GDPR: How the General Data Protection Rule Affects the Domain Industry
A five-minute glance at how the EU’s incoming GDPR will affect the Domain Industry
The General Data Protection Rule is set to come into effect on May 25, and with it will come far-reaching changes to the way businesses collect, handle and process personal data. The GDPR will replace the Data Protection Directive of 1995. It’s intended to provide uniform protections to individuals living in the EU.
However, you don’t have to be based out of the EU to be affected by the GDPR. Anyone with a European footprint, that is, any business with customers under the jurisdiction of the EU will need to comply lest they face fines or other legal penalties.
This is the third entry in our series on the GDPR. Last week we gave seven tips for web hosts as they prepare for the GDPR. This week we’ll give advice to the Domain Industry.
Important GDPR Terms to Know
As we discussed last week, one of the most important things to do when preparing for the GDPR is “learn the lingo.” Here’s a set of key terms you’ll need to be familiar with as you begin to navigate compliance.
Data Subject – The person to whom the information relates.
Subject Access Request – A written request from an individual requesting action on the data held about them. This can mean notifications about what data is possessed, where it is stored, corrections to that data and also the outright deletion of it.
Personal Data – Any information related to an identifiable person.
Data Processing – Obtaining, recording or holding information, or carrying out any operation on said information.
Data Controller – The entity that determines the purpose for which and the manner in which data is processed.
Data Processor – Any person or entity who processes information on behalf of a data controller.
What are some of the biggest changes?
To make this easier to digest we’ll just break this down into a bulleted list.
- The GDPR applies to anyone that provides services to, markets to or collects data from EU citizens, regardless of where your organization is based out of.
- Consent for the storage and use of information must now be freely given, it must be specific and informed and it must be unambiguous.
- EU Citizens have the right “to be forgotten,” meaning that they can demand their information be deleted at any time.
- All Data Protection Agencies can enforce the GDPR regardless of where a business is based.
- Fines can be up to 20 million € or 4% of the annual global group turnover.
- In the event of a breach or a leak, companies must inform the relevant Data Protection Agency immediately.
- Liability is extended to both data controller AND data processor.
How Data Flows in the Domain Industry
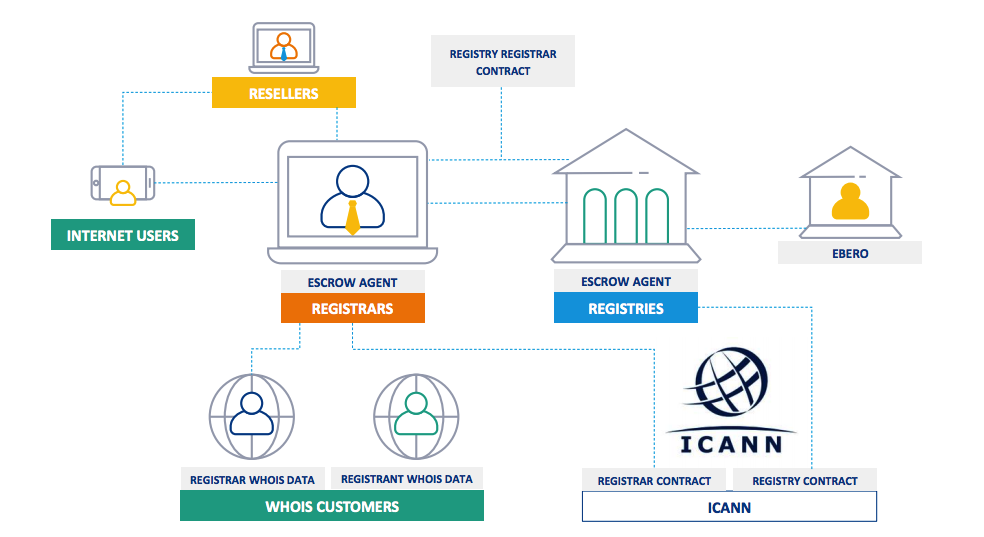
How the GDPR Affects: Domain Name Registries
Domain Name Registries will need to consider all of the following, for starters data transfers to Data Escrow Agents, EBERO, ICANN and Registry Service Providers will need to comply with the GDPR. Additionally, the data you publish on Whois will need to be reduced to just what is necessary. And a lawful basis for processing this information will need to be established. The lawful bases covered by the GDPR are: consent, performance of a contract with the individual, a legal obligation, vital interests, interest of the public, your legitimate interests.
Note: Because registries collect the data from Registrars, they cannot rely on consent to process data.
Also consider:
- A Registry is a Data Controller.
- Information collected in the first instance needs to be reduced to just what is necessary for registration of the domain name.
- Zone files that can be accessed sometimes contain personal data.
- Registries will have to process data subject access requests.
How the GDPR Affects: Domain Name Registrars
Domain Name Registrars will need to consider all of the following, for starters data transfers to Data Escrow Agents, Registry Operators and ICANN will need to comply with the GDPR. And as with Registries, the information you publish on Whois will need to be minimized to only what is required. Likewise the information you collect as a Registrar. All information must also be kept up to date. As for establishing a lawful basis for processing the information, while registrars collect data from the registrants (data subjects) and could rely on consent to process the registrant’s data, citing the performance of a contract would be a better decision.
Also consider:
- A Registrar is a Data Controller.
- Registrars will have to process data subject access requests.
Data Subjects Have the Following Rights
Data Subjects have the right to:
- Ask a company what information it holds about them, as well as why.
- Ask to gain access to their own information.
- Requests that the information be changed or updated.
- Object to or limit the processing of data.
- Receive information about how your organization is meeting its data protection obligations.
- Be informed in the event of a breach.
- Have their information deleted (under specific circumstances)
Check out the rest of the Hashed Out GDPR Compliance Series
- GDPR: Introduction to a Series
- GDPR: How it affects the Domain Industry
- GDPR: How it affects Web Hosts
- GDPR: Problems for ICANN/WHOIS?
- GDPR: Complying with EU-US Privacy Shield
- GDPR: What is a Data Protection Officer?
- GDPR: Best Practices for Privacy Notices
- GDPR: What you need to know about Cookies
- GDPR: What is the Right to be Forgotten?
- GDPR: How to perform a Data Audit
- GDPR: Encryption Best Practices
- GDPR: When to report a Personal Data Breach






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown