VFEmail: Secure email service loses EVERYTHING following hack
Apparently, some hackers just want to see the world burn
VFEmail was a US-based secure email service with nearly 20 years under its belt. That all ended on Monday when it suffered a massive hack that wiped out everything. Literally, everything. The servers. The backup servers. Every. Single. File.
All gone.
A couple days later, there doesn’t seem to be much to go on in the way of suspects, and the motives behind such an attack are still murky. But for all intents and purposes, a company has been destroyed. This is the nuclear scenario for most businesses.
So, today we’ll cover what happened and what if anything VFEmail could have done. Then we’ll finish by delving into why this kind of attack is more of an outlier – likely an act of personal malice – than our standard cybercrime fare.
Let’s hash it out.
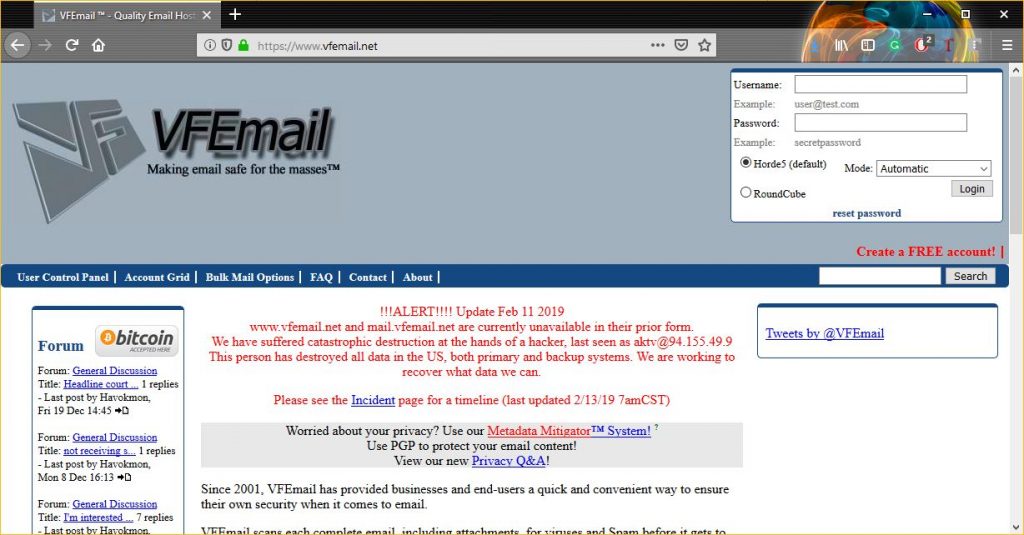
How do you lose EVERYTHING?
VFEmail was created in 2001 by Rick Romero. It discovered it was under attack on Monday when all of its servers went down simultaneously. The company’s twitter feed serves as a time-stamped outline of events. Frankly, your heart goes out to everyone involved, you can gain a sense of the desperation and panic that began to take hold as things progressed.
For almost any company, this is akin to the nightmare scenario. Everything was lost.
The attack was described by VFEmail as “catastrophic.” The attackers were finally caught formatting one of the backup servers two hours after the attack had begun, but by that point it was too late. Everything had been lost and is now seemingly beyond recovery.
Later, on Twitter, Romero didn’t mince words about VFEmail’s future prospects.
Yes, @VFEmail is effectively gone. It will likely not return.
— Havokmon (@Havokmon) February 12, 2019
I never thought anyone would care about my labor of love so much that they'd want to completely and thoroughly destroy it.
This is not the first time VFEmail has been attacked, it was also the victim of a 2015 campaign that targeted a number of mail services, including Protonmail. That attack was carried out by the Armada Collective, who DDoSed it after VFEmail refused to pay a ransom.
This one was far worse. There’s not much to go on with regard to the perpetrator, either. VFEmail’s website mentions an IP address 94[.]155[.]49[.]9 and the username “aktv,” which appear to originate from Bulgaria.
Per the Hacker News:
Romero believes the hacker behind the above-mentioned IP address most likely used a virtual machine and multiple means of access onto the VFEmail infrastructure to carry out the attack, and as a result, no method of protection, such as 2-factor authentication, would have protected VFEmail from the intrusion.
This kind of attack is an outlier, but still a scary one
There’s a quote from the great Michael Caine, playing Alfred Pennyworth in the Dark Knight, where he describes the MO of the Joker.
“…some men aren’t looking for anything logical, like money. They can’t be bought, bullied, reasoned, or negotiated with. Some men just want to watch the world burn.”
Alfred Pennyworth
That’s actually incredibly apropos of this situation, too.
Most cybercrime, like most crime in general, is done to achieve some kind of material benefit – generally money. Typically, the only reason an attacker would want to go through all of the trouble of hacking or breaching a company’s network is to somehow profit off it. It needs to be worth the time.
It needs to be profitable.
Cybercrime is a $1.5-trillion industry.
So hacking an email service just so you can completely wipe everything from its servers is a bit… counter-intuitive. What’s the payoff? What was gained?
That’s why it seems so likely this was the result of some kind of personal vendetta. At least, Occam’s razor would dictate so. From there, it gets even more conspiratorial and it’s probably not worth entertaining more outlandish hypotheticals until some more information comes out.
But suffice it to say this is an extremely unusual attack because whoever pulled it off doesn’t appear to have gained anything aside from whatever satisfaction may have come from wiping out a 20 year-old business.
This entire situation is bizarre. Hopefully we’ll get some more information soon.
In the meantime, if you’re using VFEmail you should have some extra space in your inbox.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown