Hospital Employees Open 1 Out of Every 7 Phishing Emails
The healthcare industry, in general, is highly susceptible to phishing.
A new study shines light on just how susceptible the healthcare industry is to phishing. Conducted by a group of doctors and published on JAMA Network Open, the study examined the email security practices of six major medical institutions and found that about one in every seven phishing emails ended up getting opened by hospital employees.
That generally gels with the conventional wisdom regarding the healthcare industry: that it’s overall security posture is poor. It also agrees with something else we say all the time, which is that an organization’s own employees are its biggest threat.
So, today we’re going to discuss this new study, the healthcare industry’s security issues and email security, in general. At the end we’ll also offer you a chance to download our new eBook – filled with almost 40 pages worth of insight and actionable advice on securing your organization’s email.
Let’s hash it out.
“…these click rates represent a major cybersecurity risk for hospitals.”
The study, which was published last month, is named “Assessment of Employee Susceptibility to Phishing Attacks at US Health Care Institutions,” a serviceable – if slightly uninspired – title. The study was designed to answer one major question:
Are employees at US health care institutions susceptible to phishing attacks?

Turns out the answer is yes.
In summary, current click rates in phishing simulations at US health care organizations indicate a major cybersecurity risk. These click rates highlight the importance of phishing emails as an attack vector, as well as the challenge of securing information systems.
Now, common sense likely could have saved this group some money – the answer is obviously yes – but… SCIENCE!
So, the researchers proceeded to bombard six different US hospitals with nearly 3-million (95 different campaigns totaling 2,971,945) simulated phishing emails from 2011-2018 and recorded the organizations’ click rates. The overall median click rate was 16.7% across the various campaigns and institutions.
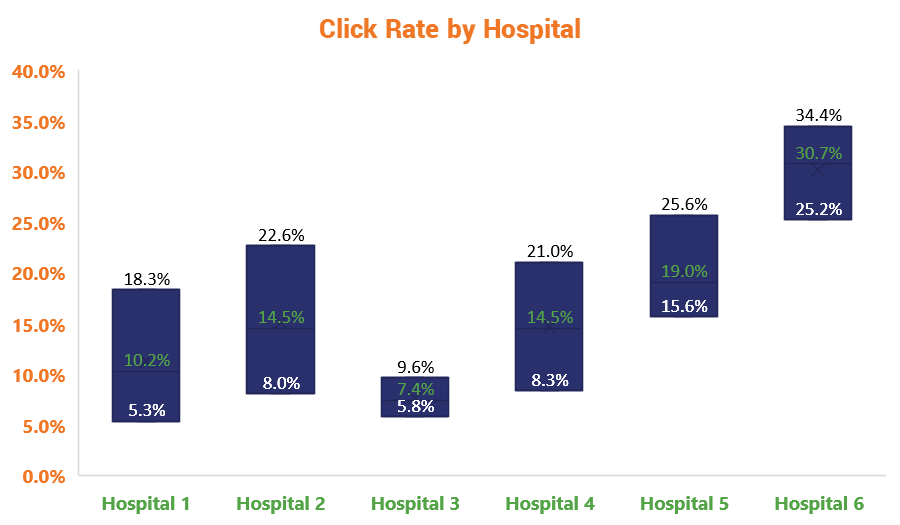
To better interpret the data, the researchers organized the various simulated phishing campaigns into three different categories:
- Office-related
- Personal
- IT-related

As we discuss all the time, the best phishing emails are constructed to trigger certain emotions. What those targeted emotions are has actually shifted a bit recently, whereas creating a sense of panic or urgency has historically been the MO, recently phish have begun to play to our vanity. This can partially be attributed to the rise of social media. Unfortunately, the study didn’t provide its raw data and didn’t offer any insight as to trends in phishing as they ebbed and flowed over the eight years the study ran. That could have been enlightening and it would be nice to compare the results over a longer duration against some of the more recent, more abbreviated phishing studies that have been completed.
Additionally, without the raw data it’s tough to know what these campaigns actually looked like, both in terms of aesthetics and the subject line and contents of the simulation emails. I’m not saying any of this to criticize the study, I’m just trying to qualify some of this information by framing it with the correct context.
While those details were rather opaque, the study did offer several examples of subject lines from each category.
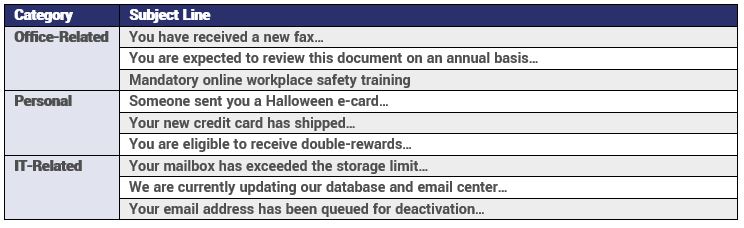
Ok, the boring methodology stuff is out of the way, so let’s look at the most interesting takeaways from the study, starting with the click rates by the category:
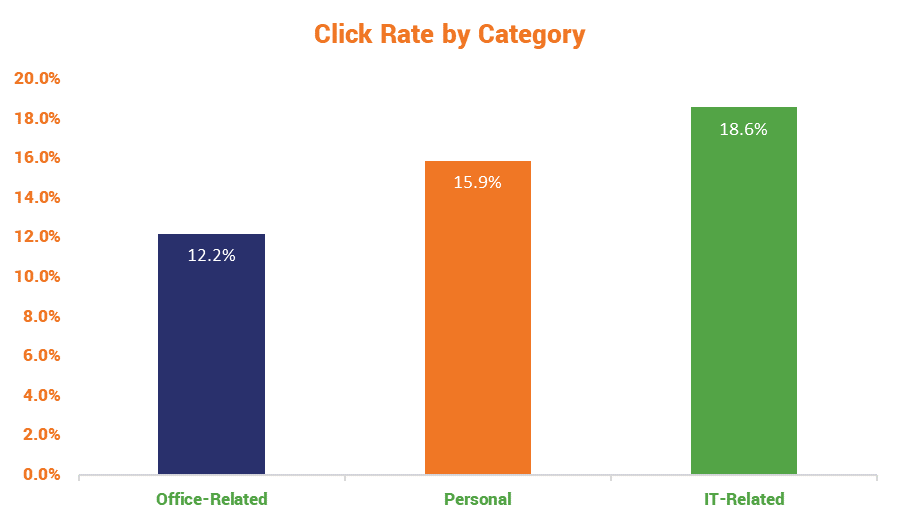
It seems like there would be quite a bit of overlap between Office-related and IT-related phish, but obviously when it comes to technology-related issues the healthcare industry – or at least the sampling from this study – is especially sensitive. This makes a lot of since given how many devices, more and more of them IoT, are critical to a well-functioning hospital. If devices or networks start going down, people could very literally die.
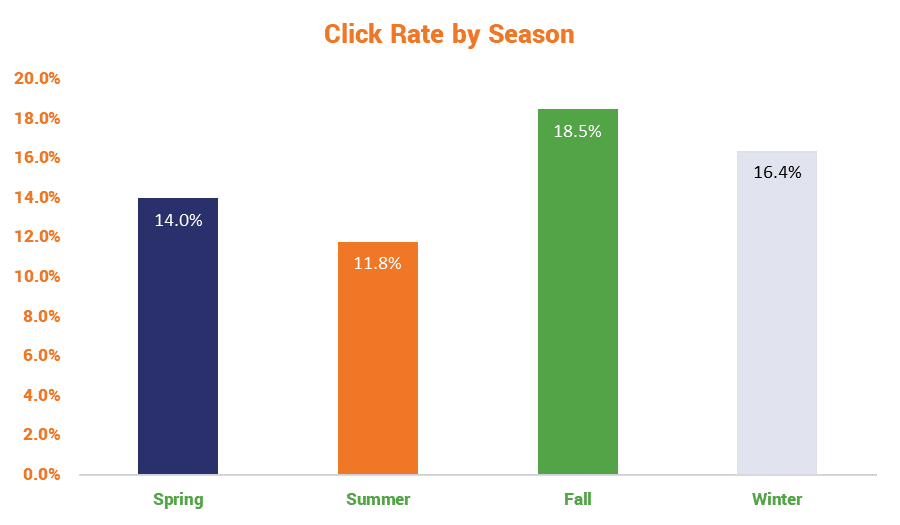
Fall is Phishing Season
Here’s a random fact that emerged from this study: hospital employees are nearly twice as likely to get phished in the Fall as they are in the Summer. I have no idea what to attributed that to, and the study didn’t even try to guess.
Finally, certain seasons were associated with click rates. For example, both spring (adjusted OR, 0.842; 95%CI, 0.735-0.964) and summer (adjusted OR, 0.751; 95%CI, 0.624-0.905) campaigns were associated with fewer clicks compared with fall campaigns, while winter was not significantly associated with click rates (adjusted OR, 1.175; 95%CI, 0.972-1.420).
Because I realize a lot of eyes are going to glaze over on account of those numbers, let’s toss it in a graph.
Phishing Simulations Really Do Work
The big takeaway from the study is that, at least in a healthcare context, these phishing simulations really do help. Over this eight-year study, across a couple of different metrics, there’s decisive evidence that phishing simulations help decrease click rates.
We found that the odds of clicking on a phishing email decreased with greater institutional experience, which we hypothesize may be due to the benefit of running phishing simulation campaigns for employee education and awareness.
Then, in their conclusion, they state it a bit more emphatically:
Repeated campaigns were associated with improved click rates, suggesting that simulated phishing campaigns are an important component of a proactive approach to reducing risk.
Let’s take a look at the total unadjusted click rate over the eight years that the study ran:
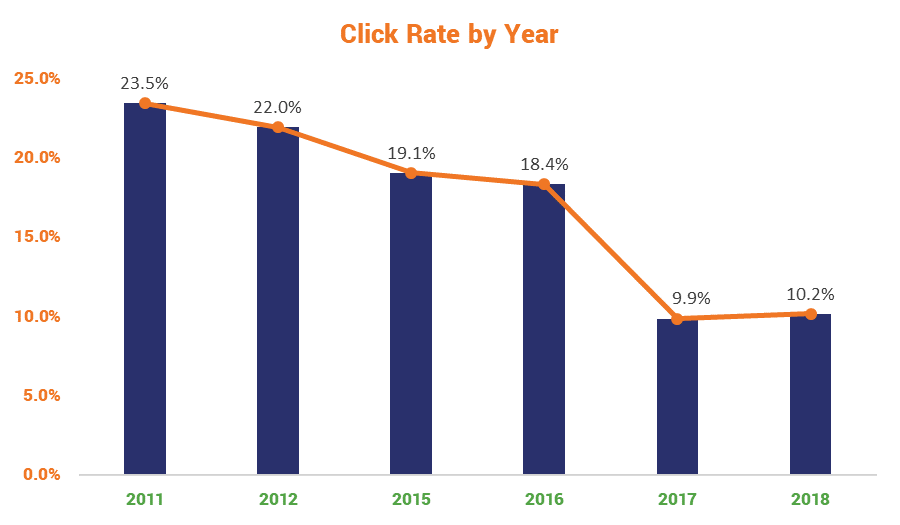
You’ll notice they didn’t run any simulations during 2013 and 2014. I have no idea why that was, nor do they disclose the reason in the report. The biggest dip came between 2016 and 2017, which lines up with when phishing simulations were really beginning to come into their own. The researchers admitted that at the start of the study, they were somewhat hamstrung by the lack of healthcare institutions with “an information security system organization mature enough to conduct phishing simulations.
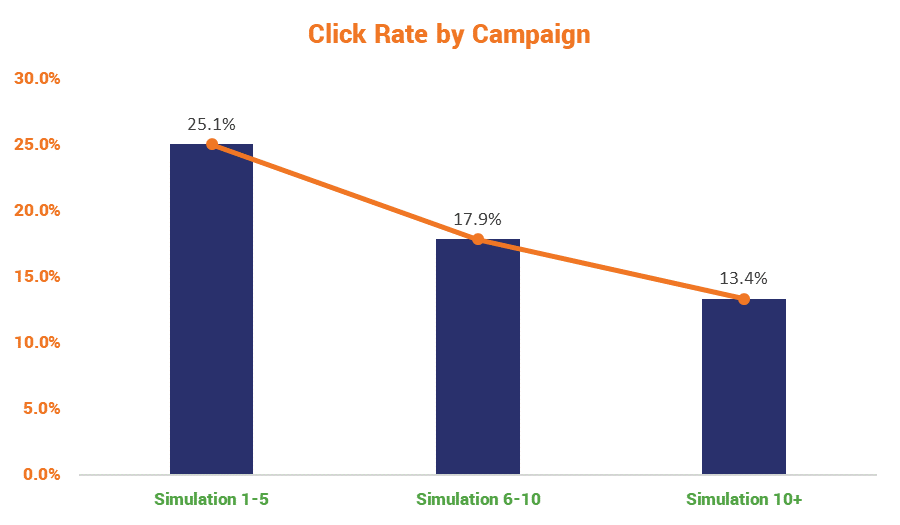
The more compelling evidence is the reduction in click rates as employees received more training. We say it all the time, but education is one of the best lines of defense when it comes to cybersecurity. Here’s how employees fared as they progressed through more and more phishing simulations:
Why is the healthcare industry such a big target?

The healthcare industry has historically lagged a bit behind other industries in terms of cybersecurity preparedness. This despite stringent industry standards for compliance like HIPAA. The reason for this is multi-faceted.
For starters, healthcare organizations have a ton of surface to cover. Medical devices, many of which are now online, are additional attack vectors, and given their functions and interdependence, their security is even more complicated. Then there’s the entire need to secure and, at times, transfer sensitive medical records that adds another degree of complexity. And those records are valuable, with some fetching upwards of $1,000 on the dark web.
Health care systems are also uniquely vulnerable to phishing attacks. Employee turnover at hospitals is high,20 and there is a constant influx of new employees (eg, trainees) who may have no prior cybersecurity training, which creates a continuous stream of newly susceptible employees. Hospital systems are vulnerable due to significant end point complexity, a term used to describe the large number of IT devices that could be targeted in an attack.
Remember, 91% of cyber attacks begin with an email. 1 out of every 101 email is malicious. And all it takes is one to infect or target the right system, which in turn could influence a significant number of downstream systems, and suddenly there’s a full-blown catastrophe.
RELATED: What if getting phished could kill you?
That only underscores the importance of good email security, which clearly starts with proactive employee education.
How else can organizations improve email security?
There are a number of different strategies you can employ to help defend against phishing, and at one point or another we’ve covered each of them. For improving security within your own organization, deploying S/MIME certificates at scale, setting up SPF and DKIM, and using DMARC will all help with the health of your organization’s email systems. They will also help ensure more of your emails get delivered outside of the organization, too.
There also needs to be specific attention paid to setting up the right email filters and rules. This will prevent a lot of these emails from ever reaching your employees’ inboxes. And then if all else fails, as long as someone in your IT department knows how to analyze an email header, you can evaluate particularly suspicious emails on a case-by-case basis.
Here were the suggestions the study proposed:
There are many strategies for preventing or minimizing the consequences of phishing attacks. One strategy is to prevent phishing emails from being received or read in the first place (eg, using technology to filter emails based on patterns suspicious for phishing or modifying emails to indicate they are from external senders). A second strategy is to minimize the value of username and passwords, by requiring multifactor authentication (eg, a unique code generated by a smartphone application that must be entered to log in) or requiring special access controls for specific systems, so that credentials are less useful even if they are obtained. A third strategy is to foster employee awareness and training, and our results suggest that including phishing simulation campaigns as part of employee awareness or training may be helpful.
As mentioned, we’ve previously covered all of these individually, but if you’d like to have an all-in-one playbook for securing your organization’s email, we’ve now got that for you, too.
Just fill out the form below and download our new eBook, 2019 Email Security Best Practices. It’s filled with nearly 40 pages of data and actionable advice to help secure every facet of your email.
Check it out and let us know if you have any suggestions or questions…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown