Unicode Domain Phishing: How you can protect yourself
Even the most vigilant internet users are susceptible to this IDN homograph attack
A new wave of Unicode Domain Phishing attacks are tricking even the most seasoned of internet veterans thanks to its clever use of homographs.
For those that don’t know a homograph is a set of two or more words that are spelled the same but have different meanings and origins. In this case, homograph is an imperfect descriptor, but it’s still sufficient.
To execute a Unicode Domain Phishing attack, you first need a Unicode domain. Typically, the URLs you type are in ASCII, that stands for American Standard Code for Information Interchange. However, in 2003, a specification was added to allow Unicode characters to be used in domain names. Unicode is an industry standard for encoding text expressed in most of the world’s written languages. The idea behind this was to give international internet users the ability to follow links in their own language.
But, as with everything on the internet, somebody found a way to exploit this.
Researcher Xudong Zheng published a proof of concept last year that highlights the issue. In the POC, Zheng uses Unicode to produce a web page that resembles Apple’s. To do this, he created a domain with Punycode, which allows for Internationalized Domain Names. He then mixed in Unicode with ASCII to create a website that actually says “Apple.com”
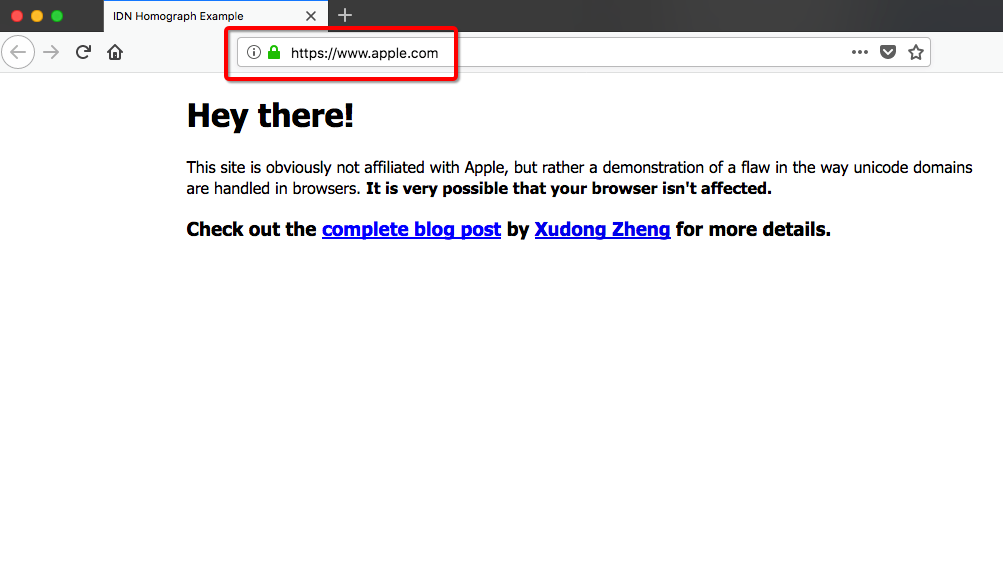
An “A” in ASCII (U+0061) is different from a Cyrillic “A” (U+0430), but the browser will render them both the same in the address bar. Now, typically, browsers will display the Punycode form to limit any confusion with the real Apple.com. However, Zheng found that the defense mechanism in Chrome and Firefox didn’t work if every character is replaced with a similar from the same language.
So, when Zheng registered a domain at: xn–80ak6aa92e.com, it bypasses the browser filters and renders “Apple.com” in the address bar. To make his POC even more compelling Zheng tossed a DV SSL certificate on his site. Now it looks like Apple, and it has the padlock so it must be safe, right?
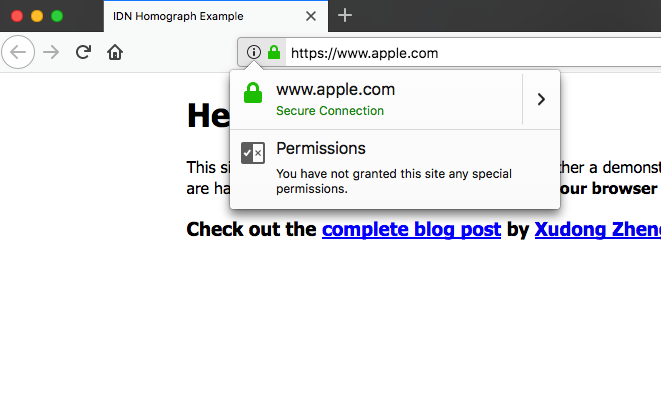
Zheng didn’t try to duplicate Apple’s homepage because he was just showing a proof of concept. But be honest, were that an actual phishing attack it would have fooled pretty much anyone.
Regardless, this is really just the tip of the iceberg. There are tons of ways attackers can take advantage of Unicode to create this Homograph attacks.
How to protect yourself from Unicode Domain phishing attacks
If you’re a Google Chrome user you’re set. Google addressed this issue in version 58.
Firefox users can prevent this from happening by typing “about:config” into your address bar. Then, in the search box type “Punycode.”
If the value of the entry titled: network.IDN_show_puny_code is false, double-click it to change it to true.
This will make your browser display the punycode, not the ASCII representation of it.
Here are a few additional security tips:
- Use a password manager – If you’re on a Unicode Domain, your password manager won’t be fooled. It also won’t populate the login fields with your data. When this happens, this should be a huge red flag about the page you’re visiting.
- Don’t follow links – There are plenty of ways a link can fool you, so for important business, or on social media sites, always type the URL in manually. This way you know you’re directing yourself to the correct domain.
- Turn on Two-Factor Authentication – 2FA can’t protect your login credentials, but it can add a much-needed layer of security should your login credentials ever get compromised. It might be a pain to have to enter a code everytime you log in to your mail account, but it will keep your account safe if someone steals your credentials.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown