The DNC Hacking Scandal Happened Because of a Typo
Recently, Security Breaches Have Been Costing Organizations Big-Time.
A new report from The New York Times revealed the Democratic National Committee’s severe mis-management of cyber security as well as poor communication with law enforcement investigators. The mismanagement started in late 2015 when the FBI notified the DNC about potential phishing and hacking attacks.
At the time, a full investigation may have caught early intrusions into its network. But the DNC’s Director of IT admitted that the organization “didn’t look too hard” into the activity on its network.[1] Ironically, the DNC was concerned that the agent was not really with the FBI. It wasn’t until March 2016 – seven months later – that any DNC employees met with an agent in-person, even though their offices were less than a mile apart. But at that point it was too late.
It’s an excellent report, that goes in-depth into the entire Democratic National Committee hacking scandal, but we want to focus on one specific detail that was absolutely shocking.
The bombshell came from Charles Delavan, a Clinton campaign aide. When John Podesta, the Chairman of the Clinton campaign, received a phishing email, it was forwarded to Mr. Delavan for verification.
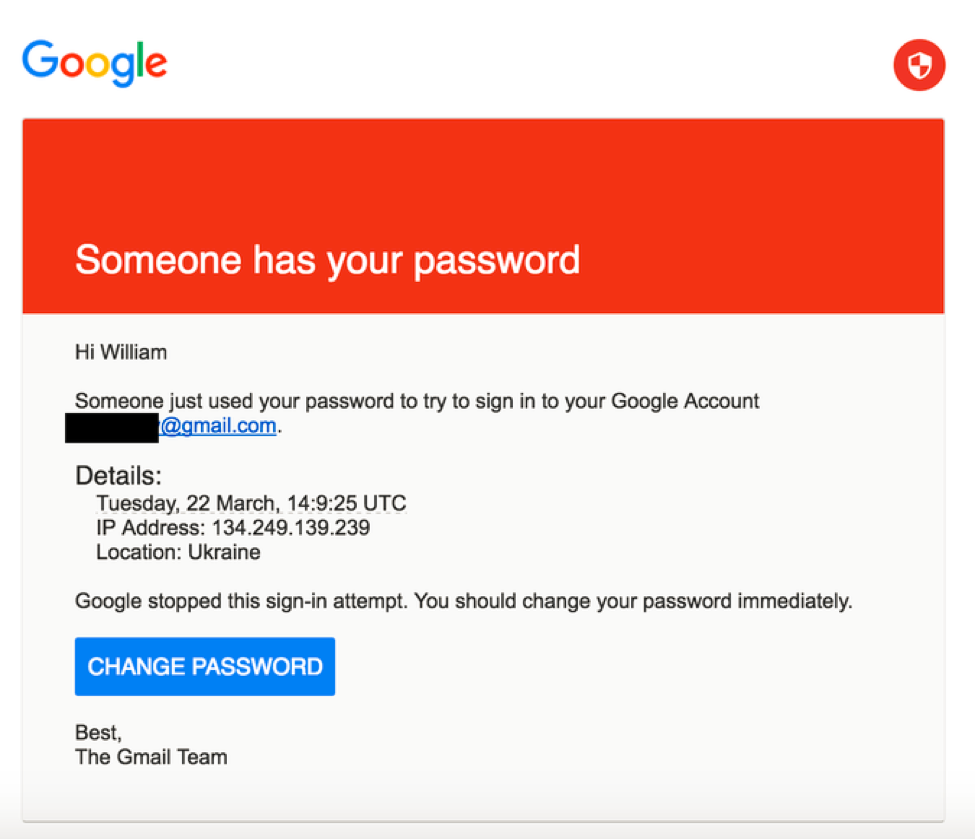
The phishing email claimed to come from Google, alerting Podesta of failed log-in attempts to his account originating from the Ukraine. It asked him to click a link and update his password immediately.
Delavan wrote back, “this is a legitimate email.” But, per Delavan, it was a typo—he meant to write illegitimate. The typo went unnoticed, and Podesta’s password was “changed” via the phishing site, giving the hackers full access to over a decade’s worth of communication—60,000 emails.
Podesta’s emails were then turned over to and leaked by WikiLeaks. They revealed unsavory information about the Clinton campaign, which ended up hurting it for months leading up to the election.
There has been speculation that Podesta’s email scandal even propelled Trump to victory. Could a successful phishing email have decided the election? Perhaps even more important than the answer is the fact that we even have to ask that question.
The Email That Phished Podesta
The email that successfully phished John Podesta’s account was sent in March 2016. The subject line stated “Sign-in attempt was blocked,” and instructed him to change his password by clicking a link inside the email.
The hackers used bit.ly, a popular link-shortening service, so they could track when someone clicked it. Bit.ly’s analytics show it was clicked twice in March.
The phishing website’s URL was myaccount.google.com-securitysettingpage.ml. The subdomain mimics the URL for Google’s account management page. Notably, it looks like the phishing site was not using HTTPS, which should have been an automatic red flag.
However, the unfortunate typo made by Clinton aide Charles Delavan convinced Podesta, or one of the other staffers who had access to his account, that it was a legitimate email. In his email, Delavan wrote “He can go to this link: https://myaccount.google.com/security to do both. It is absolutely imperative that this is done ASAP.” But instead of following the link Delavan provided, the staffer clicked the link in the phishing email.
A reply sent by another staffer to Milia Fisher, a “special-assistant” at Hillary for America, said “The gmail one is REAL. Milia, can you change [his password] – does JDP have the 2 step verification or do we need to do with him on the phone? Don’t want to lock him out of his in box!”
It seems that two-factor authentication was never turned on for Podesta’s account, or it was turned on too late.
American Politicians Have Ignored Web Security for Too Long
We get complacent with bad security, because it seems like you can go without it.
Hillary Clinton’s private email server did exactly what she needed it to – it let her use the email she wanted. It did that job well, every day, for months. The fact that it was woefully insecure was not a problem, until it was hacked.
But this is bigger than a single presidential campaign.
This entire scandal has made it obvious that the American government – from party organizations to domestic security agencies – are not taking digital security seriously. How, in 2016, do we have a single agent making half-hearted calls as the only outreach about Russian hacking efforts?
Why did Podesta – and every staff member on the Clinton campaign – not have two-factor authentication set up from day one? How does the State Department not have the ability to get hackers out of their network?
That’s not to say that good security is easy or simple. But it’s obvious that our government and political figures are not putting in a strong effort when Obama’s denouncement of Russian interference in our election was not as strong and “far less dramatic than the president’s appearance in the press room two years before to directly accuse the North Koreans of attacking Sony.”
There have also been failures in the technical community. The video game platform Steam requires you use two-factor authentication if you want to trade in-game items with other users, most of which are only worth pennies. But providers like Gmail do not require the same protections for email, which is perhaps the most important part of our digital footprint – 2FA is still entirely optional and one password can get you access to the entirety of your emails, documents, and photos.
Like a car with the check engine light on, insecure systems run until they suddenly and catastrophically break down completely. Ironically, bad security is binary – it’s fine until it’s not.
[1] The New York Times report identifies Yared Tamene as a “tech-support contractor.” But it has been pointed out that his official title was “Director of Information Technology.”





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown