58% of Phishing Websites Now Use HTTPS
Phishing saw a sharp increase in Q1 2019… again.
Stop me if you’ve heard this one before: incidence of phishing have increased since last quarter. Again. Just like the quarter before that. And the quarter before that. Dating all the way back to the days of the early internet when a down-on-his-luck Nigerian prince first sought financial relief from the well-to-do denizens of AOL and Hotmail.
Nowadays phishing has evolved. Substantially. These are no longer shot-in-the-dark style emails that somehow manage to elude your spam folder. These are now highly-tailored feats of social engineering that target specific industries, companies and individuals. Phishing, the simple act of ripping someone off with a grammatically questionable email has grown up into CEO fraud, whaling, spearphishing, etc. It’s become the most common delivery mechanism for malware and other cyber attacks. 91% of cyber attacks now start with a phishing email.
In many ways phishing is like a gateway hack. It starts off as just a few innocent spearphishing emails among friends, but before you know it, you’re huddled over a laptop in an Eastern European internet café trying to scrape together enough of a botnet to launch one more DDoS…
…anyway, according to the Anti-Phishing Working Group (APWG) phishing is up again in Q1 2019 and nearly 60% of the phishing websites the study turned up were using SSL/TLS – sporting the green HTTPS padlock. So, today we’re going to take a look at the study, break down some of the trends and offer a little insight on shoring up those defenses.
Let’s hash it out.
Phishing in Q1 2019: The big takeaways
The APWG is a non-profit industry association that was founded in 2003. Its membership comprises over 2,000 organizations across the world. It publishes quarterly reports on phishing that look at the industries targeted, total number of phishing emails received and how many new phishing websites have been created over the last three months. Keep in mind, these are not global figures – this only pertains to the cases and campaigns that were reported to the APWG.
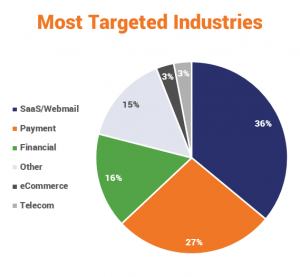
For Q1 of 2019, the APWG came away with three major takeaways (actually, four – we just aren’t going to focus on the case study in Brazil). We’ll mention them here really quickly and then drill down into the HTTPS phishing issue – given that it’s especially relevant to us.
Key takeaways:
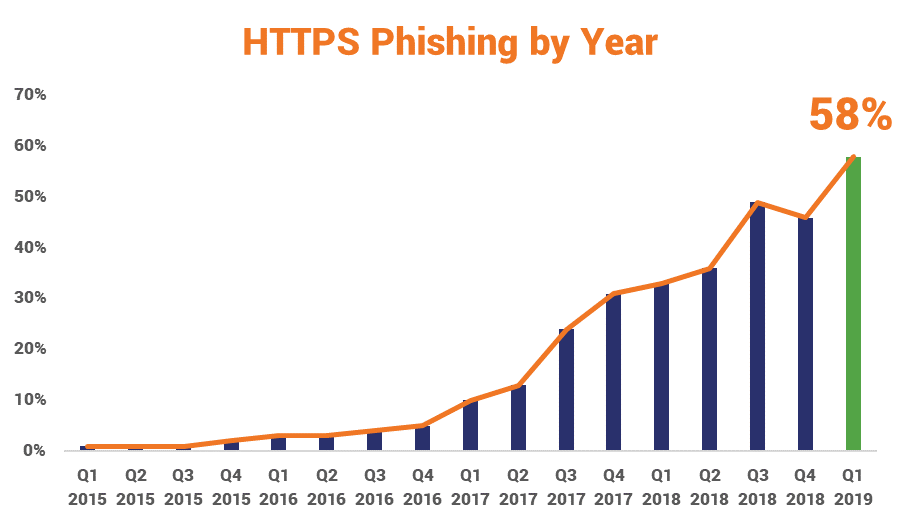
- SSL/TLS certificates are still being widely used by phishing websites, aided by free offerings from CAs like Let’s Encrypt, and hosting companies like cPanel. 58% of phishing websites are now served via HTTPS.
- The total number of phishing websites increased substantially over Q3 and Q4 of 2018, likewise the number of phishing websites increased in each month so far in 2019, peaking in March – the final month of the quarter.
- Phishing targeted Software-as-a-Service and Webmail clients the most over the first quarter of 2019. This is the first time that segment has appeared ahead of the payment industry since the APWG has been doing the study.
58% of Phishing Websites now use SSL/TLS & HTTPS
We’ve been raising the flag for a few years now on HTTPS phishing. Admittedly, things have gotten a lot better thanks to the browsers – specifically Google – deprecating the “Secure” visual indicator that was appearing anytime a website used HTTPS.
This was exceedingly dangerous because it allowed phishing websites to display a Google-given icon that proclaimed they were secure. People conflate secure and safe. Phishing exploded. It was a problem.
Now Google has gone the other way and started to deprecate HTTPS visual indicators all together, claiming that asking the user to glance at the address bar to make some kind of a security decision is “user hostile.” I would ask how burying peoples’ privacy preferences in your settings menu is any less “user hostile,” but let’s not split hairs.
Regardless, HTTPS phishing is a major problem for the internet as a whole and this industry specifically. However, given that CAs aren’t supposed to be in the business of policing content, there’s not a whole lot else to be done. Bad guys can get encryption, too. Well, at least DV SSL encryption.
Because I don’t want to say this entire trend can be attributed to free DV SSL certificates, but… this entire trend can be attributed to free DV SSL certificates.
This is why many SMBs and Enterprises have shifted to Organization Validation and Extended Validation SSL certificates. DV SSL doesn’t assert any organizational identity, it just verifies a domain name. By asserting identity with an SSL/TLS certificate organizations can help their customers avoid being phished and can ensure their employees aren’t duped by spoofed websites.
Still, HTTPS phishing has shifted from just being a startlingly large minority into – what is becoming – a highly prevalent tactic.
Websites? I thought we were talking about email…
Oftentimes the phishing email is just phase one of a much larger campaign. The email is designed to get the target to take the intended action. That could be something as simple as opening an attachment, or it could include following a link to a phishing website.
While occasionally you’ll see a watering hole-style phishing site that is just set up to take advantage of anyone unfortunate enough to navigate to it, most of these pages are designed only to be found via the links they generate and put in phishing emails. There’s a couple of main reasons for this:
One, you would never get these phishing websites to rank well enough to see any kind of results. SEO is a massive industry, it takes months and years to get results. Phishers don’t have that kind of time.
The second reason, and the more immediate one, is that Google and various other blacklists and watch dogs are actively seeking out phishing websites so they can block them and protect internet users. That’s why these pages are hidden, de-indexed, and hopefully kept away from the prying eyes of Google.
In fact, most of these phishing sites have a shelf life of just a few hours.

That being said, while they can’t all be winners (just like we can’t all be astronauts), some of these pages show an impressive level of detail, even going so far as to mimic social buttons, site seals and trust indicators.
One indicator they have not historically been able to manipulate though – at least not easily – was the green padlock icon that was associated with HTTPS. It hasn’t always been the most effective, but internet users have been trained to look for that padlock.
Unfortunately, phishers don’t keep very good statistics. There is no NetCraft for phishing where you can track success rates across industries and campaigns. It would be nice, but that level of transparency is rarely seen from criminals.
But, given the steady rise in the percentage of phishing websites that we’ve seen over the past few years, I think it would suffice to say HTTPS phishing works better than non-HTTPS phishing.
And here’s the thing, it would be naïve to think that an SSL/TLS certificate itself improves the viability of a phishing campaign. There needs to be a lot of other things that have to go right to achieve the desired results. Other brush strokes on the canvas. But when paired with all the other little touches that make a phishing site feel believable, that green padlock and HTTPS can be just enough to confirm someone’s errant impressions. The perfect final touch.
That’s why once you get to that website, all bets are off.
So, it’s best to prevent it from ever getting past that first email.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown