What Is Digital Identity & Why Does It Matter?
In a digital world where everyone (and everything) is connected, digital identity is a critical part of cyber security. Without accurate digital identity information, you could be letting hackers into your company voluntarily
The nightmare of every ecommerce business is having someone create a fake website that looks like your own. Not only is it bad in terms of losing business, but it also can damage your reputation because people will think the imposter is you. The way to combat this online identity threat is to establish a verifiable digital identity for your brand and website that proves to your customers and site visitors that you’re really you.
But your digital identity is more than just your online identity. In a more technical sense, your digital identity is what uniquely identifies you, your company and your devices as being legitimate within specific contexts. It’s also what helps you give specific users access your IT systems, data, and network or prevent them from accessing those things.
Let’s say a device accesses your organization’s financials at 8:53 on a Friday night. How do you know if that’s Bob working overtime from his home computer or a hacker who’s accessing those records via a controlled IoT device? This is where having digital identities comes into play.
In this article, we’ll answer the question “what is a digital identity?” more in depth. We’ll also talk about why it’s important to your business’s identity management processes — particularly nowadays when more employees are working remotely and doing business entirely online. And, lastly, we’ll address the ways you can use digital identity to protect your business — both in terms or protecting your reputation and preventing unauthorized access.
Let’s hash it out.
What Is Digital Identity? It’s Your Verifiable Internet “Passport”
Okay, let’s start with the basics here — a quick digital identity definition. In NIST’s Digital Identity Guidelines (SP-800-63-3), NIST describes digital identity as “the unique representation of a subject engaged in an online transaction.” In a little more technical sense, your digital identity is one or more attributes that uniquely identifies you and your devices to internal or external entities in different contexts. It also contributes to informing others about you’re a legitimate user and have permissions to access specific systems or data.
… And if that was clear as mud, here are a few quick digital identity examples that make this concept a bit more understandable:
- IP addresses,
- Login credentials (usernames and passwords),
- Digital certificates, and
- Device MAC IDs.
One of the great things about having a verified digital identity, though, is that it uniquely identifies your business on the web and lets your customers know your site is legitimate and safe. This helps you establish trust, which can benefit your brand image and reputation in the eyes of consumers in the long run.
Digital Identity is Central to Public Key Infrastructure
At its core, digital identity is a key component of public key infrastructure. PKI is an entire ecosystem of policies, processes, and technologies. It serves as the framework that secures communications over the internet rely upon and is fundamental to secure digital communications. It also serves as a critical element of effective access controls and access management for your organization.
We aren’t going to go into the technical aspects of how PKI works here because it’s way too involved to cover fully. A quick overview is that it relies on public and private key pairs to allow companies and users to store and transmit data in public channels securely. A person or organization’s digital identity is tied to those keys via a trusted third party known as a certificate authority (CA) — which we’ll speak about more shortly.
Using PKI to verify users’ digital identities helps you to implement a zero-trust architecture within your business. A zero-trust model involves the following processes:
- Verifying that someone is who they claim to be,
- Verifying that they have authorization or permissions for the files/systems they’re attempting to access,
- Granting them access once those identifiers are reviewed and their permissions are confirmed, and
- Continuing to verify that their access is legitimate throughout the duration of that connection.
Examples of Digital Identity
We already touched on this a bit but figure some additional examples and explanations might be useful. Digital identity helps you identify who (or what) you’re interacting with online and who is trying to access your systems or data. For example, it’s what helps you answer a variety of important questions such as:
- Is the device that just logged in to your network and accessed the accounting files your accountant or a hacker?
- Did that software update come from your IT department or a hacker?
- Is the website you’re on a legitimate website that’s owned by your vendor or is it a phishing site?
- Did the wire transfer request you received via email from your boss legitimate?
Digital identity establishes trust — and without trust, there can be no secure communications online. That’s because your digital identity is what identifies you as being legitimate (and, therefore, trustworthy). Components of your digital identity are the features or attributes that are unique to you. For example, common identifiers for individuals include:
- First and last names,
- Driver’s licenses and ID cards,
- Social security numbers,
- Usernames and other credentials,
- Email addresses,
- IP addresses,
- Phone numbers,
- Biometrics (such as fingerprints, voice samples, facial scans, or retinal scans), and
- Multi-factor authentication methods (something you know, something you have, or something you are).
But how does digital identity apply to businesses and organizations? After all, your company doesn’t have biometrics that users can verify. Well, there are other methods that we rely on to verify whether an organization and its website are legitimate. For example:
- Official company records (Your company name, verified address, and phone numbers),
- X.509 digital certificates (SSL/TLS certificates, email signing certificates, device or client authentication certificates, code signing certificates, document signing certificates, etc.),
- Cryptographic keys,
- Digital signatures, and
- Website trust seals.
A couple of digital identity examples for individual employees include individual users’ active directory hashes or credentials and the use of dongles or key tokens.
Digital Identity Doesn’t Exist Within a Bubble
One quick thing we want to note is that digital identities, on their own, have no value. They must be part of a larger ecosystem that supports and validates them. Your digital identity needs to have context, meaning that it must relate to specific individuals, devices or organizations and be verifiable. Without those digital identities pointing back to specific (and verifiable) individuals or devices, they wouldn’t provide any value to your security or access management initiatives. And, really, what would the point of that be?
It’s kind of like how you got the unique license plate number that’s assigned to your vehicle. You didn’t just grab a sharpie and write the numbers and letters of your choosing on some cardboard. You had to go to a trusted authority (e.g., the government) and provide multiple forms of information that proved you’re you. Only then did they give you the license plate that uniquely identifies your vehicle. (Unless you purchase a personalized plate with a specific identifier — that process is a little different, but you still have to go through that trusted authority regardless.)
Now, let’s apply this same concept to how access is given to individuals within businesses. As an employee at your company, there are certain provisions you likely had to meet before you could receive credentials to access the company’s IT systems or files. For example, before giving you any type of access, your company likely checked to make sure:
- You’re a legitimate (and current) employee of the organization,
- Your job requires you to have access to carry out specific functions, and
- Your manager authorized you to have specific privileges.
If you didn’t meet any of these requirements, then you wouldn’t get those privileges. And without those permissions, you wouldn’t be able to gain access to those resources even when you’ve completed any authentication processes. Authorization and authentication are two related but separate concepts. In a nutshell, the former (authorization) is about having the permissions or privileges to access specific data, systems, tools or other resources. The latter (authentication) is about proving your identity so that you can use or access those items that you have permissions for.
If you’re not sure how all of these things relate to validating or verifying your business’s digital identity, no worries, we’re getting to that. This is where those certificate authorities (CAs) we mentioned earlier come into play.
Certificate Authorities Use Your Digital Identity to Validate Your Organization & Users
A certificate authority is a reputable third party-organization that all of the major browsers (Chrome, Safari, Mozilla, etc.) trust because they’re required to meet certain standards and requirements (as outlined by the CA/Browser Forum, or the CA/B Forum for short). CAs use official records to verify your organization’s real-world information (company name, address, contact information, etc.). They’re also responsible for providing or helping to generate the other items on the list (so long as the requesting organizations meet certain requirements).
For example, to help browsers trust individual websites, CAs issue a type of digital certificate that’s known as a website security certificate (SSL/TLS certificate). (Note: They’re technically TLS certificates but we still call them SSL certificates because that’s the common lingo throughout the industry.)
Related: Secure Your Domain & Sub-Domains with a RapidSSL Wildcard Certificate.
This certificate is a digital file that ties an organization’s real-world identity to its cryptographic key pair. This way, these organizations — and only these organizations — can use them to prove their identities to assure users that:
- They’re connected to the right website and server (authentication), and
- Their data is secure and won’t be stolen or messed with by cybercriminals (cryptographic measures ensure data integrity and security).
This is what makes the security padlock and “HTTPS” appear in your browser whenever you visit a secure website:
It’s also what helps your website avoid this nasty little warning:
Why Digital Identity Matters
The reason why digital identity is necessary online is that the internet itself is an insecure means of communication. Data transmits across the internet, from server to server, in an insecure, unencrypted format. This means that anyone with the know-how can intercept, read, or alter the data as they see fit via man-in-the-middle (MitM) attacks.
From a business perspective, your digital identity is critical to access management and implementing a zero-trust infrastructure. It serves as a way for IT administrators to tie specific access privileges to individual users’ accounts and verify that only those users can access those systems or data.
For example, as a marketing professional, I have certain privileges. There are systems and data that I can access at The SSL Store that other employees cannot. Likewise, our IT administrator has access to other systems and data that I don’t have — and that’s the way it should be. I should have access only to the systems and data that I specifically need to do my job because anything more is a potential security liability if my credentials were to become compromised. (Implementing strong access controls is essential to mitigate cybersecurity risks.)
Digital Identity Enables You to Prove to Third Parties That You’re You
At its core, digital identity is all about having a trusted and reliable third party verify that you are who you claim to be. Without it, anyone could pretend to be your company and trick unsuspecting users into believing they’re you. And when you communicate with people around the world — people you’ve likely never seen or met in person — being able to verify someone’s identity is crucial.
For example, I could claim to be Angelina Jolie, but just me saying that I’m her doesn’t make it true. It doesn’t matter that I’m too short to be her, that she’s older than me, and that I don’t make millions of dollars a year as a famous actress. I could still set up an imposter website, email address, a few social media profiles, and do other things to try to convince you that I’m her. But, again, that doesn’t actually make me the real Angelina Jolie.
Without verifying someone’s legitimate digital identity to recognize a real site from a fake one, it would be hard to differentiate the real Angelina Jolie’s website from my imposter sites.
All of this is to say that just because someone says they’re a legitimate company and have a legit-looking website doesn’t make it true. This is why your customers — and the web clients they’re using to connect with you — need a way to verify your legitimacy. Having a verified digital identity enables you to do that.
Digital Identity Is the Difference Between Being Secure vs Safe Online
Here at Hashed Out, we always talk about the importance of using business validated SSL/TLS certificates on your website. We do this for a couple of key reasons. These certificates:
- Authenticate websites by verifying their organizational identities. These certificates require validation by reputable third-party CAs that verify your organization or company is legitimate before issuing a certificate.
- Establish secure, encrypted channels to transmit data and ensure data integrity. of the idea here is that you use encryption to secure the connections between your servers and users’ browsers to exchange data. In addition to not seeing, reading, or stealing your sensitive information, no one can tamper with it.
But there’s a caveat that’s worth mentioning: When a website uses encryption, it makes it secure, but what it doesn’t do is make it safe. For a site to be safe, you need to know who’s on the other end of that secure (encrypted) connection.
Phishing Websites Frequently Use Encryption (HTTPS)
Not all SSL/TLS certificates are made equally. Virtually anyone can get a domain validated (DV) SSL/TLS certificate for their website because, well, it requires the least amount of validation. (It’s the low-hanging fruit of website encryption.) So, what happens when the bad guys install SSL/TLS certificates on their website? In a word: trouble.
Data from the Anti-Phishing Work Group’s (APWG’s) Phishing Activity Trends Report for Q4 2020 shows that nearly nine-in-10 (89%) of phishing websites in that quarter used DV certificates to trick users into thinking their sites were safe and legitimate. Cybercriminals frequently get free DV SSL/TLS certificates because they don’t cost anything and they’re easy to get — especially from free certificate providers. (No, we aren’t naming names.)
John LaCour, CTO of PhishLabs, provided analysis data to the APWG relating to the number of phishing sites using TLS certificates in Q4 2020. The APWG’s Q4 2020 report quotes LaCour as saying the following:
“[…] the number of phishing sites using SSL/TLS increased 3 percent quarter-over-quarter and 10 percent year-over-year to 84 percent. It is virtually the default setting for web sites to use TLS certificates now […]
DV certificates are commonly provided for free, and provide the weakest form of certificate validation, requiring no authentication of the user – only the domain name being used[.]”
Now, we aren’t telling you this to slung mud at free digital certificate providers. But it’s important to recognize how free certificates play into the increase in the number of phishing and malicious websites that have been created in recent years. Not saying it’s necessarily causal, but there’s an obvious correlative effect. (If it walks like a duck and quacks like a duck, it’s probably not a goldfish.)
But what makes free DV certificates so easy for cybercriminals to get their hands on? Domain validation is an automated process that verifies only the absolute minimum about a website before spitting out a certificate within a few minutes of the initial request. But this does nothing to establish trust or ensure a company is legitimate. So, this means that security padlocks will appear in a fake website’s browser if they get their hands on one of those free certificates.
This is why asserting your organization’s digital identity on your site is so important — and you can only do that by using two other types of SSL/TLS certificates: organization validation (OV) and extended validation (EV) digital certificates.
Digital Identity Helps Users Identify the Good Guys (And Avoid the Bad Ones)
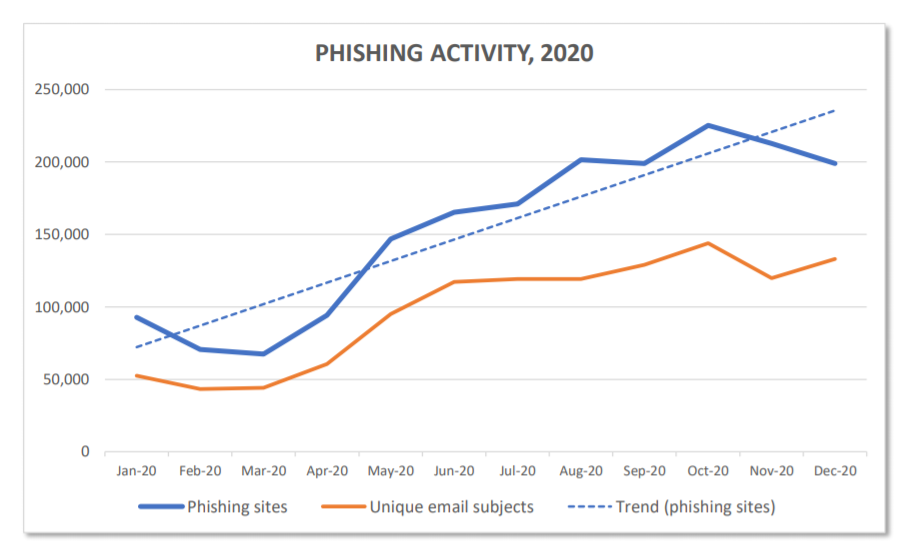
You see, anyone can create a website regardless of whether or not they’re affiliated with a company or organization. Phishing and other types of fraudulent websites are incredibly common — data from the international Anti-Phishing Working Group (APWG) shows that phishing attacks doubled in 2020.
Their Q4 2020 Phishing Attack Trends Report shows that 637,302 unique phishing websites were detected between October-December 2020 alone. (Keep in mind that this is only the number of phishing sites reported by APWG members into the APWG eCrime eXchange — it doesn’t include unknown or otherwise unreported sites.)
Pretending to be a legitimate company online isn’t hard — all bad guys need to do is purchase a domain that resembles yours and slap some graphics and copy on the site to cause irreparable damage to your brand. To make matters worse, they can take their cons to the next level by installing SSL/TLS certificates that require no organizational validation.
Free DV Certificates Contribute to Rise in Credit Card Fraud
F5 Labs’ 2020 Phishing and Fraud Report shows that cybercriminals’ use of DV certificates likely contributed to the sharp increase in credit card fraud throughout the year.
“[In 2020] we found that phishing incidents rose by a staggering 220% compared to the yearly average during the height of global pandemic fears. Fraudsters were quick to seize upon the confusion and we saw large spikes in phishing activities that closely coincide with various lockdown rules and the increase in homeworking. Using certificate transparency logs, we found that at its peak, there were almost 15,000 active certificates using “covid” or “coronavirus” in their names. On the topic of encryption, the use of HTTPS also rose sharply across all phishing sites with an impressive 72% making use of digital certificates and TLS encryption. The dramatic increase in phishing activity at the beginning of lockdown could well be a factor in the sharp rise of stolen payment cards discovered in May and June of this year. The number of cards of seven major global banks found on darknet markets was almost double a similar peak period in 2019.”
Digital Identity Helps You Protect Your Company Network
As you know, digital identities apply to far more than just your website. It also applies to your organization’s internal IT environments as well. Monitoring the digital identities of your connected devices and users can help you identify any hinky activities that takes place on your network. This helps you mitigate any potential damages or data theft that may result from network-related compromises or cyber attacks.
Let’s say, for example, that you notice your office’s smart thermostat trying to access HR databases and employee files. This should automatically set off alarms that the device is likely compromised because:
- That IoT device isn’t authorized to access those systems, and
- It doesn’t have a reason to access those systems or files.
All of these different functions underscore the importance of digital identity on the internet. So, now that you know what digital identity is and why it’s so vital, talk about how it applies to you. We’ll cover how you can prove your organization’s legitimate digital identity before talking about how you can put your own digital identity to use to protect your business.
5 Ways You Can Use Digital Identity to Protect Your Business
If you’re like most modern companies, the internet is an essential tool for your business. You rely on it for everything from marketing and selling your products or services to facilitating your company’s general operations and communications. But how can customers differentiate you from cybercriminal imposters? Here are some of the things you can do to establish your organization’s digital identity.
1. Install an SSL/TLS Certificate on Your Website
Okay, we’ve already talked about the advantages of using an SSL/TLS certificate on your website. But to quickly recap: this type of digital certificate, when purchased with basic business-level validation (OV) as a minimum:
- Authenticates your site as being legitimate,
- Facilitates secure, encrypted connections with users’ browsers, and
- Ensures your data’s integrity through the use of digital signatures.
2. Use Email Signing Certificates to Let Users Know Your Messages Are Legitimate
Email is a huge opportunity for bad guys to scam individuals and businesses alike. Email phishing, business email compromise (BEC) scams and email account compromise (EAC) issues result in billions of dollars in losses each year. The FBI’s Internet Crime Complaint Center (IC3) reports that in 2019 alone, BEC/EAC complaints resulted in adjusted losses topping $1.7 billion.
So, one way your customers can verify that the emails they receive from you are legitimate is by signing them using an email signing certificate. You see, when you send a digitally signed email, you’ll see an interactive ribbon appear in the email that you can click on (as shown below):
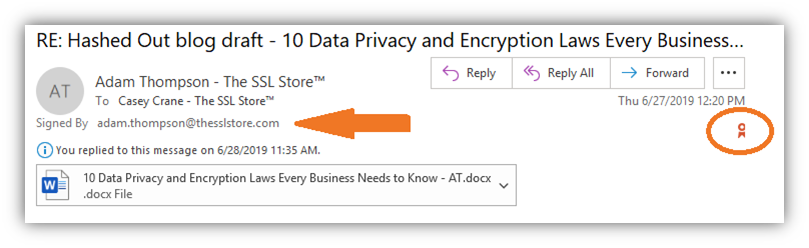
When you click on the ribbon, a popup will display that provides information about the email signer, including their verified name, email address, and a link to more information about the certificate that they used to sign the email. (You can click on the Details button in the popup, as shown below, to view that certificate information.)
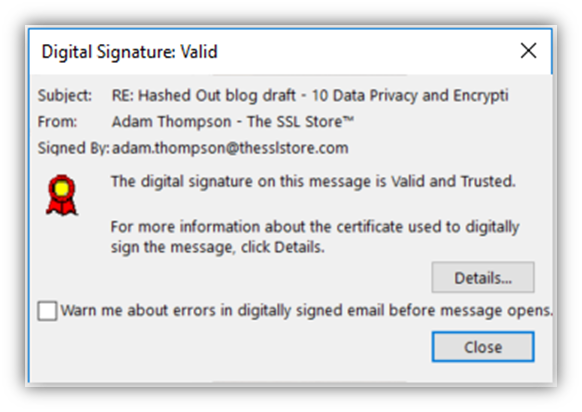
In general, the digital certificate provides you with a wealth of information about the signature, including what hash was used and timestamp information for the date/time the email was signed.
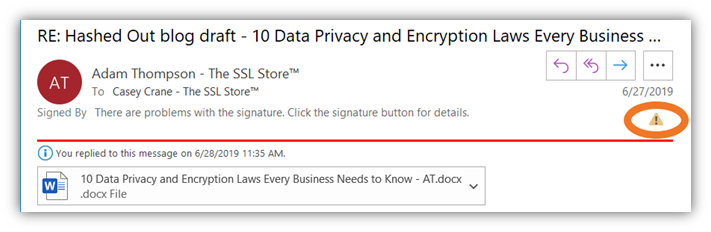
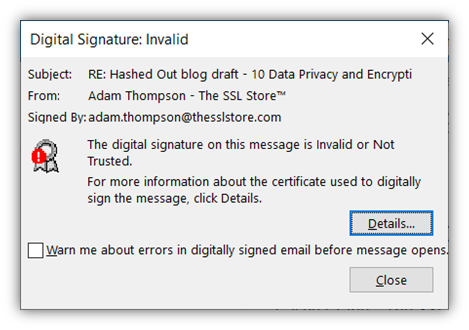
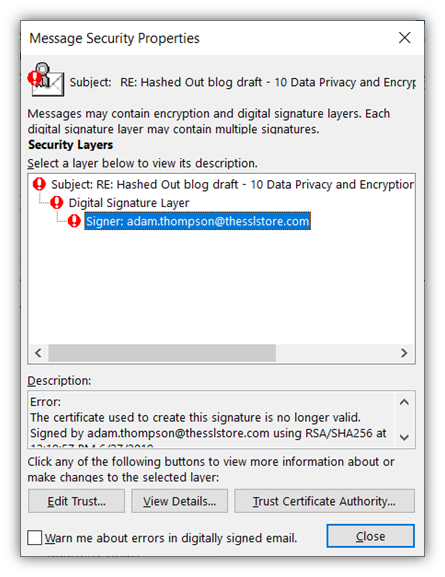
If the certificate isn’t valid or has expired, then the certificate message displays and information would look something like these images instead:
Before we move on… I’d be remiss not to mention that these certificates actually have a few other uses as well. You can use email signing certificates to:
- Encrypt emails (when exchanging emails with other email signing certificate users), and
- Authenticate your device to a server (serving as a form of passwordless authentication to up your company’s password security game) using public key infrastructure (PKI-based authentication).
Both of these benefits are just more delicious icing on the cake as far as email security goes. You don’t have to use them for those purposes, but it’s great to have the option. We’ll speak more about passwordless authentication in a few moments.
3. Sign Your Software with Code Signing Certificates to Protect the Supply Chain
You might be surprised to learn that digital certificates are good for more than just securing your email and website. There are digital certificates (code signing certificates) that you can use to sign software code. This helps you to assure users that your software is legitimate and that no one has messed with it since you released it.
Basically, it’s the difference between displaying this verified publisher information (image 1) versus this unverified publisher information (image 2):
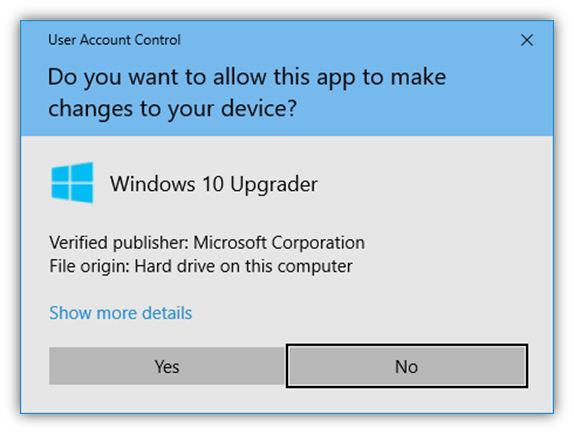
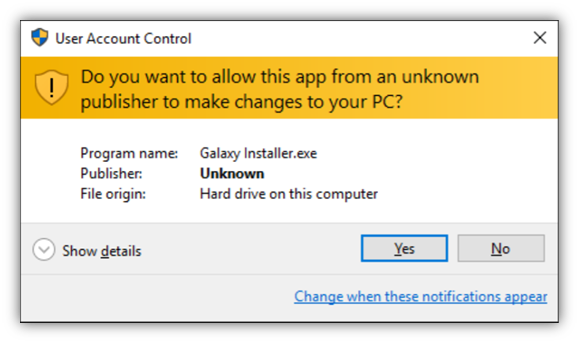
So, if you’re an IT software company and you’re rolling out a critical patch, your customers can verify that the update is legitimate and was issued by your business (and not an imposter).
One quick but important note for mobile app developers: The code signing certificates that you use to sign mobile apps for online stores like Google Play and Apple’s App Store are different from the ones devs use to sign desktop apps. To sign mobile apps for those stores, you actually have to go through Google and Apple themselves to get their code signing certificates.
Check out these links to get more information about becoming a member of the Apple Developer Program and to learn how to sign mobile apps for Google Play.
4. Use PKI Client Authentication to Simplify Logins & Avoid Credential Phishing Scams
Credential compromise is a big problem for businesses globally. Data from Verizon’s 2020 Data Breach Investigations Report (DBIR) shows that four-in-five hacking-related breaches in 2019 involved stolen or lost credentials.
One way to avoid credential compromise is to limit the sites and web apps that require users to input their credentials. You can do this by using PKI certificate-based authentication (i.e., client authentication). This passwordless authentication method enables your employees to log in to access systems, files, or data using digital certificates that are tied to their unique digital identities. It does away with the need for having to remember or type in cumbersome usernames and passwords. (You just log in to your device and that’s basically it.)
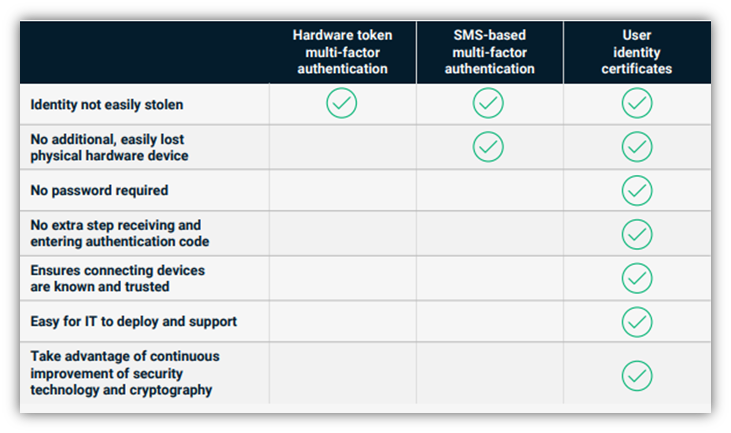
According to Sectigo, when you combine PKI-based authentication with a trusted platform module, it’s more secure than passwords and SMS-based multi-factor authentication (MFA) methods.
5. Train Your Employees to Verify Digital Identity Before Trusting Anything
Frankly, in most blog posts, we inevitably wind up talking about the importance of cyber awareness training for employees. That’s because cyber awareness training is critical for beefing up the defense of your “human firewall” (i.e., your employees’ cyber defense capabilities). You do this by making them aware of different types of threats and by teaching them how to identify those threats and react safely to them (among other things).
This training should cover the importance of verifying someone’s or something’s digital identity before trusting anything they say. For example, this could involve:
- Double-checking the sender’s name and email address to make sure they match,
- Calling their boss directly on the phone to verify whether the wire transfer request they received really came from them, and
- Checking the email for other inconsistencies and glaring issues (such as embedded links that lead to unknown websites, poor grammar usage, and common signs of social engineering).
Basically, it’s about training your employees to have a zero-trust security mindset where they never trust anything without first verifying its legitimacy. When in doubt, check it out.
IT Admins: How to Protect Your Organization’s and Users’ Digital Identities
Cybercriminals are always looking for new ways to infiltrate the networks and servers of governments, businesses and other organizations to carry out nefarious agendas. So, what can you do to keep your organization and employees’ digital identities secure?
Keep Sensitive Information Encrypted and Off Public Servers
I can’t say this enough: Never store any secret, confidential, or otherwise sensitive information on public-facing servers. It never fails to amaze me when I see headlines about companies being surprised when they experience data breaches and leaks when they store their information in unsecured servers and cloud environments.
These insecurities could be due to a lack of cybersecurity protections or accidental misconfigurations. Either way, unfortunately, these cybersecurity issues are happening more frequently (or more companies are reporting breaches more often). And this is bad news for businesses and customers alike.
Follow Digital Certificate and Key Management Best Practices
The effectiveness of public key infrastructure depends upon how well organizations protect their cryptographic keys and digital certificates. If a certificate or key becomes compromised, it’s game over in terms of keeping your data secure. This is why all organizations must use strong key and certificate management principles.
Check out a couple of our other related blogs to learn about enterprise encryption key management best practices and common PKI certificate management mistakes you should avoid.
Implement a Zero-Trust IT Infrastructure
We talked about this briefly earlier but it’s worth calling out again here. One of the best ways to help protect your organization is to implement a cybersecurity approach that says, “don’t trust anyone or anything automatically” and requires continuous authentication. It doesn’t matter whether the user requesting access is inside or outside of your network — they’ll be treated with the same amount of caution.
While this may sound like it’s unnecessarily complicated, it’s not. A zero-trust approach can mitigate the effects of cybercriminals who make it past your initial login portal by using an employee’s compromised credentials.
How to Protect Your Organization’s Online Identity to Avoid Business Identity Theft
Although your organization’s real-world identity isn’t your digital identity in the IT sense, it’s certainly related and is something you should take steps to protect.
It’s no secret that cybercriminals love to take advantage of opportunities to exploit the good names and reputations of established businesses. We see that all the time with bad guys pretending to be well-known businesses (PayPal, Apple, Netflix, etc.) when carrying out phishing scams. By pretending to be you or your organization, they take advantage of all the trust and value that you’ve established with customers over the years to commit cybercrimes and fraud in your name.
Thankfully, you can do a few things to protect your online identity to fight business identity theft (which also mitigates the resulting damages when cybercriminals’ attacks are successful).
Keep an Eye on Your Organization’s Official Records via Third-Party Sources
Every registered and established business has government records associated with it. Something that a lot of businesses neglect to do is periodically check those records to ensure they’re accurate. If a cybercriminal decides to impersonate your business, they may try to use hacking or social engineering tactics to change your official company records to meet their needs.
With this in mind, here are a few key items you should keep an eye on:
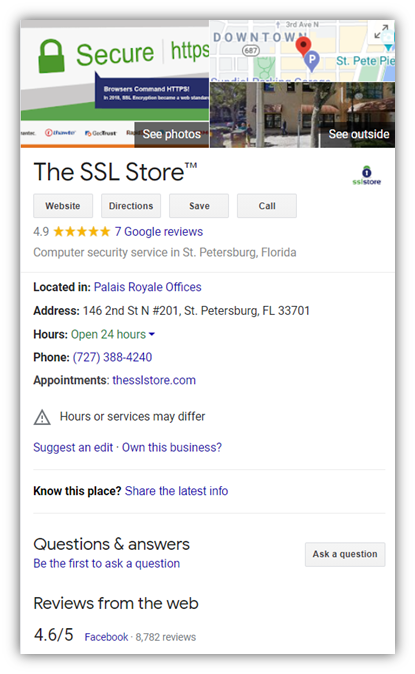
Your Google My Business & Google Maps Company Information
Check your website address, physical address, phone number and other important information on Google My Business and Google Maps to make sure it’s accurate. A couple of years ago, the Bank of India (BoI) was surprised to discover that cybercriminals had managed to post false company contact information by exploiting a loophole in Google Maps. This led to customers’ personally identifiable information (PII) becoming compromised.
Your Dun & Bradstreet Business Profile
Dun & Bradstreet is one of the leading resources for verifying company information. Certificate authorities, among with other entities, rely on their comprehensive business data to ensure businesses that apply for digital certificates are legitimate. You can also use them to keep an eye on your official company information to ensure:
- There are no fraudulent filings listed for your company,
- That all company records, business filings, contact information, and addresses are all correct, and
- No information about company officers or other key leaders has changed without your knowledge.
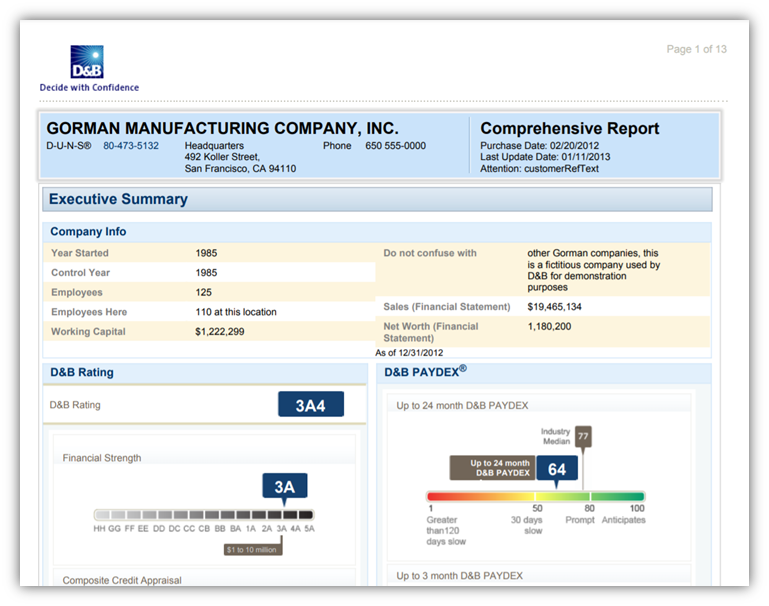
Andrew La Marca, Director of Fraud & Compliance Operations at Dun & Bradstreet, said during a March 2021 Dun & Bradstreet LinkedIn webinar that businesses can prevent this type of fraudulent activity by monitoring their business registrations and credit reports:
“You’ve gotta monitor your business credit reports, right? You want to make sure that what’s being reflected on your business credit reports is 100% accurate. And it’s super crucial in times like these to make sure that everything you’re doing is being spot-checked, and you’re also being proactive but then you’re monitoring it on a continuous basis. It doesn’t stop just because you checked it once; you want to come back two months down the road, or a month down the road, and just check on things to make sure everything’s looking the way that it should.”
Your State’s Business Registration Records
In the U.S., every state keeps records on companies, corporations, limited partnerships, and trademarks. This makes it a great resource for customers who want additional information about companies. It includes all sorts of data relating to organizations, including:
- Identifying information (such as FEI/EIN numbers),
- Registration information and statuses,
- Company registrants and officers,
- Copies of annual reports, and
- Report years and filing dates.
For example, here in Florida, we have the state’s Division of Corporations website. This is where people can search for company information for Florida businesses.
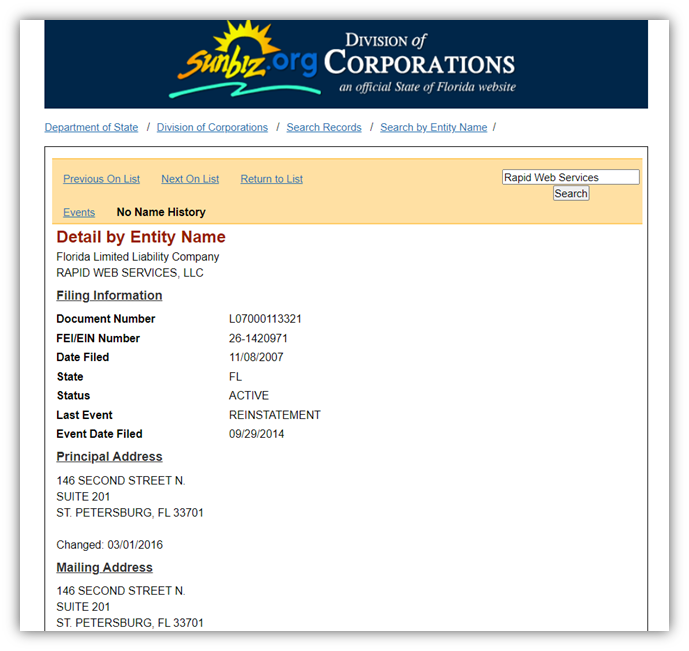
To learn more about what information is available for businesses within your state, check with your state’s Secretary of State’s office.
Buy Domain Names That Are Similar to Yours (So Cybercriminals Can’t)
One of the best ways to stop cybercriminals from impersonating your website or company is to buy look-alike domains — or domains that are similar to yours in appearance or context.
- Cybersquatting domains — Cybersquatting occurs when someone buys one or more domains for companies or brands that don’t yet have websites set up. Why would they do that? In some cases, it’s to try to sell the domains to the real organizations at inflated rates in the future. In other cases, though, it’s actually an honest mistake or ignorance on the part of the domain registrant who may not realize there’s a business or brand whose name is similar to the domain they’ve purchased.
- Typosquatting domains — Typosquatting domains are a subcategory of cybersquatting that capitalize on humans’ typing mistakes (hence “typo”-squatting). This occurs when someone intentionally buys one or more domains that visually look similar but are slightly off. For example, instead of “TheSSLStore.com,” they’d register “TheSSLSlore.com” or “TheSSLSt0re.com.” The goal is to use these domains to impersonate legitimate organizations and businesses for fraud or to carry out an agenda.
- Homograph attacks — In this situation, cybercriminals use Unicode characters to create visually-similar (or identical) domains that look like your legitimate ASCII-based ones. Asaf Nadler at Akamai shares the following example in his blog post on homograph attacks: “the IDN ‘xn--akmai-yqa.com’ which appears in Unicode as ‘akámai.com’ visually resembles the legitimate domain name ‘akamai.com.’”
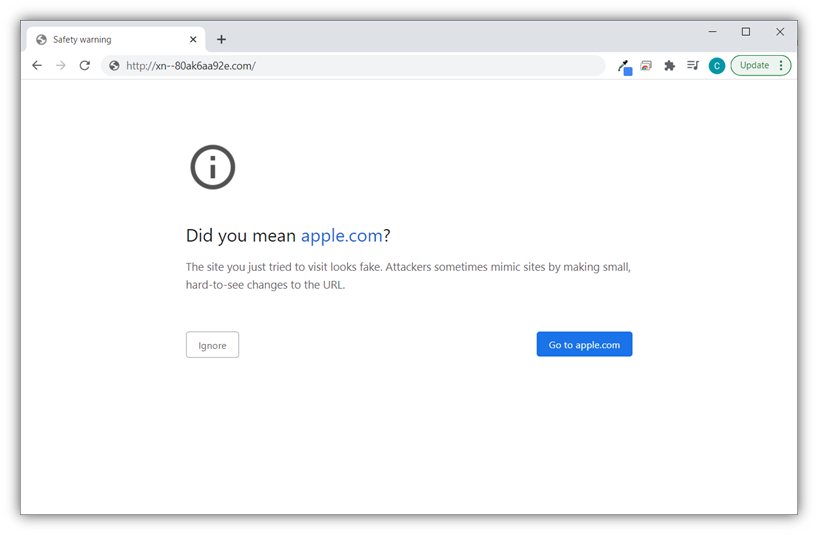
You can buy the misspelled versions of your domains to get ahead of these types of situations. You can then use redirect links to redirect users who accidentally mistype your website address to the correct site. Sure, this approach requires some financial investments up front, but it sure beats having your customers finding an imposter’s site rather than your real one.
Final Thoughts on Digital Identity
Putting the effort into establishing and protecting your digital identity is a critical function of every IT team — or, at least, it should be. It establishes trust and enables you to stand out from the bad guys who are trying to trick your customers into thinking they’re you. It also helps you to identify and verify whether someone has legitimate permissions and authorization to access your network, IT systems, servers, files, or other data.
As the world becomes increasingly reliant on the internet and digital communications, and as businesses increasingly move toward implementing zero-trust IT architectures, it further underscores the importance of using and securing the digital identities of your organization and users.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown