The Rise of Cyber Resilience
Smart organizations practice cyber resilience – not just cybersecurity.
Cyber resilience measures how well your organization can continue operating in the event of a cyber attack – how well you can take a punch. As time’s progressed and cybercrime has become more rampant, it’s gotten harder not to concede that cyber attacks are no longer a matter of “if” – but rather, “when.”
And that’s given rise to cyber resilience, which is itself both an offshoot of, and a more holistic approach to, cybersecurity. According to a 2017 Accenture study, 72% of CISOs feel that it’s “not possible” to appear “strong, prepared and competent” if security is breached.
That’s not true though.
Last year, at the end of February 2018, the developer platform GitHub got walloped by a massive 1.35 terabit per second DDoS attack. Just two years prior, the internet all across North America was brought to its knees by a 1.2 tbps attack against internet the infrastructure organization, Dyn. Despite being more powerful, the GitHub attack failed to achieve anything close to comparable results. Instead, GitHub struggled with intermittent outages for about ten minutes before calling in Akamai Prolexic, the company responsible for its DDoS protection.
After eight minutes of scrubbing traffic, the attack dropped off and business continued as usual.
While there’s quite a bit you can unpack from a success story like that, what we’re going to focus on today is the cyber resilience side of the discussion. Specifically, why cyber resilience is so important and what your organization needs to consider as it builds its own plans. We’ll also talk about how automation can help to improve detection and containment of cyber incidents by up to 25%.
Let’s hash it out.
What Is Cyber Resilience?
Let’s start with the most basic question, what exactly is cyber resilience? Cyber resilience, for lack of a more eloquent definition, is really just the measure of how well your organization can survive, and keep operating, in the face of a cyber attack or incident. That attack or incident could be anything, the obvious example would be a massive DDoS attack like we just discussed.
But at the same time, when dozens of federal websites broke and became inaccessible after their digital certificates expired during the recent US government shutdown, that also betrayed a lack of cyber resilience.
The US National Institute for Standards in Technology (NIST) defines cyber resilience:
Cyber resiliency is defined… as “the ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on systems that include cyber resources.” This definition can be applied to a system; to a mechanism, component, or system element; to a shared service, common infrastructure, or system-of-systems identified with a mission or business function; to an organization; to a critical infrastructure sector or a region; to a system-of-systems in a critical infrastructure sector or sub- sector; and to the Nation. Cyber resiliency is emerging as a key element in any effective strategy for mission assurance, business assurance, or operational resilience.
Or if you’re looking for something a little more succinct, the Australian Securities & Investments Commissions puts it this way:
“Cyber resilience is the ability to prepare for, respond to and recover from a cyber attack. Resilience is more than just preventing or responding to an attack—it also takes into account the ability to operate during, and to adapt and recover, from such an event.”
Obviously, different organizations and standards bodies have different ways of defining cyber resilience, so it should come as no surprise at all that they also vary on how it should be approached.
NIST breaks it down into four high-level goals, Symantec talks about five pillars [Editor’s note: This Synmantec resource has since been deleted], US-CERT (CISA) has a Cyber Resilience Review that examines 10 domains. One thing they all agree on: cyber resilience involves a holistic strategy that transcends just cybersecurity concerns.
Cyber resilience can be the difference between life and death for a company. Especially small and medium-sized businesses (SMBs, or SMEs if you’re European). According to an IBM/Ponemon study, 77% of organizations don’t even have an incident response plan, which is likely a fatal mistake. The National Cyber Security Alliance found that 60% of SMBs are out of business within six months of being hit by a cyber-attack. And 66% of respondents to a VIPRE Security survey said their SMB would shut down if hit by a data breach.

So, why aren’t more organizations practicing cyber resilience?
Cyber Resilience vs. Cybersecurity
Let’s start with the obvious question: what’s the difference between cyber resilience and cybersecurity? And there’s certainly a lot of overlap there, but I’d posit the biggest difference comes down to outlook.

Cybersecurity focuses on preventing cyber attacks and incidents. It’s proactive and somewhat idealistic, seeking to completely prevent these things from ever even happening in the first place. In its own way, cyber resilience is much more cynical. It’s built around the premise that these kinds of incidents are bound to happen, so while it would be ideal to prevent them you also need to take time to plan how you’ll respond and keep your organization running when one succeeds.
Therein lies a world of difference.
But that’s not the only thing that differentiates the two, here’s a quick breakdown:
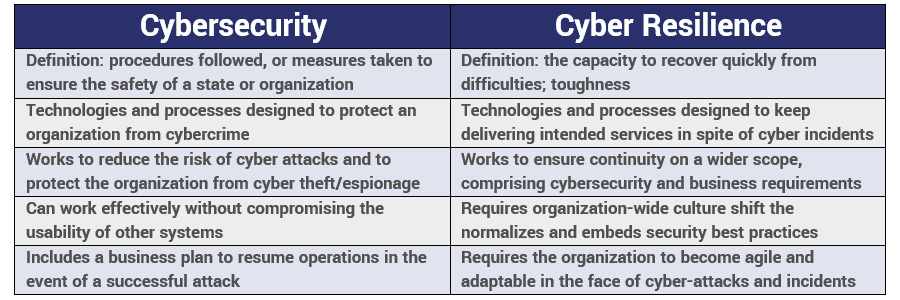
I’ve used the word holistic a few times already, but that’s because it’s incredibly apropos. Cybersecurity can be siloed off if you’re not careful. It’s easy to delegate all of the security considerations to a single employee or team and just let them worry about it.
In fact, I’ve been present at a company where that happened. A single IT admin was responsible for all of the cybersecurity for a $40-million business. The site got knocked offline, nobody had any idea why. By the time it was figured out the IT Manager had roped the company’s only programmer into working through the weekend, well into Monday morning. They both got chewed out by ownership. This is far too commonplace.
When that happens, you’re practicing cybersecurity (barely) instead of cyber resilience. A resilient organization understands that there needs to be communication between all teams as it relates to security. All of your employees need to have a rudimentary knowledge of cybersecurity best practices. And most of all, everyone in your organization needs to treat the threat of a major cyber attack or incident like an eventuality – and know what role they’ll need to play in keeping things running when it finally happens.
Cybersecurity is about having the technical safeguards and organizational processes in place, then hoping it’s enough. Cyber resilience is understanding that at some point all of the cybersecurity in the world won’t be enough – so, what do you do then?
Cyber Resilience Statistics: What are other Organizations doing?
Let’s start by taking a look at what steps various organizations are taking towards cyber resilience. As we cited earlier, IBM and the Ponemon Institute just released their fourth annual report on cyber resilience.
And fortunately, it does seem like many organizations are beginning to realize the importance of staffing specialized security personnel as opposed to just leaving it up to IT. More than three out of five organizations have identified hiring skilled professionals as a top priority, but other tactics have seen less adoption. Notably missing, and we’ll get to it specifically in a moment, is buy-in from the C-Suite.
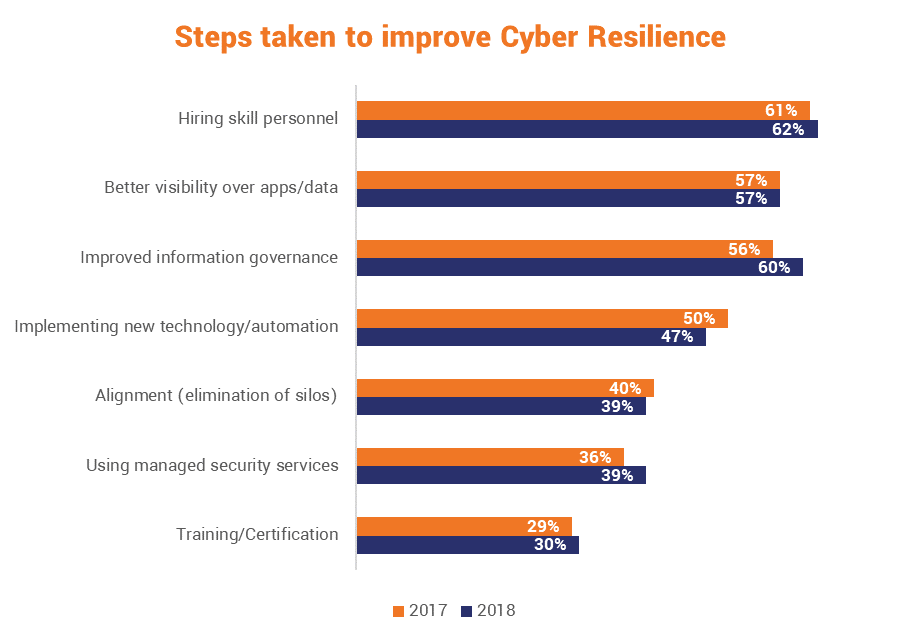
Again though, bringing up the back is C-Suite buy-in. And given that Cyber Resilience pertains to an entire organization, it’s critical to the resilience of any organization that its leaders are bought in, much less aware.
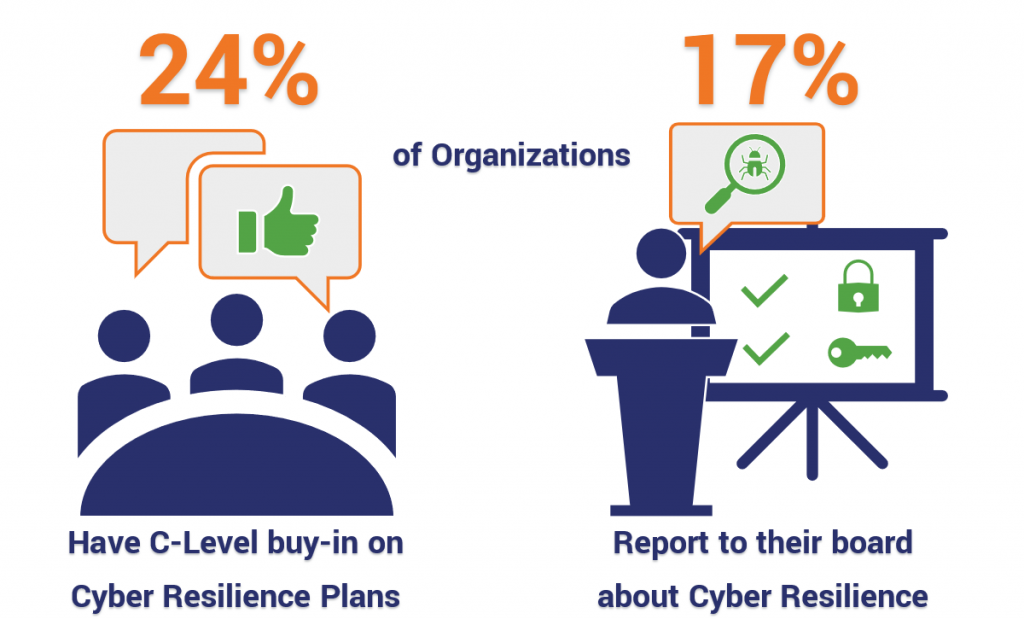
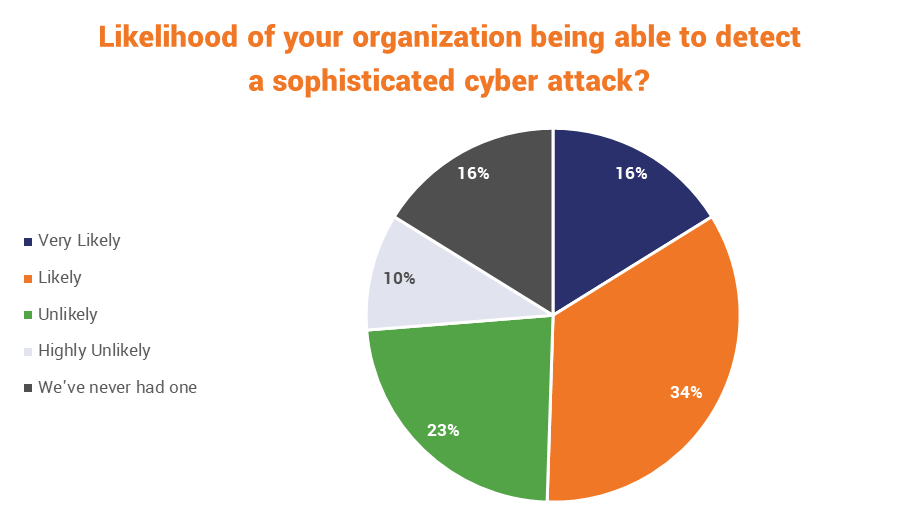
Of course, in some cases that lack of awareness might very well be by design. A surprising number of organizations that responded to an Ernst & Young survey – one-third, 33% – said they were “unlikely” to even be able to detect a sophisticated cyber attack, let alone be able to thwart one. In fact, only half were confident they would be able to spot one at all.
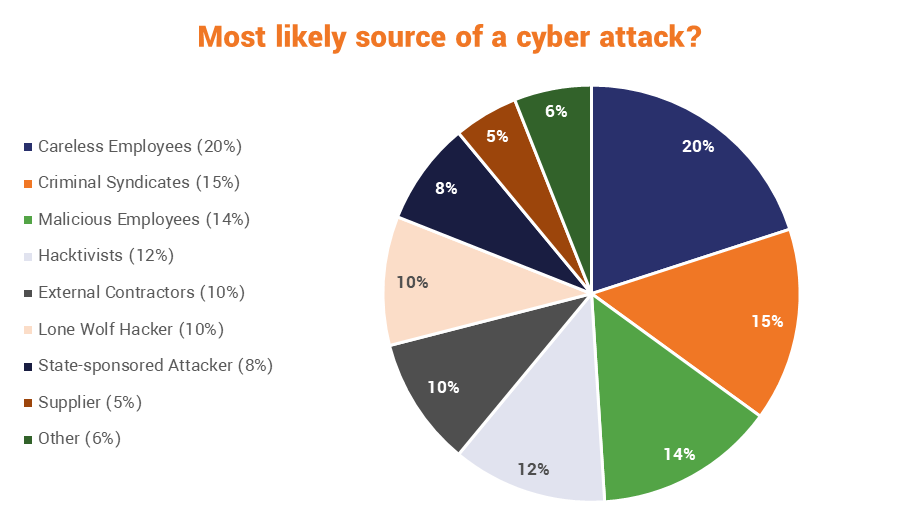
In terms of the threat actors these organizations face, you see the standard fare: hackers, criminals, hacktivists, nation states – but by far the biggest threat these organizations anticipate is their own employees. A little over 1/3 of all respondents listed their own employees as the biggest threat facing their organizations. That actually jives with a lot of the other research we’ve covered.
What’s new is the fact that many of these organizations now view the threat as being almost as much the result of malice as incompetence or carelessness. Hopefully providing that answer gave a few of these organizations pause to think about how they’re treating said employees. Happy employees generally don’t go out of their way to damage their own company’s cybersecurity posture.
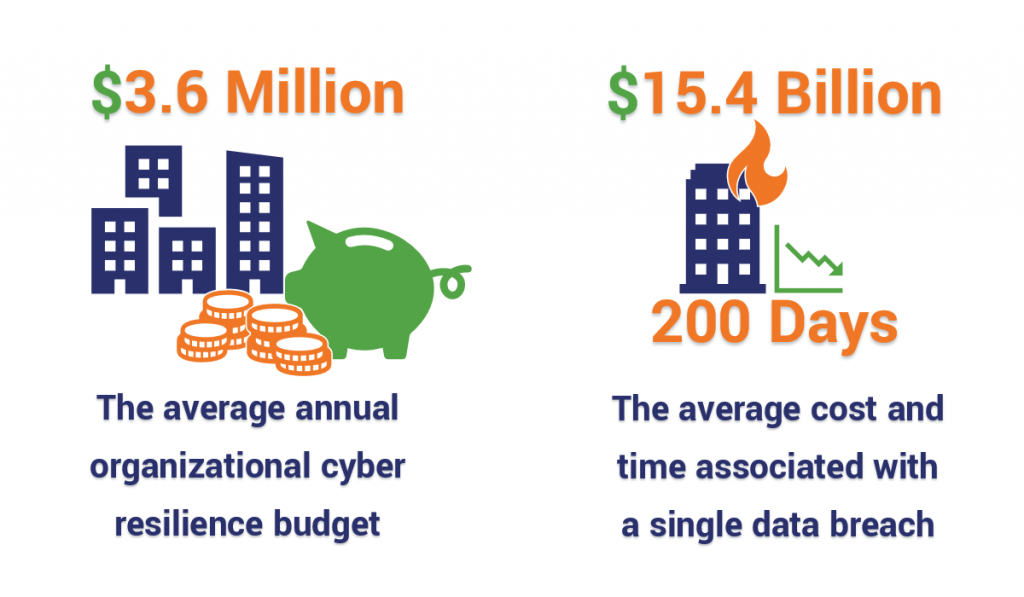
Another interesting element to consider is what makes these organizations jump. Cybersecurity budgets are hard to negotiate. Many organizations view these types of expenses as sunken costs and are loathe to devote more money.
Add the fact that cyber resilience has even less name recognition and it’s not surprising that the average cyber resilience budget is paltry. Per IBM/Ponemon, the average 2019 cybersecurity budget will be just $11.6 million with only about 31% of that, roughly $3.6 million, for Cyber Resilience activities.
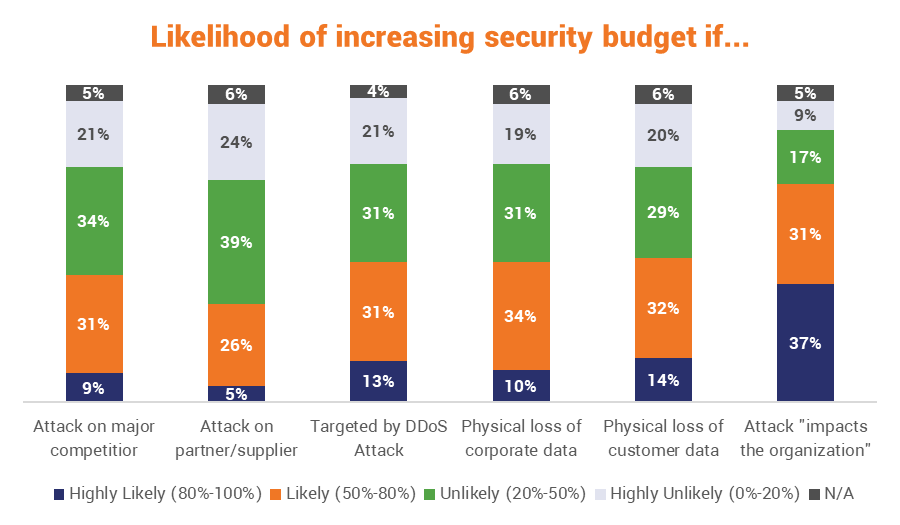
So, what will make most organizations wake up and start investing in resiliency? Getting slapped in the face.
Seriously, hands down, at a nearly 3-to-1 margin over its next closest competitor, discovering a data breach or cyber attack that “resulted in the attackers impacting [their own] organization,” was the biggest motivating factor for organizations that opted to increase their security budgets. On the other end of the spectrum, despite the constant evidence that your partners’ vulnerabilities are your vulnerabilities – only 5% of companies would be highly likely to increase their own budget on account of one of their partners being victimized.
Finally, let’s take a look at what these organizations are using to measure the success of their cyber resilience plans. This should actually be a good spot for us to pivot and start talking about how your own organization can begin working on its own cyber resiliency.
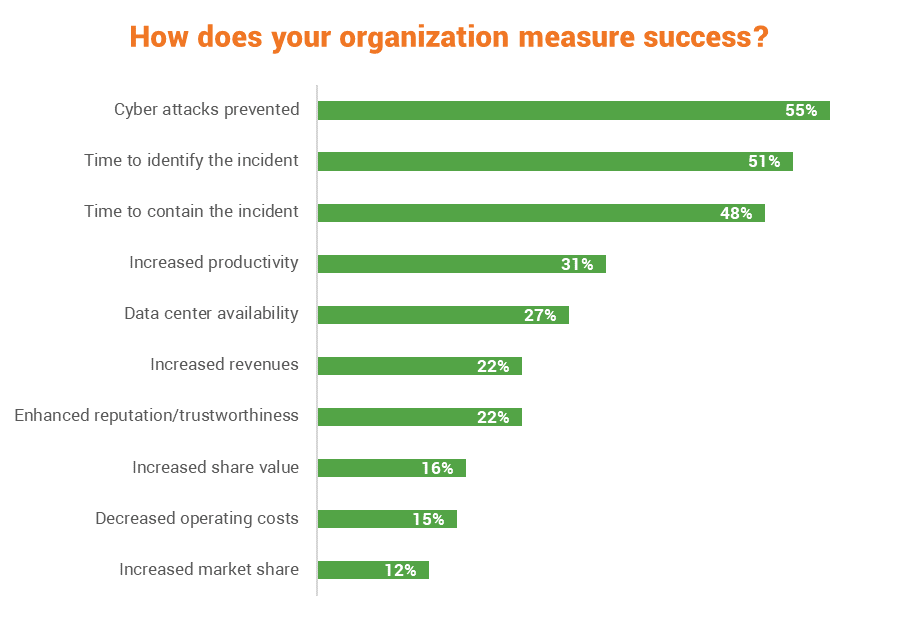
Some of those feel like they’re kind of missing the point, but the way these plans are evaluated is unique to each organization.
How should you evaluate a Cyber Resilience plan?
While there is no agreed upon metric, there is a lot of guidance out there. We tend to favor NIST, so let’s take a look at the four high-level goals proposed in its guidance from Special Publication 800-160.

To sum that up, you need to be actively aware of the threat landscape and constantly preparing for new exploits as they present themselves, and you need to have protocols and processes in place for when those threats do become reality so you can keep business running, or at least restore it as quickly as possible.
These goals are helpful because they’re going to make you start at the desired result, which would be high resiliency, and then work your way backward figuring out the best way to get these goals accomplished.
How to Build a Cyber Resilience Plan
Let’s talk about how you would go about building a cyber resilience plan. We’re going to drill down into each one of these areas with a dedicated article in the future. But for now we’ll keep it high-level and discuss the basics. Starting with what a good cyber resilience plan should even contain:
- Defining of business risks: Don’t make a habit of this, but forget about your industry’s standards for a moment and laser-focus on your specific business. What would be the most dire consequences of a cyber-attack on your business? What could you survive losing? What would put you out of business? This will help you identify the most important information that your business needs to protect.
- Development of a security plan: As we discussed earlier, depending on your perspective cyber resilience is either an offshoot of cybersecurity, or a holistic approach to it. Either way, you can’t neglect the actual technical side of cyber resilience. You still need to be deploying state-of-the-art defenses and maintaining a good security posture. Hopefully, you’ll already have a security plan, or at least part of one, to work with.
- Development of a cyber recovery plan: Your new cyber resilience plan needs to identify what steps you would take in the event of a successful attack. What would you prioritize? What channels would you go through? Who does what? It is important to be as specific as possible in this step.
- Determining a proper testing/review program: Like anything else in life, practice makes perfect. So, put your new cyber resilience plan to the test. And then test it again. Then update it. And then test it again. Your cyber resilience plan (much like your cybersecurity apparatus, in general) should never be at rest. It needs to be constantly evolving to compensate for new threats and updates to best practices and industry regulations.
One last thing, just because you’re prioritizing one area of your business doesn’t mean you can afford to neglect others. On some level everything is interconnected. So, even if it’s not mission critical, you still need to make sure to address it.
Building a Cyber Resilience Plan: Gather the Right Parties to Define Business Risks
The US Department of Homeland Security advises you should, at the very least, be consulting the following parties regarding your cyber resilience plans. So, logistics permitting, locking them all in a room together for a few hours should be an awesome way to get things kickstarted:
- IT Policy & Procedures – CISO
- IT Security Planning & Management – Director of IT
- IT Infrastructure – Network/System Admin
- IT Operations – IT Admin
- Business Operations – Ops Manager
- Business Continuity – BC/DR Manager
- Risk Analysis – Risk Managers
The DHS administers its Cyber Resilience program through the aforementioned ten domains concepts.
“…an organization deploys its assets (people, information, technology, and facilities) in support of specific operational missions or critical services. Applying this principle, the [Cyber Resilience Review] seeks to understand an organization’s capabilities in performing, planning, managing, measuring, and defining operational resilience practices and behaviors through an examination of the following ten domains:”
- Asset Management
- Controls Management
- Configuration and Change Management
- Vulnerability Management
- Incident Management
- Service Continuity Management
- Risk Management
- External Dependency Management
- Training and Awareness
- Situational Awareness
Frankly, that’s a little more granular than we’re going to get today, but I would definitely recommend using the DHS’ resources if you’re looking for a way to assess your own organization’s readiness. Again though, we’re going to stick NIST’s four goals, and – as we’ll get to in a minute – and the aforementioned five pillars for resilience.
Back to the stakeholders locked in our conference room though. Getting everyone on the same page at the outset of the process is critical. We discuss this all the times in terms of certificate and key management. Without clearly defined roles and permissions you’re only inviting trouble. That sort of confusion becomes even worse when it scales.
62% of the organizations polled in the Ponemon/IBM study, including 71% of the high performers stressed that aligning the different departments and stakeholders around a coherent cyber resilience strategy was either “very important” or “essential.”
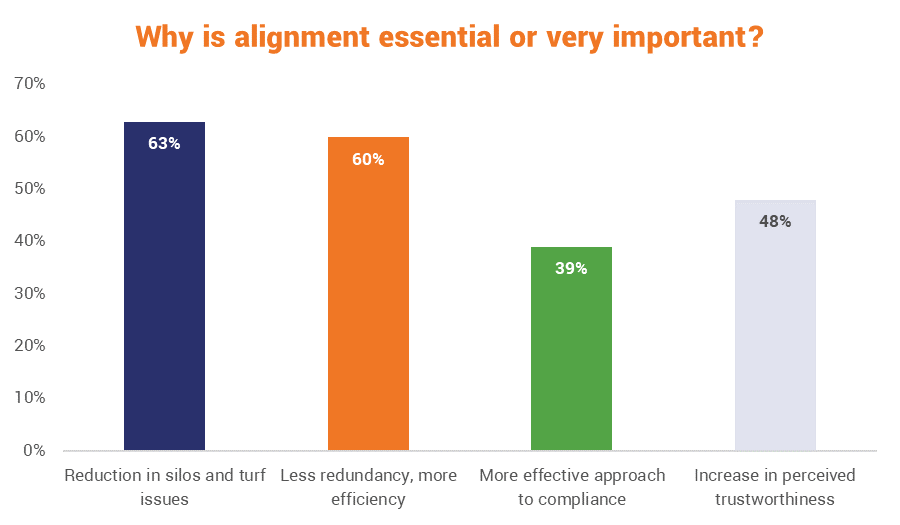
So get everyone together and start defining roles, risks and priorities. If you have already performed a data audit, bring it. If not, schedule one. The same goes for risk assessments. Bring as much information as you have, try to map out everything and achieve visibility over your organization. Be meticulous. Diligent.
We’ve already covered the stakes. So, don’t cut corners. This step is critical – just like cyber resilience, in general.
Before we move on, here are four questions proposed by NIST that you should answer during the planning phases:
- Which cyber resiliency objectives are most important to a given stakeholder?
- To what degree can each cyber resilience objective be achieved?
- How quickly and cost effectively can each objective be achieved?
- With what degree of confidence can each objective be achieved?
Building a Cyber Resilience Plan: Development of a Cybersecurity Plan
If you’re a regular reader here, you know we discuss this topic pretty regularly, so we’ll just give this a cursory glance and then include some additional resources at the end.
Symantec uses a “Five Pillar” approach to building the cybersecurity portion of the resilience approach. We’ve covered what the plan should include, but what should the overall process look like?
The process can be best thought of as a framework with five pillars: prepare/identify, protect, detect, respond, and recover. Using this framework, you can evaluate each pillar of your organization’s cyber security strategy. For example looking at the pillar for prepare/identify, vulnerability assessments can expose weaknesses that exist in an organization’s security posture. By evaluating the risk posed by each weakness and addressing the weaknesses that are most critical, you should be able to improve your preparedness for an attack. With each scheduled cycle of assessments, the security strategy is honed…
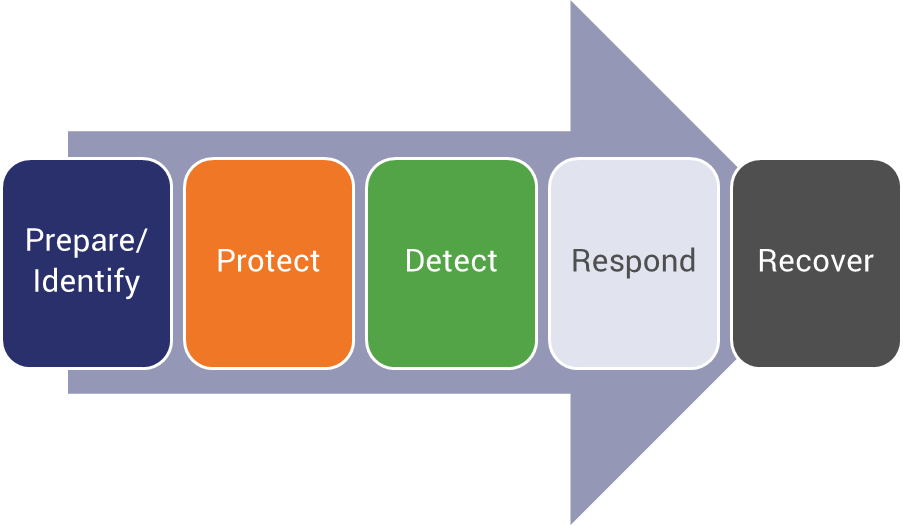
If you’ve already convened your stakeholders for the planning phase, then you should have the first pillar under control. You’ll still need to revisit it from time to time, but the heavy lifting is taken care of.
Protection and detection exist largely side-by-side, meaning they can be handled simultaneously as you decide on and deploy the technical measures you’ll be using in your defense. Additionally, there are a lot of Security-as-a-Service offerings that can help you to outsource protection, detection, response and in some cases even recovery. So, if the actual technical side of things requires more expertise than your organization currently has, then there are other methods for handling this portion of the cyber resilience planning.
Recovery, at this planning stage, only deals with identifying what you will need to accomplish to recover. We’ll get into the actual recovery plan itself in the next section.
The important thing, as we stated in the last section, is that just because you’re building a strategy around the assumption that some of these attacks are going to succeed doesn’t mean that you can afford to skimp on trying to prevent them. You still need to be on the cutting edge of cybersecurity – or at least as close to it as you can get.
Basic components of a cybersecurity plan:
- Firewalls (Application-level, stateful inspection, deep packet inspection)
- Intrusion Detection Systems
- Security Incident and Event Management (SIEM) systems
- Automated security monitoring and alert orchestration systems
- Spam filters/Anti-phishing safeguards
- Access Control
- Identity and Access Management
- Privileged Access Management
- Strong password policies/Two-factor authentication
- Encryption of sensitive data
- At rest
- In transit
- Security software and policies for mobile/IoT devices
This would also be a good time to discuss redundancy – providing multiple protected instances of a critical resource – and segmentation, as they will aid in both defense and recovery.
Additional Cybersecurity Plan Resources:
- How to perform a Data Audit
- How to perform a Risk Assessment
- How to implement adequate Technical Safeguards (GDPR)
- Encryption Best Practices
- Cipher Suites, Algorithms & Negotiating Security Settings
- You should be using ECC
- HTTP Security Headers
- SSL Offloading (Bridging/Termination)
- Common PKI Management mistakes to avoid
- Use SFTP & SCP instead of FTP
- Routing, Subnetting, Masking & Security
- Email Security Best Practices
- End/Network Device Security Best Practices
- Privacy Policy Best Practices
- When to report a Data Breach
Building a Cyber Resilience Plan: Developing a Cyber Recovery Plan
Our newest writer – and please make sure to welcome her – Casey Crane, will be going in-depth on this topic later this week. So keep an eye out. In the meantime, let’s just take a quick glance at what developing a cyber recovery plan actually means.
We just covered cybersecurity plans, a cyber recovery plan is both a component of a cybersecurity plan, as well as a follow-up to it. There will be efforts required to recover from a cyber incident that don’t technically constitute security, but are still mission critical, nonetheless. Many organizations already have a disaster recovery plan, one that includes procedures for restarting business in the event of a natural disaster and/or other physical disasters.
For the sake of cyber resilience, you’re going to need focus on the steps and procedures for maintaining continuity after a cyber disaster.
In the context of your overall cyber resilience plan, recovery is the penultimate step, coming right after detection and response.
Here are the points Casey will be covering later on this week:
- Outline the goals of your disaster/cyber recovery plan
- Inventory all physical and digital assets
- Outline your data backup strategy/plan
- List of all personnel and their cyber recovery responsibilities (if applicable)
- Develop a comprehensive communications plan
- Outline alternative work capabilities and redundancies
- Outline how sensitive data should be handled
- Ensure cyber recovery clauses are included in SLAs
- Keep your information up to date
- Test your plan regularly
Again, this is going to differ from the cybersecurity plan you just reviewed because it deals with how to get key processes and functions back up and running after an attack. So, there are going to be some logistical considerations, like who do you need to be able to reach at an odd hour to restart a key system? Or outlining what the steps for restoring a website to a previous backup would be.
This is also a good place to discuss cyber insurance and whether or not it might be beneficial for your organization to invest in it. Following the news of its 2018 breach, Marriott has so far been able to recover $25- of the $28-million in expenses it’s incurred as a result of its policy.
Regardless, you need to be meticulous, because realizing you forgot something in a moment of crisis is only going to compound the stress and emotion you’re already feeling.
Building a Cyber Resilience Plan: Developing a testing/review program
The final component of a good cyber resilience plan is developing the mechanism you’ll use to test and improve your strategy. This is where employee training, penetration testing and all of the fun white hat hacking activities come in. Basically you’re going to try to break the plans you just put in place.
There’s actually a burgeoning industry that has popped up around organizations’ needs to test and probe their own networks for vulnerabilities. Over the past few years that’s grown from simply looking to exploit digital gaps, to exploiting the human element that so often allows for these attacks to succeed. A good example would be phishing simulations where companies pay an outside security firm to bombard their employees with fake phishing emails for months at a time in an effort to train them on how to ferret out email attacks.
And here’s the thing: they seem to work. A recent study by a group of medical doctors that measured the healthcare industry’s susceptibility to phishing attacks found that with repeated education in the form of simulations, the results showed decided improvement over time.
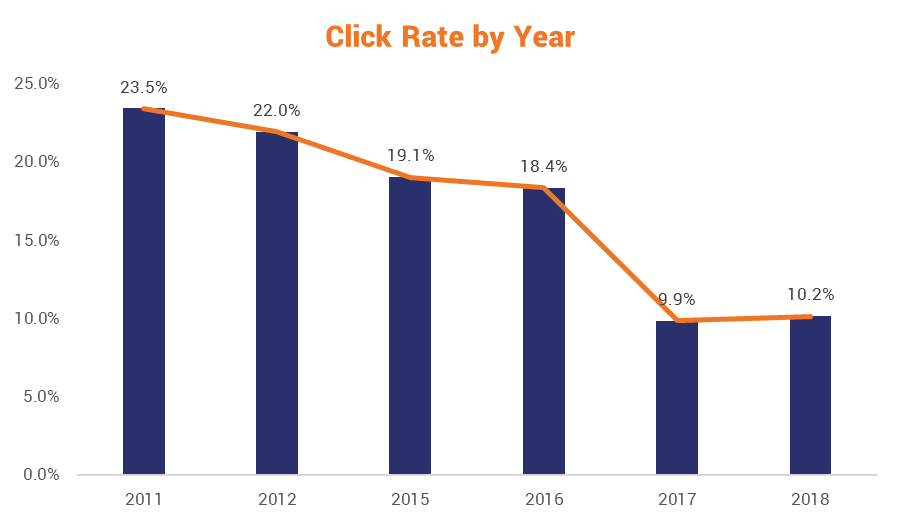
In addition to improvements with each successive campaign:
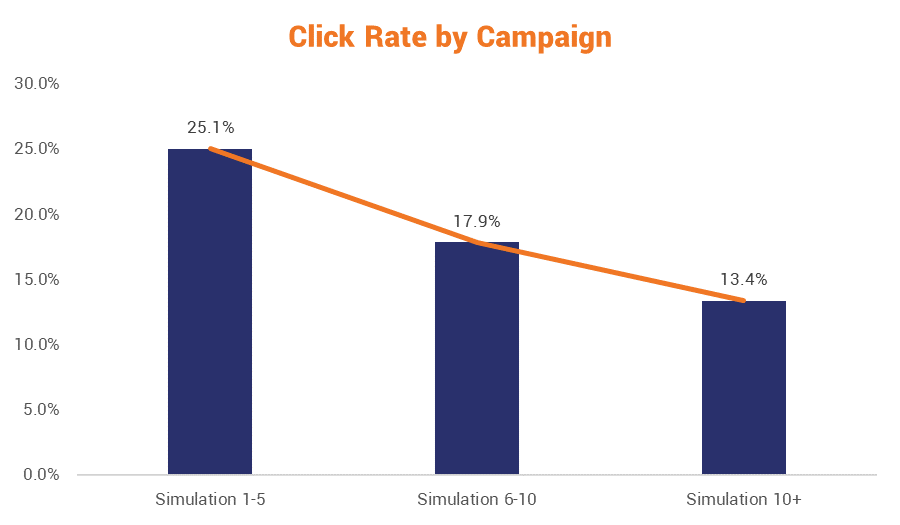
But employee education is only one facet of developing an apparatus to continually test and improve your resilience plans. You may also consider creating a bug bounty program that rewards researchers that can find and document vulnerabilities in your products and network. This is a great way to outsource some of the testing and it has the added benefit of making you look like a company with a very progressive stance on cybersecurity.
Of course, you won’t be able to outsource everything. There’s going to be some parts of your digital infrastructure that are proprietary and not for the eyes of people that aren’t under NDAs. That’s why so many of the companies IBM spoke with in its study placed such a priority on hiring skilled and qualified personnel.
And while a number of organizations are now tasking the CISO with overseeing much of the recovery and resilience efforts, that’s probably short-sighted. In its report, Ernst & Young made the case that this needs to be a shared responsibility:
Executive leadership and support is critical for effective cyber resilience. Unlike the “sense” and traditional “resist” activities which can be seen as the domain of the Chief Information Security Officer or the equivalent, in the “react” phase, cyber resilience requires other senior executives to actively take part and lead. Since 2013, EY’s annual GISS survey, have consistently shown that almost a third of responders says there is a lack of executive awareness and support for cybersecurity strategy. This statistic suggests that organizations are not doing enough to ensure that senior executives are taking the lead in building cyber resilience.
Ok, let’s tie this all together now with a practical example.
Example: Approaching Phishing with a Cyber Resilient Strategy
Let’s pick on Ross, because he writes about email security here all the time and it’s an obvious example. Say, The SSL Store is working on its cyber resilience strategy, we’re all in that stuffy conference room, Ross is in charge of IT so he’s obviously a stakeholder. And today we’re working on the email security portion of our cyber resilience plan.
Stage One: Defining Risks
We’re going to start by scoping the issue, identifying all of the different elements we need to be considering. We need to look at:

- What are we using our email for (marketing, internal communication, etc.)
- What data are we processing in our emails?
- Where is that data being stored?
- What safeguards do we already have in place?
- What is the threat model?
- What is the worst-case scenario?
- Could the worst-case scenario result in us having to shut down?
- If so, for how long?
- What would need to be done to fix it?
- How long would that take?
- What’s the best way to avoid this?
- What other incidents could you foresee occurring?
This isn’t going to be an easy conversation. In fact, it’s going to be rather exhaustive. That’s why it would be wise for Ross to have this information in-hand when the meeting begins, lest we have to spend a couple hours identifying everything before we can even start with the planning.
Stage Two: Developing a Security Plan
Now it’s time to determine what we need to put in place to protect and defend our email, which is the cybersecurity portion of our resilience plan. This is where we’re going to look at all the safeguards that are at our disposal and determine which ones are appropriate. This where any budgetary constraints are going to come up as some options might be cost-prohibitive for some organizations.
Sticking with our email example, we’re going to debate, and then potentially implement:

- Switching to a more secure mail gateway
- Encrypting the mail servers
- S/MIME certificates
- Sender Policy Framework
- DomainKeys Identified Mail
- Domain-based Message Authentication Reporting & Conformance
- Updating our Spam and Email Filtering rules and policies
- Employee phishing simulations
- Semi-annual cybersecurity training
In our case, we’re already doing most of these, but at any rate, identifying each one of the tactics and tools you’re using will be key in determining whether your overall security posture is sufficient, or if you need to invest in some improvements.
Stage Three: Developing a Recovery Plan
Now it’s time to discuss recovery. Remember how earlier we laid out all the foreseeable exploits and incidents that might befall us? Now it’s time to work through each one of those scenarios and determine what would need to be done to remediate it.
At this point, you’ve identified the systems and settings you have in place to detect (and hopefully mitigate) these scenarios, so you won’t need to worry about any of that in this stage. Frankly, this has a lot more to do with business resilience and continuity.

What servers need to be reset? Where?
You’re backing up your data, but do you know specifically what data is being backed up? How much of it is mission critical? Can you access it and recover it quickly?
What are the minimum requirements to at least get the business returned to normal operations? What, on the other hand, isn’t a priority in this scenario? Is there anything your users and customers can live without while you scramble to restore the most critical components of your business?
This is the stage of your resilience plan where you need to be answering these questions and creating the requisite procedures for accomplishing them.
“Here’s how we’re going to respond to and overcome the range of potential threats facing our email.”
You’re literally defining how your organization is going to pick itself up off the mat when it gets taken down by one of its attackers’ best shots.
Stage Four: Determining a proper test/review program
Sticking with our email example, we’ve now identified the threats, formalized our security plans and created procedures for restoring or maintaining business continuity in the even they come to pass. Great.
We’re not done.
Now we need to make sure we develop a mechanism for testing and improving our resilience plan. After all, the threats are going to continue evolving – so we need to keep evolving, too. Part of this comes down to simply keeping abreast of the constantly-changing threat landscape.
So, in our case that would be looking at things like:
- What new tactics are being used in phishing campaigns
- Common words and phrases that appear in phishing email
- Common file types delivering malicious payloads
- Commonly imitated brands and services
- New vulnerabilities and zero-days involving products we’re using
You can also roll your patching cadence (how frequently you apply security and firmware updates to devices and software) up under this category. Out-dated or unpatched software is one of the biggest attack vectors facing organizations. Additionally, new technologies like Sectigo’s Zero Touch S/MIME feature on its SCM platform integrates with your active directory and removes 95% of the work from deploying email certificates. Staying informed about developments like this, which can be implemented affordably and improve key processes, is key to maintaining resilience.
As we identified earlier, training is going to be a big portion of the email portion of our cyber resilience plan, too. As the saying goes, “technology doesn’t get phished – people do.” So we’re going to need to incorporate regular training, too. And it’s going to be important the training stay up-to-date, also.
If you had to sum up this final portion in one word it would be: evolution. A resilient organization is agile, and constantly improving.
How can The SSL Store help your organization Cyber Resilience?
Obviously, as the name might suggest, we can help you with a lot of the encryption needs you’ll have in addressing the security portions of your resilience plan.
But, perhaps the most impactful way we can assist you comes in the form of automation.
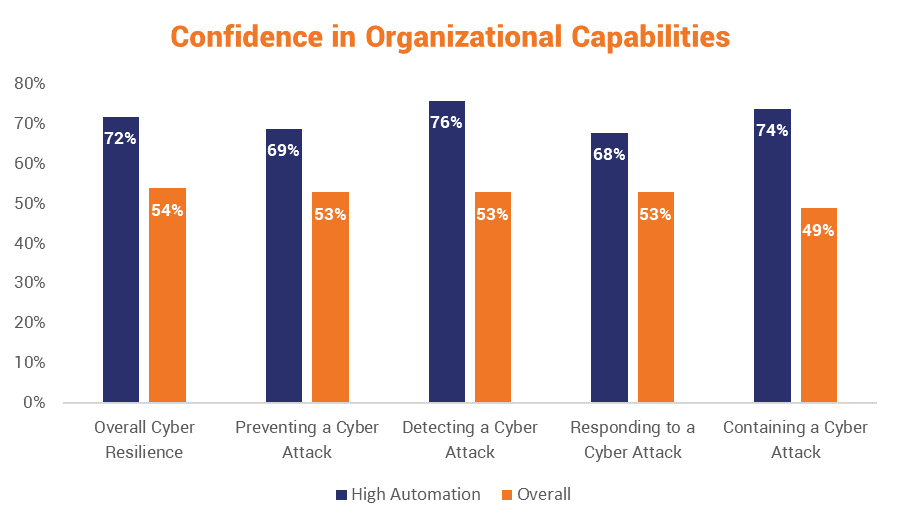
Automation is becoming an increasingly integral part of resilience. In fact, the IBM study we cited earlier found that automating certain portions of your digital infrastructure can decrease the chances of a successful cyber-attack or large-scale cyber incident by as much as 25%.
The study found:
- High automation organizations are more capable of preventing security incidents.
- High automation organizations take less time to respond to and contain security incidents
- High automation organizations rate their overall cyber resilience, prevention and detection capabilities much higher than their non-automated counterparts
- High automation organizations are more likely to recognize the importance of employing highly-trained cybersecurity professionals
- High automation organizations are more likely to use advanced technologies and threat intelligence sharing services
- High automation organizations are more likely to recognize the importance of privacy functions in achieving good cybersecurity posture and strong overall resilience
- High automation organizations have less complicated digital infrastructures.
I book-ended that list with the two most important takeaways: high automation organizations prevent more cybersecurity incidents, respond to them faster, contain them more quickly and their overall digital infrastructure is far simpler.
In fact, more organizations rated automation as being more important than cyber resilience altogether:
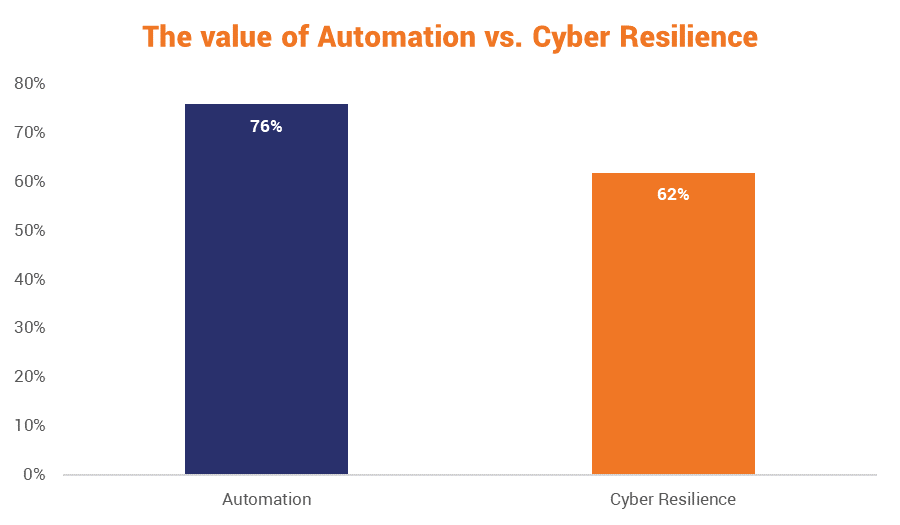
Regardless of how organizations view the importance of automation and cyber resilience, there’s no doubt that the former considerably improves the latter.
Automation improves security and resilience by removing the human element from processes and ensuring they run smoothly and efficiently. We offer platforms for both certificate and key management that can fully automate your PKI and SSL/TLS needs.
You may not think that’s a huge problem but one of the biggest culprits in terms of operational downtime and services becoming inaccessible is certificate expiration. According to a recent KeyFactor study, 74% of organizations polled have experienced unanticipated downtime/outages over the past year and the average cost per incident was $11,112,000. Rogue certificates, Man-in-the-Middle attacks and phishing websites – all of which can also be rolled up under certificate management – accounted for an additional $13,219,850 worth of losses.

Automating certificate/key management and PKI simplifies everything, reduces workloads, improves visibility and makes it much harder for humans to muck it all up.
It’s just one component of a much larger cyber resilience strategy, but a component we’re well-versed in and ready to help with. And we’ve been told we have very nice phone voices, too.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)







 (3 votes, average: 3.67 out of 5)
(3 votes, average: 3.67 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown