Homograph Attacks: Chrome Extension Detects Unicode Domains
Unicode Domain Phishing can fool even the most perceptive internet users
A new Google Chrome extension, released by Phish.ai, detects non-standard Unicode characters in domain names and warns users about the potential for a homograph attack. A homograph attack, sometimes known as Unicode Domain Phishing, uses non-standard characters to mimic the spelling and appearance of legitimate domains. Users think they’re logging into a trusted website when they’re actually having their credentials stolen or possibly even being infected with malware.
How does a Homograph Attack Work?
A homograph attack essentially creates a look-alike URL by using international characters that are different, but look similar to English characters. I wrote an article about homograph attacks and Unicode domain phishing last month if you’d like to go in-depth, but here are the basics.
The internet was designed around the English language. So as more and more non-English speakers have come online, considerable effort has been made to provide support for other languages. One of those efforts is Internationalized Domain Names (IDNs), which allow for domains and TLDs to be registered in other languages.Unfortunately, one of the unintended side effects of this was the advent of homograph attacks.
Here’s how it works, from the standpoint of your computer the American Standard Code for Information Interchange (ASCII) “a” (U+0061) and the Cryillic “a” (U+0430) are entirely different characters, but they are displayed in exactly the same way. That means to the human eye, it’s impossible to tell the difference.
You can probably see where this is going. By registering a Unicode domain, you can use non-ASCII characters and criminals have figured out that you can create some extremely convincing spoofs using this method.
Shouldn’t the Browsers Detect This?
Yes, but so far, the results have varied. Some people believe and have even proposed that browsers should not display IDNs at all, but that has been criticized as “unfairly prejudicial” against non-English users. Engineers at Google have argued that this issue is best handled at the domain registrar level.
Still, the browsers have made efforts to deal with this problem. Some browsers have begun replacing Unicode characters with Punycode, which is an ASCII-based rendering of Unicode characters. Microsoft Edge does this as a default. Last year, researcher Xudong Zheng published a Proof of Concept that fooled both Firefox and Chrome into showing a spoofed apple.com URL.
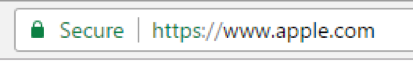
Both browsers quickly worked on a fix. Mozilla Firefox users can go to about:config and enable “IDN_show_punycode” to add a layer of protection against homograph attacks.
Google, meanwhile, improved its browser mechanism for displaying Unicode domains in version 58. That same apple.com URL now displays like this:
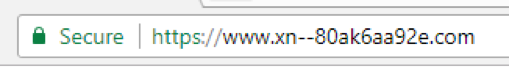
That being said, it’s still not perfect. Chrome displays the Punycode version of the URL in the Title bar, but not the address bar itself.
Phish.ai designed its extension to help fix that. In what would best be described as a love letter to subtlety, a big red window will warn users every time they attempt to access a domain that’s using Unicode characters.
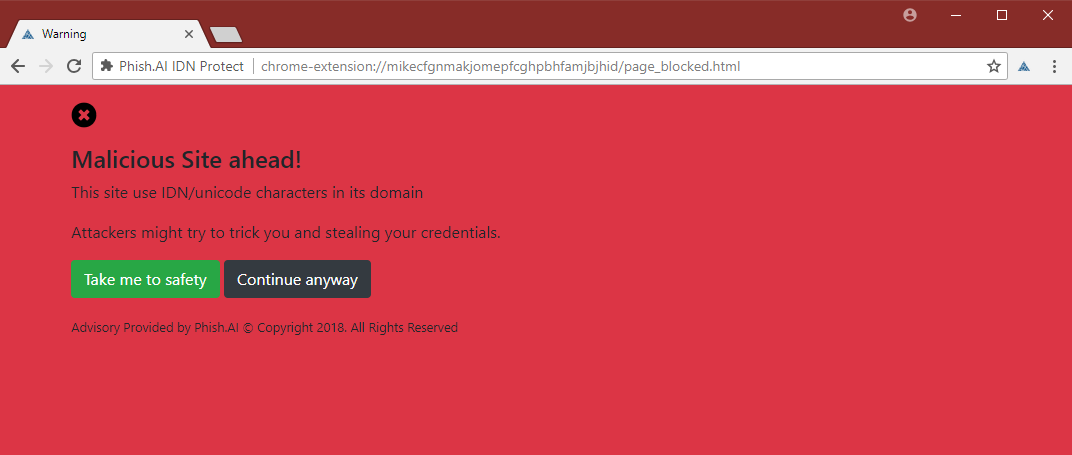
Much like Google’s Safe Browsing alert, the warning message will block access to the website and will require a response from the user to continue. If you would like to start using Phish.ai’s extension, it’s in the Chrome Web Store, or you can find the source code on GitHub.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown