1 out of every 101 Emails is Malicious
A new FireEye study examined half a billion emails from January-June of 2018
A newly released report from FireEye, an Enterprise cybersecurity company, has found that one out of every 101 emails sent is malicious. The report, titled “All it takes is ONE,” was compiled after researchers pored over nearly half a billion emails sent in the first half of 2018.
Email is the most popular attack vector for hackers and cybercriminals – by far. While the specific numbers vary by study, the vast majority of cybercrime starts via email, 91% according to a Radicati group report. A Verizon report states that 92.4% of malware is delivered via email. 76% of organizations say they experienced a phishing attack in 2017.
The average employee receives 16 malicious emails per month.
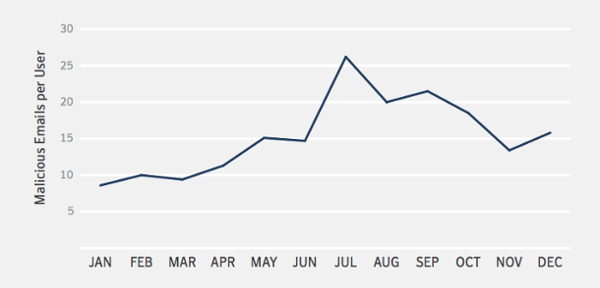
Think about that, that’s one every other day. And your employees aren’t just dealing with the threat of malicious email, they’re also being worn down by a constant torrent of spam. While the percentage of spam email has declined from its halcyon days when it was up around 75%, at the end of 2017 it was was still 55%.
All of this comes together to create a climate where people are just numb to email. Case in point: only 17% of phishing emails actually get reported.
Email Threats Come Well Disguised

We spend lots of time on phishing, but there’s never a bad time to be reminded that the level of social engineering inherent in some of today’s phishing and malware campaigns is staggering. The Democratic National Committee was undone by a convincing Google spoof. MacEwan University was bilked out of a small fortune after cybercriminals spoofed the websites of local construction companies to send phony invoices from. Hackers can use Unicode characters to make their domain names look more realistic. LinkedIn is used as a resource to research targets, which can make an email seem more convincing. Emails are crafted to create a sense of urgency.
If it weren’t so duplicitous, it would be impressive.
One of the trends Symantec pointed to in its most recent threat report was the rise of malicious links being used in malicious emails as opposed to attachments. In 2016, less than 2% of email malware contained a malicious link. Last year, in 2017, that percentage increased to 12.3%. This coincides with a considerable increase in phishing websites since the last half of 2017, with over 1.4 million new phishing sites created each month.
Not surprisingly, Public Administration is the most frequently targeted industry.
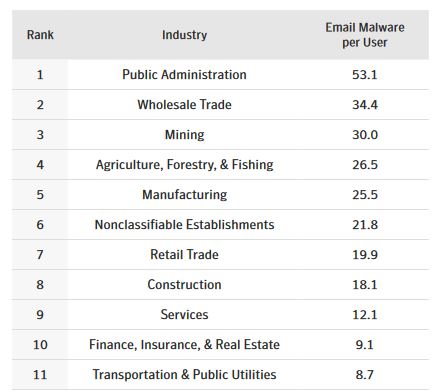
As for the way these emails are disguised and designed, the most common tactics are to disguise them as bills/invoices, legal notices, error messages and delivery notifications.
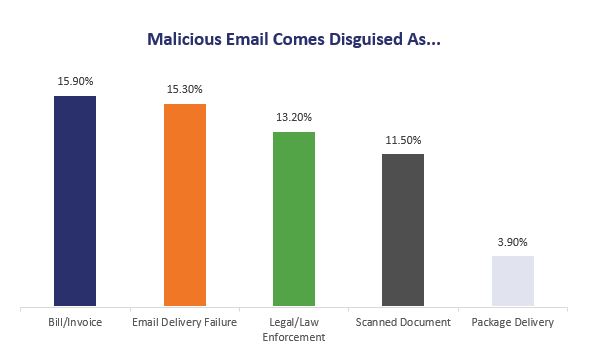
There are specific words you that appear more frequently than others, too. As we discussed, the intention is to make the email seem as urgent as possible. Obviously, the aforementioned themes accomplish that. So does word choice. In web design this is sometimes referred to as a dark pattern. These words are meant to trigger a response, ideally causing the user to take the intended action.
One technique for creating a sense of urgency is to mimic a Business Email Compromise (BEC). BECs embody all of the tactics we previously discussed, the social engineering, the background research. These are highly targeted campaigns that are aimed at getting a company to execute an unauthorized transfer of funds (as we saw in the MacEwan university phishing scheme). According to the FBI, BEC schemes cost US organizations $676 million in 2017. Here are some of the most commonly used words that appear in the subject lines of malicious emails:
- Payment (13.8%)
- Urgent (9.1%)
- Request (6.7%)
- Attention (6.1%)
- Important (4.8%)
- Confidential (2.0%)
- Immediate Response (1.9%)

- Transfer (1.8%)
- Important Update (1.7%)
- Attn (1.5%)
And then here are some of those common words that appear in those emails.
- Delivery (12.1%)
- Mail (11.8%)
- Message (11.3%)
- Sender (11.2%)
- Your (11.2%)
- Returning (7.6%)
- Failed: (7.6%)
- Invoice (6.9%)
- Images (6.6%)
- Scanned (6.5%)
In terms of payload, more than 3 out of every 5 malicious emails uses an infected script, just under a third use an executable.
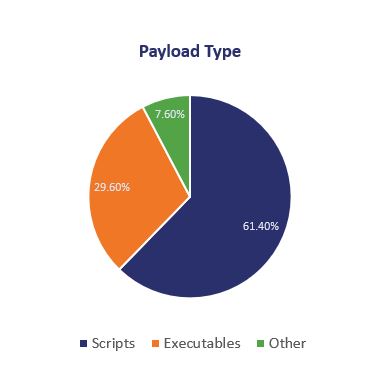
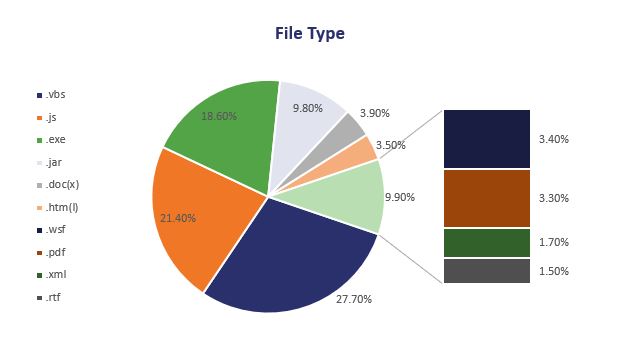
And then when we break the malicious payloads down into file type we can see that Visual Basic Script and JavaScript were by far the most common types of malicious attachment, representing just less than half (49.1%) of all malware delivered by email in 2017.
As we stress all the time, your own employees are your greatest threat. And unfortunately, 70% of US employees have no concept of cybersecurity best practices. The only tried and true way to really defend against phishing, and really all forms of email malfeasance for that matter, is education.
Fortunately, our own IT virtuoso, Ross Thomas, has written a phenomenal series on email security and the ways that you can lock down your own office’s email servers.
So read it.
Clearly, email security has never been more important.
- Email Security – Part 1: Certificate Signed Emails
- Email Security – Part 2: Phishing and Other Falseness
- Email Security – Part 3: Sender Policy Framework (SPF)
- Email Security – Part 4: DKIM (DomainKeys Identified Mail)
- Email Security – Part 5: DMARC, Reporting and Email
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown