All posts in
Beyond Hashed Out
Gartner reports taking “twice as many calls” about PKI and certificate lifecycle management (CLM) than multi-factor authentication (MFA)-related calls in 2023. Why is interest in PKI growing and why are…
Explore the public key infrastructure (PKI)-related lessons gleaned from public and private entities that got publicity for all the wrong reasons… PKI is a critical part of most IT…
Although deepfake technologies are still in their infancy, falling for scams utilizing them can cost you millions. The good news is that there are steps you can take to make…
It seems like every time you turn around, new U.S. data privacy laws are popping up. The United States is an expansive country made up of 50 individual governing states,…
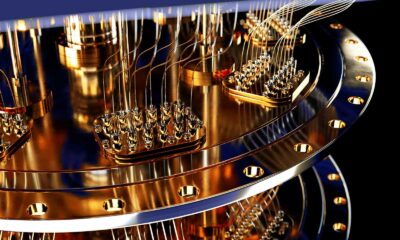
Error correction is an issue that’s been plaguing quantum computing research for decades. Now, researchers from Harvard, MIT, and other leading organizations say they’ve found a way to improve error…
Consumers increasingly find themselves facing fake media and misinformation campaigns. Having a way to prove your content and communications are authentic should be one of your business’s top priorities. Every…
From how specific cryptographic algorithms work to how countries are working to face down looming quantum threats, the November 2023 conference covered many topics. We’ve got 9 key insights and…
The results of generative AI can be seen in the media you consume online and the information you rely on to do your job. But generative artificial intelligence doesn’t come…
Starting early next year, new digital identity validation and spam-prevention requirements for bulk email senders will kick into effect. Are you ready? Does your organization send out emails to subscribers,…
If you’ve been waiting to put quantum-resistant encryption to work to protect your organization’s infrastructure and data, then your wait is over. Chrome rolled out a quantum hybrid key agreement…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)







 (2 votes, average: 3.50 out of 5, rated)
(2 votes, average: 3.50 out of 5, rated)







5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown