The GDPR and Privacy Shield – Compliance for US Businesses
Privacy Shield compliance is required for cross-border data transfers from the EU to US
The EU’s General Data Protection Regulation (GDPR) goes into effect on May 25, and companies around the world are scrambling to become compliant. As we’ve discussed many times, the GDPR doesn’t just apply to European companies, it applies to any company that does business in Europe. For companies in the United States, that means familiarizing yourself with the EU-US Privacy Shield.
Remember, Data Security is at the heart of the GDPR (hence the name), and part of the regulation deals specifically with the transfer of data from the European Economic Area (EEA) to other countries. Unfortunately, despite being one of the leaders with regard to the development and evolution of the internet, the United States does not have adequate data privacy laws. At least not in the eyes of the EU. Given that fact, the EU-US Privacy Shield is a workaround for American companies.
What is the EU-US Privacy Shield?

The EU-US Privacy Shield is a program for US companies to demonstrate adequate compliance to EU-required data privacy standards. This, in turn, allows for the transfer of data from EU jurisdiction to the US and vice versa.
The EU-US Privacy Shield was preceded by the International Safe Harbor Privacy Principles. Those were designed between 1998 and 2000 and remained active until October 2015, when the European Court of Justice ruled them invalid on the grounds that they were no longer adequate. Soon thereafter, the US Government began talks with the European Commission on a new framework. After several rounds of revisions, the EU-US Privacy Shield’s final version was published on July 8, 2016 and ratified several days later on July 12.
GDPR Restrictions on Cross-Border Data Transfers
The GDPR prohibits the transfer of data outside of the European Economic Area to a third-party country unless:
- The recipient country provides an “adequate level of data protection”
- The data exporter puts in place appropriate safeguards (such as EU-US Privacy Shield)
- A derogation or exemption exists as justification
The Recipient Country Provides “Adequate” Level of Protections
Ok, so let’s parse this a bit. The first point, that the recipient country provides an “adequate level” of data protection is straightforward as far as the GDPR goes. Currently, the list of countries with “adequate” protections includes:
- Andorra
- Argentina
- Canada (organizations must be subject to PIPEDA)
- Switzerland
- The Faeroe Islands
- Guersney
- Israel
- Isle of Man
- Jersey
- New Zealand
- Uruguay
Countries that do not appear on the list can petition the European Union for an “Adequacy Decision” that will allow cross-border data transfer to occur without the need for further safeguards. The commission will evaluate the third-party country on factors such as:
- The rule of law in the country; legal protections for human rights and freedoms
- Access to transferred data by public authorities
- The existence and proper functioning of supervisory Data Protection Agencies
- International commitments and agreements with regard to data security
Adequacy Decisions are reviewed every four years and can be repealed, amended or suspended based on the circumstances.
Why is the United States not an “Adequate Jurisdiction?”
Though the United States has worked extensively with the European Commission on data security standards, it is not considered an Adequate Jurisdiction by the Commission. Much of this stems from an executive order titled “Enhancing Public Safety” that was signed by US President Donald Trump in his first week in office. The Executive Order, #13768, signed January 25, 2017, was intended to punish “sanctuary cities” – US cities that openly refuse to comply with immigration law and deportation orders – as part of Trump’s anti-immigration agenda.
It includes this line:
Agencies shall, to the extent consistent with applicable law, ensure that their privacy policies exclude persons who are not United States citizens or lawful permanent residents from the protections of the Privacy Act regarding personally identifiable information.
Stated another way, US privacy protections will not be extended to non-US citizens. And though this may have been designed to affect Muslim and Hispanic immigrants, it also applies to EU citizens.
This situation is evolving though, in 2017 the US Congress passed the US Judicial Redress Act, which extends the protections provided by the US Privacy Act to Europeans and gives them access to American courts. The European Commission has stated that it will continue to monitor the situation. As of now, the US is not on the list of countries that provide “adequate” data security.

What are the Exemptions and Derogations for Cross-Border Data Transfers?
There are a number of other arrangements in which cross-border data transfers can be completed, even without an Adequacy Decision or compliance with safeguards like EU-US Privacy Shield.
Agreements Between Public Authorities
The GDPR allows for cross-border data transfers on the basis of agreement between a public authority in the EU and a public authority in a third-party nation. This arrangement doesn’t require authorization from a Data Protection Agency provided that other GDPR requirements are complied with.
Binding Corporate Rules
Binding Corporate Rules are internal rules and policies that multinational companies use to govern and secure data being transferred internationally. The GDPR sets out a process wherein the supervising Data Protection Authority may approve an organization’s Binding Corporate Rules (BCRs) provided they meet the GDPR’s requirements. The BCRs must be approved at the outset. We’ll cover Binding Corporate Rules more in-depth at a later date, but for now, if you’re thinking of going the BCR route, keep in mind your policy should include:
- Information about Transparency, Data Quality and Security
- Tools of effectiveness, like audits you perform, training you provide and dispute resolution systems
- Proof that the rules are binding
Article 47 of the GDPR offers further guidance on this point.
EU Model Clauses
A Model Clause is a standardized contractual clause between a service provider and its customers that ensures any personal data leaving the EEA will be transmitted in compliance with the GDPR. If an organization cites the requisite safeguards in a Model Clause it does not need any further authorization from a Data Protection Authority.
Data Protection Agency Clauses
This is an alternative to the EU Model Clauses, if the relevant local or national DPA has its own contractual clauses – akin to the Model Clauses used by the EU – then those may also suffice, and additional transfers will not require further approval. Keep in mind, the European Commission will still need to approve the DPA clauses before they can be used. In the US, the Federal Trade Commission has exerted itself as the de facto DPA for most organizations.
Ad Hoc Clauses
In addition to standardized clauses provided by the EU and your DPA, you may also establish ad hoc clauses that are agreed upon by both parties (organization and data subject) and that satisfy GDPR requirements. These clauses do still require approval from the DPA, who will also apply a consistency mechanism – which is basically a means to regulate it.
Codes of Conduct
The GDPR allows for cross-border transfers when they are done in accordance with a binding, enforceable Code of Conduct. The Code of Conduct must be in compliance with the GDPR and it must be approved by the DPA before it can be used as a justification.
Certification Schemes
One of the lesser discussed components of the GDPR is its attempts to help support Seals and Certifications as a way to showcase compliance. While it’s fairly difficult to set up a certification scheme yourself, if you’re taking part in a DPA-approved one, then that provides justification for some types of cross-border data transfers. We’ll have an entire post dedicated to this in the near future.
Consent
Consent is the most powerful legal basis for doing anything under the GDPR. And while there are a few other exemptions and derogations, they mostly apply to government entities and public authorities. So we’ll finish with consent. Provided that you do a good job with your privacy notification – meaning that you gave a straightforward explanation of what you planned to do with the data, risks included – all you need is someone’s explicit consent and you can perform a cross-border data transfer, no problem.
Let’s Get Back to EU-US Privacy Shield

We’ve covered just about every possible justification you can give for transferring data from the EEA to the US. And for many companies and organizations, those justifications may work for some transfers, some of the time. But if you’re an American company doing any business in Europe you would be wise to cover your backside and get Privacy Shield certified.
What are the requirements for Privacy Shield?
Before we get to what you need to do to (self) certify for the EU-US Privacy Shield, let’s cover the requirements. You need to know what you’re committing to before you pull the trigger on this. As we discussed earlier, Privacy Shield is the successor to the Safe Harbor framework that was in place until 2015. Not surprisingly, it builds on Safe Harbor’s foundation. If your organization was already certified to Safe Harbor, you’ve got an excellent head start.
Privacy Shield has seven principles, six of which can be grouped into Individual Data Privacy Rights, and one which deals with enforcement and liability.
Privacy Shield Principle: Notice
Much like with the GDPR, much attention has been paid to notification. You are responsible for notifying data subjects of:
- Your organization’s participation in Privacy Shield
- The type of data being collected
- The purposes the data is being used for
- Any third parties you will share the data with
- Their rights to access the data
- The means at their disposal for limiting the use and disclosure of the data
- What recourse mechanisms are available
You must also acknowledge the authority of your supervising DPA. Once again, for the US this would likely be the FTC.
Privacy Shield Principle: Choice
Your organization must provide “clear, conspicuous, and readily available mechanisms” for data subjects to opt out of the disclosure of their personal data to third parties, or use of the data for a purpose other than what it was collected for.
Also, there is a distinction between personal data and special categories of personal data. Special categories of personal data refers to things like racial or ethnic origins, information about gender or sexual identity, political, religious or union opinions and activity, etc. If your organization is sharing this kind of data, it requires explicit consent from the data subject.
Privacy Shield Principle: Accountability
Organizations must now be careful in their third-party contracts to specify that transferred data “may only be processed for limited and specified purposes consistent with” the consent of the data subject. Basically, your organization is now liable to your customers for the data privacy practices of your partners, so you’ll have to make good decisions downstream. Privacy Shield-certified organizations are even required to supply the Department of Commerce with relevant third-party contractual provisions in some cases.
Should anything happen to the data, your organization will be the first one on the hook. Getting out of trouble would involve proving that your business wasn’t responsible for “the event giving rise to the damage.” That’s not a place you want to be.
Privacy Shield Principle: Security
Similar to what was in place with Safe Harbor, certified organizations will need to “take reasonable and appropriate measures” to secure data against “loss, misuse and unauthorized access, disclosure, alteration and destruction.” This one is pretty straightforward. You don’t need to reinvent the wheel here, just follow industry best practices.
Privacy Shield Principle: Integrity
The EU-US Privacy Shield expands on Safe Harbor’s requirement that data must be “relevant for the purposes of processing,” by adding limits. Now organizations must limit their collection of data to only what is relevant, and must act to ensure that the data being maintained is “reliable for its intended use, accurate, complete and current.”
Another thing to consider, these regulations apply to any data collected during the time you were certified—under the shield, so to speak. It’s like this data is timestamped in a way, as you will still be bound by these restrictions with regard to said data, even after certification has lapsed.
Privacy Shield Principle: Access
Again, similar to the GDPR itself, Privacy Shield requires that data subjects have access to do their personal data, along with the ability to correct it, amend it or even delete it (provided it’s inaccurate or in violation of the Privacy Shield principles). This is actually a fairly complicated topic (one that we will tackle in another post), but at least in this case there is solid direction in regard to how organizations should comply. It even allows organizations to charge a reasonable fee for access. Don’t do that. Charging people to access the information you have collected about them is a great way to kill any good will your brand may have had up until that point.
Privacy Shield Principle: Enforcement
This is the biggest changes from Safe Harbor to Privacy Shield, you must now provide detailed mechanisms for recourse and dispute resolution. And these need to be implemented thoroughly, not just tossed into a proposal and documented somewhere on your website. Organizations will need to have an official process for handling complaints.
Privacy Shield lays out three requirements for “effective enforcement:”
(a)(i) recourse for individuals to whom the data relate;
(a)(ii) follow up procedures for verifying that the attestations and assertions they have made about their privacy practices are true; and
(a)(iii) obligations to remedy problems arising out of failure to comply with the Principles and consequences for such organizations.
Here are a couple of things to remember about this, too. Privacy Shield requires the use of a third-party body for dispute resolution. This can be a panel provided by the DPA or some other arrangement. You must also be able to demonstrate that these processes are actually being implemented and are viable.
Remember, once you commit to Privacy Shield, you’re openining yourself up to regulation and punishment. Basically once you commit to Privacy Shield, as we’ll get to in a second, you have to make good on it. They’re going to hold you to your commitment.
How do I get certified for Privacy Shield?
Now that you know what’s required, let’s talk about what you need to do to get (self) certified. Yes, that’s right this requires self-certification. Basically your self-certification for Privacy Shield is going to involve two commitments.
First you commit to the US Department of Commerce that you will follow the principles we just discussed. Second, your organization must “publicly declare” its commitment, which in turns is a promise to data subjects that you will only process their data in accordance with the Privacy Shield principles.
Ok, but how do you that? It’s going to require an actual application to the Department of Commerce, we’ll get to that in a second, but first here are the four requirements you must meet before the DOC will add you to its certified Privacy Shield list. You must:
- Fall under the enforcement authority of the Federal Trade Commission (FTC) or another qualified US agency that can ensure compliance
- Publicize your commitment to comply with Privacy Shield principles
- Publicly disclose your privacy policy
- Actually do all this stuff, like, in practice
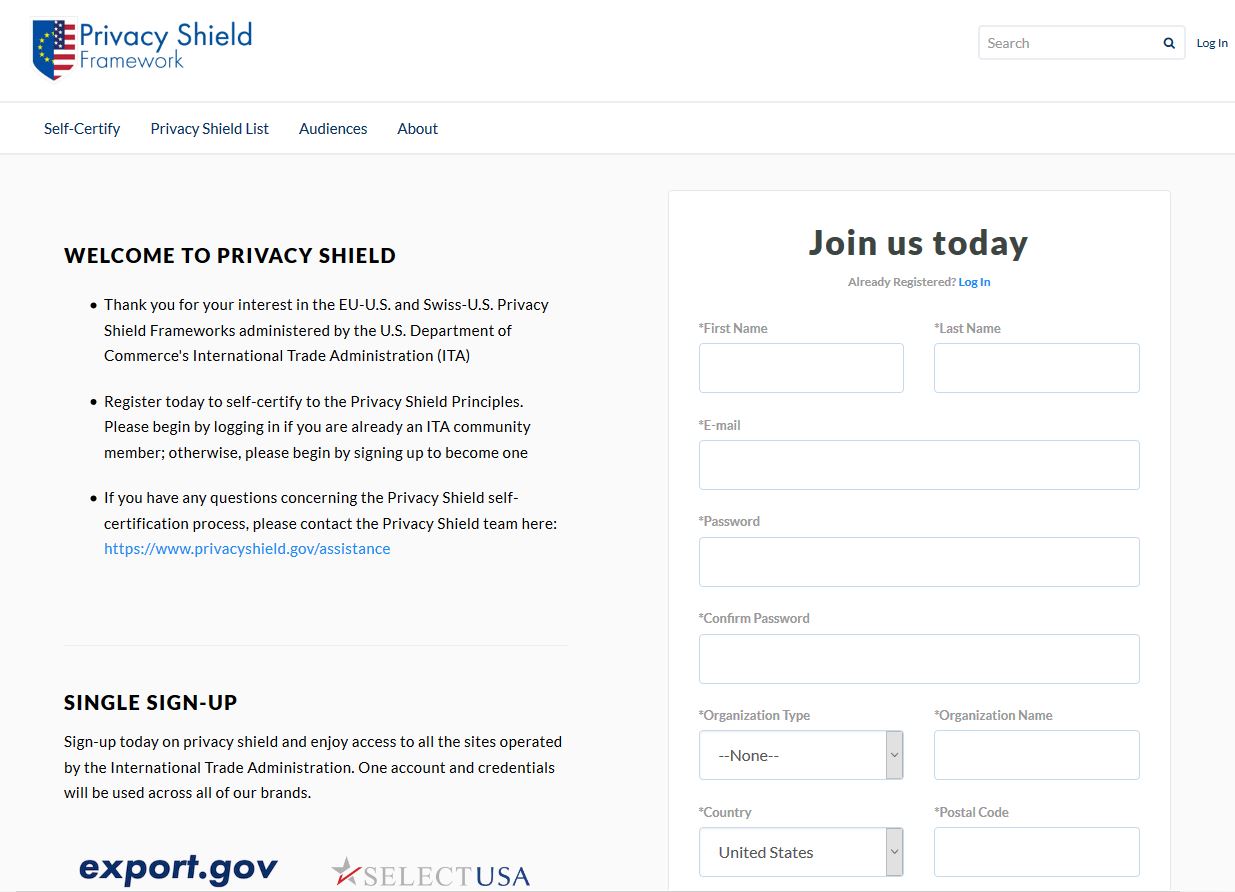
Privacy Shield Self-Certification Information for the DOC
Ok, so now it’s time to actually put together your submission to the Department of Commerce. You won’t be officially Privacy Shield-certified until the DOC adds you to its list, so let’s go over all of the information you’ll need to supply them to make that happen.
Before you head over to the Privacy Shield site to apply, here’s what information you need to gather.
Organization Information:
- Organization Name
- Address
- City
- State
- Zip Code
You’ll also need to provide information on your organizational contact:
- Contact Office
- Contact Name
- Contact Title
- Contact Email
- Contact Phone
- Contact Fax
In addition, you’ll be required to supply information about an Organizational Corporate Officer. This is the individual that will be certifying your compliance and signing your re-certification letter every year. You’ll need:
- Corporate Officer Name
- Corporate Officer Title
- Corporate Officer Email
- Corporate Officer Phone
- Corporate Officer Fax
Beyond that, you will need to provide a clear, concise description of your organization’s data practices in the EEA. You’ll also want to list any subsidiaries (the EU calls these undertakings) that are operating under Privacy Shield guidelines in the EEA, too. Make sure to include what types of personal data your organization is processing, the purposes for which it’s processing the data and any third parties it shares data with.
As we discussed in the last section, you’ll also need to provide an outline of the enforcement mechanisms that your organization is employing to help EU citizens with conflict resolution.
Finally, you’ll need to supply:
- Information about your Privacy Policy as it pertains to your commitments under Privacy Shield
- The statutory body that has jurisdiction to investigate claims against your organization
- Your organization’s verification method (self-assessed or outside review)
- Any additional privacy programs your organizations is a part of
- Your organizational revenue (pick a category)
- Less than $5 million
- $5-25 million
- $25-500 million
- $500 million – $5 billion
- Over $5 billion
You’re not required to do so, but it may also help to provide what industry or sector your organization resides in, as well as how many employees you have.
A Final Word on Privacy Shield
Eventually, one would hope, the United States will do enough to satisfy the European Commission and receive an “Adequacy Decision” regarding our data privacy laws. Then American businesses wouldn’t have to adapt to yet one more regulatory framework on the path to GDPR compliance.
But as of right now, a little less than two months until the GDPR goes into effect, that’s not the case. So if you’re tackling GDPR compliance from the US, make sure you’re also adding Privacy Shield certification to your efforts. Because until further notice, for American companies, the two go hand in hand.
As always, leave any comments or questions below.
Check out the rest of the Hashed Out GDPR Compliance Series
- GDPR: Introduction to a Series
- GDPR: How it affects the Domain Industry
- GDPR: How it affects Web Hosts
- GDPR: Problems for ICANN/WHOIS?
- GDPR: Complying with EU-US Privacy Shield
- GDPR: What is a Data Protection Officer?
- GDPR: Best Practices for Privacy Notices
- GDPR: What you need to know about Cookies
- GDPR: What is the Right to be Forgotten?
- GDPR: How to perform a Data Audit
- GDPR: Encryption Best Practices
- GDPR: When to report a Personal Data Breach






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown