Email Security – Part 2: Phishing and Other Falseness
Ask yourself, would PayPal really be asking me to update my password with an unbranded email originating from a strange domain?
Throughout history, people have preyed on one another’s ignorance and good nature for some sort of gain — whether monetary, power, or any other reason using lies and deception. Confidence Men are as old as time itself. Most scams can be evaded by simply recognizing the intent. Does that sound easier than it is? It does. As insight into these scams has become noted, the scam pitches became more convincing. Nothing makes recognizing career liars more difficult than having no physical interface with them. After all, human senses and intuition are useful tools when it comes to spotting scammers.
In all my experience and education regarding security in technology, one truth sticks out and has been proven time and time again: the weakest link in any line of security is the user. That, coupled with the sheer volume of possibilities, makes email a superior venue to hustle unsuspecting and trusting people.
*Sigh* Yes, Jump Through the Hoops
Comedian, John Mulaney, has a good bit in his Netflix special Kid Gorgeous about the constant scrutinization that everyone faces to prove that we are not robots (warning: profanity in Facebook video link). In it, he infers that we spend more time deciphering letters and pictures without stop signs than actually accessing our own content. It feels that way sometimes. And, we can expect that the evolution of hoop jumping will take some new twists and turns as robot programmers find a way to beat these Turing Tests (Here’s Google’s new AI having a go with success). For now, these tests bolster security and really are worth it despite the pain that we all go through when executing those lines of security.
 Other hoops, such as a MFA (Multi-factored Authentication), work well for authentication recovery/reset but are time consuming. We have had our own pains using the AWS MFA hardware that appears to lose its syncing due to lack of NTP (Network Time Protocol). However, knowing that nearly everyone else is going through similar pains is a sure sign that people are who they say or propose they are.
Other hoops, such as a MFA (Multi-factored Authentication), work well for authentication recovery/reset but are time consuming. We have had our own pains using the AWS MFA hardware that appears to lose its syncing due to lack of NTP (Network Time Protocol). However, knowing that nearly everyone else is going through similar pains is a sure sign that people are who they say or propose they are.
Despite all the hoop jumping, more than likely, everyone has had some sort of account compromised. I frequently get emails from “my brother” that start with “Hi!” There! Right there, I know that is not him. It is usually followed with something like, “Check this link out,” and is, of course, followed by some shady link. The important takeaway here: I tell him. Every. Bloody. Time. He needs to know. I need to jump through that hoop. He needs to step up his password/security but he needs to know. That’s a hoop he needs to jump through not only for his sake but for the sake of all his contacts. Sadly, because of this, that email account has made my list of shadiness and I will take the extra measure of verifying with him.
Teach Me to Scrutinize Like You
Certain emails come through and they are clearly as advertised. You know your grandmother’s written tone. You know your sales vendor’s marketing template. But when you receive an email from your brother’s account with a shady looking link? Well, that warrants some suspicion and the obvious stuff is just that: obvious. Certain cues may not be obvious, but they can certainly be spotted out. After all, spammers are not going for obvious.
 One thing to consider is that a lot, if not most, spam is generated by some sort of automated process (code or bot). That’s not to say that wording is generated by a bot, but the bot would receive instruction from the perpetrator of what the email template should say (static context), how to propagate (spread the email out), and how the dynamically generated context is sourced and placed, e.g., a spreadsheet from compromised data containing things like names, email addresses, account IDs, etc. Most of these emails do contain a link that will attempt to run malicious scripts, capture certain system/application data or trick the user into providing sensitive information to gain access to whatever they are phishing for.
One thing to consider is that a lot, if not most, spam is generated by some sort of automated process (code or bot). That’s not to say that wording is generated by a bot, but the bot would receive instruction from the perpetrator of what the email template should say (static context), how to propagate (spread the email out), and how the dynamically generated context is sourced and placed, e.g., a spreadsheet from compromised data containing things like names, email addresses, account IDs, etc. Most of these emails do contain a link that will attempt to run malicious scripts, capture certain system/application data or trick the user into providing sensitive information to gain access to whatever they are phishing for.
Unsure about an email received? Good. You should almost always be unsure. A good rule of thumb is to scrutinize everything by default and let the sender deal with the burden of proof that they are whom they say are. That’s not to say that they need utter the secret password (‘Swordfish’) every time there is communication, but they should strive to pass the eye test however that needs to be executed. We know that this verification can come from many places, as I briefly outlined in my first blog and as I will “detail” in the subsequent blog posts for this email security series.
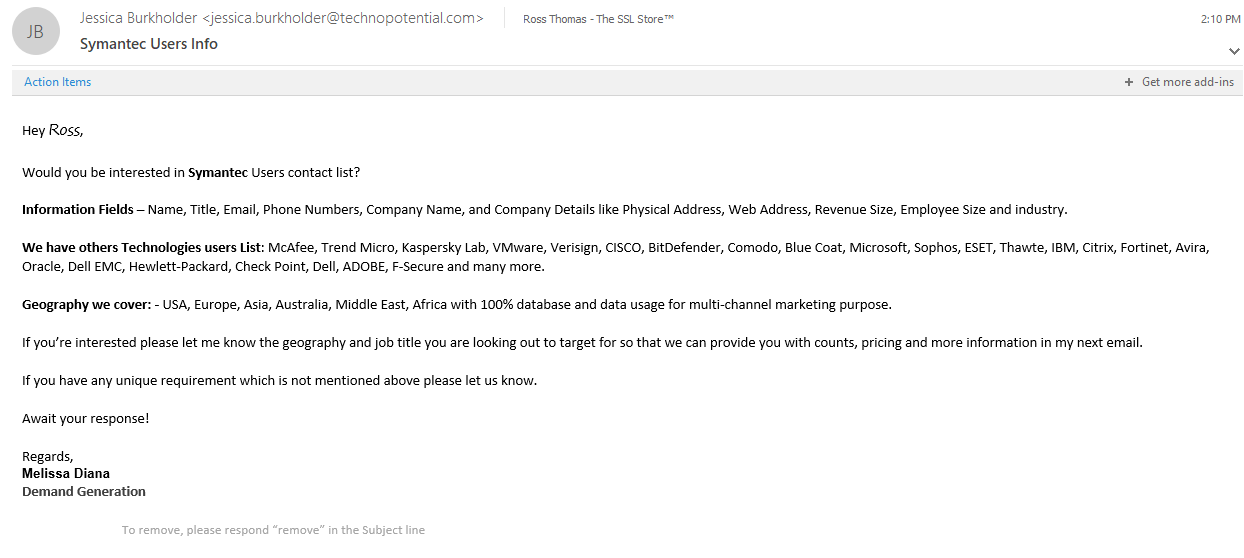
Coincidentally, while writing this post, I received this email (an image, not the email). Notice a few things about it? Let’s confirm:
- The word ‘Ross’ is in a different font (?)
- The ‘From’ header, Jessica Burkholder, Jessica.burkholder@technopotential.com, does not match the name in the signature, Melissa Diana
- The content is shady (asking if I want to buy a user contact list)
Seems like spam to me…..
Hope For the Best, Expect the Worst and Brace For Impact
We all hope that we will not have any account compromised. After the Equifax breach, it appears that nothing will ever be secure and sacred. The grind for breaching will not, nor ever, stop. Expect it. So, we mitigate damages by, as the title of this section indicates, bracing for impact. Some things to consider when bracing for impact:
- What sites do I have an account with?
- What safe guards do said sites have in place?
- Review security policy
- What information do they have of mine?
- Emails
- Banking or financial information
- Personal information
- Family information
- Do those sites need that information?
- Do those sites share certain information with other sites?
Now that all of this has been said, err, written, the word needs to be spread. Informing our fellow man (or woman) is an obligation that we are all unofficially bound to (that’s right, I’m not afraid to end a sentence with a preposition). So try to share this with the people in your life that could use a little more vigilance in their regular email activities. Tell 2 friends and have them tell 2 friends and keep that going and let’s try to deal a blow to phishing. Honestly, I think this article may pick low hanging fruit. This article may be best for those that are not technically savvy (I’m looking at you, Dad). So, aim for “my Dad” types to spread the message to (another preposition; told you I’m not afraid heh).
I don’t consider myself a pessimist but the pessimist in me expects a defeated phishing system to evolve into something new that must also be defeated. Security and breaching techniques are always evolving so stay tuned, stay sharp and happy scrutinizing!





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown