DigiCert Leads Initiative to Enhance EV SSL Certificates
In collaboration with several other certificate authorities, DigiCert has proposed 4 enhancements to the EV SSL validation processes

“On the Internet, nobody knows you’re a dog.”
Cartoonist Peter Steiner penned those words in a cartoon strip all the way back in 1993. The cartoon was funny and made a lot of people laugh, but it was highlighting a serious issue that was just developing back then—how easy it was to trick people via the anonymity of the internet. Unfortunately, Peter nailed it! Today, that problem is even bigger than anyone – even Peter – could have imagined—1 in 25 branded emails is actually a phishing email.
So, why is online identity so important? How will DigiCert’s proposal help consumers?
Let’s hash it out.
Why Online Identity Is So Important
The internet is flooded with unknown actors, and a lot of times they’re up to nefarious activities—phishing, bullying, catfishing, scamming, preying on children, swatting, and more. That’s why most internet users tend to be suspicious of interactions with people, websites, and companies they don’t know—typically, we want to know the real-world identity of the individuals and companies we interact with online.
What would you think if you went to your local shopping center and saw a shop with no business name, like this?

You’d be intrigued — but you probably wouldn’t trust that company. You’d certainly have some questions! Customers don’t trust anonymity — they want to know who they’re doing business with.
The same thing is true online — customers want to know who they’re buying from. At your local mall, it’s pretty easy to tell who you’re buying from — there’s a physical store with signage and staff right in front of you. Online, though, identity can be… slippery. As Steiner pointed out, you can be a dog, a scammer, or a predator… and nobody will know until it’s too late.
In an environment saturated with anonymous trouble-makers, EV SSL is a great tool consumers can use to confidently see who runs a website, helping them decide whether to trust the website owner or not. That’s why we strongly support making EV SSL as strong and usable as possible — people want/need what it can provide. And that’s why we’re excited to see DigiCert leading the charge to update and enhance EV SSL.
DigiCert’s 4-Pronged Proposal to Enhance EV SSL
DigiCert is proposing four specific ways to update and enhance the CA/B Forum standards for EV SSL certificates. These enhancements will make EV SSL stronger and satisfy some “weaknesses” pointed out by security researchers. Let’s go through each of them, and see how they’ll help improve online identity for all:
1. Enforce Validation Level via CAA Records
A CAA record is a DNS entry that lets website managers restrict which CAs may issue certificates for their domain. It’s a great tool for fighting shadow IT certificates — ensuring that an organization’s certificates are centrally managed and authorized.
But currently CAA records can only specify certificate authorities. DigiCert is proposing expanding CAA records so domain admins can control or restrict the validation level of certificates that can be issued for their domain. For example, a website admin could restrict their domain to only issue EV SSL certificates from a certain CA.
Why This Is Beneficial:
Let’s look at a hypothetical scenario. Let’s say example.com hires a freelance web designer to update their blog with a fresh, new design for 2020. That designer isn’t authorized to issue SSL certificates for the domain. But let’s say the website designer installs a WordPress file editor plugin, so they can complete domain control validation and get an SSL certificate issued. Example.com now has an SSL certificate issued by an unauthorized party — they don’t control the certificate or the private key, which is a significant security issue. What happens when the certificate expires?
If example.com had implemented a CAA record that restricted the domain to EV certificates from DigiCert CA only, the web designer wouldn’t have been able to get that certificate issued because any attempt to get a certificate type not identified in the CAA record would fail.
2. Include LEI Data in SSL Certificates
If you’ve got a feeling of déjà vu right now, it might be because we mentioned this idea back in October 2019. TL;DR:
LEIs are Legal Entity Identifiers, they were created in the aftermath of the financial crisis that occurred a decade ago. They are numerical codes recognized by 150 different countries. The entire system is overseen by a Swiss non-profit called GLEIF. An LEI can help prevent collisions and confusion. Now, I can already hear the objections percolating, that, like confusing organizational names, people won’t know what to do with an LEI number. But there are several workarounds for that. For one, the browser could just use the LEI code and generate the associated information. Granted that might require an additional call, which may be anathema to browsers – but it’s an option. You could also make it easy to click on the LEI number and follow it to a database with the information. This would require the user to take an action, but some might find it useful. But more than anything, it could send up a red flag when an eCommerce website or some other organization that transacts in valuable data DOESN’T have an LEI.”
Why This Is Beneficial:
Adding LEIs to EV SSL certificates offers two key benefits:
- adds additional information about the organization, and
- provides consumers a direct way to research and verify company details for myriad reasons.
If you look up a company in the LEI database, you’ll get a report with a lot of details about the organization. Starting with basic info:
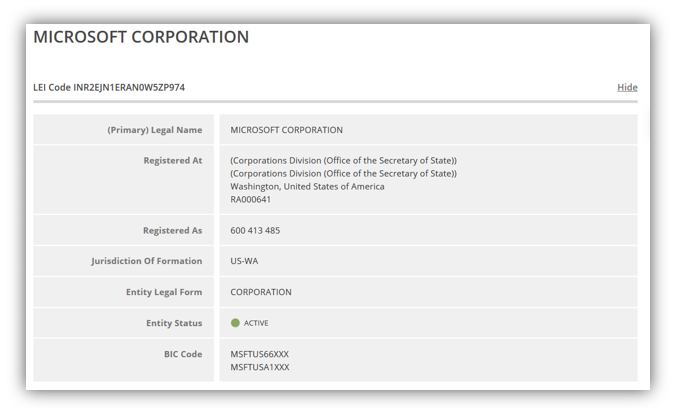
And even including information about subsidiaries and parent companies:
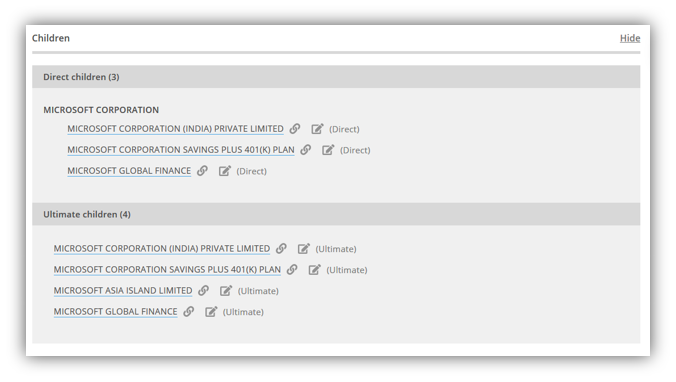
In the end, this info is ripe for being used as another data point to solve any corporate identity assurance use case. Like EV SSL, the infrastructure is already in place, why not use it (or at least consider it) for resolving such an apparent problem?
3. Standardize Data Sources for EV Validation
Under the current EV guidelines, each certificate authority decides what data sources they will use for validation of organization details in EV SSL certificates. (Keeping in mind that they’re validating organizations across hundreds of countries, there can be a lot of variation in the quality of data sources being used from country to county.) DigiCert is proposing that the CA/B forum specify a standardized list of acceptable data sources to use in the EV validation process.
Why This Is Beneficial:
Using standardized data sources will offer several benefits:
- improve the consistency and speed of EV validation,
- close some potential gaps bad actors could use, and
- this could be used as a basis to deal with naming collisions (which has been one of the criticisms against EV—for de minimis reasons if you ask me.)
4. Include Trademark Verification During EV Validation
Since EV SSL certificates are all about showing customers the verified identity of the organizations they’re interacting with, trademarks are a logical add-on. As DigiCert’s Dean Coclin explains:
Trademarks are well known, understood, unique and can be validated. Consumers recognize them and so if a browser wanted to include the trademark in their UI, they could do so with confidence that it had been properly validated. If they don’t, that’s fine, but it would be in the cert for any relying party to examine.”
Why This Is Beneficial:
Trademarks are another way for consumers to be sure they’re interacting with the company they think they are. For example, Windex is a trademark owned by the SC Johnson company. But many consumers probably don’t know the Windex brand is actually owned by SC Johnson. The current EV guidelines state that it can only say SC Johnson. However, if their EV SSL certificate displayed the Windex trademark, that might help a consumer be more confident that they’re on the official and intended website.
The Other Part Of The Equation: Browsers’ Need An Effective UI To Display Website Identity Information
Ultimately, for EV SSL certificates to reach their full potential in helping users, the browsers need to research, identify and introduce a more effective interface for displaying identity information to users. (Incidentally, the browser’s identity interface wouldn’t have to be limited to data from EV—it could contain data from other verified sources to provide consumers all the data they need to make an informed decision.)
Since Chrome and Firefox removed the old “green address bar” due to concerns that it wasn’t effective, the onus is on the browsers to develop a new UI that helps users understand who is running the websites they’re interacting with. In my opinion, removing EV without replacing it with a viable alternative did the world a huge disservice. EV may not have helped 100% of internet users, but it certainly helped more than 0%. It wasn’t perfect, but it was all the internet had. It’s like saying, since automobile accidents still happen at intersections, get rid of all traffic lights until we think of something better. For some reason, logic just seemed to go out the window on this one.
It doesn’t seem like too big of an ask for the browser community to seriously come together and help create a universal display that will help consumers with the identity of websites that they interact with. I think if browsers put their users’ interests first, the answer will come very easily.
Social Media Sites Have Already Created a UI for Online Identity, Let’s Learn From Them!
I took 15 minutes with my team and came up with a half-baked idea that seems to make quick sense. One of the big things that the EV naysayers harped on was that the “green address bar” needed education to understand what it actually meant. They believed that it should require no training or education and that it should just be immediately understood. Well, in minute three of our discussion, we realized that all of the social media channels over the past decade have already educated the world on this exact problem. The social media eco-system recognized issues with identity and addressed it head-on years ago by introducing the verified account status symbol. A verified account status is reserved for high-profile accounts of companies, brands or individuals that are especially vulnerable to impersonation.
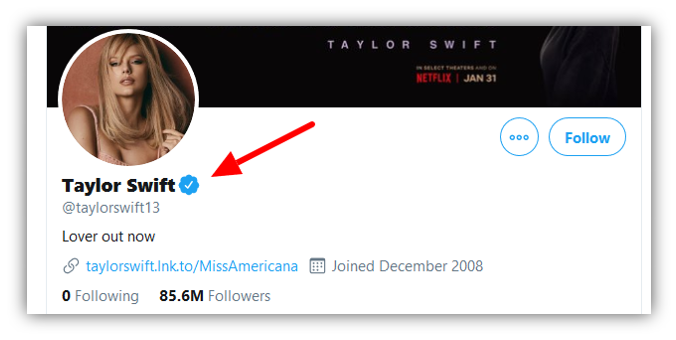
For obvious reasons, fake accounts that are used to impersonate a popular user on a social media platform could easily cause irreparable brand damage to both the real account holder and the platform’s business model. That’s specifically why the verified account status and symbol exist. Well, since the social media channels have already done the educating and have fully conditioned users at scale to look for verified account symbols when consuming content, why not adopt that developed behavior to work in browser environments? It can quickly be used to address online identity on a wider scale than just social media. Seems like the logical next step. Does it somehow go against browser business models?
Below is what we came up with over a cup of coffee. For DV SSL, since the lock doesn’t mean what it used to, simply hide it. Then let’s introduce two, or maybe just one, verified website symbol. I’d bet that if you did a study, users would immediately understand what this means. Without education. With conviction.
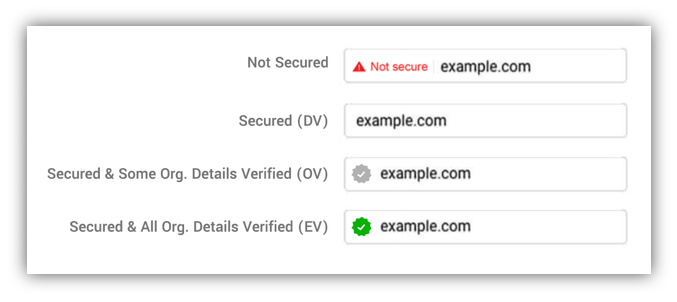
Mousing over the verified icon could display a tooltip showing more specifics on what the icon means.
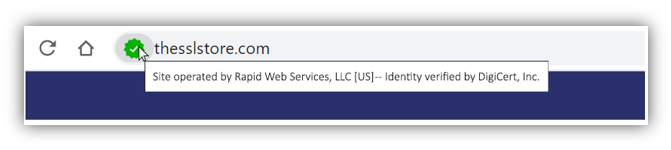
If you click on it, something like this could display. It’s very similar to what used to be displayed, but with a few tweaks.
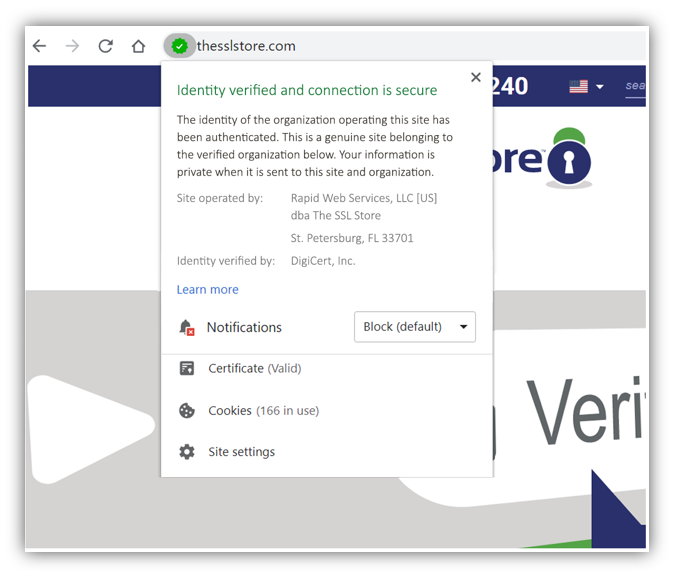
Just to reiterate, this idea would be after the EV guidelines have been enhanced. I’m sure there are more things worth consideration, but this took us 15 minutes in an informal meeting setting. I wonder what a group of browser security experts and security researchers could come up with if they tried to solve online identity head on… for the sake of Internet users. At the least, it’s worthy of a real discussion where all parties come together to really solve a larger issue for the greater good of society. Not just go through the motions.
On the Internet, nobody knows you’re a legit website. DigiCert is trying to do something about it. Browsers, you’re up.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown