Sectigo may have just revived S/MIME
Email signing certificates just became easy to deploy. That changes everything.
S/MIME certificates have always been a great idea – in theory. They give organizations the ability to sign and encrypt email. Which, as we’ve covered before, is an invaluable tool for organizations trying to stop phishing and email attacks.
But email signing certificates’ Achilles heel has always been deployment.
Deploying them has always been a long, tedious process that many organizations just don’t feel like putting up with. That’s hamstrung their proliferation. At a recent event our VP Michael Ward was told by a heckler that S/MIME is dead.
But reports of its death have been greatly exaggerated. Also, who heckles at a business conference?
Let’s hash it out.
Sectigo just solved S/MIME’s deployment problem
The biggest issue with S/MIME has always been the fact that you had to have someone go to every single device and install the certificate manually. That’s a pain in the butt for a small company. Our prodigious IT manager (and regular Hashed Out contributor) Ross Thomas had to do this a few months ago. Every. Single. Device. Seriously, we had to nail the windows in his office shut to keep him from leaping out of one.
Until recently, every time a new employee was hired Ross had to slog through the installation process again. And he had to revoke any certificate that belonged to departing employees. It’s a process he knows by heart, but a tedious one. Let’s be honest, constantly being asked to perform the same tedious task at work over and over and over gets to you after a while.
Then Sectigo unveiled its new Zero-Touch S/MIME solution. Full disclosure, we work very closely with Sectigo. We get a sneak peek at what’s coming. We knew about the new name before they even announced it to the rest of their partners. The point is, it may have been announced at the end of February, but we’ve been working with Sectigo’s Zero-Touch S/MIME solution for a few months so we could figure it out ourselves.
Let’s put it this way: Ross no longer swears at the mere mention of S/MIME. 95% of the tedious work that used to come with email signing has been alleviated because deployment is now automated. Sectigo’s Zero-Touch S/MIME solution integrates with your Active Directory and gives you the ability to manage everything via a single interface.
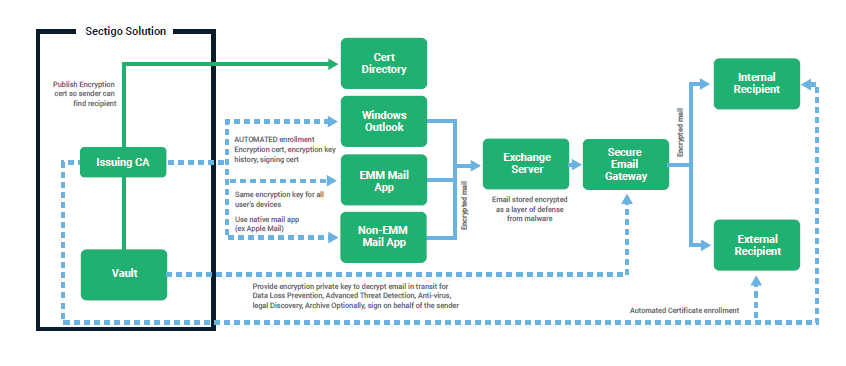
When new employees sign on, as we had with our new office manager just last week, deployment is a simple, straightforward process. When employees leave, their certificate can be revoked, but their email will still be decryptable.
All of the pain points have been alleviated.
This is how S/MIME was supposed to work
The biggest reason that S/MIME certificates aren’t more popular is that – given the workload involved – IT admins are loathe to tell management that they even exist. I’m kidding. Mostly. Anyway, as we’ve discussed, the real issue has always been deployment. End users had to acquire their own certificate and install it themselves. And part of that is our fault as an industry.
That’s partially because companies and organizations perceive digital certificates and PKI as costly and time-consuming. Security is nice, but not at the expense of productivity and budgeting for other projects.
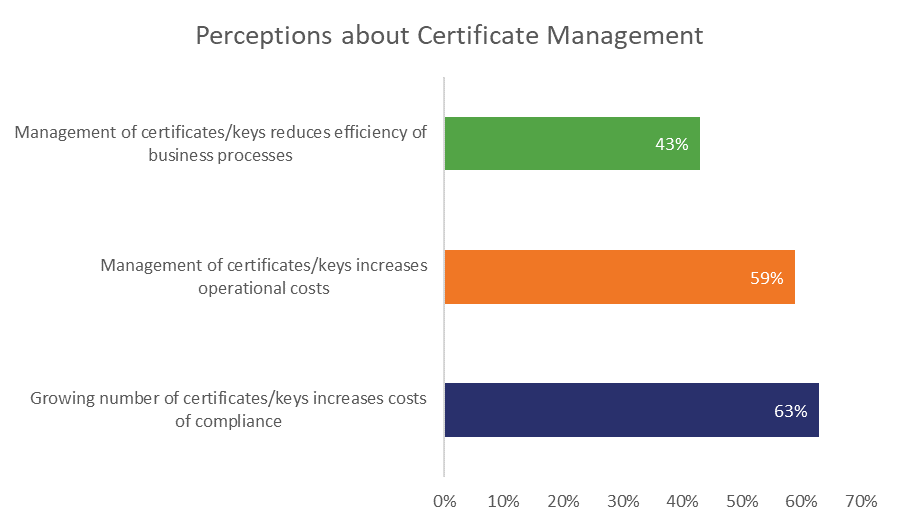
That’s why S/MIME hasn’t been more widely adopted until now. It’s been difficult to convince most organizations that deploying and managing all those certificates is worth the hassle.
Zero-Touch S/MIME could change that. It will also help organizations with compliance by providing a means to encrypt and sign email.
Having the issuance and deployment of S/MIME certificates automated, saves a lot of time AND money. And Zero-Touch is a part of Sectigo’s larger Certificate Manager, which means it further consolidates your digital certificate management. As we’ve discussed many times, the certificate management presents a major problem for many organizations – especially larger ones.
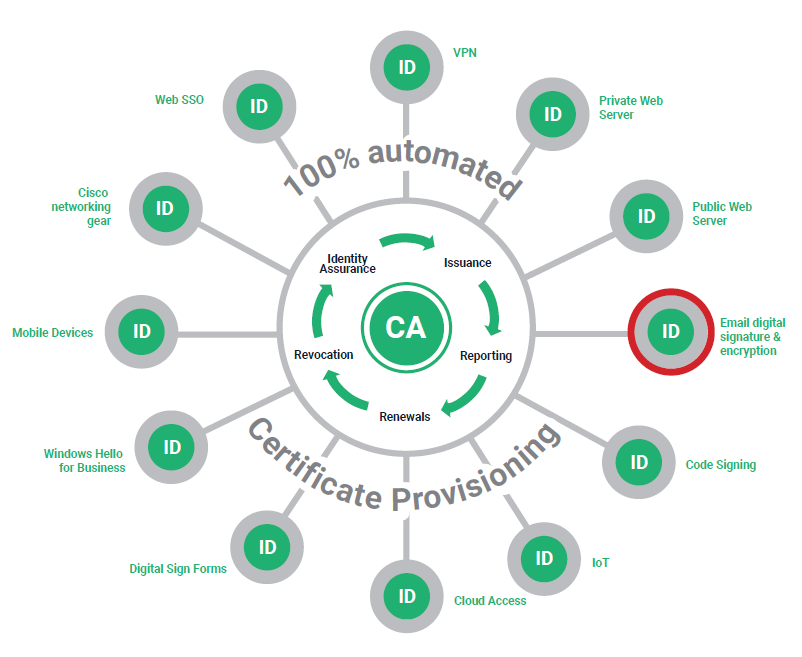
Having the ability to manage all of your certificates, including S/MIME – which can now be rapidly issued and deployed – through a single interface could save your organization millions in the long run. Literally millions.
| Scenario | Extrapolated Cost |
| Cost of unplanned outages due to certificate expiry | $11,122,100 |
| Cost of failed audits/compliance due to undocumented or poor key management | $14,411,500 |
| Cost of server certificate and key misuse | $13,423,250 |
| Cost of Code Signing certificate and key misuse | $15,025,150 |
| Cost of CA compromise or rogue CA for MITM and/or phishing attacks | $13,219,850 |
| Total Cost | $67,201,850 |
Look, I’ve been writing Hashed Out for nearly three years now and in that time I’ve never openly pitched anything to you. I may have hinted at one of our solutions a few times but Hashed Out operates with a degree of autonomy and we try to be objective, never sales-y.
And that’s not what I’m doing here, either. At least not directly. I’m simply pointing out that since we started using this Zero-Touch S/MIME solution, our IT manager, Ross, enjoys coming to work again, we can once again trust him around open windows and, perhaps more relevantly, our S/MIME certificates work seamlessly in the background.
Now every email is signed. The important ones are encrypted. And, most importantly, it’s no longer a burden. It’s just a quick glance at the dashboard a few times a week to ensure everything is running smoothly.
S/MIME certificates used to be a big pain in the ass.
They’re not anymore. We know that first-hand.
As always leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown