The government shutdown is catastrophic for US cybersecurity
While the short-term impact is jarring, the long-term effects could prove even more harmful
The current US government shut down is doing serious damage to the US cybersecurity apparatus, but the longer-term impact could be even worse.
If you’ve paid any attention to the news in the US lately it’s hard to ignore the massive government shutdown currently taking place. Case in point, last night all of the American networks paused whatever they were carrying to air a presidential address about said shutdown. Then an opposition response about the shutdown.
It’s kind of a big deal.

My job isn’t to wax philosophic about politics, so I’ll just stick to the facts. The dispute is over immigration, specifically securing the United States’ southern border with Mexico. The president, in keeping with a campaign promise, wants $5 billion to pay for a physical barrier, a wall, and has refused to sign any legislation to continue funding the government until he gets it. In the meantime, the US government is effectively shut down – including the State department, Justice Department, Treasury, Transportation Department, Department of the Interior, of Agriculture and of Homeland Security – and about 800,000 federal employees are currently furloughed or working without pay to carry out “essential” operations like air traffic control.
So today we’re going to talk about what the shut down is doing to the United States’ cyber defenses, and what impact this could have in the future.
Let’s hash it out.
Who is still at work?
As we discussed in November, the US recently created a new agency, the Cybersecurity and Infrastructure Security Agency (CISA), under the umbrella of the Department of Homeland Security.
“Elevating the cybersecurity mission within the Department of Homeland Security, streamlining our operations, and giving NPPD a name that reflects what it actually does will help better secure the nation’s critical infrastructure and cyber platforms,” said NPPD Under Secretary Christopher Krebs. “The changes will also improve the Department’s ability to engage with industry and government stakeholders and recruit top cybersecurity talent.”
Now, not even two months later, CISA has effectively been knee-capped by the shutdown. As has the National Institute for Standards in Technology (NIST).

The Cybersecurity and Infrastructure Security Agency
Let’s start with CISA, the agency that has been created specifically to help with US cybersecurity.
What the federal government considers “essential” is a bit opaque, and purposefully so. But that does mean some of the federal security apparatus is exempt.
Per the Office of Management and Budget in a January 2018 memo offering guidance on a previous government shutdown:
“At a minimum, agencies must avoid any threat to the security, confidentiality and integrity of the agency information and information systems maintained by or on behalf of the government… Agencies should maintain appropriate cybersecurity functions across all agency information technology systems, including patch management and security operations center (SOC) and incident response capabilities.”
But, as reassuring as that may sound, it forgets two very important facts:
- Roughly half of the federal workforce (estimates range from 345,000 to 400,000) is furloughed, so these departments are not functioning at anything even close to full strength.
- The employees that are working, currently are not being paid for that work. They’re working for free. And this happened right in the middle of the holidays. So morale is probably great.
Now, the Senate did pass a bill that should give these employees backpay, but that doesn’t change the fact that these people haven’t been paid in at least 18 days and this shutdown could continue for weeks.
And beyond that, even at full strength the US cyber defense apparatus is being pushed to the brink by foreign, state-sponsored hackers and cyber cells. So weakening it puts the whole country at greater risk.
“Cyber threats don’t operate on Washington’s political timetable, and they don’t stop because of a shutdown,” Lisa Monaco, former assistant to the president for homeland security and counterterrorism, told Axios.
Or, as a report from Duo Security said:
“Trying to keep networks and data safe and thwarting attacks when not at full-strength is risky, especially when no one can predict how long this state of affairs will last.”
Right now, 45% of the Cybersecurity and Infrastructure Security Agency is furloughed. 45% is also the percentage of employees on the DHS’ analysis and operations teams – comprised of the Office of Intelligence & Analysis, and the Office of Operations Coordination – that are furloughed, too.
The National Protection and Programs Directorate – which handles a range of functions like the US-CERT (US – Computer Emergency Readiness Team) Continuous Diagnostics (CDM) and Automated Indicator Sharing (AIS) programs – has a whopping 85% of its workforce furloughed.
And depending on how long this shutdown continues, we could see a lot of these agencies that are currently operating on short-term reserves run out of money and be forced to shutter even more of their operations.

The National Institute of Standards in Technology
NIST is the agency responsible for setting standards. For instance, it’s issued extensive guidance on encryption standards that has helped inform the industry standards set forth by the CA/B Forum. It’s an exceedingly useful agency and it has been thoroughly depleted by this shutdown.
85% of NIST is furloughed.
That means a number of new standards that have been under review – standards that businesses rely on to set a baseline for their own security programs – are now on indefinite hold.
That includes:
- The risk management framework
- Changes to the federal government’s guidelines on security controls
- Requirements to access controlled unclassified information
Currently, clicking any of those links effectively leads you to a dead end courtesy of this shutdown.
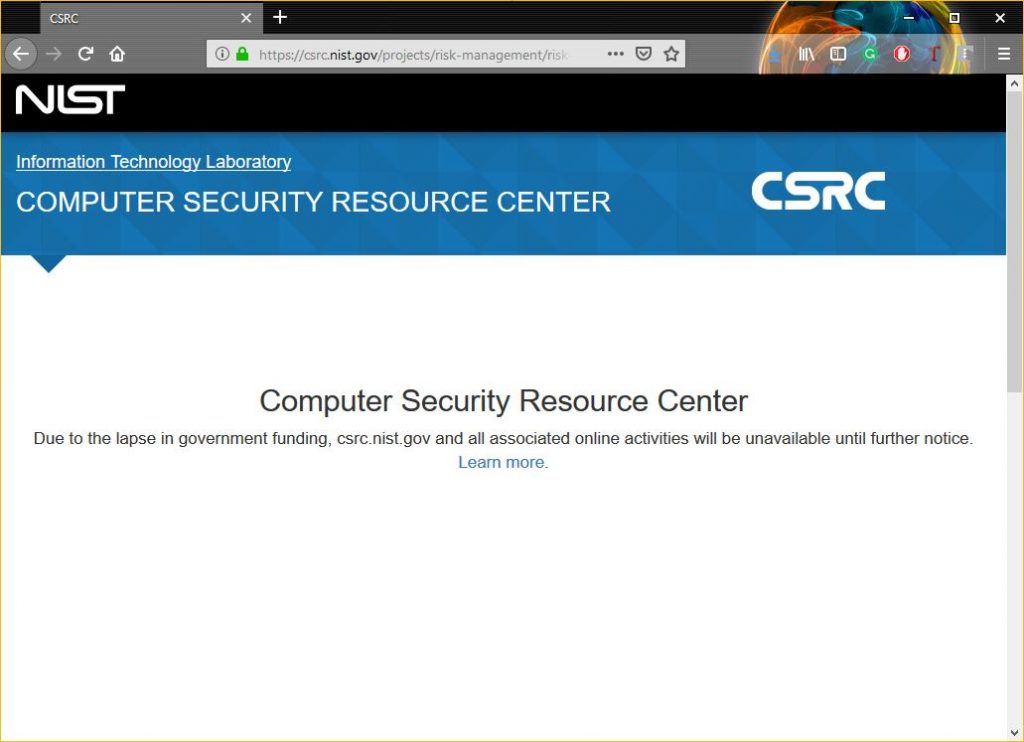
There are a few NIST services that will stay open, but to say they are lightly staffed would be a profound understatement.
- A computer scientist and an IT specialist will manage the National Vulnerability Database
- 16 employees will manage NIST’s time servers
- And an IT specialist will be present at the National Cybersecurity Center of Excellence
That’s one of those tidbits of information that is supposed to make you feel better but actually just makes everything seem worse. That’s less than 20 people handling critical functions for a country of nearly 300,000,000.
The real damage this shutdown may cause is long-term
Eventually, possibly as soon as today, this shutdown will end. But it’s also quite possible that it stretches on days or even weeks longer. With every passing day, more and more long-term damage to the US national cybersecurity apparatus is being done.
Here’s why: If you’re a talented cybersecurity professional, why would you ever work for the US government?
That may sound silly or unpatriotic, but ask any of the nearly 400,000 federal employees that didn’t get paid over the holidays if their patriotism took care of their power bill or put food on their family’s table?
No, patriotism is going to give way to pragmatism, and let’s look at the facts:

- You could go to the private sector where you’ll be better compensated with more opportunities for advancement.
- You could work for the government where your ability to work and be paid are subject to the partisan whims of elected officials.
And here’s the real match in the powder barrel, all of those government officials whose whims have cost you pay and potentially even caused you to have to work for free – they’re all getting paid.
Congress and the Executive Branch have already been funded via a previous spending bill.
And while historically the federal employees that are currently affected – both furloughed and working without pay – have been given backpay to compensate, the timing of that backpay is contingent upon the shutdown ending and Congress passing a bill (oh, and the wheels of bureaucracy churning) before you actually see that money.
Already, they’ve missed an entire pay period (December 23-January 5).
None of that is going to attract the best and brightest. And why should it? The average American couldn’t scrape together $400 in an emergency, try taking away an entire paycheck. That’s the type of uncertainty you’d do well to avoid.
And this is not without precedent, the NSA got hammered following the 2013 shutdown. For one, it caused management to divide employees into “essential” and “non-essential” categories – not exactly a shot in the arm for morale – and the 16 days out of work threw many lives into disarray.
“I was paying money out of my pocket… The guys were sitting at home, they couldn’t go work with the shutdown because they had to work from government spaces, so they really could not go,” one former NSA employee who left following the 2013 shutdown told Buzzfeed. “I can say anecdotally, because I do know several guys who worked there who went off on their own around 2013, 2014. There was a bigger exodus than normal, and you’ve gotta [sic] figure at least some of that was due to the shutdown and guys going ‘screw this.’”
The current shutdown has already gone on two days longer and if a morning conference between the president and the two leaders of the congressional democrats doesn’t solve things—it could go on much longer.
UPDATE: It didn’t solve things.
In the meantime – and possibly for the foreseeable future – our national cyber defenses will suffer.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown