on a computer or on an email server are still vulnerable.
PGP
Pretty good privacy (a very convincing moniker, we agree) is a quasi-collection of algorithms that are used for public and private key cryptography, as well as data compression and hashing. This can be used to secure email communications as well as other uses such as encrypting directories and files. Like S/MIME, PGP is used to encrypt email content and files. However, once viewed as a secure method of encryption, a PGP vulnerability (ironically called EFAIL) came to light in 2018 that showed that many implementations of “pretty good privacy” were not good enough. This security concern is in addition to the issues some users have with PGP’s clunky and cumbersome configuration process that makes PGP-encrypted emails difficult to work with for most users.
I only mention these other types of email encryption to show examples of the different types of encryption that are available and highlight some of the vulnerabilities they may create for your business. With S/MIME encryption, your business can use their existing email clients, whereas other solutions often require the use of their specific web portals or even separate email applications. There is something to be said for use of use, convenience, and experience.
How an S/MIME Benefits Your Business
Through encryption and the use of digital signatures, S/MIME helps to protect users from email-related cyber attacks such as phishing, spear-phishing, CEO fraud, “whaling,” and more. S/MIME email signing certificates prevent malicious users from “eavesdropping” on your email communications — even if they are actively “listening,” your plaintext communications will still be indecipherable because of the encryption.
Why should you care about data encryption through S/MIME? Because your customers care about data privacy — a lot. According to research from SAS on 525 adult U.S. consumers:
“Almost three-fourths (73 percent) of survey participants said they are more concerned about their data privacy now than they were a few years ago. And 64 percent said they feel their data is less secure today than it was a few years ago.”

Research shows that hospital employees open one in seven phishing emails. This vulnerability means that more than 14% of all emails hospital employees engage with could potentially result in a cyber attack or data breach. A healthcare data breach, in turn, often results in major complications concerning Healthcare Insurance Portability and Accountability Act (HIPAA) privacy violations, significant financial costs and compliance fines, and the loss of trust of patients.
However, these types of email security risks are not limited to only healthcare environments. ProofPoint research indicates that 83% of surveyed global info sec professionals reported experiencing phishing attacks in 2018. In a time when phishing is the leading cause of cyber security attacks, it’s imperative that businesses implement email protection mechanisms to help keep their email accounts — and their businesses as a whole — secure.
How You Can Send Encrypted Email
Some companies and individuals opt to use secure email service providers, such as ProtonMail, to send secure emails. ProtonMail uses end-to-end encryption to enable users to send free encrypted digital messages through their email service. However, a drawback of end-to-end encryption is that for it to work, both the sender and recipient must have ProtonMail accounts. This limits the usability of the email platform for your business.
Also, many secure email service solutions are not perfect and are still susceptible to attacks. A prime example is VFEmail, a U.S.-based secure email service which had been in operation for nearly 20 years when the company sustained a catastrophic cyber attack. The attackers virtually destroyed their servers and data backups, leaving the company in shambles and unable to recover. Even ProtonMail was targeted in a 2015 attack campaign on email services and a DDOS attack in 2018, although they said they were ultimately able to repel the attacks.
Companies who want to digitally sign and send encrypted emails via their existing email platforms can do so by implementing S/MIME, which the IETF (Internet Engineering Task Force) considers a standard for public key encryption. Even the National Institute of Standards and Technology (NIST) has updated their recommendations concerning the use of S/MIME and considers it a “recommended protocol for email end-to-end authentication and confidentiality.”
How to Implement S/MIME
Hands down, the greatest challenge of S/MIME is its deployment. We’ve written extensively about how you can implement S/MIME certificates on different platforms including Outlook for Apple and Windows platforms. However, depending on the service provider and solution, S/MIME implementation can still be a time-consuming process that requires a station-by-station rollout. This is, in part, because S/MIME email signing certificates need to be installed manually on every individual device.
The task of downloading and installing S/MIME certificates can be performed by an IT pro or by end-users. However, this can result in an assortment of issues. Not to mention the hassle and cost of managing all of the certificates and keys once they are installed… these are the types of scenarios that gives many IT professionals, CISOs, and CFOs nightmares.
Luckily, as we’ve also mentioned before, S/MIME implementation has come a long way in recent years. For example, Sectigo has helped to eliminate this challenge by creating a zero-touch S/MIME solution. This zero-touch solution works by integrating with your Active Directory. This allows you or your IT pros to manage everything from one interface rather than manually repeating, implementing, and managing the process on individual devices. However, for people using other forms of S/MIME certificates, they must continue to slog through the tedious manual certificate installation process.
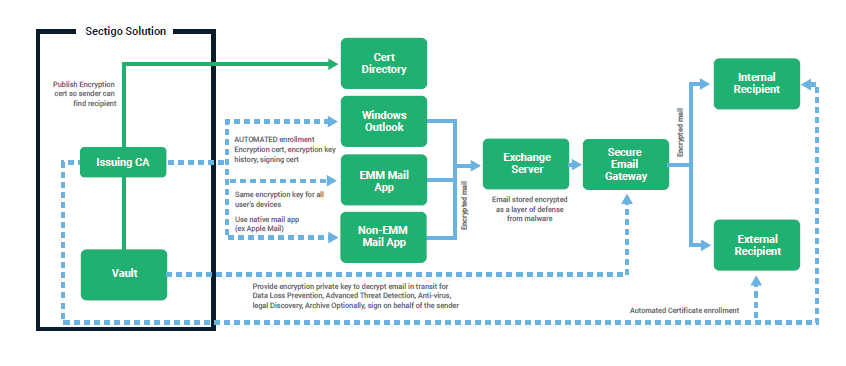
Manage Your Email Certificate Keys (and Other Certificates) Easily and Efficiently
A report from NCipher and the Ponemon Institute shows that “end user encryption keys (e.g., email, full disk encryption)” are among the most difficult types of keys to manage. Those ranked more difficult include SSL/TLS certificates, signing keys (code signing and digital signing), SSH keys, and external cloud or hosted services keys (including BYOK). This is one of several reasons why companies opt to use key management solutions.
Using an automated certificate manager that incorporates the management of S/MIME certs and encryption keys into its capabilities in lieu of a manual manager helps to further consolidate the digital certificate management process. Automation helps to ensure that certificates are renewed before expiring, that renewed certs are implemented on each device, and private key histories are up to date.
This could help save your business significant money in the future — potentially millions of dollars if you consider the fines and other costs that result from unplanned outages from certificate expiry, noncompliance, and certificate and/or key misuse.
Final Thoughts
If you implement S/MIME using a reliable certificate manager across your organization, you’ll be able to breathe a sigh of relief knowing that you’ll never again have to wonder whether your messages are secure when you are using a secure email solution. You’ll know with confidence that your identity (or that of your organization) has been verified, that your messages are encrypted, and that the integrity of your attachments is protected.
Have you implemented secure/multipurpose internet mail extensions on your email clients and devices? As always, be sure to share your thoughts and perspective on the topic in the comments below.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown