Put Your Risk on Mute: Using PKI to Simplify Remote Workforce Security
With 74% of surveyed CFOs saying they intend to move at least 5% of their on-site workforces to remote positions after the current pandemic, properly managed PKI is more important than ever
Disney World may have closed its doors, but there’s a new fantasy land that opened up and its making many hackers’ dreams come true.
Thousands of fresh-faced “wait, I don’t have a desk or chair at home; how long are we going to be out of the office; hey, you’re on mute; sorry, my dog is barking” employees suddenly need remote access to applications and networks from laptops, smartphones, and employee-owned devices.
That means a more opportunities for malicious actors to target. So, how can PKI ruin their good time and help secure this new remote workforce?
Let’s hash it out.
PKI Is the ‘Meat and Potatoes’ of Your Remote Workforce Security
Public key infrastructure (PKI) doesn’t have fancy LEDs or logos on it. You can’t walk into the data center and see how it was clearly worth the money the way it shines in your 48U server rack. But PKI is like that: it’s quiet, unassuming… and 100% critical to your success.
The enterprise security world is no longer just a firewalled network stack. “Zero Trust” is what the cool kids are doing, and according to the National Institute of Standards and Technology (NIST), PKI is a key component of a properly managed security environment.
How Can We Effectively Secure a Remote Workforce?
Globally, many employees have been deemed nonessential and organizations have shuttered brick-and-mortar office spaces. Consequentially, both employees and organizations see benefits in having a larger remote workforce on a permanent basis. There’s a laundry list of studies done on remote work cost savings (probably a few funded by the global sweatpants manufacturer association) covering everything from office space to sick leave.
Over the past few months, many IT departments have been tasked (with less than a week’s time in many cases) with scaling networks and providing remote access to the applications and services that employees needed to do their job effectively. But are they secure?
There are some key weaknesses we can address right now:
- Passwords can be secure, but our minds less so…
- Multi-factor authentication (MFA) is great — until it’s not.
- Strengthen security with certificate-based authentication tools:
- How certificate-based authentication works
- What type of certificates do you need?
- Automation of the certificate lifecycle is crucial
Let’s go over each step in more detail…
1. Passwords Can Be Secure, But Our Minds Are Less So…
Passwords are the most well-known layer of internet security, but they’re failing in several ways, including:
- Stolen passwords. Aggressors have gotten much better at deceiving employees and pirating passwords. According to the most recent FBI internet crime report, business email compromise (BEC) scams caused the most damage in 2019 with adjusted losses of just over $1.7 billion. Business email compromise has had significant traction and targets both businesses and individuals. According to the same FBI report, “the scam is carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques.”
- Shared passwords. So, passwords are a secret shared between the employee and the server, right? Unfortunately, passwords often aren’t very secret. 69% of employees admitted to sharing passwords with colleagues to access accounts as indicated by the 2019 State of Password and Authentication Security Behaviors Report, a study that was led by Ponemon Institute.
- Forgotten passwords. Besides the possibility of attacks, raise your hand if you’ve ever forgotten a work password after a long vacation. Ok, EVERYONE can put their hands down now.
PKI authentication succeeds where password authentication fails because:
- The private key isn’t sent to the server, meaning that it can’t be intercepted or stolen in-transit.
- Client certificates and keys (unlike passwords) can’t be stolen via common phishing attacks.
- Brute forcing a 2048-bit key is pretty much impossible — cracking a private key is like counting grains of sand at the beach, you can start but good luck finishing.
- The tedious process of entering usernames or changing passwords becomes extinct.
Pratik Savla, Senior Security Engineer at Venafi, did a great job summarizing the benefits of certificate-based authentication:
“Certificate-based authentication is based on the X.509 public key infrastructure (PKI) standard. It offers stronger security compared to other forms of authentication by mutually authenticating both the client, (via a trusted party — CA — Certificate Authority) and the server during the SSL/TLS handshake. In other words, both sides involved in the communication have to identify themselves, whether that is for user-to-user, user-to-machine, or machine-to-machine communication.
As this design involves exchange of digital certificates instead of a username and password, it helps in preventing phishing, key-logging, brute force as well as MITM (Man-in-the-middle) attacks amongst other risks commonly associated with a password-based design.”
The estimated cost of both time and loss for organizations annually just on password issues is $5.2 million, according to the aforementioned Ponemon Institute report. Using PKI-based identity certificates changes the entire organization’s burden of remembering, updating, and managing passwords.
2. Multi-Factor Authentication is Great — Until It’s Not
Multifactor authentication: pretty spectacular and very, very secure, right? Not if you ask Twitter CEO Jack Dorsey. Malicious actors gained access to his personalTwitter account. Hackers used a SIM swap scam to spoof his account and receive the second layer of the MFA.
If you’ve ever signed into Gmail or attempted to access a secure banking site from an unrecognized browser that requires you to input a pin number sent through SMS, you’ve seen and used multi factor authentication. In many cases, this process reduces the chance of stolen identity, but in the case of remote working, it also adds an additional application, making things more complex for IT admins.
But you might be wondering, how much better are user ID certificates than phone-or token-based multi-factor authentication? Let’s take a look at this comparison chart from Sectigo:
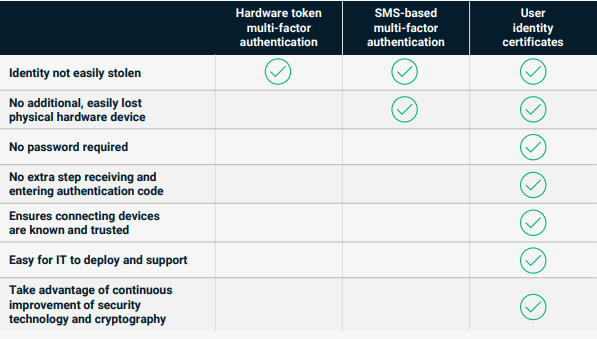
As this chart highlights, PKI is significantly better than passwords. Here’s how Tim Callan, Senior Fellow at Sectigo, explains it:
“A certificate in conjunction with a TPM is stronger than a shared secret with phone-based MFA. So changing from password plus phone-based MFA to client certificates (especially when TPMs are present, as they go a long way in securing the key from theft), is a definite step up… Remember, the device itself (laptop, phone, tablet) can and should require a password to unlock. By mandating that requirement for devices attaching with certificates, the IT department has enforced a thing-you-have (certificate) and thing-you-know (device password) scheme.”
Besides PKI-based certificates offering the strongest form of identity authentication, they also make connecting simple and easy for the remote workforce. An employee’s private key is stored directly in their device (ideally via a trusted platform module, or TPM), whether that’s a laptop, smartphone, or tablet. The employee can open the needed applications and just work. What a novel concept right? They’re authenticated with no extra steps!
3. Strengthen Security with Certificate-Based Authentication
Using manual processes to manage the certificates for even a few employees can be labor-intensive, technically demanding, and error prone. PKI is often underutilized and feared because of these exact issues.
How Certificate-Based Authentication Works
In the words of the immortal Michael Scott: “Why don’t you explain it to me like I’m 5?” Can do. Here’s how certificate-based authentication works in the work-at-home scenario we’re currently seeing:
During the SSL/TLS handshake between the device at home (or the beach, you rascal!) and the server at corporate, the device and server exchange pleasantries. This is just like a normal TLS handshake but with a couple extra steps:
- The client (device at home) sends its certificate and public key to the server.
- The server verifies the client certificate before allowing the connection.
The server will reject connection requests from any device that doesn’t provide a valid, verified, and authorized client certificate.
What Type of Certificates Do You Need?
The major certificate authorities all offer certificates that are suitable for use within a remote work PKI environment. They’re referred to by a few names, such as:
- Client certificates,
- Device certificates,
- User certificates, and
- Personal authentication certificates.
Sectigo/Comodo Personal Authentication Certificates are a perfect example of the type of certificates that can be used for certificate-based authentication.
Automation of the Certificate Lifecycle Is Crucial
Managing PKI at scale is usually not viewed as an easy process, but, fortunately, there are tools that enable automation across the certificate lifecycle. Properly managed automation permits your IT security group to issue, revoke, and replace certificates with ease. This can be done at scale both rapidly and dependably.
Equifax was the target of one of the largest data breaches in history. This breach almost assuredly could have been avoided with the use of properly managed PKI automation. After a thorough investigation, the Government Accountability Office determined:
“Equifax did not see the data exfiltration because the device used to monitor [the vulnerable server’s] network traffic had been inactive for 19 months due to an expired security certificate.”
It apparently took them a couple more months to fix the issue, after which they “immediately noticed suspicious web traffic.” Because of user error, the breach cost Equifax $1.14 billion in 2019 alone.
The total cost of implementing PKI automation not only saves you the headaches and costs associated with downtime and noncompliance, but it also gives your IT team back the valuable time that they need to work on higher-level tasks that will benefit your company in other ways. When you understand and can quantify revenues, costs, compliance and risk, PKI automation becomes a valuable tool without equal.
Final Thoughts on Remote Workforce Security
The global situation is changing rapidly, and it’s difficult to predict what will come in the coming weeks or months. On March 16, 2020 the U.S. government issued a set of guidelines for 15 days to slow the spread of a pandemic virus. Almost 90 days later, I’m completing this article and have yet to go back to my office.
There are many companies who assume they may never go back to a regular office setting. There are reports daily that malicious activity targeting remote workforces is increasing exponentially. Unfortunately, economies are still teetering on edge, the food supply chain is being drastically affected, and there is growing sense of desperation.
But in the midst of all this, cybercriminals aren’t taking a vacation. In fact, they’re using Coronavirus-themed scams to target potential victims. A few weeks into the pandemic, major dark web hacking groups were promising not to hit healthcare targets. But as of the writing of this article, the U.S. Department of Health and Human Services Office for Civil Rights Breach Portal lists 2,961,860 individuals whose personal information has been affected by hacking or unauthorized access since the first reported case of COVID-19 in the U.S. (The first reported case in the U.S. was dated Jan. 20, 2020.)
While the topic of this article is placing the pandemic as top of mind, these are tools that can protect organizations no matter what the outside environment looks like. The sooner that organizations can deploy properly managed PKI authentication to users and devices in the network, the sooner their remote workforces can have peace of mind. Even if that peace of mind is wearing sweatpants and hasn’t had its nails done or a haircut in three months.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown