The Role of Access Control in Information Security
Access control systems are everywhere and play a key role in identity and access management (IAM)— let’s break down the different types of access control models & how they work
Access control is a part of everyday life and is also an integral component of IT and data security for businesses. It’s a broad term that describes a variety of ways to control who has access to your organization’s resources. In addition to giving you greater control over your network, data, website, or other sensitive systems or assets, access controls also help you stay compliant with various industry standards and regulations.
By restricting access to sensitive systems or data, you’re limiting the potential risks associated with data exposure. For example, if fewer people have access to your customer database, it’s less likely that the database will be exposed through credential compromise or insider threats.
But what is access control? What are the different types of access control systems and models, and how do they work? And what are some of the challenges of implementing access control for businesses?
Let’s hash it out.
What Is Access Control? Definition & Meaning in Security
In the most basic sense, access control in information security is about determining who gets access to what stuff (files, directories, applications, etc.). For example, if I access our company’s file server, I can see documents related to marketing. Someone in our Finance department, on the other hand, would be able to review financial documents. But someone external to the company wouldn’t be able to access any of these things.
All of these things are possible thanks to access controls that determine who can access what.
Looking for a more technical definition? Access control is a broad term that describes policies and methods that ensure only verified individuals can physically or virtually touch items that they have permission to access. This process involves restricting access or granting permissions that allow someone to do something to a protected item. This includes having permissions to do any of the following to protected items (digital or physical resources):
- Access,
- Read,
- Modify,
- Communicate,
- Delete or otherwise destroy.
For longtime IT cybersecurity expert Greg Scott, access controls typically boil down to understanding the relationship between two specific terms: subjects and objects.
“Subjects are usually people or groups. Objects are usually files or directories. The key is, subjects access objects, and so access controls regulate how subjects access objects.”
In this understanding, objects could be resources that you want to protect from unauthorized access, use, or disclosure. And the subject is the user (or group of users or even non-person entities such as applications or services) that the access controls apply to. So, access controls (in a more technical sense) are the tools, policies, models, and mechanisms that enable you to grant or restrict access to your organization’s digital or physical resources. This includes everything from restricting or granting access to specific files and databases to IT systems and physical locations.
If you look at the definitions of access control on the National Institute of Standards and Technology (NIST) website, you’ll see a lot of variations. However, they all basically mean the same thing in a roundabout way: access control is a way for you to ensure that only the individuals (or groups) you choose have access to your sensitive data, applications, technologies, and critical infrastructure.
Basically, these types of physical and logical restrictions prevent unauthorized individuals from doing things they shouldn’t with your sensitive systems or data. Furthermore, they also help to prevent inadvertent exposure or disclosure of sensitive items.
Where Authorization and Authentication Fit Into the Picture
Authentication and authorization are key components of information security, cybersecurity, and access control. They’re also integral to identity and access management.
- Authentication is all about proving or verifying that someone is who they claim to be. This differs from identification, which is when you (or someone else) claims to be you, but that claim isn’t verified. Authentication involves verifying someone’s identifying information (for example, a username and password) against the information you have on file. This process prevents Carrie in customer service from pretending to be Harry from Human Resources to access systems she doesn’t need access to.
- Authorization refers to granting someone the ability to access, use, or modify some type of asset or resource. So, once they’re logged in or otherwise authenticate themselves, this next part of the process will determine whether or not they have the system permissions or privileges to do what they’re trying to do.
So, let’s consider an example. Let’s say I want to access one of my company’s intranet sites to access some marketing related files.
- Identification would be me typing in my username in the login field for the page.
- Authentication would be me typing in my corresponding password (or using a PKI-based passwordless authentication method such as a client authentication certificate) to prove my identity so that I can access the site.
- And authorization would be the permissions or access privileges that my director or our sysadmin set for me. These access controls determine what I can do to any files once I’ve proven my identity and logged in to the system.
Types of Access Control Systems
Access control systems can be logical or physical in nature and fall within three sub-categories:
- Technical control systems,
- Administrative control systems, and
- Physical control systems.
Does your organization require your employees to use an ID badge to access specific areas, such as your server room? That’s an example of physical access control because it prevents just anyone from meandering in. An example of administrative access control is limiting which of your employees — or groups of employees — can make changes to specific files. A technical form of access control would be limiting which IP addresses (or ranges of IP addresses) can access your network through your firewall.
For example, here at The SSL Store, only certain individuals can access our customer records. Same with our blog — not everyone has or needs access to add, modify, or delete posts on Hashed Out. (I feel lucky enough to be among the chosen few.) If everyone could access all of our systems, it could spell disaster in the event of credential compromise or an employee being swayed by the power of the Dark Side (as Obi-Wan would say).
Some examples of virtual and physical access control systems include:
- Login credentials (such as usernames and passwords).
- PINs and one-time passwords (OTPs).
- Virtual private network (VPN) access to internal networks.
- Physical access cards, FOBs, tokens, locks, and keys.
- Security guards with access lists.
- Biometric readers (such as for facial, retinal, and fingerprint scans).
- Digital authentication certificates and digital keys.
While access controls may seem inconvenient or cumbersome, they’re integral to the security of your organization. They can help to prevent your sensitive data from being exposed as the result of human error or an employee going rogue by limiting who has access to it.
Access Control Lists
An access control list, much like the name would imply, is a list of privileges or permissions that authorize or deny access for specific people or groups to specific objects. ACLs consist of various access control entries (ACEs), which specify the subject and any privileges they have for specific objects.
ACLs serve different functions in terms of how and where they’re used and are central to several different access control models — we’ll speak more to those shortly. In the meantime, here are just a few quick examples of common access control lists:
- Filesystem Access Control Lists,
- Active Directory Access Control Lists, and
- Network Access Control Lists.
How Access Controls Come Into Play Within Your Organization
When talking about access controls, they can be implemented done through multiple avenues. Let’s consider a few examples of access control that your organization might already be using.
File-Sharing Platforms like SharePoint and Google Docs
If you use these types of file-sharing platforms, then you’re already familiar with this type of access control. Whenever you create or share a document, you can choose to either keep control to yourself or give permissions to view or modify the document as a viewer, commenter, or editor.
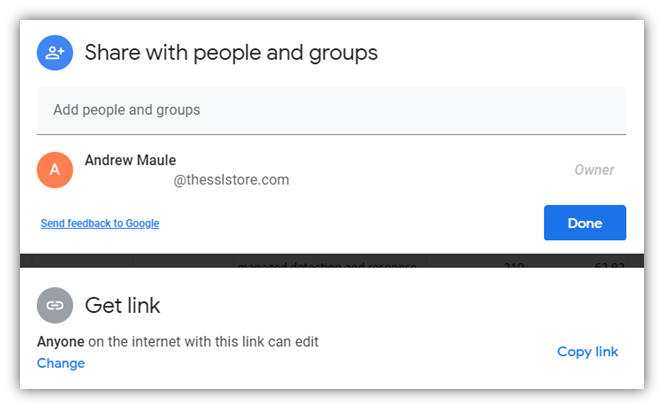
Think about the last time someone sent you a link to their Google doc file. This frequently happens for us when we’re working with guest contributors. We’ll receive a link to a Google Doc file that we don’t have access to, so we’ll have to request access to gain permission to see and edit it.
Windows Active Directory
We’ll use Windows Active Directory as our next example. You can set up folder permissions for groups and individuals in Active Directory:
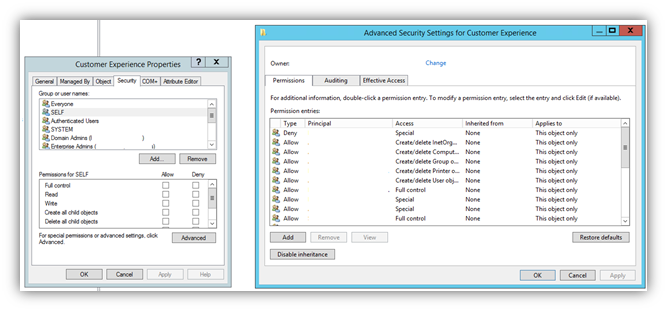
A screenshot from Active Directory that shows user and group permissions. The image has been edited to remove sensitive information.
These permissions can be set for specific objects or groups of objects.
Linux Access Controls
Don’t worry, penguin fans; you also can use access controls for filesystems. This process involves the use of Linux ACLs to grant permissions to one of three options: users, groups, or others. The level of access that each of these permission categories could have includes read, write, and execute.
Now, I’m not going to go into the specifics here about how to set up Linux ACLs. But you’re welcome to check out this great resource from RedHat that goes over setting up a basic ACL using Linux.
WordPress Access Controls
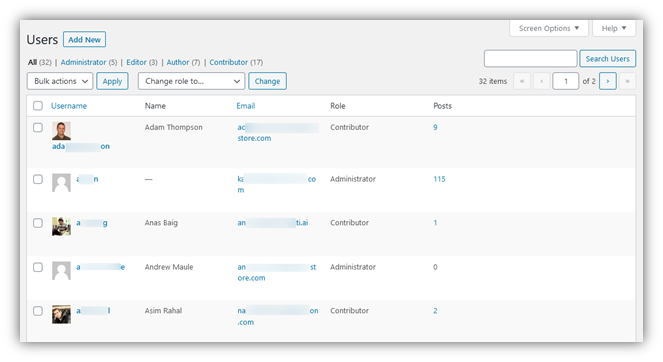
In WordPress, you also have the option of implementing access control. Think of the different access control settings in WordPress. You may give a few users Administrator access, which allows them to give other users access, whereas you may only give some editors author access.
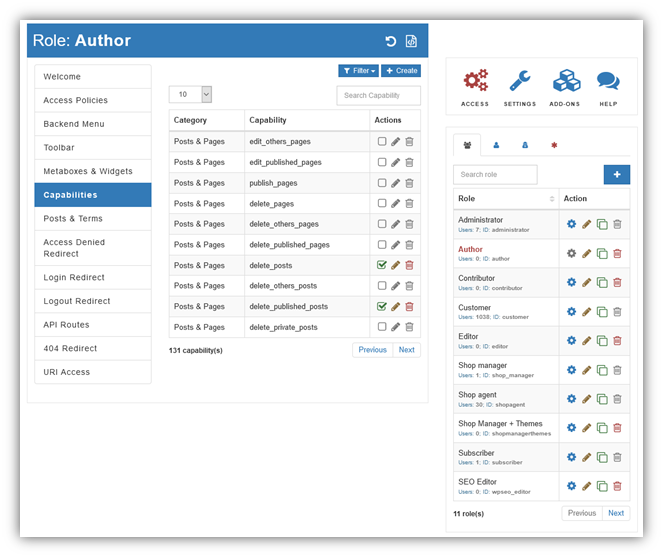
You can also use WordPress plugins like the Advanced Access Manager (AAM) to set more specific, granular access controls. For example, in AAM, you can manage access for any type of role:
4 Access Control Models to Know
There are actually several models or varieties of access control to choose from in information security to determine user access. If you check out other websites’ lists of access controls, you may notice that there are anywhere from two to five main access control categories. Here, we’re just going to go with four and list them alphabetically to make it easy to follow.
1. Discretionary Access Control (DAC)
Discretionary access control enables a file or system owner to control, grant, or limit others’ permissions. For example, think of when you create a Google Sheets spreadsheet in Google Drive. As the file owner, you can choose to grant access to specific individuals to either access, read, or modify the document. You can also set it so that anyone with a link can access the document or open the document up to the public.
DACs, which are commonly used for operating systems, rely upon access control lists (ACLs). These lists generally specify individuals (or groups of individuals) along with their access permission levels. Discretionary access controls are also more flexible and less restrictive with the next type of access control we’re going to talk about. However, they’re also the least secure method as well because access control is left up to the file or system owner.
Of the different control access models we’ll discuss here, DACs are the least restrictive and are commonly used.
2. Mandatory Access Control (MAC)
Unlike DAC, mandatory access control is nondiscretionary and is simply based on the decisions of a central authority such as a security administrator. The file owners and users themselves have little to no say in who can access their files.
MAC relies on labels (such as confidential, secret, top secret, etc.) and clearances to associate any programs or levels of access with users. Documents receive labels that determine which levels of clearance you need to have to access, modify, or disclose them.
An administrator can set these levels of access for individuals and groups of users, which the users themselves can’t change. This model of access control is the most restrictive and has been adopted by U.S. government and military organizations to exercise control of sensitive information.
3. Role-Based Access Control (RBAC)
As you can probably guess from the name, role-based access control gives access permissions based on user roles. What I mean by “role” is the functions that an employee performs. Users may have one or more roles and may be assigned one or more permissions as a result. Doing this gives users who have those roles access to the info they need to do their jobs without affording them access to information that they don’t need. RBAC is a broader form of access control than, say, MAC.
In Windows, for example, you can use Groups to set RBAC.
Let’s say, for example, that you want to grant access to employees’ benefits information to human resources specialists John Doe, Jane Smith and Lois Lane, and HR manager Kermit D. Frog. Rather than having to manually grant access to each person individually, you could instead grant access to the group of human resources specialists and their manager. Since they’re already identified as having specific roles within your organization, they’ll automatically be granted access through this type of RBAC.
NIST says that the first formal general-purpose role-based access control model came about in 1992, although the concept of specifying roles and responsibilities has been around since at least the 1970s. There have been several variations of the RBAC model that incorporate varying levels of hierarchy — from partially-defined to fully-defined hierarchy. A unified standard was adopted by the International Community for Information Technology Standards (INCITS) as ANSI INCITS 359-2004 in 2004.
4. Attribute-Based Access Control (ABAC)
The next type of access model is known as attribute-based access control (ABAC). According to NIST:
“It represents a point on the spectrum of logical access control from simple access control lists to more capable role-based access, and finally to a highly flexible method for providing access based on the evaluation of attributes.”
ABAC helps us to link people or groups with the types of data that they can use within specific parameters. It supports the use of Boolean logic to create more granular policies that are also more flexible.
Attributes could be specific characteristics or specifications that are applied to either subjects (subject attributes) or objects (object attributes). Some examples of subject attributes include management levels, employee IDs, organizational roles.
Some examples of how you can use this type of access control include:
- Restricting access to your network or specific systems before 9 a.m. or on the weekends.
- Limiting the ability to edit a document to the file owner.
- Giving permissions to a specific class of employee to read or modify files within a specific folder.
- Restricting access to software to employees within a specific team.
Why Access Controls Matter Regarding Data Security & Compliance
Whether you’re a small business or a large organization, controlling access to your data or physical infrastructure is integral to security. Scott says that strong access controls are important for all organizations, regardless of size. It helps them to:
- Limit liability and damage from attacks
- Carry out anomaly tracking, and
- Increase accountability.
Scott calls out the importance of DACs in particular:
“Every organization needs a good discretionary access control model, only granting permission to subjects with a business need to access various objects. By itself, this single simple access control could limit the damage from a ransomware attack or protect an organization from huge potential liabilities.
Good password/passphrase management is also important to all organizations. Larger organizations must solve the same problems, but on a bigger scale, and so their models and tools are more sophisticated than small organizations.”
What some people may not realize is that permissions and access controls are central to several industry data privacy-related regulations. For example:
- The Payment Card Industry Data Security Standards (PCI DSS) outline requirements for businesses that handle credit card related consumer data. Requirements 7, 8, and 9 entail implementing strong access controls to protect said data.
- The Health Insurance Portability and Accountability Act’s (HIPAA) Security Rule Access Control standard also outlines the need for limiting access. HIPAA compliance depends on it. Any employee who has access to electronic personal health information (ePHI) must be assigned a username and PIN code from a centralized authority.
- The Gramm-Leach-Bliley Act (GLBA) also outlines requirements for financial institutions regarding user access rights and privileges.
Of course, this isn’t a comprehensive list. There are other data privacy and encryption laws that call out restricting access. But this brief list at least gives you an idea about some of the types of regulatory compliance concerns that your business faces.
Access Controls Are Central to Zero-Trust Security
Maintaining strict access controls is also essential to the concept of zero-trust security. That’s because the zero-trust model requires users to have authorization and to authenticate themselves before they can access or modify any systems or data — and they must continue to do so to maintain said access.
Basically, the idea here is that everything is treated as being suspicious — even when it’s something that’s coming from inside your network.
Check Point’s 2020 Cyber Security Report underscores the importance of access control as part of a zero-trust network:
“The best practice is to create a very granular segmentation by defining “least privileged” access control strategy; where user/system can gain access only to the resources that they are meant to use. For example, an access to source code should be granted only to R&D team members. This way only the absolute minimum, legitimate traffic between segments is allowed, while everything else is automatically denied.”
The Challenges of Controlling Access for Organizations & Businesses
Access control systems are critical to your organization’s information security and cybersecurity overall. But when restrictions and permissions aren’t implemented well, and if these controls aren’t regularly maintained, then it can be disastrous for your business.
So, what are the challenges for managing access for businesses large and small?
There’s a Perception That Access Controls Limit Efficiency
Considering that access controls are among the most basic ways to protect your data and property, it might come as a surprise that some organizations are resistant to doing so. Why? The answer often comes down to human nature.
People are frequently resistant to change. They also prefer for things to be convenient and to have fewer steps involved to accomplish a task. Basically, it’s just human nature.
For example, people frequently reuse or recycle their passwords across multiple accounts. But this can lead to issues considering that Verizon’s 2020 Data Breach Incident Report (DBIR) shares that 37% of data breaches resulted from the use of stolen or compromised credentials.
Scott says that the callous mindset toward access restrictions can often be found at all levels of organizations:
“People from the C-suite to the grass roots might not take access controls seriously. It’s easy to share passwords with a coworker who needs access to your files. It’s easy for system admins to just grant access to everyone for everything, especially at small organizations. I’ve heard many top managers complain about all the security getting in the way of getting work done.”
Flexibility & Consistency Are Key to Monitoring & Managing Access Controls
Traditionally, access control processes were static. But for modern access controls to be effective, they need to be flexible in their capabilities and consistently supported.
Administrators need to continually monitor them to identify any potential security holes or non-compliance concerns, too. For example, there should be a procedure in place for terminating access for employees who leave your organization. Whether they quit, get laid off, or get fired, you don’t want someone to have access to things they shouldn’t.
Final Thoughts on Access Control Systems, Lists, and Models
I hope that this article has given you a better idea of what access controls are and the roles they play in information security. There’s a lot to know when it comes to access controls, and our intention with this piece was to provide you with a greater overall understanding of access control systems and how they work without getting too technical.
Access controls can be physical, technical, or administrative in nature. But what makes information access control systems especially valuable for businesses is that they give you greater control over your data. Just how you go about doing so depends on the method you choose:
- DACS are pretty laid back and give greater control to file owners. It’s the least restrictive method on the list of access control models.
- MACs, on the other hand, leave those controls up to a central authority within your organization.
- RBACs enable you to grant or restrict access to individual users or groups based on the roles or functions they fill.
- ABACs rely on assigned attributes to determine someone’s access level and what they can do with it.
Be sure to share your insights regarding effective access control systems and implementations in the comments below.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown