Digital Signatures: Why you should sign EVERYTHING
A digital signature asserts identity and proves integrity – that’s never been more critical.
Digital Signatures have become confusing. The concepts at play aren’t what’s confusing so much as the way digital signatures are described, marketed and regulated.
That’s owing to the fact that digital signatures are so closely linked to electronic signatures and, as per usual, nobody can agree on the nomenclature. And of course there’s the patchwork of international laws that can make things even murkier.
And that all adds up to many organizations – ones that aren’t legally obligated – deciding it’s just not worth the trouble and avoiding it altogether.
That’s a mistake.
Whereas electronic and digital signatures have traditionally been viewed mostly as a contractual tool that can provide adequate consent without the need for the two parties to physically meet – digital signatures are capable of a lot more than that. They can assert identity and verify a file or program’s integrity. And in 2019, that’s never been more important.
So, today we’re going to try to clear things up a bit. We’ll talk about Electronic and Digital Signatures, what they do and why you should be using them for a lot more than just contracts.
Let’s hash it out.
What we’re hashing out…
- A digital signature asserts identity and proves integrity – that’s never been more critical.
- Where does it mention a Digital Signature?
- Are Electronic Signatures and Digital Signatures the same thing?
- Different Types of Digital Signature
- Classes of Digital Signatures
- Who uses Digital Signatures?
- What does the law say about Digital Signatures?
- How do I digitally sign documents?
- Adobe Digital Signatures
- Microsoft Digital Signatures
- Two different approaches to Document Signing Certificates
- Digital Signature key security is critical
- What does a Digital Signature actually secure?
- Ok, so how do Digital Signatures work?
- So, why should we be digitally signing EVERYTHING? (The Advantages of Digital Signatures)
Where does it mention a Digital Signature?
The United States passed the Electronic Signatures in Global and National Commerce (ESIGN) Act back in 2000, and has been amending it ever since. It’s made electronic and digital signatures legal in virtually all contexts. The EU enacted the Electronic Identity and Trust Services (eIDAS) regulation in 2016, which provides a framework for electronic and digital signatures.
The problem with both of them – at least from a digital signature standpoint (there are plenty of non-digital signature problems, too) – is that they never explicitly mention digital signatures by name. Rather, you’re left to extrapolate. And historically that’s gone poorly.
Not that this kind of thing is rare. A lot of these laws and regulations are written to be technology-, and sometimes even solution-agnostic so that they may stay relevant for longer. [Insert boilerplate statement about technology and cybersecurity evolving quickly].
But that leads to some rather confusing situations – like GDPR telling websites to use HTTPS, but never explicitly mentioning it, or SSL/TLS, or any of the actual mechanisms used in the real world to encrypt data in-transit.
In this case, the result is many people have no idea what the difference between an Electronic Signature (sometimes called an eSignature) and a Digital Signature is. The two are often used interchangeably. And the additional value provided by the Digital Signature gets lost in the shuffle.
Are Electronic Signatures and Digital Signatures the same thing?
Yes and no.
Before we get into the explanation, here’s a good visualization.
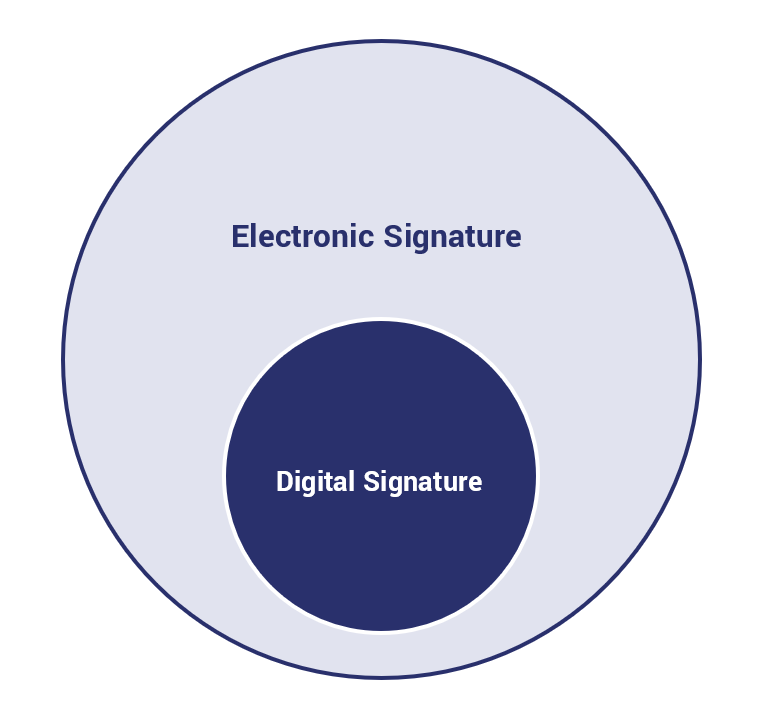
A Digital Signature is a type of Electronic Signature, but not every Electronic Signature is a Digital Signature. In other words, Digital Signatures are a subset of Electronic Signatures
What is an Electronic Signature?
An Electronic Signature, in the conventional sense, refers to any electronic process that indicates legal acceptance of an agreement/record.
An Electronic Signature consists of two components:
- Identity Authentication Method
- Secure Process with an Audit Trail
By “Secure Process with an Audit Trail,” we mean a method for demonstrating proof the file or document was signed securely and can be accounted for through each step of the process.
There are a variety of different mechanisms for identity authentication. A Standard eSignature only uses single-factor authentication. It verifies identity using things like email addresses, social media IDs, passwords, phone PINs – not exactly cutting edge authentication methods. Nor entirely reliable.
Advanced Electronic Signatures, which are defined by eIDAS, do use multi-factor authentication, which increases security.
That leads us to…
What is a Digital Signature?
Ok, remember how we just mentioned that an Electronic Signature requires both an authentication method and a secure process with an audit trail?
Well a Digital Signature is a type of Electronic Signature that uses digital certificates and PKI for authentication and encryption/hashing for security and its audit trail. Digital Signatures are Advanced Electronic Signatures (and in some cases Qualified Electronic Signatures – we’ll get to that next).
eIDAS defines Advanced Electronic Signatures as being:
- Uniquely linked to the signatory
- Capable of identifying the signatory
- Easily used with a high level of confidence by the signatory
- Linked to the signed data in such a way that any change to said data is detectable
To be clear, while eIDAS was written to be technology-neutral, this is mainly referring to Electronic Signatures that use Public Key Cryptography – Digital Signatures.
What is a Qualified Electronic Signature?
This is a specific type of digital signature, the most legally recognizable in eIDAS terms. eIDAS breaks down electronic signatures into three categories:
- Basic Electronic Signatures
- Advanced Electronic Signatures
- Qualified Electronic Signatures
The latter two, Advanced and Qualified are both digital signatures that require a CA to issue you a digital signing certificate. We’re going to get into the specifics a little more later, but a Qualified Digital Signature is basically an Extended Validation Digital Signature. The CA must perform a thorough vetting of the signer and the signing key must be physically stored on a qualified device like a physical hardware token, data card or cloud-based HSM.
Qualified Digital Signatures are considered on par with physical signatures and can be used for all EU business.
Electronic Signatures vs. Digital Signatures
Here’s a table that spells out some of the differences between Electronic Signatures and Digital Signatures. Or perhaps more appropriately: Standard Electronic Signatures vs Digital Signatures.
| Electronic Signature | Digital Signature | |
| Purpose | Used to verify the document. The source of the document and its authors are also identified. | Used to secure documents and files so they cannot be altered by people without authorization. |
| Regulation | Not regulated. | Authorized and regulated by trusted Certificate Authorities. |
| Security | Not Secure. | Protects signed documents and files from unauthorized tampering. |
| Types of Signature | Electronic signatures can be: scanned images, verbal agreements or checked boxes on an electronic document. | Different signatures schemes are based on document processing platforms from companies like Adobe and Microsoft. |
| Verification | Difficult to verify authenticity if the signature is not certified. | Can be easily verified using digital certificates and PKI. |
| Intention | Typically shows the intent to sign a document or a contract. | A legally binding, easily traceable way to sign files and documents, while also protecting it from unauthorized changes or tampering. |
Ok, now let’s talk about different types of digital signature and how the law applies to them.
Different Types of Digital Signature
We’re discussing Digital Signatures in the context of document signing in this article. But, Digital Signatures can be used in a number of different contexts. It would be fair to argue that the Digital Signature is the backbone of PKI.
Digital Signatures can be affixed to:
- Documents and Files
- Software
And they’re used to authenticate X.509 Digital PKI certificates – SSL/TLS certificates, S/MIME certificates, Code and Document Signing certificates.
Digital Signatures do far more than just authenticating the signer’s identity and protecting files from tampering. They can authenticate web servers and applications, they’re used to secure corporate email systems, there are tons of ways to use them.
Again, we’re focusing on document signing today, but Digital Signatures play a MAJOR role all across the digital landscape.
Classes of Digital Signatures

To avoid any confusion, this doesn’t relate to the eIDAS standards for electronic signatures. This actually pertains to the three classes of digital signing certificate and the digital signatures they make. Or, to put it another way, this is basically the document signing version of SSL/TLS Certificate validation levels. Each Certificate Authority uses its own verbiage, but the requirements are the same across the board.
Class One Digital Signatures
These are the equivalent of a DV SSL certificate. They’re the easiest type of document signing certificate to acquire and assert the least amount of identity. They are validated simply using an Email address and a username. As a result, Class One Digital Signatures cannot be used for legal business documents and are only suggested for use in low-risk environments.
Class Two Digital Signatures
The Organization Validation (OV) of the Document Signing Certificate world, Class Two Digital Signing Certificates authenticate the signer’s identity against a pre-verified database. This is good for environments with moderate risk and can be used for e-filing tax documents.
Class Three Digital Signatures
Basically the Extended Validation of Digital Signing Certificates. To create Class Three Digital Signatures the individual or organization must present in front of the issuing CA to prove their identity. Class Three Digital Signatures are good just about anywhere. They satisfy a high legal burden and are suggested for Enterprises and any environment that poses a high risk.
Who uses Digital Signatures?
Digital Signatures are widely used in the business sector, in government – just about every industry has a use for digital signatures, even if their use hasn’t been widely adopted yet. Here are some examples:
- Financial Industry – Financial sectors across the world use digital signatures for a litany of different business items. In the US, digital signatures can be used for contracts, online banking, loans, insurance – all regulated by the aforementioned ESIGN Act of 2000.
- Government – Myriad US government agencies digitally sign all of their publications, from budgets to legal guidance to congressional bills. But the US is far from alone in that practice, EU countries, adhering to eIDAS also make wide use of digital signatures.
- Healthcare – The healthcare industry is one of the biggest users of digital certificates, owing to the fact most medical records have gone online and there’s a great need to assert identity and authenticity in a medical context. Use of Digital Signatures is governed by HIPAA and ESIGN in the US, eIDAS and GDPR in Europe, and other national laws in other localities.
- Manufacturing – The manufacturing industry has a wide range of uses for digital signatures. They are a huge tool in speeding up processes like product design, QA, marketing and sales.
And of course, as we’ve alluded to, digital signatures are an integral part of cyber security, networking and most other internet-adjacent industries.
What does the law say about Digital Signatures?
It depends on where you live. We’ve already talked about laws and regulations like eIDAS in the EU and ESIGN in the US. But, obviously, the world is a lot bigger. So, here’s a quick reference guide for where Digital Signatures can be used in legal business around the world:
| Country | Legality | Restrictions |
| Argentina | Yes | Does not apply to death, family law or other “highly personal” matters |
| Australia | Yes | Doesn’t apply to migration or citizenship documents |
| Austria | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Belgium | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Bermuda | Yes | Some real estate agreements and wills are exempt |
| Brazil | Yes | Must use Brazilian PKI |
| Bulgaria | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business | |
| Canada | Yes | Some real estate agreements, wills, estate agreements and powers of attorney are excluded |
| Chile | Yes | Acts or contracts that require personal attendance may not use Digital Signatures |
| China | Yes | Documents related to personal relationships (marriage, adoption, etc.) and some real estate contracts are exempt |
| Colombia | Yes | Conveyance of real estate rights, aircraft, ships, corporations or other business associations; bylaws; mortgage agreements; unlimited agency agreements and incorporation of branches are exempt |
| Croatia | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Czech Republic | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Denmark | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Estonia | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| European Union | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Finland | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| France | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Germany | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Greece | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Hong Kong | Yes | Excludes wills, powers of attorney, government leases and some real estate deals |
| Hungary | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| India | Yes | Legal agreements like powers of attorney, wills and real estate are exempt |
| Indonesia | Yes | Digital signing certificates must be issued by government-approved CA; notarial deeds, letters of court summons and bond certificates are exempt |
| Ireland | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Israel | Yes | Qualified Electronic Signatures only |
| Italy | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Japan | Yes | Using digital signatures for documents related to property transfers or wills is advised against (but legal) |
| Latvia | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Lithuania | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Luxembourg | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Malaysia | Yes | Section 62 of the Malaysian Digital Signature Act REQUIRES the use of digital signatures where the law requires a signature |
| Malta | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Mexico | Yes | N/A |
| Netherlands | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| New Zealand | Yes | Some types of agreements have additional requirements |
| Norway | Yes | Debt certificates, premarital agreements and a board’s signing of annual accounts are examples of excluded transactions |
| Peru | Yes | N/A |
| Philippines | Yes | Section 8 of Republic Act No. 8792 specifies ALL signatures must use a digital certificate |
| Poland | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Portugal | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Republic of Cyprus | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Republic of Korea | Yes | N/A |
| Romania | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Russia | Yes | N/A |
| Singapore | Yes | The law excludes wills, negotiable instruments, powers of attorney and some real estate transactions |
| Slovakia | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Slovenia | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| South Africa | Yes | The law excludes long-term leases; transfers of property; the execution, retention and presentation of wills; and bills of exchange |
| Spain | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Sweden | Yes | Subject to eIDAS; Qualified Electronic Signatures can be used for all EU business |
| Switzerland | Yes | N/A |
| Taiwan | Yes | Getting express consent to do business electronically is pre-requisite |
| Thailand | Yes | N/A |
| Turkey | Yes | Digital Signatures must be made using digital certificates |
| United Kingdom | Yes | Subject to eIDAS (for now); Qualified Electronic Signatures can be used for all EU business |
| United States | Yes | Subject to ESIGN act, which excludes real property transfers, wills and some legally required notices to consumers |
| Uruguay | Yes | N/A |
How do I digitally sign documents?

The first thing you need to do before you digitally sign anything is acquire a Document Signing certificate. As we just discussed, there are three different classes.
Unfortunately, there are no free document signing certificates to be had. This is a little different than SSL/TLS, the relying party’s identity does need to be validated. That’s kind of the whole point of Digital Signatures.
And that validation ain’t cheap. So, you’ll need to put a little money down. Frankly, there’s a range of pricing that is contingent on a number of factors determined by your own use case. Some Class One certificates run as low as $13. Other classes can be in the hundreds. It really depends what you want to use it for, what class you need and who you’re purchasing it from.
And, as with Code Signing, different platforms have slightly different requirements. They all use X.509 digital certificates, but the way they’re used – the clients, the file formats, etc. – vary somewhat.
The biggest two platforms for document signing are Adobe and Microsoft. Not surprisingly, they also have the two most dominant document processing platforms.
Adobe Digital Signatures
Adobe has two different types of signature:
- Certified
- Approval
Certified Signatures are Digital Signatures, they indicate the identity of the document’s author and place a blue ribbon atop it showing the information from the certificate used to sign it. That includes the owner’s name and the CA that issued it.
Approval signatures, by contrast, are meant to capture things like physical signatures and any other requisite information.
How to create a Certified Digital Signature in Adobe
Before we get started, keep in mind that you need to have digital signatures enabled by someone with Admin privileges to sign anything. Now, here’s a quick guide on how to digitally sign Adobe files:
- In the Adobe Sign dashboard, choose the Fill & Sign tool.
- Open the document you need to sign.
- Click the Sign tool, then select Add Digital Signature.
- Select Cloud-Based Digital ID certificate, then click Apply.
- Now select the CA you’d like to issue your document signing certificate or click the link to get a new digital ID.
- Follow the prompts to obtain your document signing certificate (they may differ CA to CA) and then activate it.
- Now it’s time to sign, select Click to Sign and enter the PIN number you chose, plus any additional validation information that’s required.
After that, Adobe will create a signed version of the document for you.
Microsoft Digital Signatures
Microsoft has similar signature options, just with slightly different names:
- Invisible
- Signature Line
Invisible signatures are basically the same as Certified signatures, they’re digital signatures that provide authentication and indicate whether the document has been tampered with.
Signature Lines are used to capture signatures, you can actually sign a signature line using a document signing certificate and a digital signature, but we’re going to show you the other way – an Invisible Digital Signature – because that’s a little more in scope and a bit more straightforward (incidentally, this might be the only context in human history where something invisible is MORE straightforward).
How to Create an Invisible Digital Signature in Microsoft Office
Again, before we get into this, you need to have the correct permissions before you go signing anything. We can’t just let people go signing documents all willy-nilly. So assuming you’ve got signing enabled, here’s how to do it in Microsoft Office:
- Open your document and click on the File tab.
- In the Info section, select Protect Document.
- In the drop-down menu, click Add a Digital Signature.
- Select a Commitment Type, this is basically just explaining what you signed and why you signed it.
- Insert the physical hardware token your document signing certificate’s private key is stored on.
- Enter your PIN number and click OK.
You should see Signature Confirmation box indicating that the signing went correctly.
Two different approaches to Document Signing Certificates

There are now, for all intents and purposes, two different variants of document signing certificate. Maybe variants is a bit too strong, let’s say there are two different approaches to document signing certificates.
As you just saw, Microsoft continues to use the more traditional approach. A document signing certificate is issued and the certificate is stored on your servers and its key is kept on a physical hardware token, which might be an HSM (Hardware Security Module) or in Microsoft’s case, on a PIV (Personal Identity Verification) smart card. It must be presented, along with a PIN or password (two-factor authentication) to create a Digital Signature.
On the other end of the spectrum, what Adobe has been pushing towards is a cloud-based model. Rather than the certificate and key being stored locally, or on a physical token, it’s stored in the cloud on a cloud-based HSM and the end user can outsource securing it to some extent. It also has the added benefit of making signing possible from anywhere – not just on your own network.
Adobe still accepts physical hardware tokens if you want to go that route, but organizationally it’s really pushing its cloud-based digital signature model hard.
There are trade-offs to both approaches. On the one hand, using the traditional method puts a greater onus on organizations and individuals to secure their own keys and certificates. But it also provides a greater degree of control. The cloud-based approach puts it out of your control to some extent. So while there is a benefit to being able to sign from anywhere, it may come at the cost of better security.
Digital Signature key security is critical
If you haven’t noticed a theme here at Hashed Out, it’s largely: “secure those keys!” Any kind of key compromise can be catastrophic, but no more so than when it comes to signing keys. The ability to make a trusted digital signature is powerful. It’s why Certificate Authorities require so much validation before they’ll even issue you a document signing certificate.
While there’s tremendous upside to being able to sign and secure documents, there’s also tremendous risk should the key used to make the digital signature ever falls into the wrong hands.
Imagine the ability to imitate a VP or C-Suite level executive by creating signed and trusted documents and files. Think how much trouble that could cause. It could blow up internally, be used to trick partners or who knows what else – this is part of why I’d never make it as a black hat: I’m just not criminally creative.
At any rate, that’s why qualified digital signature keys are required to be stored on physical hardware tokens. It’s a lot easier to break into a company’s network than it is to break into their offices. That means you can focus most of your efforts on physical, internal safeguards like access control cards and good old-fashioned locks and stuff.
The cloud-based version obviously doesn’t take that approach, instead storing keys in the cloud on an HSM where they are (ideally) just as difficult to access without authorization.
Personally, I prefer the physical HSM approach because I’d rather the hacker have to mug me than just breach my network. I like my chances more with the former.
What does a Digital Signature actually secure?
There’s a little bit of confusion on how digital signatures provide security and this is largely born out of the way they’re marketed. It’s not done to be deceptive or mislead anyone so much as it’s just a function of trying to explain an extremely technical concept to someone that really just wants to know what it does.
There is no good elevator pitch for hashing and check-sums, so it’s easier to just say that a digital signature protects documents from unauthorized modifications – that it can’t be tampered with.
The truth is a bit more complicated. Encryption is not the cryptographic function being used with digital signatures. Cryptography and encryption get used a little too interchangeably – which is a topic for another day – but there are other cryptographic functions beyond just encrypting and decrypting data.
The portion of the Digital Signature that “protects” against tampering is a cryptographic function called hashing. Hashing is essentially a one-way function. Reversing a hash is prohibitively difficult, even more so than breaking encryption, which makes it a good check-sum.
You can still alter a signed document. A digital signature does not actually prevent someone from going in and tampering with a signed file. But, much like the dye packs banks use or that little sticker on your cell phone that changes colors if it gets wet – a digital signature will indicate that the file WAS tampered with and not to trust it.
That’s done thanks to hash functions.
Ok, so how do Digital Signatures work?

Now we’re getting into the technical portion. We touched on the integrity portion last section, but let’s zoom out and look at the whole thing.
Digital Signatures are a foundational part of Public Key Infrastructure. When we say PKI we’re referring to the entire ecosystem of Certificate Authorities, Root Programs, Browsers – all the various parties that issue, interact with and regulate digital certificates.
With a digital certificate, the certificate itself acts as the identifier, authenticating the identity of the entity that owns the private key. The private key is what actually performs the cryptographic functions that the certificate is intended for. Each private key is unique, and each key has its own unique signature.
OK, one more thing before we get into the actual step-by-step process: hashing.
Hashing is a cryptographic function that maps data of any length to a fixed-length output. As we said earlier, it’s a one-way function. That makes it worthless for encrypting information, but great for use as a check-sum.
That’s because no two disparate inputs can ever create the same hash value. Were that to ever happen it’s called a collision and the hashing algorithm being used would be considered compromised and then deprecated. Google created a SHA-1 collision several years ago just to underscore the need to deprecate it.
Anyway, when you perform a hash function on a piece of data, as long as it hasn’t been changed someone else could perform the same hash function and get the same hash value/result/digest. But, if it’s altered even the tiniest bit, it will produce a completely different hash value when you run the hash function on it again. That’s what a check-sum is. You run the same hash function on the same piece of data to check if it’s been altered.
Git does the same thing for versioning. In fact, it still uses SHA-1.
How it Works: Creating a Digital Signature
Now let’s look at the process step-by-step
- The file or document you’re signing is hashed.
- The hash value that’s produced is signed/encrypted with the private key.
- In addition to the signature, a timestamp is added to indicate the time of signing.
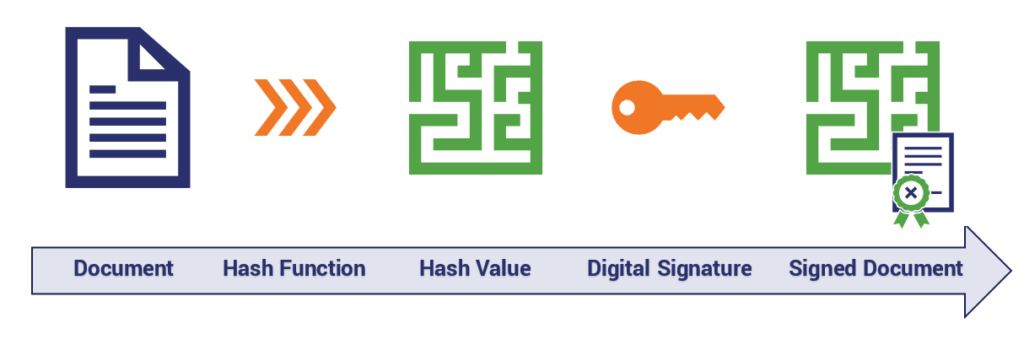
That’s pretty much it from high level. The document is hashed, the hash value it produces is signed and “encrypted,” then sent along with the document signing certificate and its public key.
Remember, the document itself isn’t being signed, just the hash of the document.
Now let’s dig in a bit. Oftentimes when you see document signing and digital signatures described it will say that the private key “encrypts” the hash.
That’s true to an extent but also a little misleading.
Because of the mathematical relationship between the public and private key, the public key can be used to verify or “decrypt” the private key’s signature. The reason the document itself isn’t signed, and rather just the hash value is to save time and resources. Signing is an expensive function, so it’s easier to sign a fixed-length piece of data than the alternative.
Ok, so now let’s talk about how a signature is read and authenticated.
How it Works: Reading a Digital Signature
Let’s round this out by discussing what happens when a digital signature gets read. We’ve already covered what goes into creating one, now let’s reverse it and show how the digital signature gets read.
- The recipient of the signed document (or rather, their device/system/network) takes the public key from the accompanying document signing certificate and uses it to decrypt the signature/hash.
- The same function that was performed during the signing is run again on the document.
- The recipient checks the hash value that was just produced against the one that was signed.
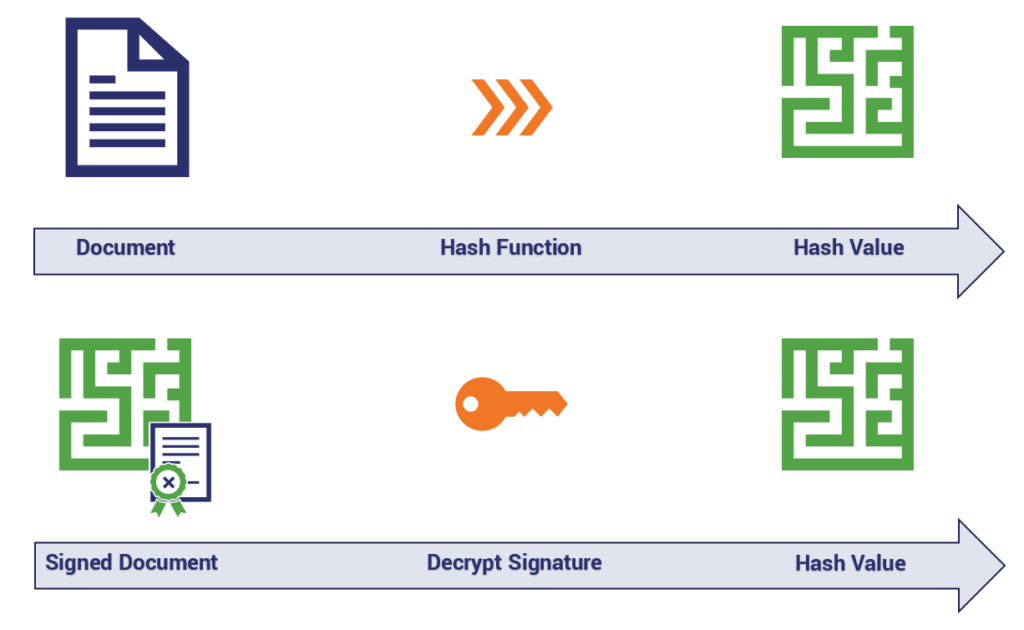
Provided both – the digital signature and the check-sum – can be verified the document’s authenticity and integrity have been proven.
However, if any part of the check fails, then an error message is issued and the document is considered untrustworthy. Or, in other words, those two green symbols that rather hamfistedly represent a hash value in the visualization above must be equal.
So, why should we be digitally signing EVERYTHING? (The Advantages of Digital Signatures)
Well, if the past 5,000 words haven’t convinced you, let’s just lay out the advantages of digital signatures in some bullet points. Maybe you’ve been skimming. Or maybe you’re just messing with me… with this hypothetical question… that I posed to myself…
- Identity – A unique digital signature asserts your identity and prevents you from being impersonated.
- Authenticity – Thanks to the hash functions involved with Digital Signatures any unauthorized modifications to your signed documents will be immediately evident.
- Strong Validation – Certificate Authorities are obligated to perform their due diligence, which means others can be sure you are who you say you are.
- Time Stamping – Knowing when a document was signed can be incredibly important, Digital Signatures include a timestamp that indicates when the signature was created.
- Two-Factor Authentication – An additional layer of security comes in the form of passwords, PIN numbers and other credentials that are required at the time of signing.
But beyond bullet points, being able to identify a document’s author and whether or not the document has been tampered with since it was signed is a key part of data security. It can help protect against imitation, phishing, malicious payloads – you name it.
When you send someone a digitally signed document it leaves no doubt that this is the genuine article. And authenticity has never been more important than it is right now in 2019.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown