Report it Right: AMCA got hacked – Not Quest and LabCorp
This is just one more example of the way the media mucks up cybersecurity coverage
Chances are, if you’ve had blood drawn in the US recently and didn’t pay your bills on time – your information has been compromised. Over the past couple of days both Quest Diagnostics and LabCorp, the two biggest US medical testing companies, have gone public with news of a third-party breach that will affect nearly 20 million customers (12-million for Quest, 7.7-million for LabCorp).
Here’s the thing though: neither of those two companies were actually the ones that messed up – the American Medical Collection Agency was. And frankly, the AMCA should be the one getting pilloried in the news headlines right now.
This is indicative of a greater problem with the way the media covers cybersecurity though. Which is to say, poorly. That’s likely a result of a general lack of understanding on the part of the people reporting it. But it’s also unacceptable because it can give false impressions and actually even end up harming security.
So, today we’re going to talk about the AMCA Data Breach, the way the media covers cybersecurity issues and what needs to be done to fix it.
Let’s hash it out.
Let’s place the blame where it’s due: AMCA
Let’s start with what actually happened before we begin dissecting the coverage of it. AMCA got breached. The American Medical Collection Agency is a debt collection service. When you go get a medical procedure done – not just bloodwork, really anything billable – and you don’t pay on time, it gets sent to the AMCA (or a company of its ilk). According to its website, the AMCA is:
“…the leading recovery agency for patient collections…and one of the nation’s top high volume lower balance agencies, managing over $1 billion in annual receivables for a diverse client base.”
I’m not going to wax poetic about the morally bankrupt practices of the collections industry or provide anecdotal evidence of all the scummy ways they go after people. For all I know the AMCA is nothing like that. The Better Business Bureau gives them a rating of D-, but hey at least it’s not an F.
Regardless of your feelings about the business it conducts though, the AMCA should be the company that’s wearing this one. It got breached and it didn’t even know it.
“We are investigating a data incident involving an unauthorized user accessing the American Medical Collection Agency system. Upon receiving information from a security compliance firm that works with credit card companies of a possible security compromise, we conducted an internal review, and then took down our web payments page,” a spokesperson for AMCA said.
But that’s not how this is being covered. Nearly every single headline mentions either Quest or LabCorp. There’s a reason for that. HIPAA guidelines require both of these organizations to report this data breach, even though it happened to a partner and not them directly.
This would be a good time to mention that under the GDPR, HIPAA and a number of other regulations and laws – you also have some culpability when your partners screw up, even if you weren’t directly responsible. This is why it’s important to have Data Processing Agreements and other similar mechanisms in place to help limit legal liability.
But, as we’re seeing, even if you follow the letter of the law, your partners’ mistakes can end up hurting you way more than it hurts them. The AMCA isn’t being singled out for this. Its reputation isn’t taking as much of a hit as the two medical testing companies’ are.
And this is only going to get worse, because the AMCA has other DBAs, such as “Retrieval-Masters Credit Bureau” (BBB: F rating… welp) and “American Traffic Solutions,” (not BBB accredited). It has clients well beyond just the medical industry. But given the status quo, as more and more of the affected companies are notified and come forward, it will be their names in the headlines – not AMCA’s.
But make no mistake about it, this is on the AMCA.

We have to do a better job reporting on data breaches
I started out my career as a newspaper reporter. I know what it’s like to work a beat, I know what it feels like to get tossed on a story you know nothing about – I get it. It’s not an easy job and the media is too reviled in this country. Having said that, there needs to be a higher standard for cybersecurity coverage.
And this is not isolated to just this incident. Take, for instance, the news last week that Checkers and Rally’s had been breached and millions of people could potentially have their financial information compromised. Go Google that real quick.
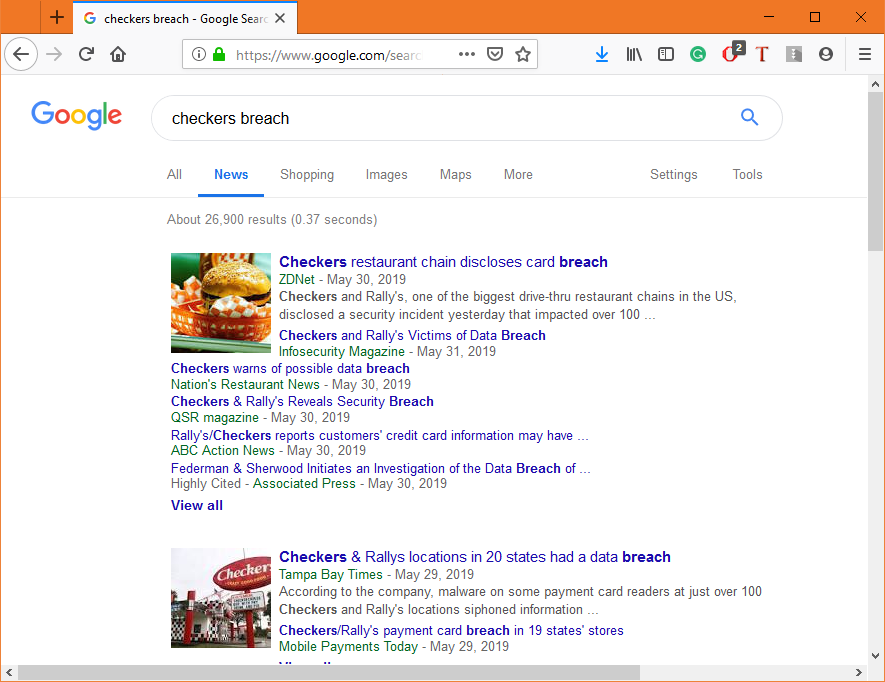
Look at the headlines. You may be asking, “what’s wrong with that?” The problem is that it seems to misunderstand the way people consume this kind of news, and just news in general. Headlines have never been more important than they are in the digital age, where people are bombarded by media from all angles.
Many people only read the headlines. Trust me, outside of the cybersecurity community most people aren’t going to click on a link to read about a data breach at Checkers. I see the traffic for Hashed Out every Monday and stories about data breaches aren’t what move the needle. Add in that we’ve all kind of become numb to the term “data breach,” and it’s apparent these headlines aren’t accomplishing what they need to be.
In this case “Data Breach” is too vague. You see a couple of headlines that mention the number of locations or that it was a card breach, which is closer to where it needs to be, but only one outlet actually got it right: ThreatPost.
Even if someone just skims the headlines, this at least paints a clearer picture of what’s happened. If they’re concerned, they may actually click and find out what “POS Malware” actually is. This is useful. But just throwing it under the catch-all term “data breach” is at best inefficient and at worst downright lazy.
People need a clearer idea about whether this affects them. The headline is your best chance to do that.
Now let’s turn back to the AMCA data breach
Once again the headlines are failing to capture the reality of the situation. This was not a LabCorp breach, this was not a Quest breach – this was an AMCA breach. Failing to mention that, or at least say that it was a third-party breach is frankly a disservice to these companies as they practice responsible disclosure of what was affected.

And while that’s bad for the individual companies, it’s worse for the cybersecurity ecosystem. We need companies to come forward with disclosures when one of their partners messes up and data is compromised. We’ve tried to legislate that with varying degrees of success but at the end of the day, many companies are still loathe to do that.
A study by nCipher that came out just last week found that 71% of UK C-Suite executives would be willing to cover up a data breach if they could escape the penalties.
Now, what about the way this news is being presented would ever make a company want to willingly admit to something like this? Because right now, the average internet user that sees any of these headlines thinks it was Quest or LabCorp – or any of the other companies that will likely make announcements in the upcoming days and weeks – that messed up.
And it wasn’t, their biggest mistake was trusting the wrong company. That’s both a strong reason to vet your potential partners and ensure they’ve got adequate security safeguards in place, but also an indictment of the way these stories are covered.
And again, beyond mis-attributing the fault, at least at a glance, the headlines aren’t even that helpful. If I know it was those companies’ collections agency, I know whether or not it affects me. Just saying Quest or LabCorp got breached really lacks the proper context.
Again, the headlines are what most people are going to skim. You have to make them count.
What can be done to improve the way the media covers cybersecurity?
This is a multi-faceted issue that isn’t going to be changed with a single fix. A lot of these media companies are struggling to keep up with the digital landscape, they’re understaffed, their reporters are overworked. There’s a reason I left my job as a reporter.

So one of the biggest issues is that the resources just aren’t there. But part of the problem is also archaic views on the way a news division should be organized. Tech and cybersecurity are major topics nowadays and media outlets should be trying to invest in reporters and journalists with expertise in those areas. They need dedicated coverage. You wouldn’t hire a business reporter without a strong knowledge of the financial industry. You wouldn’t hire a sports reporter that doesn’t know about sports. But with a lot of these tech topics that’s what happens. You get a reporter that’s honestly just trying to do their best with a topic they’re not knowledgeable about.
Unfortunately, there’s a big cybersecurity skills gap right now. There are a lot more roles than talent. And a lot of those roles pay better than being a reporter or journalist does. So the incentive to become a cybersecurity reporter at any but the best outlets isn’t very high.
Granted, some organizations, like the New York Times and Washington Post do staff actual cybersecurity experts. Most don’t though, and that means they have to approach the story from a layman’s perspective and try to latch on to the things that they THINK are the most important without knowing for sure whether or not they actually are.
LabCorp and Quest are much bigger names than AMCA, so putting them in the headline makes sense from a recognition standpoint, but it also distorts people’s impression of the actual news.
As I said, there is no easy fix for this, no magic wand to wave or pixie dust to sprinkle. But it still needs to be brought up.
And look, I have no problem with the media taking an irresponsible or negligent company to task. That kind of public shaming can actually be a net-positive. But it has to be used appropriately. Not every breach is the same. The devil is in the details.
That’s why improving the media’s coverage of these issues is so important.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown