The Healthcare Industry is lagging behind on Cybersecurity
Healthcare ranked 15 out of 18 US industries in cybersecurity
The Healthcare Industry is struggling to keep up with growing cybersecurity demands, per Security Scorecard in its 2018 report.
This is especially troubling considering that Electronic protected health information (ePHI) is an extremely attractive target for hackers and cybercriminals. That’s owing to the fact that ePHI typically contains a cornucopia of personal information, such as social security numbers, financial information, health insurance and driver’s licenses, just to name a few.
Here are the key insights taken from the 2018 Security Scorecard:
- The healthcare industry ranks fifteenth in terms of cybersecurity health when compared to 17 other major U. S. industries.
- The healthcare industry is one of the lowest performing industries in terms of endpoint security.
- Social engineering attacks continue to be a common attack vector.
- The most common cybersecurity issues in the healthcare industry relate to poor patching cadence.
- Healthcare organizations, even top performers, struggled with patching cadence and network security.
To find these results, Security Scorecard looked at over 1200 healthcare organizations from July through the end of the year (six months).
Let’s Hash Out the rest of the report.
Why is Healthcare such an attractive target?
As we’ve already discussed, ePHI contains a lot of personal information. Medical records can go for up to $100 dollars on the Dark Web, depending on just how much information they contain. So, as you can imagine, a breach could be a real windfall. That’s what makes the Healthcare industry’s low ranking so troubling.
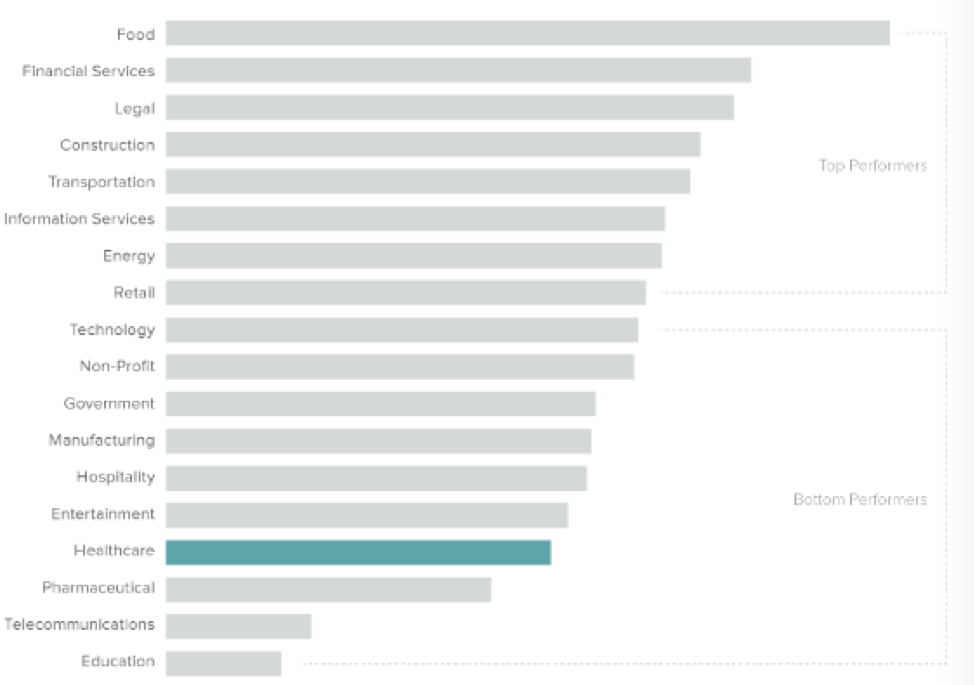
Given the value of healthcare records, it’s fair to say that the healthcare industry is doing a poor job of securing its data. It’s also fair to question whether the Anthem breach that was discovered in 2015 actually taught the rest of the industry anything about cybersecurity.
If you need a quick refresher, Anthem and some of its subsidiaries (Anthem Blue Cross, Anthem Blue Cross and Blue Shield, Blue Cross and Blue Shield of Georgia, Empire Blue Cross and Blue Shield, Amerigroup, CareMore, and UniCare) were hit by a major breach that compromised 78.8 million records.
Frankly, it’s understandable that the rest of the industry didn’t learn anything because Anthem only received a slap on the wrist. While the company did have to pay $115-million in a settlement, in the greater scheme of things that’s just a drop in the bucket. In 2017 Anthem’s operating revenues grew to $89.1 Billion, its stock price climbed all four quarters of 2017 and it has $4.2 billion in cash flow.
And apparently, the rest of the healthcare industry took note of the (lack of) consequences, since the last Security Scorecard in 2016, the entire industry has dropped six places to 15.
Endpoint Security is a Problem
Admittedly, the Healthcare industry starts a disadvantage because they have so many endpoints to secure. This has only been complicated by the Internet of Things (IoT) which provides even more endpoints. Specifically, tablets create a giant vulnerability because they may contain ePHI records, or at least a gateway to them.
Despite constant efforts to keep all endpoints secure, all it takes is one outdated device to exploit and suddenly you’re dealing with a crisis.
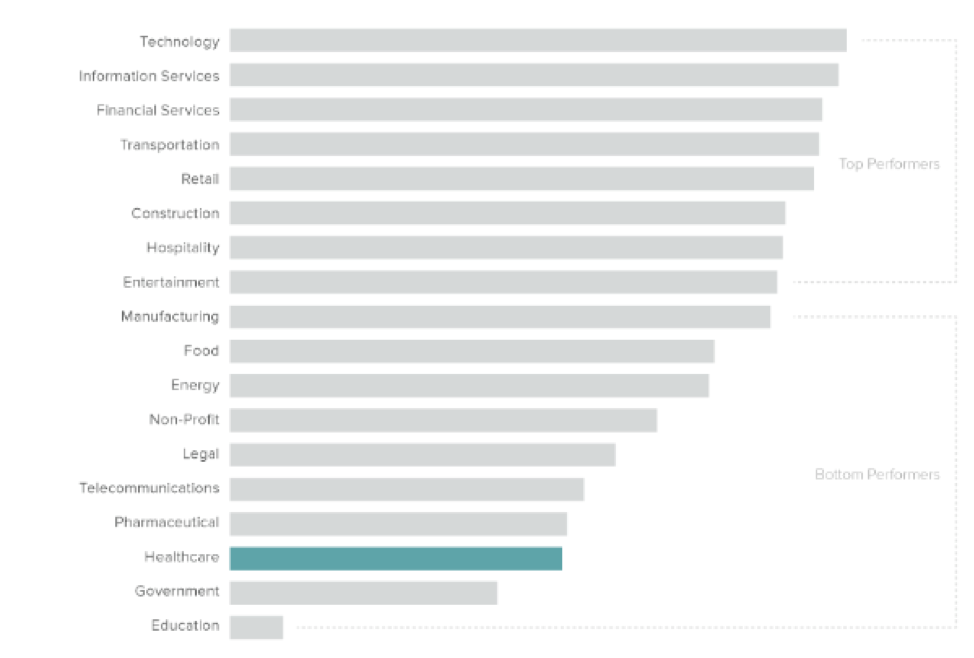
The Healthcare Industry gets a “C” on Patch Management
The Equifax breach occurred because it didn’t patch a known vulnerability. And while it’s easy to pile on with Equifax, not patching systems in a timely manner is a risk that many organizations take.
The reason for this is because it’s disruptive. Updating software means coordinating downtimes and making sure nothing else broke with the update. That’s taxing on an IT department and oftentimes the C-suite doesn’t want downtime for fear of losing business.
Regardless though, it’s something you absolutely have to do. Especially in the healthcare industry. For one thing, it’s important for HIPAA compliance, which states that risk analysis should be an ongoing process. It’s actually more in-depth than that, requiring penetration tests and a whole range of other considerations, like having an SSL certificate to protect data in transit, as well as strong encryption to protect data at rest.
Per Security Scorecard, plenty of healthcare organizations are failing at this.
Actionable Advice
Security Scorecard lists the following tips for Healthcare Organizations:
- Frequently patch systems as recommended by system and application vendors
- Ensure only required ports are open on systems
- Frequently scan to identify system vulnerabilities
- Prioritize addressing system vulnerabilities according to risk severity
- Ensure SSL certificates are current and enabled properly






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown