What is Phishing? A Look at One of Cybercrime’s Favorite Tactics
An in-depth look at the types of attacks that are involved in 32% of all data breaches
In our news-heavy world, there isn’t a lot that surprises us anymore. But there are a few questions we’re surprised to receive in our technologically advanced era. One of the most critical of which is “what is phishing?” It’s not always this exact question, however. Sometimes, it’s one variety or another of the same question that’s just phrased differently, such as “what does phishing mean?” “what is a phishing attack?” or “what is a phishing email?”
Although these questions are commonly posed by random individuals who come across our blogs, they’re sometimes posed by corporate executives — a fact that is particularly worrisome for obvious reasons. After all, if an organization’s leader lacks that necessary knowledge or cyber security awareness, how can they expect their employees to be knowledgeable enough to avoid the most common types of cyber attacks? Leaders need to lead by example, and this means learning everything they can about these cyber threats.
Phishing is a very real and very dire threat to organizations and individuals alike. In fact, in 2018 alone, nearly one-third of all data breaches involved various types of phishing attacks or tactics. We’re not just pulling this number out of a dark region; this research comes from Verizon’s 2019 Data Breach Investigations Report. This is just one of many reasons why phishing is so dangerous to businesses, brands, employees, and consumers alike.
So, now, it’s time to break down the internet age old questions, “what is phishing?” and “what makes phishing so effective?” We’ll cover different types of phishing and will also dive into some of the ways to help mitigate receiving phishing emails and how you can prevent your brand from being used in phish that are sent to others.
Let’s hash it out.
Phishing Definition: What is Phishing, or What Does Phishing Mean?
Phishing is an overarching term for an entire category of cybercrime against people and businesses alike that involve cyber fraud. Based on the concept of fishing, phishing is a virtual form of hunting that involves tricking users into “taking the bait” and getting hooked. The category of attacks typically involves cybercriminals impersonating a person or organization and using various tactics to extract information or compel the victim to perform a particular action. The attacks can be made via email, over the phone, using text messages or even social media accounts.
At its core, phishing is a medium for an attack but isn’t the weapon itself. These attacks often require you as the victim to do something — click on a link, open an attachment, download a file, etc. These actions typically will trigger the “payload” — the actual weapon of choice — which often comes in the form of malware or ransomware. However, some cybercriminals will instead drive you to a fake site that’s designed to look like the real deal. There, you’ll be asked to update, change, or confirm sensitive information like your account information and passwords.
Research from Duo shows that 62% of simulated phishing campaigns capture at least one set of user credentials. Considering that it only takes one set of credentials for cybercriminals to break into your network, gain access to your databases, access employee and customer data, etc., you can see why even one set of credentials is such a major concern.
Phishing is about preying on the human element of organizations and businesses. In their annual Human Factor 2019 report, ProofPoint researchers indicate that “more than 99 percent of threats observed required human interaction to execute.” The study, based on an analysis of 18 months of data, analyzed the company’s global customer base. Less than one percent of the attacks targeted system vulnerabilities.
Some more involved types of phishing involve weeks or even months of pre-attack reconnaissance. This can involve cybercriminals using malware, spyware, man-in-the-middle (MitM) attacks via unsecured Wi-Fi networks to monitor or insert themselves in their target’s communications. They also will often research the target online using websites such as Monster, LinkedIn, and various social networking platforms.
An Example of Phishing in Action
But what does phishing look like? Let’s paint you a not-so-pretty picture:
It’s a busy Friday afternoon in the accounts payable department. Your employees are slammed with work when an email pops up from a regular contact at one of your IT vendors. The subject line says it’s urgent: There’s been a mix-up with a payment, and your organization’s account is delinquent. The account needs to be brought current or else they’ll stop your service, which will bring your company to a grinding halt. The body of the email goes on to explain the dangers of further delinquency and encourages to fix the situation ASAP. They also explain that their company recently updated their account and they provide you with their new payment information.
For the sake of expediency, your employee uses the new payment information the vendor provided to make the payment and continue on with their day without another thought. What they don’t realize, however, is that it wasn’t your vendor contact who sent you the email. It was a cybercriminal pretending to be him. Fast forward a couple of months and your IT vendor reaches out again. This time, however, they say that your account is delinquent because they’ve not received payment in a few months. Thinking there must be a mistake, your employee goes back to verify the account because they know they’ve made the payment.
After some back-and-forth communications with the vendor, your employee realizes that they’ve been scammed and have been making payments to a fraudulent account. They come to you to find out what to do. You tell them to halt any future payments to the fake account and to try to reverse any previous payments, but it’s too late. The money — and the criminal — are now gone, and your company is now out thousands or even millions of dollars.
We all know this scenario isn’t good for your organization’s reputation. Nor is it good for job security. All you have to do is look at the headlines from recent years to see the impact of successful phishing attacks.
Spelling It Out: Why is Phishing So Effective?
A similar scenario as the one we described above happened to Facebook and LinkedIn. A Lithuanian hacker sent a series of fake invoices to both companies while pretending to a tech vendor they both did business with. Both companies fell for the scam, and their mistake them more than $100 million combined between 2013 and 2015. And they’re not alone — even local governments throughout the U.S. have fallen for multiple phishing scams this year (and over the past several years) that resulted in costly ransomware attacks.
You may wonder how anyone can fall for such seemingly simple tactics or obvious scams. But, remember: Phishing is about targeting people in ways that catch them unawares. It’s about making convincing, seemingly innocuous emails that convey a sense of urgency. This may involve contacting the victim while impersonating someone they know — such as a friend, boss, or vendor contact — or by simply using urgent language that spurs them to take action now to avoid catastrophic consequences later.
ProofPoint’s Human Factor 2019 research:
“Instead of attacking computer systems and infrastructure, threat actors focused on people, their roles within an organization, the data to which they had access, and their likelihood to “click here.” Whether attacking at a massive scale in large, indiscriminate campaigns, going after specific industries or geographies with more targeted campaigns, or seeking out a single person within an organization, attackers and their sponsors consistently found human beings to be the most effective vectors to infiltrate organizations and facilitate fraud and theft.”
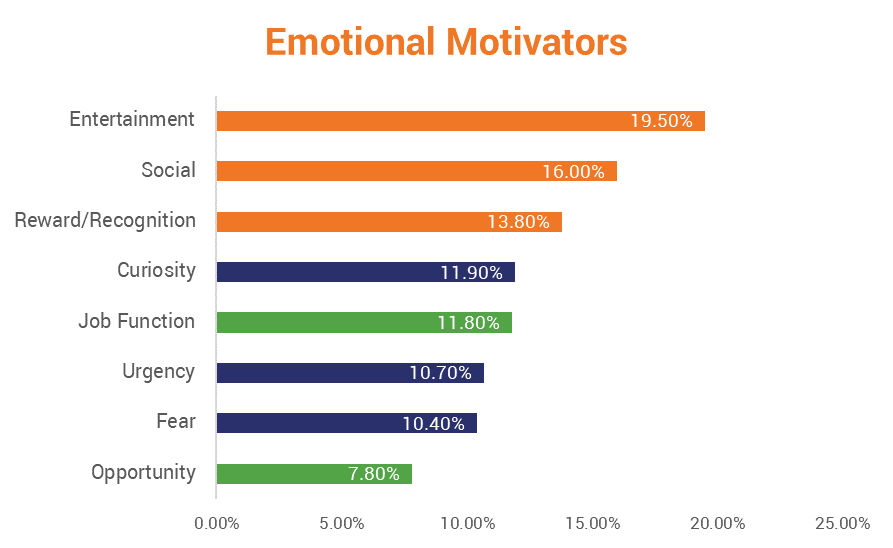
So, why is phishing so effective? Phishing, in general, is all about creating a sense of urgency, plausibility, and trust. So, what are some of the factors that come into play when it comes to phishing?
- People are not infallible. Because your employees are not perfect, they make mistakes. They rush, or they may simply be unaware of certain dangers. Regardless of the reason, employees represent your organization’s biggest attack vector or vulnerability when it comes to phishing attacks.
- Cybercriminals use a variety of tactics,
including social engineering. Social engineering takes advantage of our social
expectations, interactions, and instincts as human beings. Criminals use these
tactics with the express purpose of obtaining information or cause you as a
target (victim) to perform a specific action. It’s all about using your trust,
expectations, and very nature against you. They do this by:
- Impersonating your family, friends, colleagues, boss, executives, and vendors.
- Tailoring email content that speaks to you as an individual based on your likes, interests, activities, and other information they glean from your social media accounts.
- Writing content that evokes a psychological response: Cybercriminals write emails that convey a sense of urgency, or that can elicit a response of fear (you’re going to lose your account or services if you don’t act NOW), curiosity (check out these recipes, pictures, or other things you’re interested in), lust (you know the ones), etc.
- Cybercriminals frequently impersonate trusted brands. Cybercriminals love using the reputations of well-known and trusted brands as part of their attacks. Impersonating a company such as PayPal, Amazon, or even FedEx makes it easier to get a target to open and engage with their phishing email. This is, in part, because the target has a certain expectation of trust and safety from those brands.
Types of Phishing Attacks
When it comes to answering the question “what is phishing,” it’s important to recognize that there are many types of phishing. Some types of phishing are pretty generic in their approach while others are highly targeted. You have the basic, old school “Nigerian Prince” email scams. You know, the whole “Dear friend, I have millions of dollars that I need to protect, and only you can help me do it!” spiel. Then you also have the more convincing and planned types of phishing that are known as spear phishing or CEO fraud, which are far more convincing and pose significant threats to your organization.
Here’s a hilarious variation of an old school spam-type phishing email that was received by one of our customer experience team members:
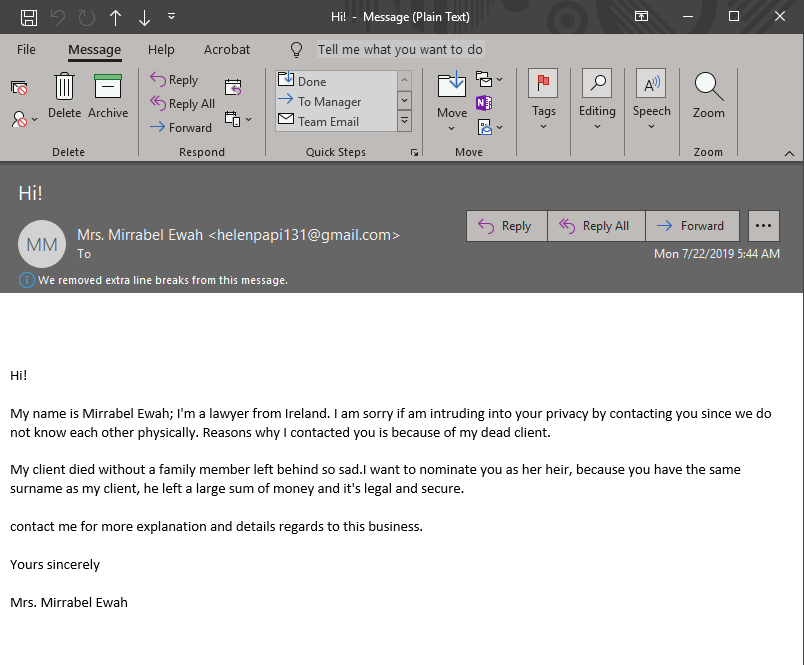
Wow… It looks like my colleague can retire early! Lucky lady.
But, seriously, it’s hard to believe that someone is going to fall for this type of obvious phishing. But we know somebody, somewhere is because if cybercriminals had absolutely no success with these types of messages, they wouldn’t bother sending them.
The list of common phishing attacks doesn’t end with just spam-type messages and spear phishing. And phishing attacks are not limited to emails alone. In fact, phishing can be conducted using a variety of technologies, including telephones, text messages, websites, or even social media accounts.
So, what are some of the most common types of phishing attacks? We’ve already spoken about many of these types of phishing in previous articles on Hashed Out, but we’ll rehash them here briefly just to help remind you:
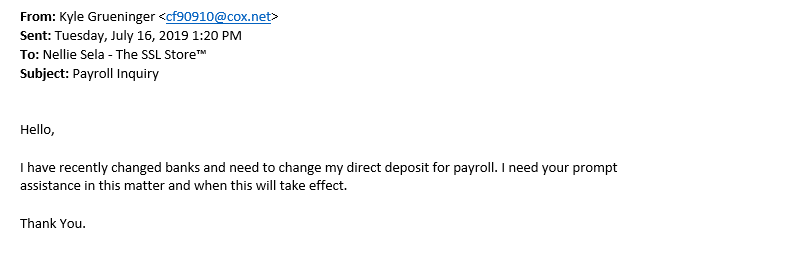
Business Email Compromise/CEO Fraud
A BEC or CEO fraud attack typically involves an attacker imitating the company’s CEO or another high-level executive and sending emails to lower-level employees directly with the goal of eliciting an intended reaction. The goal could be to gain access to sensitive data or to get significant funds via wire transfers.
Here’s a CEO fraud phishing email example that our office manager recently received:
Clone Phishing
This type of phishing involves a cybercriminal using the language, design, and “feel” of a legitimate message from a company and creating a virtually identical, malicious version of it. For example, if someone regularly receives legitimate package tracking emails from FedEx or DHL, they’re not likely to closely study every email to see if there are any discernible differences from the ones they previously received. They’re more likely to simply skim the email or jump directly to clicking on the fake tracking link. All it takes is one moment of unawareness — and that’s what criminals are counting on.
Domain Spoofing
Much like how it sounds, domain spoofing occurs when a hacker uses either fake emails or fraudulent websites and makes them look like they’re legitimate. In the case of email, the criminal “spoofs” the emails to make them look like they’re coming from the company’s legitimate domain. With the website domain spoofing, they’ll adopt the legitimate website’s design and use either a similar URL or use Unicode characters to replace the ASCII characters in the domain.
Evil Twin

Unlike the other types of phishing that made this list, an evil twin phishing attack is one that capitalizes on Wi-Fi. In this type of phishing attack, cybercriminals are like spiders: They spin “webs” and wait for their prey to come to them. They do this by creating a rogue Wi-Fi hotspot that looks legitimate — even using set service identifiers (SSIDs) that are the same as the real network — to trick users into connecting. This approach allows the attacker to eavesdrop on their network traffic to gather personal and corporate information without the victim being any the wiser.
HTTPS Phishing

This type of phishing is pretty basic — yet surprisingly effective. We’ve previously written about how 58% of all phishing websites are served via HTTPS. The trick to this type of phishing method is that the criminal sends an email with only a legitimate-looking link in the body — either in a clickable- or non-clickable format.
So, why would anyone be foolish enough to click on such an obvious phishing email? Because the attacker sends the message so that it appears to come from a legitimate source — the target’s boss, family member, friend, or even their CEO. It all comes back to the social engineering tactics we mentioned earlier.
Smishing
Smishing stands for “SMS phishing.” In a nutshell, it’s a way for
cybercriminals using text messages that appear to come from legitimate sources to
lure users into downloading malicious payloads via malicious URLS. The links
could appear to be a coupon code from your favorite Mexican restaurant or even
free tickets to an upcoming show.
Spear Phishing
Spear phishing is the antithesis of old school spam emails. Rather than blasting out emails to thousands of people in a massive generic campaign, this type of scam involves a phisher researching their target in depth. They often consult social media profiles and other publicly available information — to socially engineer a convincing scenario. This information is used to trick or compel the target into clicking on and engaging with the email. The goal is to get them to provide information or perform a specific action. Because these emails are so highly customized, they often can avoid traditional spam filters.
Vishing
A vishing attack is simply the phone-based variant of phishing, or what’s known as “voice phishing.” This type of attack occurs when a criminal calls via phone and tries to get you to either provide personal information or perform an action. Think of those notorious fake IRS phone calls where they tell you that you owe X amount in taxes and threaten to have you thrown in jail — a consequence you can avoid by simply making a “payment” using pre-paid gift cards. Yeah, that sounds legit. Who knew Uncle Sam was such a big fan of Amazon or iTunes?
Other forms of vishing include criminals pretending to be your bank, credit card company, or even Marriott hotel and telling you that you’ve won a free vacation — all they need is some personal information.
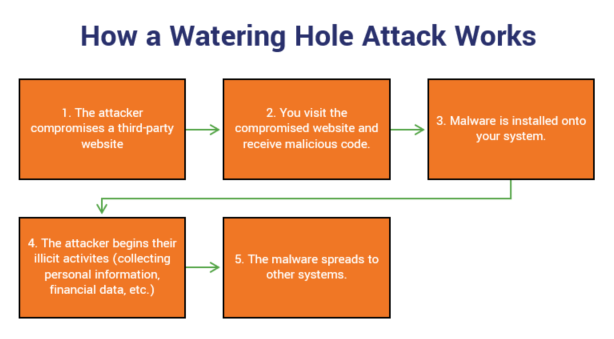
Watering Hole Phishing
This type of large-scale phishing attack targets organizations by identifying specific websites that they frequently visit — such as a vendor’s site — and infects one or more of those sites with malware. In 2018, a watering hole campaign compromised at least 21 major government and media websites in Southeast Asia.
Whaling

In some ways, whaling is the lovechild of a spear phishing attack and a quasi-CEO fraud attack. Don’t follow? Rather than targeting low- to mid-level employees, whaling attacks target CEOs and other high-level executives with spear-phishing attacks. This is sometimes done while pretending to be a third-party company or by impersonating an executive at another office within the targeted organization.
But what do virtually all of these types of phishing have in common? They all use some type of technology, and many employ social engineering tactics.
Here’s one example of a recent phishing email that targeted one of The SSL Store’s vice presidents:
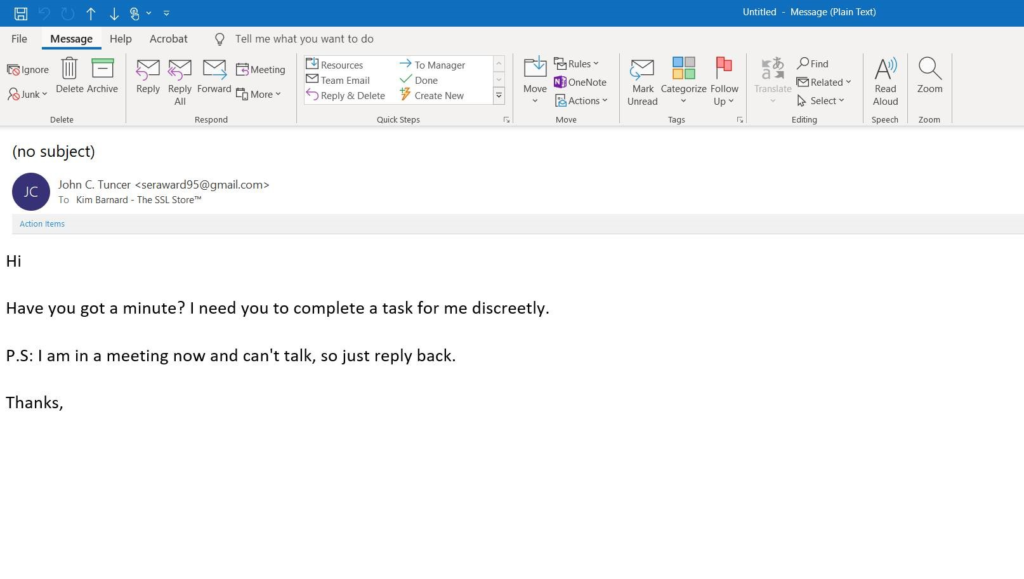
Who Are the Victims of Phishing?
Where phishing is concerned, there’s always more than one victim. Victims include:
- the person or company being targeted,
- the company being imitated, and
- in phishing cases that result in the loss or breach of employee or customer data, employees and customers are victims as well.
Top 25 Most Commonly Impersonated Brands Used by Phishers
When phishers use the names and brands to trick their victims, there are certain corporations they use more frequently than others. The Q2 2019 Phishers’ Favorites report from Vade Secure shows that Microsoft tops the list of the 25 most impersonated brands in phishing attacks. The list of the brands most commonly impersonated in phishing is as follows:
- Microsoft
- PayPal
- Netflix
- Bank of America
- Apple
- CIBC
- Amazon
- DHL
- DocuSign
- Credit Agricole
- Dropbox
- Wells Fargo
- Chase
- Adobe
- AT&T
- Orange
- Alibaba
- Yahoo
- Stripe
- Societe Generale
- Comcast
- OVH
How to Keep Your Organization Safe
Suffice to say, after all this, that we’ve answered your initial question, “what is phishing?” But now that you know what it is, how can you prevent them from being successful? And how can you help prevent your own organization and brand from being used by phishers to victimize others?
Unfortunately, there’s no one-size-fits-all solution when it comes to email security and stopping phish. However, there are a variety of best practices and multi-layered defenses you can implement to protect your organization. Here are several methods and strategies you can use to arm yourself in the war of email security:
Implement Regular Employee Awareness Training
Not to sound cruel or completely pessimistic, but the thing that comes to mind is this unfortunate truth: There’s a sucker born every minute, and some of them likely work for your company. This is why it’s important to inform them through cyber awareness training.
Awareness training should cover multiple areas of consideration, including:
- Learning how to “read” emails to identify spam, phishing, and other malicious emails (looking for suspicious language, spelling errors, reviewing the “from” field to ensure it’s the sender’s legitimate email address, etc.).
- Learning how to use email signing certificates to sign and encrypt their emails;
- Not responding to emotionally to emails (not engaging with them out of curiosity or acting without forethought due to fear or panic).
- Taking the time to verify that the email came from someone by contacting them directly through other communication channels (take the time to call the person using an approved number or walk over to their office to speak with them).
- Instructing employees on how to react to phish by not responding to the emails or clicking on any links or attachments, as well as flagging the messages as spam.
This type of training, which should be held every three to six months (ideally), should be mandatory for everyone with access to your network and databases. This includes all full- and part-time employees (including CEOs and other top-level executives), board members, and interns.
Create Security-Oriented Computer Use and BYOD Policies
Although it’s not ideal, it’s not uncommon for employees to use their employer’s devices (laptops, iPads, smartphones, etc.) for personal purposes such as checking their personal email and social media accounts. This includes checking their email and social media accounts using those devices. Or, your organization may even allow employees to bring their own devices (BYOD). While this can initially save money in the short run, if those devices are infected and are used to connect to your network or log in to databases, you can face costly consequences in the long run in terms of data breaches, ransomware, and security noncompliance fines.
Implement Effective Access Management Policies and Processes
One way to reduce the potential impact of phishing attacks is to limit access to sensitive systems to those employees who actually need access to do their jobs. Dave in accounting doesn’t need access IT administrator access. And Sally in sales doesn’t need access to payroll or personnel records.
In addition to ensuring that only the employees who have access actually need it, periodically review the list to ensure that those employees’ access needs have not changed. For example, if Paul in human resources quits or is fired, deactivate his credentials and access immediately to prevent him from having access to any sensitive data.
Use a Combination of Effective Email Protection Technologies
Truly savvy organizations use a multi-layered approach to email security. We discuss several of these methods in our Email Security Best Practices eBook, which was created as a resource to help protect you from phish as well as keep you from being imitated in phishing emails that are sent to others. We’ll briefly discuss them below, but for more in-depth information — as well as information about how to implement them — you’ll want to check out our eBook:
Some of these technological methods to prevent being phish and used in phish include:
- Blacklists and whitelists. Every organization needs to maintain a living, breathing list of banned or approved email addresses. Blacklists allow you to filter out harmful messages based on their sender’s domain, email address, or IP address/range. Whitelists, on the other hand, inform your servers and filters about which emails to allow through using the same qualifying factors.
- A secure email gateway (SEG). This is typically an on-premises appliance or cloud service that intercepts emails and filters them for spam, malware, and phishing.
- Simple mail transfer protocol (SMTP). Want to mitigate spoofing within your own organization? There’s a tool for that. SMTP is frequently used by organizations to defend internal email from spoofing by setting up custom rules in email clients.
- Sender policy framework (SPF). This protocol, referenced by a DNS entry, helps you to discern legitimate emails from fake ones for emails you receive from regular contacts such as vendors. It does this indicating whether an email from a sender’s IP address truly came from the legitimate vendor’s network and not a different one. This means that so long as an email is sent from an IP address in the DNS’ SPF record, it’ll be allowed through. This is also useful for helping to prevent your own domain from being used in copycat phishing emails by cybercriminals pretending to be you. SPFs, which are ideal for smaller companies or organizations, work hand-in-hand with DKIM. It’s important to note, however, that SPFs only work with mail servers that check SPF records.
- Domainkeys identified mail (DKIM). Much like SPF, DKIM involves updating your DNS records; however, it includes the use of a cryptographic key that signs and validates emails as legitimate (because the signature shows they’re authorized to be sent by your server). Using SPFs and DKIM together will also help you get the most out of the next tech recommendation.
- Domain-based message authentication, reporting, and conformance (DMARC). This email authentication, policy, and reporting protocol is used to help detect and mitigate proof and forged sender addresses. There’s far more to DMARC than that. But without getting too much into the weeds, the general idea is that having a strong DMARC reputation helps to allow more of your legitimate emails to reach their intended recipients and help them be less likely to fall for phish that imitate you.
- Personal authentication certificates, or S/MIME certificates. These certificates assert identity and help to enable email encryption. S/MIME, which refers to secure/multipurpose internet mail extensions, is a protocol that enables secure email by protecting the integrity of the email data through at-rest and in-transit data encryption.
Final Thoughts
Having effective email security is no longer an option. If you want to protect the reputation and standing of your organization, the privacy of your employees’ and customers, and the integrity of your data, then these are all steps that you need to implement now. Now that you know what phishing is and how it works, there’s simply no excuse to do nothing.
Phishing attacks aren’t going to stop. Cybercriminals are going to continue to use them until they’re no longer effective, and they move on to using other tactics. The longer you wait to protect your organization against phish, the more at risk your business will be to phishing attacks and the associated risks that come with them.




































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown