How to Perform a Cyber Risk Assessment
Every company needs a cyber risk assessment nowadays, here’s everything you need to know.
A cyber risk assessment is a crucial part of any company or organization’s risk management strategy. Nowadays, just about every organization relies on information technology and information systems to conduct business. And there are risks inherent in that. Risks that, up until the digital age, companies never had to really contend with.

Risk assessments are nothing new. They’ve been around in some form or another since at least the ancient Egyptians, when they would use various calculations to try and determine whether they needed to store up extra grain because the Nile river would fail to flood. For all intents and purposes, they became much more formalized in the early 1900s when labor movements started pushing for safer workplace conditions.
And you have to be careful when you’re looking for advice on performing a cyber risk analysis, because if you forget the word “cyber” you end up in a land of industrial manufacturing accidents and death & dismemberment clauses.
That’s why we’ve put together this guide on how to perform a proper cyber risk assessment. We’ll be going by National Institute of Standards and Technology (NIST) guidelines. NIST is a US agency that’s rolled up under the Department of Commerce. It publishes guidance on things like encryption best practices. As you’ll see, it also provides a system for calculating risk that will be useful as we develop our assessment.
What Is a Cyber Risk Assessment?
Cyber risk assessment is a fairly autological term, you are literally performing an assessment of the cyber risks facing your company or organization. NIST defines it thusly:
Risk assessments are used to identify, estimate, and prioritize risk to organizational operations (i.e., mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation, resulting from the operation and use of information systems.
You can toss out the line about “and the Nation.” NIST issued these guidelines for federal entities. For most of us, our cyber risks will not rise to the level of potentially being a national security threat.
At any rate, the primary purpose of a cyber risk assessment is to help inform decision-makers and to support proper risk responses. Bear in mind, most C-suite executives and even some directors don’t have time to delve into the minutiae of your day-to-day cyber operations. So this cyber risk assessment will serve as a sort of executive summary to help those parties make informed decisions about security.
The best way to do that is to identify:
- Relevant threats to your organization
- Internal and external vulnerabilities
- Impact if those vulnerabilities are exploited
- Likelihood of exploitation
If you can answer those questions you should be able to make a determination about risk.
Why Do We Need to Perform a Cyber Risk Assessment?
There are a number of reasons you might want to perform a cyber risk assessment—and a few other reasons why you need to. Let’s go through them:
- They can reduce long-term costs – Obviously, identifying potential threats and working to mitigate them has the potential to prevent security incidents, which saves your organization money in the long run.
- It provides a template for future assessments – Cyber risk assessments aren’t a one-off, you need to continuously update them. By doing a good job on the first one, you create a repeatable process that can be picked up by someone else in the event of staff turnover.
- They provide your organization with greater self awareness – Knowing where your organization’s weaknesses lie helps give you a better idea of what areas your organization needs to grow and invest in.
- It helps you avoid breaches and other security incidents – This hearkens back to our first point, a well-done cyber risk analysis can improve your security implementations and mitigate attacks and personal data breaches.
- It can improve communication – Typically a cyber risk assessment (on that’s done well) requires input from a number of different departments and stakeholders, this can help increase organizational visibility and enhance communication.
If that was unconvincing, let’s look at two reasons you NEED to do a cyber risk assessment:
- You need one to get cyber insurance – As we discussed yesterday, cyber insurance has never been more critical. Without it, organizations can be put entirely out of business—2 out of every 3 uninsured SMBs hit by a breach go under. If you want cyber insurance, you need to perform a cyber risk analysis.
- It may be legally required – Various industries with various regulatory requirements may already have a legal obligation to perform a cyber risk assessment. For instance, under HIPAA (Health Insurance Portability and Accountability Act) all “covered entities” must perform a proper cyber risk assessment. There are also PCI-DSS requirements, federal requirements—even in our own industry, the baseline requirements set forth by CA/Browser Forum require every Certificate Authority to perform a yearly cyber risk assessment.

“A risk assessment is often a mandatory baseline that compliance regulations ask for,” says Sanjay Deo, President of 24by7 Security. “HIPAA, FERPA, NY State Cybersecurity Regulations are only some of the laws that require a risk assessment to be done by impacted companies in the healthcare, education and financial sectors. By performing this required step, companies can not only work towards compliance with these regulations but also have a good baseline of their current security posture and recommendations for improvement. Every risk assessment report must have a view of the current state of the organization’s security, findings and recommendations for improving its overall security”.
Beyond that, cyber risk assessments are an integral part of any organization-wide risk management strategy. We’re not going to go too far into the weeds discussing holistic risk management strategies – that is a discussion for another day – but suffice it to say risk management strategies are, themselves, a crucial element of organizational security.
Who Should Perform a Cyber Risk Assessment?
Ideally, your organization would have personnel in-house that could handle this kind of assessment. You’ll need to have IT staff with an understanding of how your digital and network infrastructures are set up, as well as high-level executives that understand various information flows and potentially proprietary organizational information that will be useful during the assessment. Organizational visibility is a major component of a thorough cyber risk assessment.

But, sometimes organizations, especially small or medium sized businesses (SMBs), may need to outsource the assessment because they don’t have the right people to do the job in-house. In that case, you’re going to need to find a third party to do it. There are both companies as well as individual consultants that can provide this service.
Here are some things to consider when you’re looking:
- Ask for recommendations – Chances are you may have partners that have already used a company or consultant for a cyber risk assessment and can give you a recommendation. Alternatively, organizations like the Chamber of Commerce and Better Business Bureau should be able to offer you a referral.
- Request a quote – Don’t wait until the assessment is being delivered to talk price. While there is always the potential for fluctuation, given the size and scope of your operation, it’s best to have a firm idea about cost before you get started.
- Vet your risk assessor – Regardless of its another company or a single consultant, you should be able to find reviews and feedback that will indicate whether they do a good job or just enough to complete their report. If you’re working with another company on the assessment, find out who specifically will be doing the work on your account.
If you’re a consultant performing an assessment for another company, here’s a free bit of advice, too. Diligence is key.
Jack Plaxe, a 30-year security veteran, is the founder and managing director of Security Consulting Alliance in Louisville, Kentucky.
“Perhaps the single best tip is to take time to understand the organization you’re assessing,” says Plaxe. “Read the annual report and SEC filings. Ask for and review and internal documents they’ll share, including policies and procedures, protocols, employee handbooks, training presentations, etc. Interview not only senior leadership but also employees from different departments and at different levels of the organization. This research will give you broader insights into the business that will help you during the risk assessment process.”
How to Perform a Cyber Risk Assessment
Let’s start with a top-level overview and then we’ll drill down into each point in subsequent sections. Before you do anything to start actually assessing risk, you’re going to need to take stock of what data you have, what infrastructure you’re protecting, etc. You may want to start with a data audit. A well-done data audit identifies what data your company is storing and what its value might be. A good data audit answers the following questions:
- What data are we collecting?
- Where are we storing the data?
- How do we protect and document the data?
- How long do we keep the data?
If you’ve already performed one of these for GDPR compliance you’re a step ahead.
Next, we’re going to need to define parameters for your assessment. Here are a few questions to help guide that process:
- What is the purpose of the assessment?
- What is the scope of the assessment?
- Are there any specific priorities or constraints affecting the assessment?
- Who do we need to talk within the organization to get all the information needed?
- What risk model are we going to use for this analysis?
Some of these questions are self-explanatory. But, you really want to get a sense of what you’ll be analyzing, who holds the expertise you need to really perform the analysis, are there any regulatory or budgetary preferences that need to be considered—that kind of stuff.
As far as the threat model, we’ll go with what NIST has suggested.

Now let’s talk about what steps actually need to be taken in order to complete this cyber risk analysis.
- Identify threat sources
- Identify threat events
- Identify vulnerabilities and the conditions needed to exploit them
- Identify the likelihood such attacks would succeed
- Identify the potential impact
- Determine the risk posed
After that you should be able to prioritize your responses to the risks you have identified.
Now let’s break down each one of those steps a little further.
1. Identify and Document Threat Sources
For our purposes there are two types of threats. There are adversarial threats that can be exploited by third-party attackers. And then there are non-adversarial threats where, via negligence, a mistake or some other non-malicious means your organization could face risk.
For instance, your adversarial threats may be:
- Individuals – Third-parties, insiders, trusted insiders, privileged insiders (these refer to varying levels of employee permissions)
- Groups – Established hacker collectives, ad hoc groups
- Organizations – Corporate espionage by competitors, suppliers, partners or customers
- Nation-states
Non-adversarial threats typically come from regular users of your website, employees or admins.
Now, it’s probably worth noting again that NIST produces guidelines that apply to federal entities, so some of these “adversaries” are not likely parts of your threat model. You probably won’t need to worry about North Korean hackers or Fancy Bear.
After you’ve identified the threats facing your organization, you’ll need to assess them (this is, after all, a cyber risk assessment). Here’s something important to remember, too: during these first two steps you are operating in a hypothetical sense—almost in a vacuum. We will compare these against your actual security implementations and organization readiness later, but for now you’re just listing all the things that COULD happen.
Here’s what you need to assess. For adversarial threats, you’ll need to assess the capabilities, intentions and targeting of the potential attackers. Here’s an example of the scale NIST uses to quantify threats. Notice the way that the assessment is broken up into threat levels with accompanying values. These are going to be instrumental in calculating your risk.
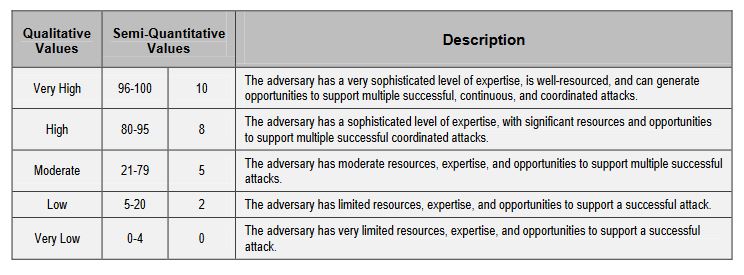
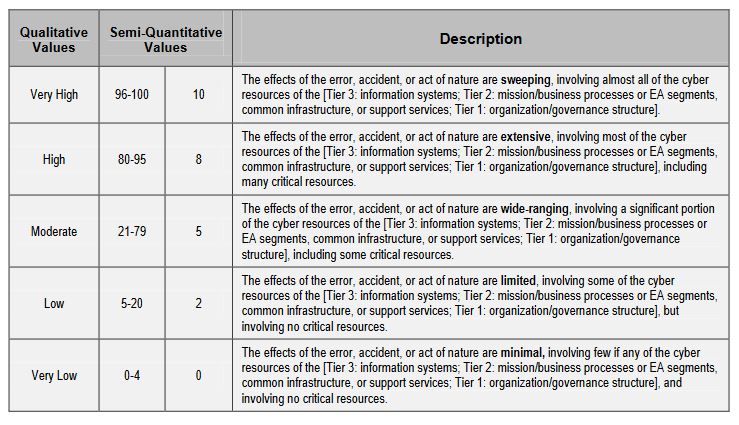
For non-adversarial threats, you just need to weigh the potential impact should an event take place.
2. Identify Threat Events
Threat events are the actual attacks or events that could potentially be perpetrated against your organization. Now that you’ve covered the potential actors, you are literally going to list every potential attack, exploit, glitch or mistake that you can think of, divided up in the aforementioned categories (adversarial and non-adversarial).
Per NIST:
Threat events are characterized by the threat sources that could initiate the events, and for adversarial events, the [Tactics, Techniques and Procedures] used to carry out attacks. Organizations [need to] define these threat events with sufficient detail to accomplish the purpose of the risk assessment.
As usual, this is best illustrated with an example. Here’s just part of the table that NIST put together as a reference. Eventually, you’re going to have to assess the risk involved in each one of these, but for now it’s more important just to be as comprehensive as possible. That includes making sure that your descriptions actually apply to your organization and aren’t just some boilerplate definitions you pulled off Wikipedia.
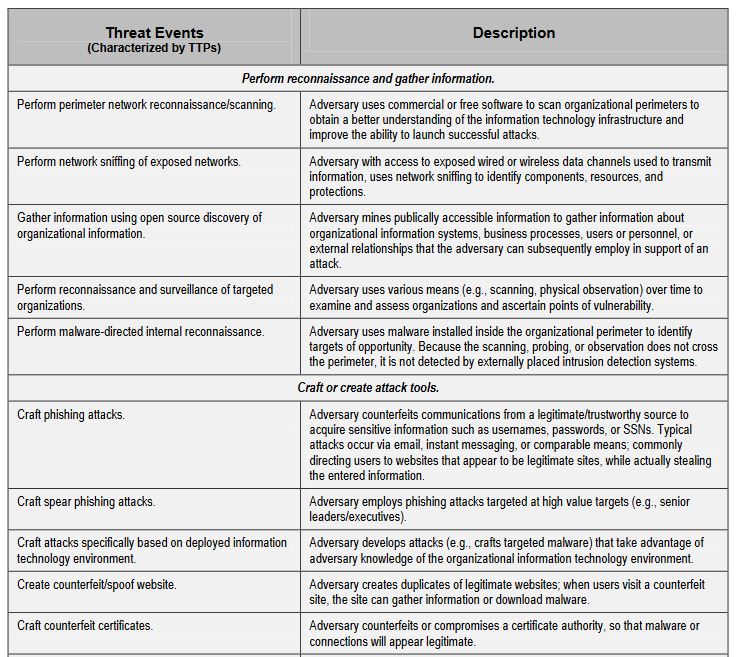
The example NIST gives is five pages long, which just reinforces how comprehensive you need to be. You can’t prepare for threats that you didn’t anticipate, so this step is absolutely crucial. Here are some types of threat that nearly every organization faces.
- Unauthorized access – This can be both adversarial and non-adversarial in nature, potentially occurring from an attack, malware or even just employee error.
- Misuse of information by authorized users – This is typically an insider threat that can occur when data is altered, deleted or used without approval.
- Data leaks/accidental exposure of PII – Personal Identifying Information, known as personal data in the EU, is considered breached anytime it is altered, deleted or disclosed to an unauthorized party. Even if it’s accidental.
- Loss of data – This dovetails with the previous points, it occurs when an organization loses or accidentally deletes data as a result of a botched backup or poor replication.
- Service/productivity disruptions – This one is pretty self-explanatory.
Now it’s time to take that list you’ve just compiled and assess just how critical each threat is. As we’ve discussed, we’re using the NIST template (for the sake of simplicity I am omitting the various organizational tiers in order to streamline what is already a cumbersome process) but if you feel that something else works better for your organization, then by all means use that instead.
The concepts being presented here will work regardless of what formula you ultimately decide to use.
So, how do we assess the relevance of each threat? With another table, of course. First, here is the scale we’re using:
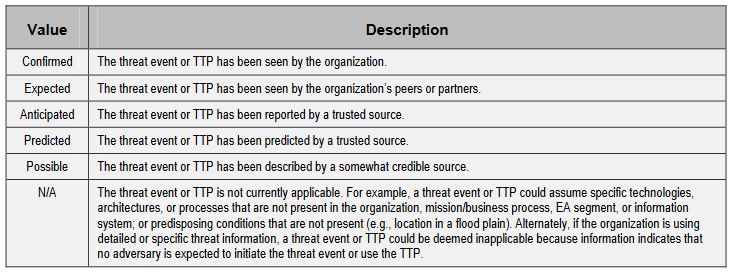
Now let’s talk about how you set up the table. It’s nothing you need to call in the design team for. We need three columns. The first column lists the threat event, the second column lists the potential source(s) of the event and then finally, the third column will list the relevance we determined using the table above this paragraph.
3. Identify Vulnerabilities and the Conditions Needed to Exploit Them
Now it’s time to move from the hypothetical to reality. What you should have been doing up until this point is compiling a comprehensive list of everything that COULD happen. Now let’s measure the threats against your actual digital infrastructure and organization security implementations to determine their real-life severity.
The severity of a vulnerability is an assessment of the relative importance of mitigating such a vulnerability. Initially, the extent to which mitigation is unplanned can serve as a surrogate for vulnerability severity. Once the risks associated with a particular vulnerability have been assessed, the impact severity and exposure of the vulnerability given the security controls implemented and other vulnerabilities can be taken into consideration in assessing vulnerability severity.
You will have to determine what vulnerabilities coincide with what threats, and then factor in what – if any – controls are in place to mitigate such an event. Here is the scale that NIST uses:
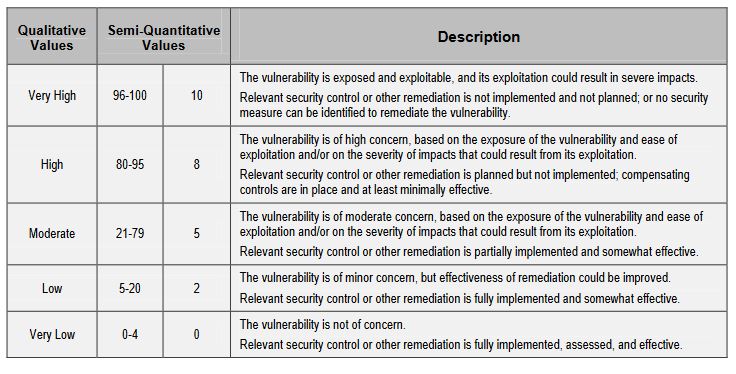
Now, you can get extremely granular and start breaking vulnerabilities down into taxonomies and the pervasiveness of conditions that could enable these exploits, you can read more about that in the actual NIST guidelines, but for the sake of streamlining this exercise and avoiding paralysis of analysis, we’re going to keep it at this level.
There’s always time to further organize and refine the threat data in future cyber risk assessments.
4. Identify the Likelihood Such Attacks Would Succeed
Ok, so now we have identified the threats, the risks and how they apply specifically to your organization’s infrastructure and security posture. Now it’s time to take a look at how likely these attacks and events actually are. And not just whether you might face one of these events at some point, but what it’s potential for success might be.
Please note that the way we are using the word “likelihood” differs from its colloquial use. This isn’t likelihood in the strict sense of the term, it’s used in almost an insurance context, resulting in a “Likelihood score.” Risk assessors assign this score (or likelihood assessment) based on available evidence, experience, and their expert judgment.
It’s basically an equation that weighs the likelihood of initiation or occurrence of an event against the likelihood that said event would have an adverse effect. This isn’t just you making arbitrary decisions about how likely you think an event or attack would be to succeed.
Instead you need to base the likelihood of an attack being initiated on the capabilities of the attacker(s), their intent and who they have historically targeted. So, for instance, the Russian-backed hacker group Fancy bear has historically gone after US government institutions and political parties. So if I’m putting together a cyber risk assessment for the Department of Justice (which, if you guys are reading, I’m available), you could say there is a high likelihood of that threat being initiated. Conversely, if I were running a deli in Queens I probably wouldn’t even need to list Fancy Bear.
Organizations assess the likelihood that threat events result in adverse impacts by taking into consideration the set of identified vulnerabilities and predisposing conditions. For threat events initiated by adversaries, organizations consider characteristics of associated threat sources. For non-adversarial threat events, organizations take into account the anticipated severity and duration of the event (as included in the description of the event).
To accomplish this, we are going to use the assessment scales listed below.
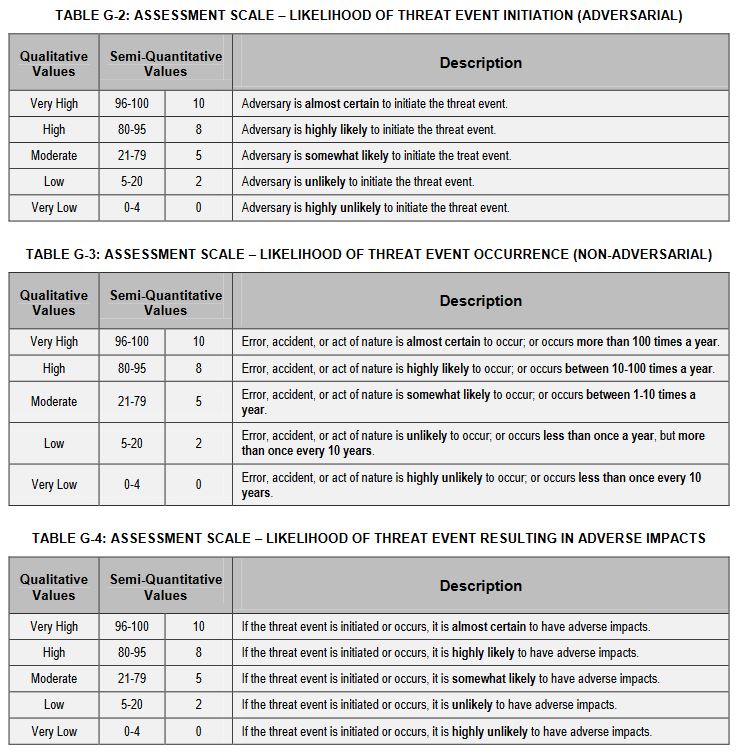
Now, in order to calculate your actual risk you’re going to determine the overall likelihood score by factoring the overall likelihood that an event will occur (via attack, human error, etc.) against the likelihood that the event would result in adverse impacts for your organization.
The formula used to determine total likelihood varies from assessor to assessor. They are generally influenced by:
- Organizational attitudes toward risk
- Tolerance for uncertainty regarding certain risk factors
- Organizational weighting of risk factors
As for what works best, NIST is fairly agnostic, even offering a handful of models in its guide. The important thing is that you are consistent in the formula’s application once you decide how to factor things.
5. Identify the Potential Impact
It’s time to take what we’ve already put together, which is basically your organization’s threat model, and use it to determine the impact any of these events would actually have. And in sticking with a common theme in cyber risk assessments—there are a lot of factors to consider when determining potential impact, including:
Where the threat event occurs and whether the effects of the event are contained or spread, influences the severity of the impact. Assessing impact can involve identifying assets or potential targets of threat sources, including information resources (e.g., information, data repositories, information systems, applications, information technologies, communications links), people, and physical resources (e.g., buildings, power supplies), which could be affected by threat events.
So, like we did in step two, create a table with two columns and organize the different types of impact (harm to operations, harm to assets, etc.) on one side, while listing the different ways that impact could play out. Here’s an example.
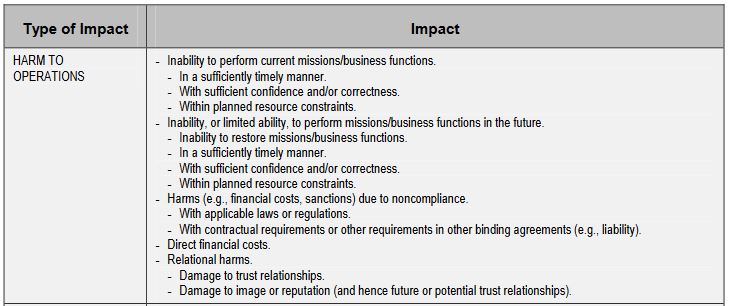
You’ll probably also want categories that cover harm to assets (you may even want to segment it further and get into physical assets, digital assets, etc.), harm to individuals or data subjects, harm to third-party organizations like your partners and if you’re feeling patriotic NIST also has a category for “harm to the Nation.”
And for reference, here is the scale that NIST proposes for measuring impact.
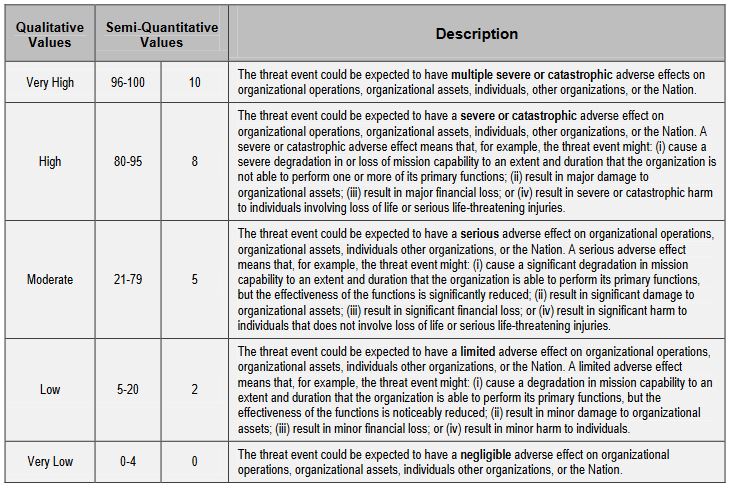
And finally, you’re going to assess the potential impact for each item you listed under “Type of Impact” in the first table.
Now it’s time to put everything you’ve done over the previous five steps together.
6. Determine Your Organizational Risk
Your risk is ultimately going to be determined by the confluence of the likelihood of an event and the potential impact it poses. There are a number of ways to calculate this, you can use the scales provided by NIST, assigning numbers to likelihood and impact and then calculating it that way or you can use an alternative methodology that is supported by your industry or a regulatory body that oversees your organization.
Since we’ve been citing NIST for this article, let’s use their examples one last time. Here’s the scale NIST proposes for government entities to quantify level of risk:
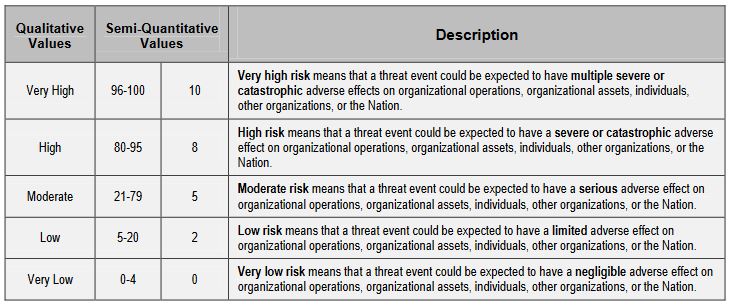
So, using the values given earlier, you need to factor likelihood against impact and the scores you produce will represent your organizational risk for each potential event.
Now it’s time to finalize your cyber risk assessment and start using it to improve your security posture.
What Do to When You Finish Your Cyber Risk Assessment
The first thing you’ll need to do upon completing your assessment is probably double-check your team’s work. Following that, it’s time to share the information you’ve put together with decision makers in your organization, as well as with any stakeholders that can use the actionable parts of your assessment to improve security in their areas of operation.
These two groups will usually be your organization’s C-suite and its IT team, but there could be other relevant parties, too.
Additionally, this cyber risk assessment should not be a one-off. Whether you choose to make it a living document or start fresh next year, you need to continuously revisit your cyber risk assessment to ensure that it is up-to-date and that your organization maintains compliance.
Ideally, as your security implementations are improved and you react to the contents of your current assessment, the risk score in your future cyber risk assessments will steadily decline.
You’ll never completely mitigate all risk. It’s foolish to even think that you can. But you can minimize risk by continually assessing it and then working to implement safeguards that diminish the likelihood and impact of any security event.
As always, feel free to leave any comments or questions below!
Cyber attacks and data breaches are no longer a matter of “if,” but “when.” The smartest organizations know this and focus on being cyber resilient – not just secure.
Like what you read? Check out our series on GDPR compliance:
- GDPR: Introduction to a Series
- GDPR: How it affects the Domain Industry
- GDPR: How it affects Web Hosts
- GDPR: Problems for ICANN/WHOIS?
- GDPR: Complying with EU-US Privacy Shield
- GDPR: What is a Data Protection Officer?
- GDPR: Best Practices for Privacy Notices
- GDPR: What you need to know about Cookies
- GDPR: What is the Right to be Forgotten?
- GDPR: How to perform a Data Audit
- GDPR: Encryption Best Practices
- GDPR: When to report a Personal Data Breach
- GDPR: Don’t forget to train your Customer Service team






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown