What Is PKI? A Crash Course on Public Key Infrastructure (PKI)
Ever wondered what public key infrastructure (PKI) is and how it works? It’s only one of the most critical systems used to ensure authentication, data integrity, and privacy…
The world of cryptography is full of brilliant ideas, and one of those ideas is public key infrastructure (PKI). But what is PKI and what does it entail for organizations and data privacy? In a nutshell, it’s a system of processes, policies, authentication, and technologies that govern encryption and is ultimately what protects our text messages, emails, passwords, credit card information, and cute cat photos… okay, you get the point, right?
PKI is an infrastructure that has become an essential part of our everyday lives — and the overwhelming majority of us don’t even know what it is! Well, that’s something that saddens all of us here at Hashed Out, and that’s why we try to break down complicated, nerdy stuff into an understandable form.
So, what is PKI? In this post, I’ll introduce you to the art and science that is public key infrastructure (PKI) and everything that it entails.
Let’s hash it out.
The “Key” Problem in Conventional Encryption
But before we move on to answering the “what is PKI?” question and talking about how it works, let’s first consider a simple scenario. Let’s say there’s a spy named Alice who wants to send a confidential piece of information to Bob, her senior officer. She can’t send this information in plaintext as enemies could easily intercept and read/tamper with it. That’s why she must send this information in an unreadable form that Bob will be able to derive, but their enemies won’t. In other words, Alice will need to encrypt the information.

But here comes a problem. If Alice locks (encrypts) the message using a key (some logic), then how will Bob decrypt it? He must have the key with him, right? To give the key to Bob, there’s no option other than meeting with him face-to-face, which is totally impractical (to say the least) or to send it via courier and risk it being intercepted.
Such an encryption method is problematic not only in the physical world but also in the virtual world. Every time two computers want to communicate securely, they’d have to agree on a single encryption key every single interaction. This is a mathematical process and takes time. And if there’s a server (for example, a bank) that communicates with multiple users, then the server will have to perform a computational process for each client transaction, and that would slow it down even further. All of these things involve a variety of complex processes and agreements that must be handled at micro speed.
That’s where PKI comes in.
How PKI Changes Everything
In addition to conventional encryption (also known as symmetric encryption) in which the same key is used for encryption and decryption, PKI also involves the use of a key pair — a public key and a private key — in a process that’s known intuitively known as public key encryption. One of these keys encrypts information and the other decrypts it. Both these keys are distinct, but they’re mathematically related to each other. It means that the information encrypted with one key can be decrypted only using the key associated with it. The public key, as the name implies, is available publicly. The private key, on the other hand, is kept private.
So, if Alice and Bob are using public key infrastructure instead of the symmetric encryption method, Alice could encrypt the secret message using Bob’s public key that she has. Bob, with his private key, is then the only person who can decrypt the message. This way, they could communicate securely without letting their enemies read/tamper with it. Not only that, but Bob can be sure of that the message came from Alice and not from someone else.
Quite cool, isn’t it?
Popular Areas in Which PKI Applies
When answering the question “what is PKI?” you need to talk not only about what it constitutes but also how it’s used. There are several ways that businesses and organizations around the world use public key infrastructure:
Website Security (HTTPS/SSL)
The most popular use of PKI is in providing secure, encrypted communication between web browsers (clients) and web servers (websites). This is done by employing the HTTPS protocol, which is implemented by installing an SSL certificate on the web server.
The SSL certificate works as the identity card of the website through which browsers can verify that they’re communicating with the right website. When you purchase an SSL certificate, you get the public and private keys. The private key is stored secretly on the web server, and the server uses it to prove its legitimacy.
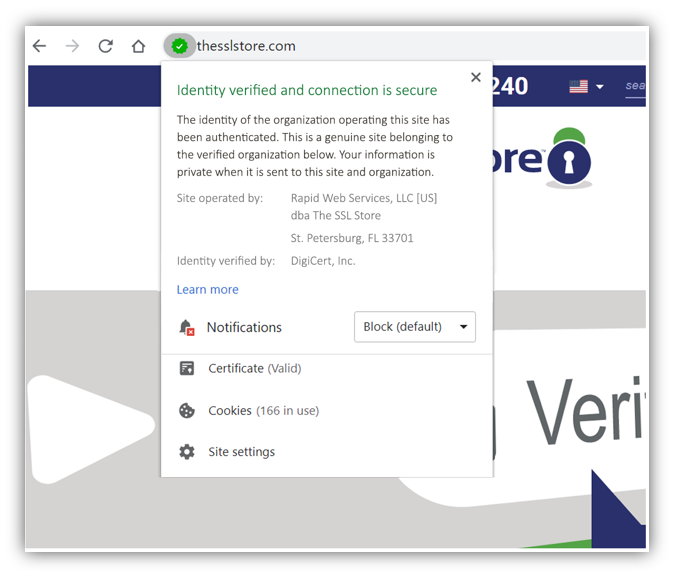
Through its use of PKI, an SSL certificate:
- protects the integrity of the message,
- protects the information from man-in-the-middle attacks, and
- authenticates both the communicating parties (browser and server).
Such a three-pronged approach to security is vital when you send critical information such as passwords, credit card information, private messages, etc. That’s why it wouldn’t be an exaggeration to call PKI “the bedrock of web security.”
Secure Shell Protocol (SSH)
Secure Shell (SSH) is a cryptographic network protocol that provides secure network services in between hosts and users over an unsecured network. It’s used to facilitate a secure remote login from one computer to another. SSH also has the public key infrastructure (PKI) at its heart.
Email Security (S/MIME Protocol)
Another significant use of PKI is done in encrypting and digitally signing emails and email communications. This is done through an internet standard/protocol known as S/MIME, or what’s known as a secure/multipurpose internet mail extension). These certificates are known as S/MIME certificates.
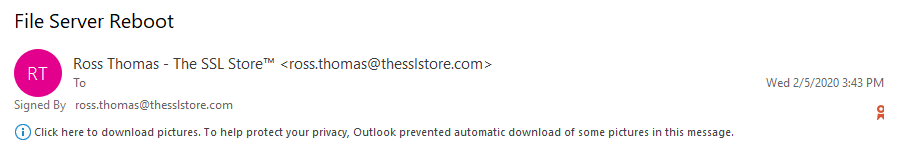
Like the SSL/TLS protocol, here too, PKI is implemented using a certificate — but the way they do so differs. Instead of encrypting the secure communication channel, this end-to-end encryption encrypts the message itself.
This means that S/MIME certificates not only encrypt emails but also digitally sign them to authenticate the identity of the sender and the integrity of the message itself.
Secure Messaging
Whether it’s WhatsApp, iMessage, Facebook Messenger, or other such messaging services, we all use communications services or apps. Many of these services are encrypted using PKI and protect against attempts of data interception and tampering. End-to-end encryption in particular is something that many governments would like to do away with, though companies such as Apple, Microsoft, and Facebook are holding firm in their plans to implement it.
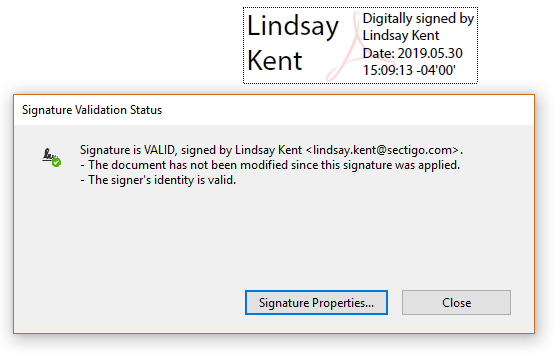
Document Signing
Like physical signatures to authenticate physical documents, there’s a need to sign documents digitally. For one, it helps the recipient ensure that the message is coming from a verified entity; it also allows them to ensure it’s not been tampered with. This is also done by PKI using document signing certificates.
Code/App Signing
Millions of users download millions of applications on computers and mobile devices every single day. Development companies or individuals create these programs. But what’s the guarantee that the software you’re installing is from the company/individual that you think it’s from? Can’t someone just change the name of the file and disguise malicious software as the software? Yes. And that’s a very real concern for everyone. Well, that’s where code signing certificates come in.
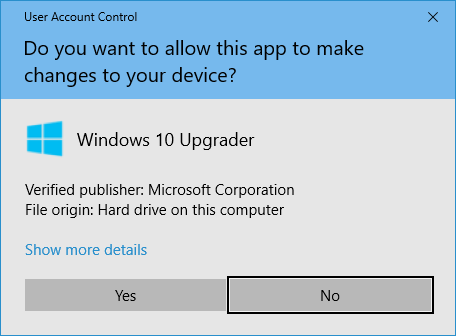
A code signing certificate authenticates the identity of the developer or publisher and the integrity of the file. This enables browsers to verify that the software itself hasn’t been altered in any way using public key encryption. It does this by applying a digital signature and a one-way hash.
PKI 101: Certificates, Keys, & Certificate Authorities
Many people ask us, “What exactly is PKI?” Well, the answer is quite simple: it’s a system that’s used for encryption and authentication purposes and isn’t so much a specific product/software. Therefore, it needs some material basis to implement encryption. This comes in the form of a variety of technologies (hardware and software), entities (such as certificate authorities, which we’ll speak to more later), processes, policies, and procedures. This system facilitates and governs encryption and everything that makes it possible — everything from the basics of public keys and digital certificates to the management of them and understanding the CAs that issue and revoke them.
Consequently, we can say that the public key infrastructure is made of three main elements: key pairs, X.509 digital certificates, and certificate issuing authorities.
Now that we understand key pair, let’s understand the other two crucial components of the PKI — digital certificates and certificate authorities (CAs).
Digital Certificates
A digital certificate is a set of files through which we can implement various security applications of public key infrastructure (PKI). In simpler words, it’s a document that proves the identity of its owner. It consists of information about the key, information about the identity of its owner, and the digital signature of the certificate authority. There are several different types of digital certificates, which (you may notice correspond to the popular uses of PKI that we covered above). Here are some of the types of X.509 digital certificates that you can find within the PKI infrastructure:
- SSL/TLS certificates
- S/MIME certificates
- Code signing certificates
- Client authentication certificates
Certificate Authorities
Let’s understand a simple scenario.If Alice wants to send Bob an encrypted message, she can get his digital certificate, encrypt the information using its public key and send him a secure message. But here comes a potential problem: How can Alice be sure that it’s actually Bob who owns the certificate and the public key she used? What if she actually sends a message to an enemy spy who’s just claiming to be Bob?
Here come certificate authorities (CAs) to the rescue!
Certificate authorities are the trusted third-party entities that issue and manage digital certificates. They’re the most crucial entity in PKI since millions of users — knowingly or unknowingly — are going to rely on them.
Before issuing a digital certificate, a CA is supposed to conduct a vetting process to make sure that it issues the certificate to a legitimate entity. Even just a small mistake in the vetting process could result in a mis-issuance and cause a disaster not just in terms of the damage, but also in terms of the overall trust in the system that is PKI. Therefore, to be a trusted CA, you must fulfil super-stringent criteria formed by an independent body of browsers, operating systems, and mobile devices that’s known as the CA/Browser Forum (or CA/B Forum for short). On top of that, you need a multi-million dollar infrastructure that includes sizeable operational elements, hardware, software, policy frameworks, practice statements, auditing, security infrastructure, and personnel.
Advantages of Public Key Infrastructure
With all of this in mind, there are multiple advantages of using public key encryption as part of your public key infrastructure. What are they? Oh, I’m so glad you asked…
Authentication
In the age when fraudsters and scamsters are trying every trick in the book to fool users, authentication/validation becomes an out and out necessity. When you’re transmitting information through a website, an email, or text messages, making sure that you’re communicating to the intended entity is a must. Thanks to the vetting process conducted by certificate authority and the use of the private and public key, PKI facilitates authentication in an unprecedented, smooth way.
Privacy
One of the essential security elements when it comes to online communication is privacy. After all, nobody wants to disclose their passwords, credit card information, or cute cat photos. By encrypting the data between the sender and the recipient, PKI keeps the original data secure so that only the intended recipient can see the data in its original format.
Data Integrity
When you send sensitive information online, it’s imperative for both the parties to have the recipient receive the data in the unaltered form. Through a technique called “hashing,” PKI allows the recipient to check whether the message/document/data has remained in the same form or not.
Non-Repudiation
PKI provides a mechanism to digitally sign online transactions (files, emails, documents, etc.), the way we physically sign documents and stuff. This way, it acts as proof that the person who signed it is the originator of the data. And, therefore, it also makes it impossible for the sender to deny that he/she was the one who signed and sent it. This is called “non-repudiation.”
Disadvantages of Public Key Infrastructure
While there are many advantages of public key infrastructure and the encryption it provides, we’ll admit — it’s not perfect. There are some specific disadvantages as well that are worth noting:
Speed
PKI is an extremely secure process that delivers what it’s supposed to. A large part of the credit goes to the key pair and super-complex mathematical algorithms. However, this complexity brings computational overhead when it comes to encrypting data in large volumes. As a result, it slows down the data transfer process to a minor degree, 5 milliseconds (ms) to be precise. In terms of CPU usage, the difference between encrypted connections and unencrypted connections is found to be 2%. Although this difference is quite small, you could consider migrating to HTTP/2 to speed up the data transfer process.
Private Key Compromise
The mathematics behind PKI is supposed to be so strong that even super-computers (let alone hackers) aren’t able to crack it within a practical time. However, the entire PKI security doesn’t depend on the unconquerable mathematics; it also depends on the security of the private key as it can decrypt the data encrypted by the public key.
Therefore, if the private key gets compromised, a cybercriminal doesn’t need to crack the super-complex mathematical algorithms. They can decrypt the data (of the past as well as of the future) with the private key and can also imitate the server to fool clients. This could result in organizational secrets, passwords, financial information, etc. being compromised. In other words, it could cause unprecedented disasters. This is a significant cause for concern while using PKI.
Reliance on Certificate Authorities
PKI is not a technology; it’s a system. And like every other system, it has components. One of the key components of PKI are the certificate authorities who issue the certificates. As we saw earlier, CAs are supposed to conduct vetting process and sign digital certificates to make sure that certificates are issued only to the legitimate people/organizations. But if, for some reason, the CA gets compromised, then it could cause security mayhem for millions of people and organizations worldwide.
How PKI Works in SSL/TLS
There are more than 4.5 billion internet users in the world, and all of them use PKI through SSL/TLS, even if they might not be aware of it. As you’re reading this sentence right now, your browser and our server are transferring data through a PKI encryption process known as an “SSL/TLS handshake.” Let’s explore this process in a bit more detail:
1. First, when the client (browser) visits the web server upon request by the user, the client sends the server its supported cipher suites and compatible SSL/TLS version to initiate the connection. This is regarded as a “client hello” message.
2. In return, the web server checks the cipher suites along with the SSL/TLS version and sends its public certificate to the client along with the “server hello” message.
3. On receiving the certificate file, the client (browser) authenticates it. If the certificate is found to be valid, the browser initiates the process of private key verification by encrypting the “pre-master secret/key” with the public key of the SSL/TLS certificate.
4. In return, the web server decrypts the pre-master secret with its private key.
5. Now, both the client and the server generate session keys from the client random, the server random, and the pre-master secret. This session key generated by both must be the same.
6. The client sends the “finished” message, encrypted with the session key.
7. The server sends the “finished” message, encrypted with the session key.
Once all of the above steps are done and the SSL/TLS handshake process is complete, a secure connection is established between the client and the browser.
Voila! That’s it.
(Note: The above handshake process is of TLS version 1.2. Although the process is quite complex, we’ve simplified it here for better understanding. Check out this post for an in-depth look at the SSL/TLS process. It’s also important to note that TLS 1.3 is also in use, but that TLS 1.2 is more commonly used as of the writing of this article.)
Final Word
We think we’ve thoroughly answered your question “what is PKI?” As you now know, public key infrastructure is the stone wall that keeps the cybercriminals at bay from our emails, passwords, financial details, personal messages, etc. It’s what forms the bedrock of today’s web security — and it’s impossible to imagine a world without it, considering that PKI keeps us secure from many fronts.
Is PKI unbreakable? No, it has scope for improvement; and that’s why, time after time we see changes in the PKI ecosystem. The world’s leading certificate authorities are pro-active and are always looking for ways to improve our security. It’s safe to say that we’re in the best hands.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown