LinkedIn Phishing: This Is Why We Can’t Have Nice Things
LinkedIn has become one of phishing’s biggest resources.
As social media has evolved over the last decade and a half, LinkedIn has settled in as an integral part of the business community. It’s the platform “for professionals” and facilitates marketing, hiring and a whole range of other business. It’s terribly convenient. But there are perils associated with that convenience.
One of them, in particular, is LinkedIn phishing.
In the past we’ve talked about how LinkedIn is a great resource for spearphishing, providing criminals with useful information about targets and companies. But that’s just the tip of the iceberg when it comes to LinkedIn phishing.
So, today we’re going to discuss some of the more popular permutations of LinkedIn phishing, why LinkedIn is such an attractive option for phishers (phishermen? phisherpersons? Bueller?) and how you can make sure not to get ensnared by it.
Let’s hash it out.
Why Phish via LinkedIn
It’s not all that mentally taxing to figure out why LinkedIn lends itself to the pursuit of phishing. LinkedIn offers Phishers a cornucopia of information. People also have a tendency to trust LinkedIn more than they might trust other social media sites.
Specifically, we’ve distilled it down to three main factors:

- People trust LinkedIn – As we just stated, people tend to associated a degree of professionalism and trust with LinkedIn that other sites don’t enjoy. According to Business Insider, LinkedIn is the most trusted social media site by a wide margin. The natural tendency when you trust something is to let your guard down, which is exactly what criminals are counting on.
- Lack of verified status – While LinkedIn does offer premium accounts that show a little “IN” logo on people’s profile pages, that’s not the same as providing verified identity. Anyone can pay for a premium membership. While other sites like Twitter and Facebook put a little check next to the name of verified people, LinkedIn doesn’t. That muddies the water for criminals.
- Enterprise Data is valuable – The information that’s present on LinkedIn can be exceedingly useful. You’re not just learning about an individual, but also the company they work for and even what conversations it’s having.
Let’s look at what you can glean from LinkedIn if you want to pursue spearphishing. Spearphishing is a certain variant of phishing where you tailor your attack to a specific individual, oftentimes posing as a coworker, recruiter or someone the target might reasonably trust.
10 Types of Phishing Attacks and Phishing Scams
There’s more than just one type of phish. Knowing what to look for can help your organization from getting swallowed. Here are 10 different types of phishing.
Obviously this includes things like:
- Name
- Place of employment
- Position
- Other connections
But even something as simple as a company email address can be exploited. How? Aren’t email addresses fairly low-risk? Generally, but if your company is like ours, it uses certain syntactic conventions when assigning email addresses. Many organizations do. We use the employee’s first and last name, separated by a period. For other organizations it might be a first initial and a last name or some other variation.
A criminal can discern that when they see your email address and then use it to figure out other addresses within the company. You can probably see how useful that might be.
Even things like what content and updates a person has been sharing can be used against them. Say for instance the target has been posting a lot of updates regarding a new software rollout. Now the criminals know about a topic that can be used to grab the attention of the target – something they’re talking about a lot – further enhancing their odds of success.
But as we stated at the outset of this article, things have evolved well past just using someone’s LinkedIn profile and connections to harvest data for a spearphishing operation.
Let’s start with phishing that purports to be FROM LinkedIn and then move to phishing that’s done ON LinkedIn.
LinkedIn Phishing: Spotting Fake LinkedIn Email
Ok, so now we’ve covered all the information that can be gathered from LinkedIn, let’s talk about how people use the platform to phish – starting with emails that claim to be FROM LinkedIn.
Let’s use an example from KnowBe4, which is located just down the road in Clearwater (shout out to the Tampa Bay area):
Earlier this year a torrent of LinkedIn spam messages was sent on January 3rd, so many that at one point during the day a full 25% of all malicious email being sent was these LinkedIn phishing scams.
According to Cisco, which sent out a notification about the emails:
Starting this morning, at 10am GMT, cyber criminals sent spam email messages targeting the LinkedIn social media community.
Victims are emailed an alert link with a fictitious social media contact request. These messages accounted for as much as 24% of all spam sent within a 15-minute interval. Clicking the link, victims are taken to a web page that says “PLEASE WAITING…. 4 SECONDS” and redirects them to Google. During those four seconds, the victim’s PC is infected with the ZeuS data theft malware by a drive-by download. ZeuS embeds itself in the victim’s web browser and captures personal information, such as online banking credentials, and is widely used by criminals to pilfer commercial bank accounts.
Organizations should encourage individuals to delete such requests, especially if they do not know the name of the contact. This is the second spam attack this month, preceded by the “Here You Have” email worm a few weeks ago. Cisco expects to see more spam messages containing malware sent to organizations to collect personal information.
This is just one of many such attempts to mislead people using emails designed to look like they’re from LinkedIn. This kind of brand phishing is nothing new, but it’s incredibly effective.
The reason we used the KnowBe4 example (beyond the whole Bay Area connection) is that KnowBe4 provides phishing simulations to organizations, which provides awesome data points on the efficacy of these campaigns.
And in KnowBe4’s simulations, LinkedIn is used in 56% of the top phishing emails.
How to Spot a Fake LinkedIn Email
There are some solid tips for trying to discern whether an email is really from LinkedIn, but there’s only one fool-proof piece of advice we recommend above all others. Here are some tips, first:
- Check the domain of the sender, not just who it says it’s from but the actual address it originated from. If the domain doesn’t say LinkedIn, junk the email.
- Grammar and spelling matter. LinkedIn is a billion dollar company, it doesn’t send out poorly worded or grammatically incorrect emails. Period.
- Check the logos and branding, LinkedIn pays very specific attention to aesthetics. Outdated logos and formatting issues are a dead giveaway.
- Hover over any links with your cursor and make sure they resolve to LinkedIn URLs. This should be another dead giveaway.
Also, trust your spam filter. If an email is in your junk folder, it’s probably for a reason. Make a rule to trust LinkedIn notifications originating from the proper domains and trust your filters to do their job.
According to LinkedIn, any legitimate email it sends you will include a unique, tell-tale sign:
In our messages to you, we include a security footer message with your name and professional headline to help you distinguish authentic LinkedIn emails from “phishing” email messages. “Phishing” emails often look very similar to legitimate ones, but they likely wouldn’t have this personalized information and may also contain links that direct you to malicious sites instead of LinkedIn.
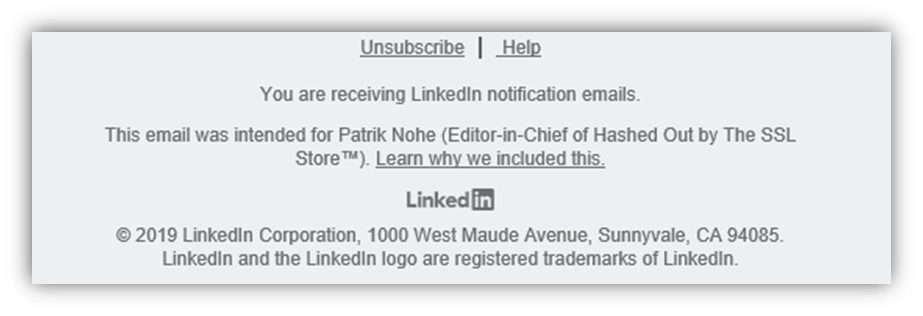
LinkedIn also uses DMARC and signs it emails.
Ok, now here’s the fool proof piece of advice on spotting fake LinkedIn emails: ignore all email from LinkedIn.
When LinkedIn sends you a notification – a real notification – it also places that information in the “notifications” section of your account. Any legitimate email from LinkedIn will also have a matching notification on the site. If you think something happened that needs your attention on LinkedIn, navigate directly to LinkedIn yourself. Type in the URL. Log in. You’ll see if the notification was legitimate immediately. LinkedIn phishing is a pernicious enough problem that you should look at all LinkedIn emails with an air of suspicion and use the website to verify.
Phishing ON LinkedIn
Ok, now let’s talk about phishing that’s done on LinkedIn itself. This typically takes the form of fake profiles, fake connection requests and malicious links.
We want to believe that everyone on LinkedIn is acting in good faith. That’s not the case though. There are, unfortunately, a great number of fake LinkedIn profiles that exist entirely to defraud people and infect devices.
So, let’s talk about vetting your LinkedIn connection requests.
How to Spot a Fake LinkedIn Profile
First things first. NEVER blindly accept a LinkedIn connection request from someone you don’t at least know of. What I mean by that is that if you haven’t met that person at some point, or are at least familiar with their work/role in your industry – perform a little due diligence before connecting.
It’s not bad to think critically, “why would this person want to connect with me?” And I don’t mean that in a sort of “whoa-is-me” self-loathing kind of way – I mean that in life everyone is angling for something and if you can’t figure out what that something is, you should be skeptical.
So, what should one check for?
Well, let’s preface by saying that not all of these are, by themselves, disqualifying. But they’re things that should send up red flags, especially if a profile checks several of these boxes.
- Look out for common names – The problem with a name like John Smith is that it’s difficult to pin down with a Google search. There are tons of John Smiths, making it easier for a fake John Smith to hide. If someone has a common name, it doesn’t mean you should immediately distrust them – it just means you need to look a little closer.
- Image search their profile picture – Fake profiles generally use fake images. It wouldn’t make much sense to use your real picture to commit fraud – and most criminals are smarter than that. So they either rip off images from a real person or use stock photos. This can be sniffed out easily using a Google image search. If the search doesn’t kick up any results, or it kicks up results related to a person by that same name – that’s a good sign. If it kicks up a listing on a stock photo site or someone else’s social pages – run.
- Check their company – This can be of limited value given that you don’t have to verify employment to list it on LinkedIn, but it can serve as an immediate disqualifier if said company doesn’t seem to exist. Companies, real companies, are registered with their local and national governments and have extensive digital footprints. Fake companies don’t.
- Look at their other connections – This can be useful in determining the legitimacy of a profile, too. Don’t just look at the number of connections, look at who they are and where they work. Typically, there will be lots of connections from their own company, their own community, wherever they went to school and from their own industry. If you don’t see that, you should be skeptical.
- Look at their profile – We listed this last because a good LinkedIn phishing account is likely going to bring a pretty convincing profile. That’s one area the criminal has direct effect over. Still, it’s worth just double-checking that the profile is complete and passes the smell test. That means looking for key indicators like their employment history, any recommendations others have made about them, updates and shares – the profile needs to look active and legitimate. Again, you need to go off more than just how the profile looks. But if it looks fake, it probably is.
If you think you’ve found a fake profile, you can report it here.
LinkedIn Phishing Using Messages and InMail
Just connecting with a fake profile doesn’t ensure you’ll get phished. it just gives the criminal an attack vector. That’s why we started with spotting a fake profile. That’s going to be your first and best line of defense.
There are two kinds of messages that can be used for LinkedIn phishing on the platform itself. Regular messages are typically sent between connections or can be attached to a connection request. InMail is a marketing tool. It’s a lot harder to phish with InMail because LinkedIn does a pretty good job of regulating it and it costs money. Criminals don’t like spending money.
Anyway, as we just stated, it’s possible to message someone without being connected. So, let’s cover that first. I won’t go so far as to say it should be considered best practice, but I don’t click links or download anything from LinkedIn messages if they’re not sent from a connection. Categorically. If I think it might be legitimate, I’ll make it a point to reach out and connect with that person before I even consider taking whatever action they’re requesting of me.
I look at it like this, I know foreplay is a lost art but if you ask me to do something for you the very first time we have contact I’m going to be skeptical until I get a better grasp on your motivations.
You don’t have to be as cynical as I am, but you should be as skeptical.
Now, aside from random messages from strangers, let’s say just for the sake of this exercise that some exceptionally clever criminal does manage to trick you into accepting their connection request and now they’re messaging you.

What then?
Again, be skeptical. Altruism isn’t a concept that you see a whole lot of in the business world or in capitalism, in general. So if someone reaches out to you with an unexpected offer, or the promise of something free – that should at least give you pause.
Ask yourself again, what is the point of sending me this? Could this pose some kind of risk? Do I trust this person?
There is no single litmus test for this, rather it’s a range of factors that need to be considered alongside one another. It’s better to not click on something legitimate and to follow up via other channels than to click something malicious on the off-chance it might be legitimate.
Err on the side of caution.
LinkedIn offers the following advice on staying safe:
- Don’t share personal information via messages or InMail
- Don’t enter information by clicking on links, navigate to the site directly instead
- When applying for jobs, be wary of requests to send personal information to addresses that aren’t associated with their company
- Use caution when clicking links (probably doesn’t need to be said, but some people need it spelled out)
- Make sure any messages from LinkedIn include the security footer.
What Is LinkedIn Doing About LinkedIn Phishing?
Obviously, LinkedIn is addressing phishing issues that occur on, or purport to be from its own platform. But, as is the case with all cybercrime, it’s a perpetual game of cat and mouse.
LinkedIn has built an entire website dedicated to protecting its users from this kind of malfeasance, in addition to creating reporting mechanisms that people can use to report fake profiles and phishing attempts.
If you receive a LinkedIn phishing email, forward it to: phishing@linkedin.com and make sure to block the address from contacting you in the future.
This problem isn’t going away, so you need to learn to be vigilant – even in the places you don’t think you’d have to be.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown