The Rise of Zero Trust: Threats Are No Longer Perimeter-Only Concerns
The zero-trust strategy approaches security from the mindset that no one — not even your internal network users — can or should be trusted automatically. Here’s why zero trust security is picking up traction with organizations and governments globally…
… It’s not paranoia when someone really is out to get you. And if you’re an organization or business, you can virtually guarantee that someone, somewhere has you in their crosshairs. Verizon reports 82% of data breaches involve the “human element” — including everything from phishing and social attacks to general errors and misuse — so, it’s clear why all organizations need to change how they approach cyber security.
This is why the U.S. Department of Defense published information regarding plans to shift its network to a “zero trust architecture” by 2027. In its Zero Trust Strategy and Roadmap document, the federal defense agency shared its goals about what it aims to achieve and what its vision is for the future: implementing stronger defenses against cyber attacks via a dynamic and adaptive approach (zero trust).
This move toward zero trust security has been picking up traction with businesses and other organizations globally over the past several years. It contrasts the traditional notion that cyber security efforts should focus on external threats and hardening your perimeter defenses to protect against threats outside your network. Imagine the cyber security incidents (and resulting data breaches) that could have been avoided if the targeted organizations had implemented zero trust:
But what is zero trust and why is it something that can benefit organizations and businesses across all sectors (not just the DoD)?
Let’s hash it out.
What Is Zero Trust Security? The Strategy of Trusting Nothing & Verifying Everything
Zero trust is an organization’s answer to the childhood warning “stranger danger!” It’s both a framework and strategy that operates with the understanding that no one — not you, your devices, your apps, or even your CEO — can (or should) be trusted automatically. And it’s nothing personal — it’s not because your IT admin doesn’t like you. This real-time security strategy approaches cyber security from the perspective that everyone inside and outside your network is a potential threat.
Zero trust touches everything relating to your IT ecosystem and everything that goes on in the background. It promotes the idea that there are no traditional network boundaries; your assets and resources can be anywhere — on prem, in the cloud, or a mix of both. This makes it a versatile approach to hardening your cyber defenses. Therefore, everyone with access to your organization’s network or IT resources must have their identities continuously vetted throughout their connections.
Regardless of where your assets are that you want to secure, there are three guiding principles at the heart of zero trust security:
1. Never Trust, Always Verify
What we mean by this is that users need to authenticate in a verifiable name. Simply taking them at their word just won’t cut it. This entails using setting default-deny policies, setting least access privileges, and using public key infrastructure (PKI) based tools (such as client authentication certificates).
Whenever someone logs in or tries to access something in a zero trust environment, they’ll need to continually authenticate (prove their identity) throughout the session. Why? Because session IDs can be hijacked and someone unintended can take over a connection. By implementing comprehensive identity and access management, you’re reducing the potential harm an account compromise could cause.
2. Assume a Hostile Environment or That a Breach Has Occurred
With zero trust, you assume the worst (someone bad is already in your network) but hope for the best. You’ll want to assume that every network connection and access request is from an attacker. This involves monitoring all users, devices, connections, requests, and configuration changes continuously to ensure that no one is accessing something they shouldn’t.
3. Verify Explicitly
Verify that users are accessing things securely. Have security mechanisms in place to ensure they’re doing that. This includes enforcing policies dynamically via the policy engine and policy administrator (PE determines whether access is approved or denied and the PA executes that decision). And, as always, monitor and log all access requests and traffic.
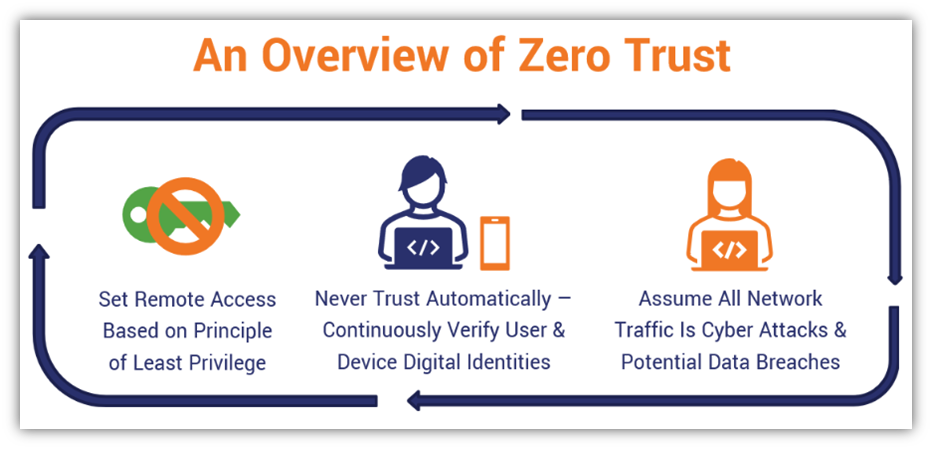
There’s No One-Size-Fits-All Approach to Zero Trust
There are different approaches to zero trust put out by different organizations and different standards as well. Probably the most commonly known zero trust framework is the National Institute of Standards and Technology’s (NIST) special publication: NIST SP 800-207 — Zero Trust Architecture. This document laid the groundwork for other frameworks from agencies such as the U.S. Department of Defense and the National Security Agency (NSA).
These other frameworks have a lot to offer information of information and applications. (The DoD guidelines, in particular, offer more breadth and depth than the NSA’s.) And we’ll touch on key concepts from these resources throughout the article.
Why Zero Trust Matters: Looking Beyond the Surface to Secure Your Digital Assets
We live in a time when you can no longer take things at face value. You can’t simply assume that someone is who they claim to be simply because they type in a username and password; all it takes is a small third-party data breach for someone’s password to become known to the dark web. And if that person uses that same password to secure multiple accounts, then attackers can use it to brute force their way into their accounts.
This is why it’s crucial that we look much deeper and look at other verifiable and contextual information. This approach helps us determine whether someone requesting access to sensitive resources is authentic and has the authorization to access those assets.
Discussing this topic of zero trust always makes me think of scenes from the Mission: Impossible movie franchise. In several movies, Tom Cruise’s character, Ethan Hunt, wears masks and contact lenses to impersonate key characters. Sure, on the surface, he looks like each of the people he’s pretending to be. He can even use a voice modulator of some kind to sound like each person he’s impersonating. But just because he looks and sounds like that person doesn’t mean Ethan Hunt (Cruise) really is them.
Now, let’s leave Hollywood behind for a second and imagine if someone who looks and sounds like your boss or CEO walks into your building. You’d likely assume that it’s him or her. That would be pretty hard to fake, right? Heck, if I saw someone walk in who looked and spoke like our CEO, Bill Grueninger, I’d likely assume it’s really him, too. But if I walked up and started tugging on his face to see if it’s a latex mask or is the real deal, I’d likely find myself landing a really uncomfortable meeting with HR.
In a digital environment where users authenticate remotely, though, you need to have a way to verify their identities are legitimate. It makes you wonder what major cyber security incidents and data breaches may well have been avoided if the targeted organizations adopted zero trust policies and processes…
Zero Trust vs Traditional Trust-Based Environments
A zero-trust environment differs from a traditional security approach in that zero trust means you have continuously prove your trustworthiness, whereas a traditional environment means that once you’re inside the network, you’re automatically assumed to be safe.
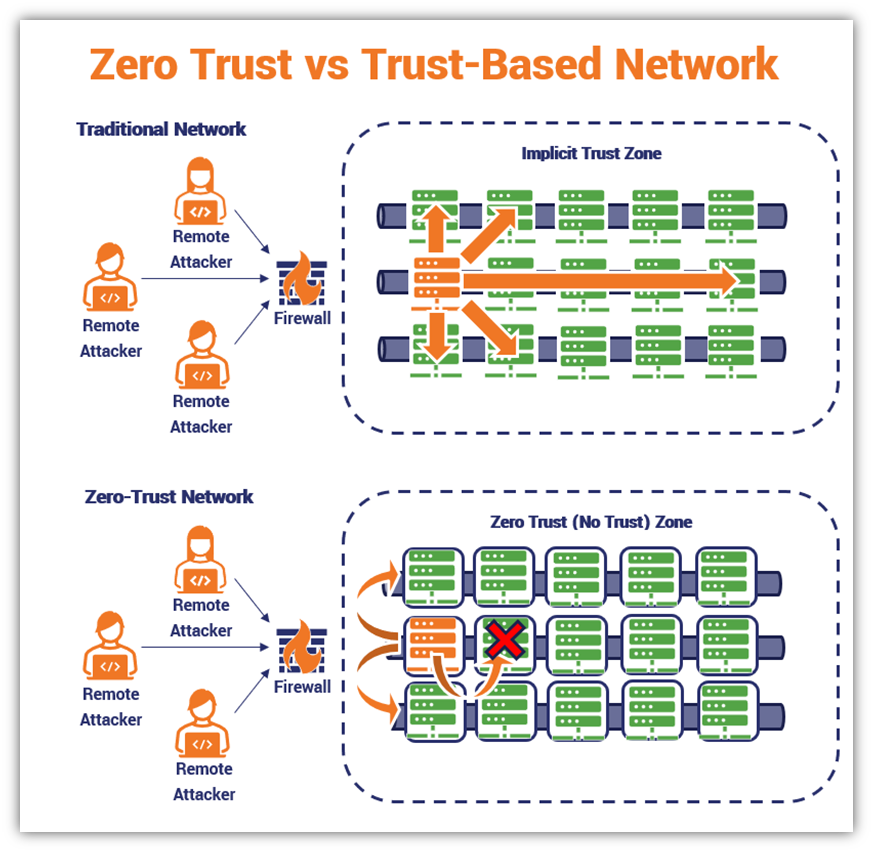
Unfortunately, the traditional model no longer works in a world of credential phishing and session hijacking. You need more robust security and authentication measures in place.
The Seven Pillars of Zero Trust
If you search online, you’ll notice that different organizations approach zero trust in different ways. For the sake of this article, we’ll talk about the seven pillars of zero trust in terms of how the U.S. Department of Defense framework defines them. The seven zero trust pillars we outline below are overarching categories of focus for implementing zero trust. Each pillar involves monitoring and logging but also entails other specific protections.
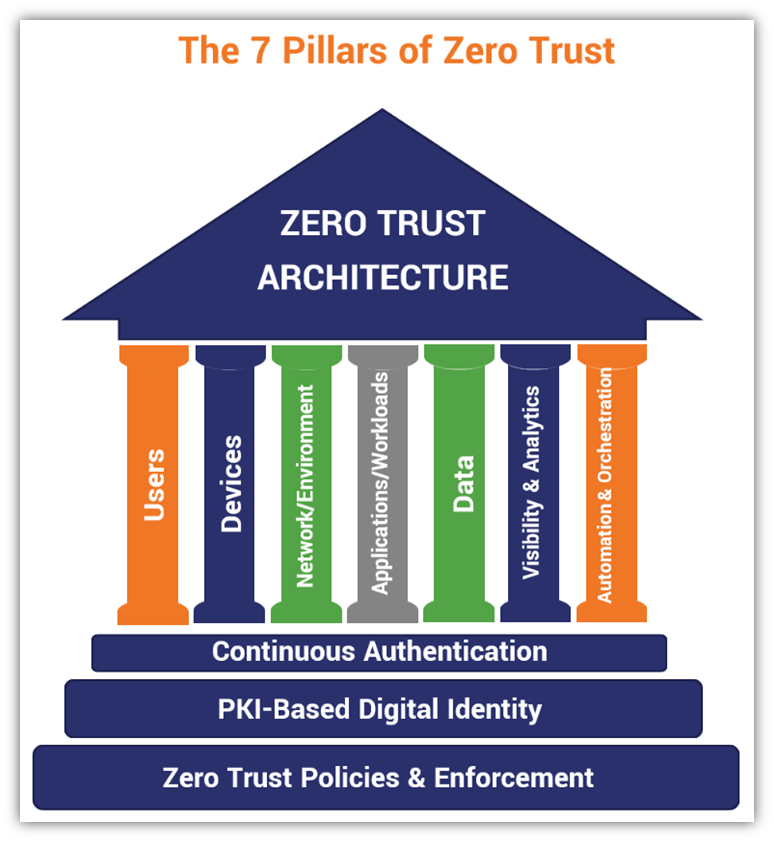
- Users — Controlling access to protected resources by continuously authenticating users using digital identity components (such as client authentication certificates) and verifying users’ access authorizations.
- Devices — Use device digital identity (think TPMs, device certificates, etc.) to authenticate access in real time. Devices also must be patched to mitigate vulnerabilities.
- Network/Environment — Segmentation, isolation, and policy restrictions are three critical components to control access and manage how data moves on your network. This approach helps to restrict access and prevent lateral movement within the network.
- Applications and Workloads — Whether you’re using resources that are on-prem, cloud, or a hybrid approach, the idea here is to secure the application layer.
- Data —Secure your data by developing a comprehensive data management strategy and integrating data security measures such as at-rest and in-transit data encryption. This will help protect your data both while it’s on your servers or moving between two endpoints.
- Visibility and Analytics — Having full visibility of your IT environment is crucial to keeping it secure. You can’t protect assets you don’t know exist, and you can’t stop attackers when you don’t realize something is wrong. You can gain actionable insights to improve your cyber security by analyzing your network’s traffic and user behaviors in real time to identify threats. Just be sure to consider that some traffic may contain sensitive data, so decide the best approach (such as informing users and obtaining their consent ahead of time).
- Automation and Orchestration — Automation is a scalable approach that takes monotonous tasks off your team’s plates, freeing them up to focus on tasks that require critical thought processes. These tools also enable you to quickly sort through all the noise your security tools generate to find valuable data.
Access Controls & Access Management Are Critical to Your Organization’s Cyber Defenses
Zero trust as a cyber security approach has gained strong support over the last several years. This is partly because of the use of identity-based authentication and user authorization that’s required. In a nutshell, here’s a quick overview of how access controls and management play together to boost your organization’s cyber security:
- Access controls are the rules, settings, and tools you use to control access to sensitive data and resources.
- Access management is the process of setting up and managing who has authorization to access specific resources and systems.
Of course, neither of these things is foolproof and requires another security layer in the form of authentication. User and device authentication are all about ensuring that only entities (i.e., those whose digital identities have been verified and their authorizations confirmed) can access your secure digital assets.
Continuous Authentication Is Integral to Zero Trust
A key element of the zero trust approach is a concept known as continuous authentication. The idea behind continuous authentication is that all network users, including your employees, must not only prove their identities when they first log in but also continuously prove their identities throughout their sessions.
Why is this necessary? Because session IDs can be set to last for extended periods — anywhere from a few hours to even a few weeks. This means that if a cybercriminal steals an authenticated user’s access tokens (session IDs and cookies), they can pretend to be them and access whatever protected resources their account has the authorization to access.
While some platforms have mechanisms to prevent authentication from happening, this may not always be the case. And it’s true that you can set timeout limits to take effect after certain periods, but if you don’t bother setting up these security limits, then it’s inevitable that at least one bad guy might slip through the cracks.
Continuous Authentication Requires Verifiable Digital Identity
For zero trust security to work, you need to have a way to prove that you’re really you and aren’t an imposter who’s trying to fraudulently access sensitive data, systems, and other resources. The way to achieve this level of reliable and verifiable digital identity is through the use of public key infrastructure (PKI) and digital certificates. (We’ve talked a lot about these concepts before, but we’ll talk more about them again a little later in the article.)
Digital certificates are small data files that pack massive punches. They contain verified identifying information about you and/or your organization that a trusted authority (certificate authority) attests is authentic.
You can think of digital certificates in much the same way as an official passport: that little government-issued booklet contains verified information about you that proves your identity to people you’ve never met. This way, you can show your passport to airport security and other authorities (i.e., people who don’t know you) to prove you’re really you. (Sorry, there were a lot of “yous” in that paragraph.)
What do digital certificates and continuous authentication have to do with one another? Everything, really.
- In a zero-trust environment, there are no implicitly or explicitly trusted users, devices, or zones within your network or IT environment. The digital identities of everything and everyone must be authenticated continuously using verifiable methods — period. And digital certificates are a means of doing precisely that.
- Digital certificates enable trusted third parties to attest to your digital identity’s authenticity. It’s kind of the digital equivalent of how the U.S. Department of State attests to an American’s identity each time it issues a passport.
Public Key Infrastructure and Zero Trust = The Perfect Combination
In a zero-trust environment, each employee, device, or other network user must have a way to mutually authenticate in a way that’s verifiable. How? By using a security mechanism that the security of the internet itself is built upon: public key infrastructure (PKI).
Public key infrastructure is the combination of rules, processes and technologies that enable two parties to communicate securely. Without PKI, if you were trying to connect to your bank’s website, it would be risky: you wouldn’t have a way to securely send your data because you wouldn’t know for sure who was on the other end of the connection. Even if the connection is encrypted, if you’re connecting to a cybercriminal, they’d have the decryption key to unscramble your data and read it.
Remember the DoD Zero Trust initiative that we mentioned earlier? Its DoD Zero Trust Architecture document shares one of the most beautiful lines we could hope to read in a government resource as an explanation: “The use of mutual authentication of users with PKI-based client authentication or mutual authentication certificates to web applications has long been the effective standard.”
Darned right, it is. And that’s because PKI isn’t the new kid on the block; it’s been around the block many times since its inception in the mid-1980s. PKI has served as the trusted foundation of internet security since that time because it’s what enables secure remote communications and data transmissions that, otherwise, would be impossible.
Why Zero Trust Is Necessary to Improve Cyber Defenses
When it comes to remote user authentication and access, looking beneath the surface is a necessity. You can’t simply see that someone logs in using a basic username-password combination and assume it’s the legitimate account owner; you need an additional layer of verification that continually proves it’s the authentic user. Adopting a zero-trust approach can help in several ways:
Prevents Compromised Credentials and Access Tokens From Being Exploited
Implementing zero trust is a way to prevent cybercriminals from taking advantage of vulnerable access tokens (session cookies, IDs, or weak credentials) to gain access to sensitive resources while pretending to be legitimate network users. Yup, that’s right — if even one of your employees who has privileged access uses a weak password for their account, it could be game over for your business. All it takes is one bad enough “oops” to cause you to face immense penalties, lawsuits, or even have to close your doors forever.
Protects Your Brand and Nurtures Customers’ Trust
Incorporating zero trust into your cybersecurity strategy is also a great way to help protect your organization’s reputation, brand, and bottom line. Okta’s 2021 State of Digital Trust report shows that 75% of American consumers say they likely won’t do business with brands they don’t trust (i.e., after a data breach or misuse of data). Almost half, a whopping 47%, say they’d take things a step further and would permanently stop using a company’s services for the same reasons.
Imagine what would happen if an unauthorized user gained access to your most sensitive data. This could be your intellectual property (IP), customers’ financial data, or even employees’ records. Regardless of which type of data they get their slimy paws on, exposing sensitive data would spell disaster for your organization.
Helps Mitigate Other Issues
In addition to the no-brainer reason of you don’t want your information accessed by unauthorized individuals, there are also other concerns that adopting zero trust could help you avoid
- Non-compliance issues with regard to industry standards,
- Data breaches that can lead to hefty fines, penalties, and lawsuits,
- Your reputation taking a big hit, and
- Customers not trusting you or your services.
What It Looks Like When You Don’t Adopt Zero Trust and Things Go Wrong
We’ve seen this type of scenario happen time and again in various data breaches. Here’s a quick example of what could happen without a continuous authentication mechanism in place:
- An attacker phishes one of your company’s key employees, tricking or manipulating them into coughing up their privileged access credentials or session ID. This may not be hard considering that IBM’s X-Force Threat Intelligence reports phishing as the attack vector in two in five incidents their team responded to.
- The attacker uses their login info or session ID to access secure resources using that employee’s account. Once in, they’re able to move laterally across the company’s network — accessing applications, databases, and other resources that the employee’s compromised account has access to — pillaging as they go.
- Once they find interesting and valuable data, the attacker exfiltrates whatever data they can to an external server they control before installing malware onto your systems. It’s a devastating one-two punch you never saw coming that can bring your company to its knees.
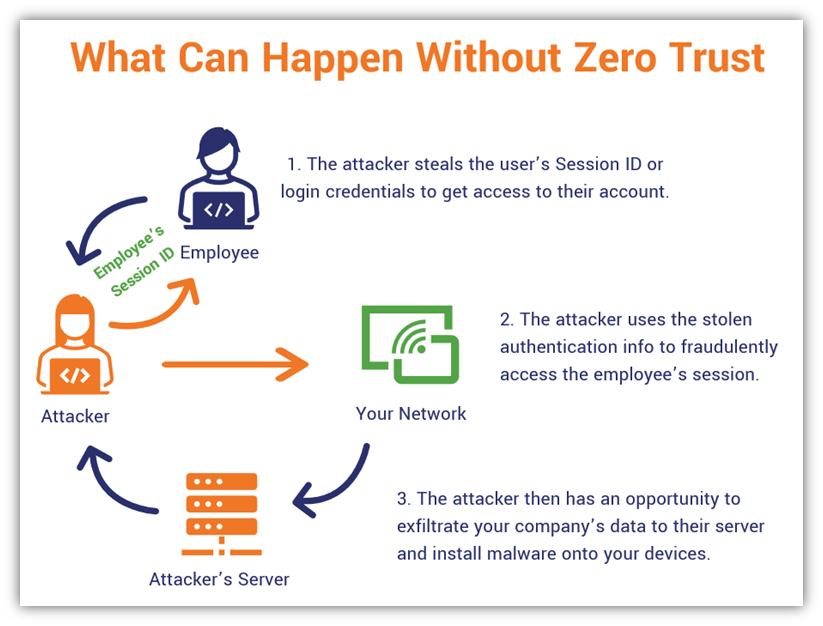
Because your organization didn’t require continuous authentication (i.e., didn’t implement zero trust) or have restricted policies in place that are enforced, your IT security admin or cyber security team doesn’t realize that anything is amiss until it’s too late. Now, you’re not only dealing with a data breach, you’re also scrambling to deal with the ransomware situation as well.
But wouldn’t a firewall be able to tip off your cyber defenders that something’s wrong? Sure, event logs will show a significant increase in traffic. But since the traffic appears to be legitimate (because the attacker is using the employee’s legitimate credentials, may be using a proxy IP address to disguise their true location, and you’re not analyzing device identity attributes or behaviors), they may not initially realize that it’s actually an external attacker and not your legitimate employee accessing your systems until the damage has already been done.
Oh boy. We hope you have business continuity, disaster response and disaster recovery plans in place, and that those plans are not only current but that your employees know what their roles and responsibilities are! Cyber resilience is crucial; but without the right security mechanisms, strategies and plans in place, you may not like the outcome.
Insider Threats in Action: A Real-World Look at the Elliott Greenleaf Breach (2021)
Attackers are becoming increasingly sophisticated and potential attack surfaces are expanding. As such, our defense of these systems must become more robust and dynamic. To go beyond discussing zero trust from a largely conceptual standpoint, let’s dive deeper and explore the damage caused to a real-world organization by bad actors within its trusted internal network.
What Happened
In January 2021, the Pennsylvania law firm Elliott Greenleaf was the victim of an insider attack and sustained catastrophic financial losses, according to WestLaw.com. According to multiple reports, four attorneys and a paralegal secretly downloaded a slew of invaluable sensitive data, including confidential files, trade secrets, and client lists. Their actions as insider threats resulted in irreparable damages to their former employer, which has since filed a lawsuit against the four attorneys and the paralegal.
The National Institute of Standards and Technology (NIST) defines insider threats as:
“The threat that an insider will use her/his authorized access, wittingly or unwittingly, to do harm to the security of organizational operations and assets, individuals, other organizations, and the Nation. This threat can include damage through espionage, terrorism, unauthorized disclosure of national security information, or through the loss or degradation of organizational resources or capabilities.”
As it turns out, these legal professionals, who were trusted to operate internal systems (seemingly with little to no oversight), were wolves in sheep’s clothing. They were joining a rival law firm in Delaware (Armstrong Teasdale) and, it appears, wanted to take Elliott Greenleaf’s info with them.
Unfortunately, this isn’t an uncommon scenario; Code42’s research shows that there’s a one in three chance an organization will lose intellectual property when one of its employees quits.
How It Happened
Let’s quickly break down what occurred that enabled these insiders to wreak havoc based on information shared by Digital Guardian and WestLaw:
- The attorneys had immense access to files and data. The attackers had access to read, steal, and destroy highly sensitive information. For example, they reportedly shredded 288 lbs of physical documents. (That’s approximately 28,800 pieces of paper if you’re using standard copy paper). In some cases, they enlisted the help of the paralegal to get certain data for them.
- They accessed systems that appear to lack monitoring and/or alerts. To steal data, they were able to use one or more personal USB devices and had cloud-based file-sharing apps installed on their company devices.
- They were able to send and delete emails containing sensitive information without detection. As such, they could send additional sensitive information to personal email accounts — and subsequently “double-delete” the messages in an attempt to cover their trails. Granted, the company says it’s able to access the delete emails via their data backup systems, but by that time, the damage had already been done.
The Big Takeaway From the Elliott Greenleaf Law Firm Situation
Unfortunately, the Elliott Greenleaf law firmed learned a valuable lesson the hard way: This catastrophe likely could have been prevented (or identifier earlier) if Elliott Greenleaf had adopted a zero trust approach. With zero trust:
- the employees’ access should have been continuously verified across all systems,
- their reach (i.e., their permissions and breadth of access) should have been restricted to only what they needed to do their jobs (think policy of least privilege), and
- their access to resources and use of USB devices should have been disabled — or, at the very least, monitored, logged, and analyzed.
It’s our hope that you that you keep this story in mind and recognize that the threat from within your organization can be as, if not more, dangerous than outside attackers. Although the damage caused by this insider breach is irreversible, future attacks of this nature can be prevented through by adopting a zero trust posture.
How to Adopt a Zero Trust Strategy
Now, we’re not going to get into the nitty-gritty of how to actually implement zero trust. There’s far too much information that would need to be covered that it would, basically, entail creating a whole other article. However, NIST (SP 800-207) and the DoD (DoD Zero Trust Reference Architecture) provide some guidance for federal agencies on how to build zero trust architectures (from the ground up or migrate their systems to zero trust over time). Some of this information may be useful to your organization as well.
Adopting a Zero Trust Strategy Is One of the Best Ways to Secure Your Organization
Zero trust isn’t totally new, and it certainly isn’t going anywhere anytime soon. It’s gaining traction over time. Okta reports that 55% of surveyed organizations globally indicate that they have a zero trust initiative in place. A whopping 85% of global 2000 (G2000) companies said they’d allocated “moderate” or “significant” year-over-year increases in budgets to fund these initiatives.
Of course, there is still room for improvement. Research from Forrester and Illumio shows that only 6% of organizations indicate that they have fully deployed zero trust within their IT environments. But, hey, it’s a start, right?
One of the key attributes of zero trust is limiting who has access to what. This involves setting and enforcing policies, using verifiable digital identity, following the least privilege principle, monitoring all access attempts and behaviors, etc. By limiting a user’s reach to only the resources and systems they need to do their jobs, you reduce your attack surface. So, rather than having cybercriminals have access to everything, they can only access the systems and data that the user is authorized to access.
In a zero-trust environment, a bad guy will first have to go through a series of verification checks to ensure they’re the authentic user. If they fail that, then they won’t get access to anything. If they succeed, then at least their reach will be restricted to the privileges you’ve assigned the compromised user’s profile. And since you’re keeping an eye on everything and are logging everything for analysis, it’ll help you better mitigate these issues in the future.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown