5 Examples of When to Use a Digital Signature Certificate
Whether you’re a software creator or sales manager, digital signatures are essential to the security and authenticity of your data. Here are several of the ways that you can use digital signature certificates to enhance trust in your organization
We live in a world where you really have to question everything: is this email from your boss legitimate? Is the software update you want to install authentic, or is it a trojan that’s waiting to infect your device? When you log in to your favorite eCommerce website, how do you know it’s legitimate?
A digital signature certificate could hold the answer in all of these cases. These digital certificates are tiny data files help your web or email client verify that the file or other party you’re connecting to is trustworthy and authentic. This way, you don’t inadvertently share your sensitive login information or other data with cybercriminals.
But how can you use digital signature certificates to your advantage? We’ll go over all of that in just a few moments. But first, we think it would benefit our newer readers to briefly recap what a digital signature is and why you need a digital signature certificate to create it.
Let’s hash it out.
Note: If you’re already well acquainted with digital signatures and digital signature certificates, jump ahead to our list of digital signature certificate use cases.
What Is a Digital Signature? A Quick Recap
Digital signatures, also called public key signatures, are a cryptographic method of showing who created a digital asset and ensuring the item hasn’t been changed by another party. Examples of such assets include emails, PDFs, Word files, software application codes, etc. Applications frequently use visual marks of some kind (e.g., a ribbon mark in Microsoft Outlook) to represent digital signatures.
These signatures are trusted because you need to have a special file called a digital signature certificate in order to sign them digitally. But before you can get this digital certificate, a publicly trusted third party (called a certificate authority or CA) has to carefully vet your identity. Once you receive and start using your digital signature certificate, it proves that whatever you sign is authentic because it was created and signed by you, and your identity has been validated.
Digital signatures are a type of electronic signature. But unlike regular electronic signatures, which generally look similar to handwritten signatures, digital signatures might not look anything like traditional signatures. Here are a few quick examples to showcase the difference between electronic and digital signatures:
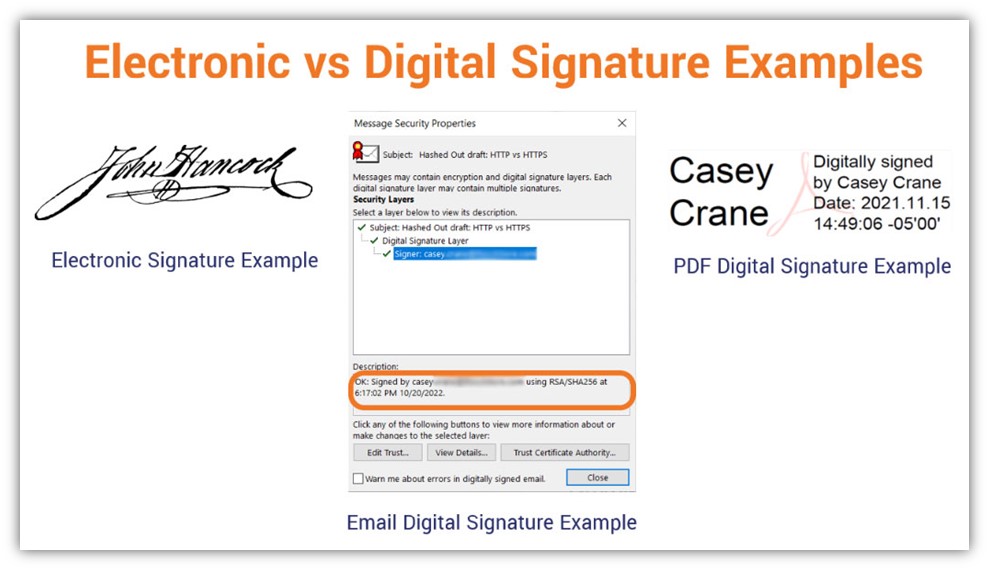
How Digital Signatures Are Created
To create a digital signature, you first need to have a digital certificate in hand. A digital certificate is a small data file that contains verified, identifying information about you or your organization. (This is the main info that displays to users.) But that’s not all that’s required. Without getting too technical, digital signatures are created by applying two cryptographic tools to the data you wish to protect:
- A special cryptographic function (called a hash function or hash algorithm) — This creates a hash value (a mishmash of letters and characters) of a fixed length, which masks the true size of the input and ensures the integrity of the data.
- A private key, which encrypts the hash value — When the recipient receives or downloads the file, they can decrypt it using the signer’s public key. This key ensures only the intended user can read the data.
Digital Signatures Enable You to Prove You and Your Files Are Legitimate
A digital signature validates your identity to other parties and ties it to whatever you’ve created and signed. It’s one of the critical elements that helps create digital trust in our otherwise insecure online world. Digital signatures pair digital identity with complex security measures to help prove you and your digital assets are authentic and unaltered.
The important takeaway here is that digital signatures offer two key qualities that you won’t find in regular electronic signatures:
- Authentication — This means you can prove that you or something you created is legitimate.
- Non-Repudiation — This ensures recipients that you, and only you, created or signed the item in question; that an imposter didn’t fraudulently make it.
Historically, if you wanted to prove that you’re the legitimate signer of a document, you’d have to meet up with a public notary to have them observe you signing it. This process required providing the notary with verifiable proof of identity — this is typically some form of ID from a trusted entity (i.e., your driver’s license or ID issued by your state or country’s government).
This is fine if you’re physically located in the same area where it’s easy to meet up to carry out this process. But what if you’re trying to do business with someone in another country? Meeting up face-to-face then becomes a lot more complicated and costly.
So, where do you find digital signatures? All over the place, honestly. You’ll find digital signatures used in everything from website connections to document signing.
You Need a Digital Signature Certificate to Use Your Digital Signature
Digital signatures are typically stored in special files known as digital certificates. For the sake of this article, we’ll call them digital signature certificates. Digital signature certificates are small digital files that enable you to use those signatures online.
A few examples of these digital signature certificates include:
- Email signing certificates (S/MIME certificates),
- Document signing certificates, and
- Code signing certificates.
Of course, there’s another type of digital certificate that uses digital signatures: an SSL/TLS certificate. This file is what enables you to prove that your website is legitimate because it’s been signed off on by a trusted CA (like DigiCert or Sectigo). But we’ll talk more about that in a little bit.
Okay, now that we have all of that out of the way, let’s jump right to what you need to know about how you can use each of these digital signature certificates…
5 Digital Signature Certificate Use Cases For Your Business
For virtually all of our readers, you’re likely already using digital signature certificates in one way or another (you just might not know it). However, there may be some use cases that you’re not as familiar with or aren’t sure how to implement within your IT environment. We’re here to explore those and more:
1. You Need a Way to Show Your Microsoft Office and PDF Files Are Authentic
Nowadays, you practically can’t do anything within your business without using Word, Excel, or PDF files. Of course, you’d like to assume that someone will send you only legitimate files via email. However, the reality isn’t as pretty. While it may be true, say, 90% of the time, the remaining percentage is enough to crack those rose-colored glasses.
As recent cyber security statistics and cyber crime statistics show, the threat landscape continues to change. New threat actors seemingly arrive on the scene almost daily and attack methods evolve with them. For example, SonicWall reports the prevalence of malicious Microsoft Office files decreased 64% in 2021; malicious PDFs, on the other hand, increased 52%.
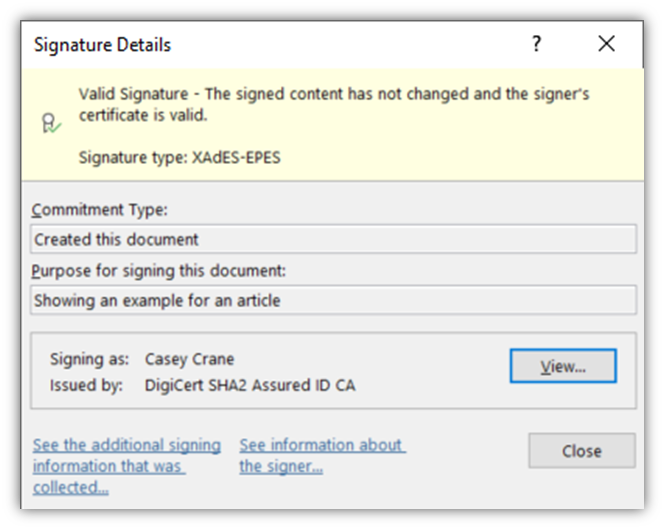
So, how can you show users that your documents and files are legitimate? Digitally sign them first using a document signing certificate. For example, this is what it looks like when you sign a Word document using a document signing certificate:
Here’s what it looks like when you sign an Adobe PDF file with an applicable digital signature certificate:

2. You Want to Eliminate Warning Messages When Users Download Your Software
SonicWall’s 2022 Cyber Threat Report data shows that malicious executables represented a whopping 30.27% of the cybersecurity company’s malicious file detections. As such, as a software developer or publisher, you need to have a way to show that:
- Your software is authentic,
- It’s actually from you, and
- No one’s modified it.
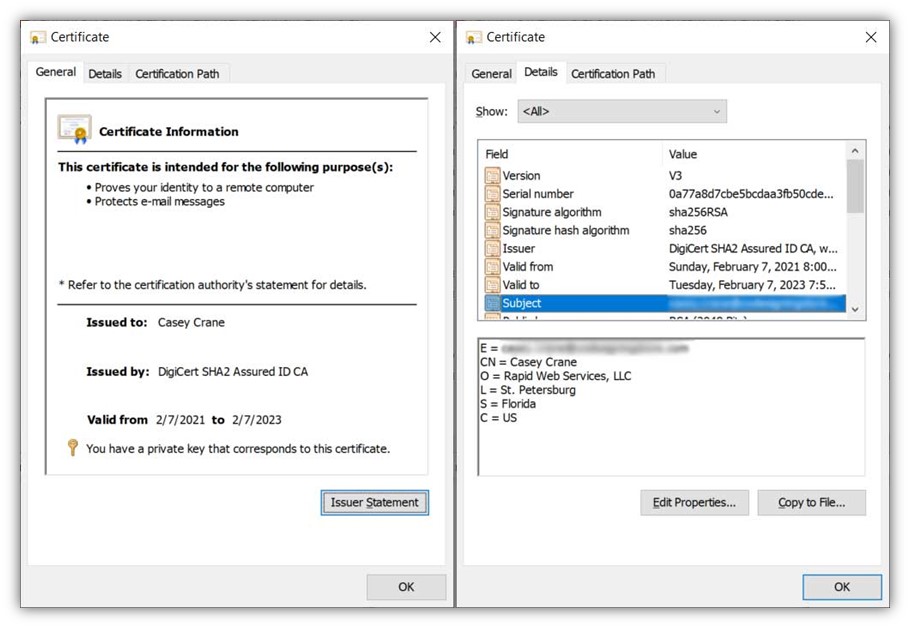
You can do this using a code signing certificate. These certificates are typically offered with two options of validation levels: organizational (i.e., standard) and extended. (Note: Some certificate authorities offer individual validation as well.) When you use this type of digital signature certificate to sign your software, you attach your organization’s verified information to the file regardless of the validation type you choose.
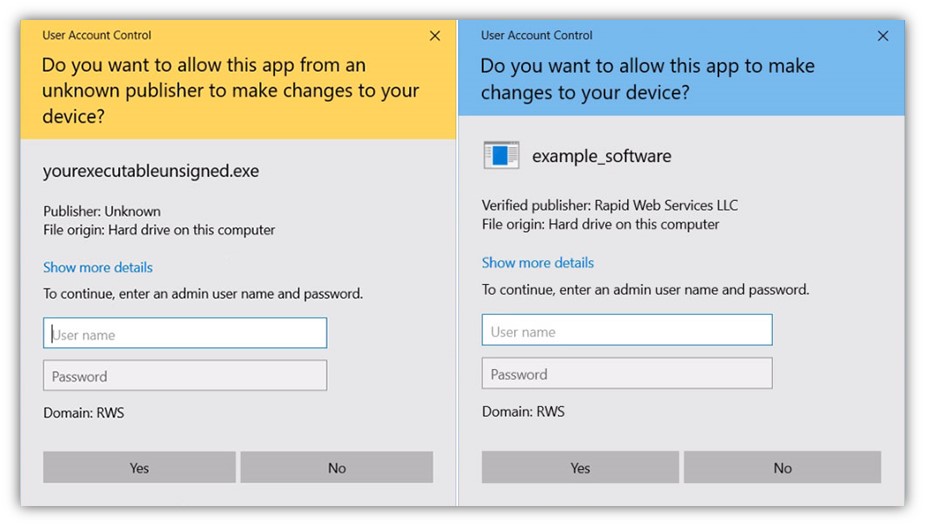
Both types of certificates are trusted automatically by browsers and operating systems. The big difference between the two validation levels is that Windows Defender SmartScreen requires an EV certificate if you don’t want an ugly warning message to pop up:
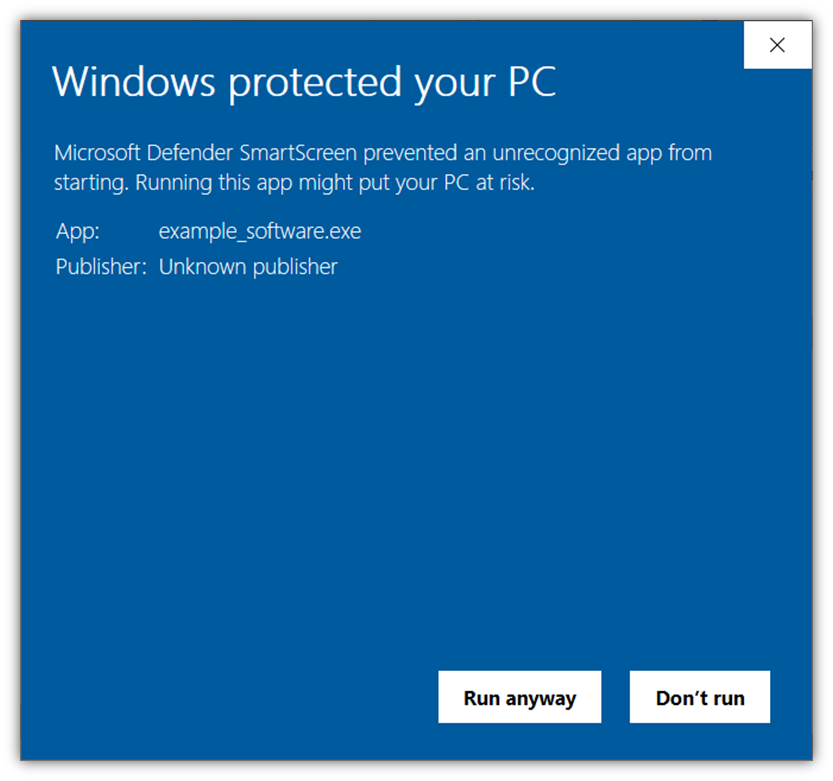
3. You Want to Give Customers and Prospects a Reason to Trust Your Website
Trust is hard to earn yet fragile as glass. Once you earn your customers’ trust, you need to do everything possible to protect it. Having a way to prove that your website — your brand’s digital representation — is legitimate is essential to that mission.
Every time you visit your favorite website, the server sends your browser a file (i.e., an SSL/TLS certificate) containing crucial identifying data that proves you’re connecting to the right server. This website security certificate is issued and digitally signed by a publicly trusted entity known as a certificate authority (CA). The CA’s trusted root
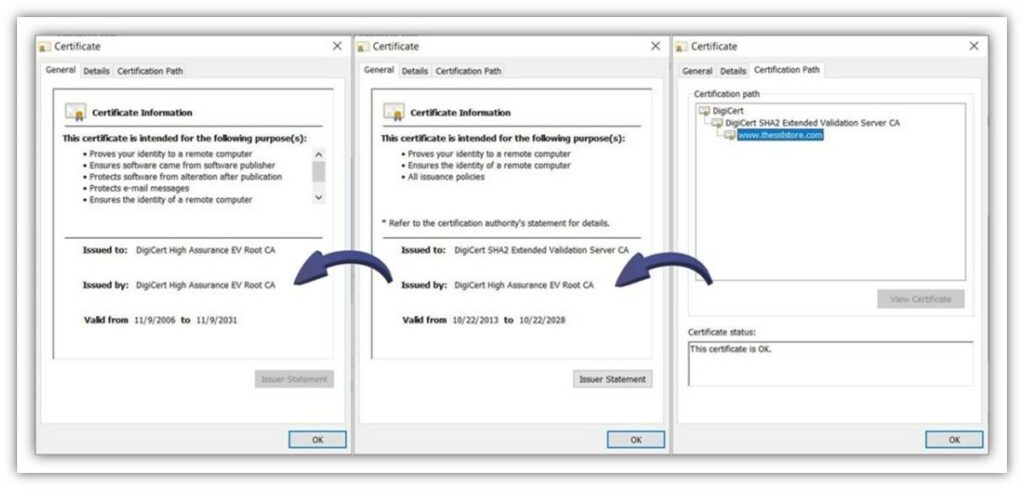
The CA’s digital signature means that this globally trusted entity is vouching for you, saying that you’ve, essentially, been vetted and are trusted. Having such a way to prove your organization’s authenticity is particularly crucial when you consider recent data from Bolster shows that their systems detected nearly 10.7 million phishing and scam pages in 2021 alone. To put this in more relatable terms, it means Bolster’s team detected an average of 29,190 fraudulent pages every day throughout the year.
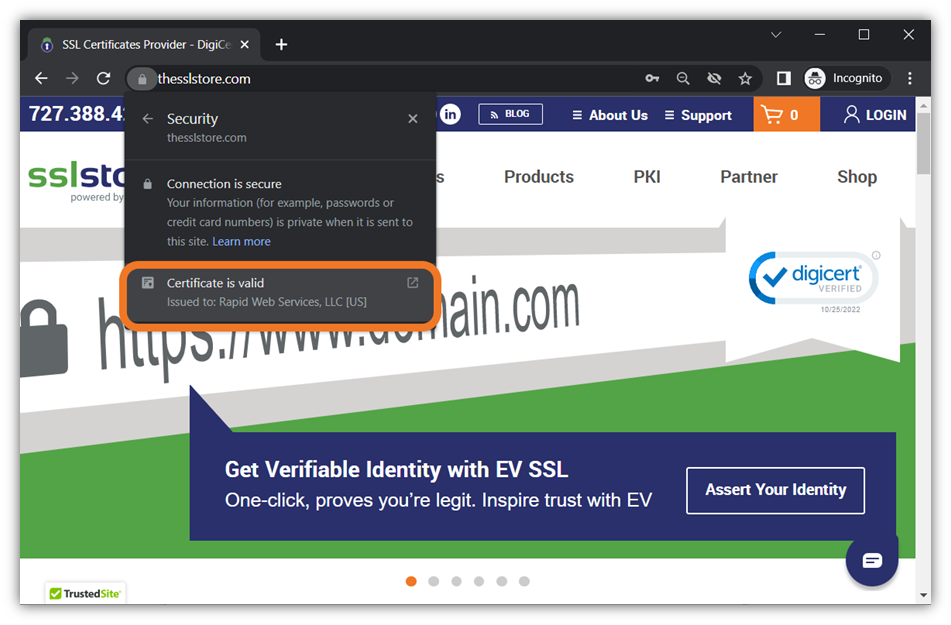
Want your authentic website to stand out from the sea of fraudsters’ sites? Then slap your vetted and validated identity on it by installing an SSL/TLS certificate right away. In addition to asserting your digital identity, SSL/TLS certificates enable users to communicate securely with your site. If you install an extended validation (EV) code signing certificate, then you take your digital identity to another level by displaying your verified company information upfront. This way, users don’t have to dig around your certificate info to find the details.
4. You Need to Prove to Recipients That Your Email Communications Are Authentic
Phishing is one of the top cyber attack methods used by cybercriminals. Verizon’s 2022 Data Breach Investigations Report (DBIR) data shows that email is one of the two leading attack vectors used in known data breaches. Furthermore, their report indicates that 75% of the malware the median organization received in 2021 came via email.
Sure, you can — and should — train your employees to recognize the threats associated with phishing attacks and social engineering. But it doesn’t hurt to add another more technical layer of security to the equation; this is where digital signature certificates for email come into play.
These certificates are known as email signing certificates or S/MIME (single/multi-purpose internet mail extension) certificates. They allow you to attach your digital signature to messages so your recipients can confirm they came from you. These certificates offer the added benefit of enabling you to encrypt your emails as well. This helps to provide end-to-end encryption by securing the emails before they leave your email server.
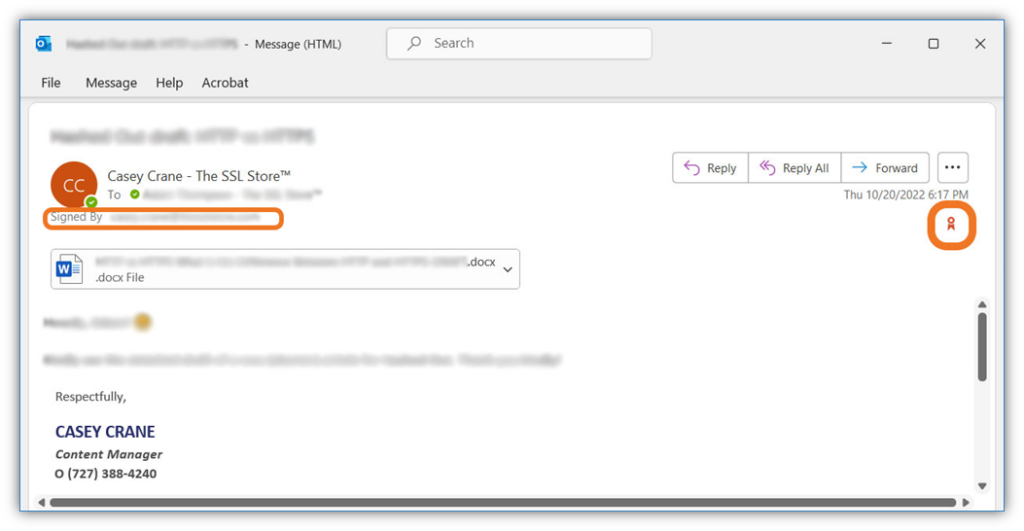
Here’s a quick look at what a digitally signed email looks like to your recipient:
5. You Want to Authenticate Without the Risks Associated with Traditional Passwords
There’s no such thing as a perfect authentication method; an enterprising cybercriminal will inevitably find a way to authenticate as you (fraudulently) if they’re truly motivated. But the goal is to make yourself as difficult a target as possible; this way, 99% of cybercriminals will give up and move on to the next target. Make yourself one of the hardest-to-reach fruits on the tree instead of one of the easy-to-steal, low-hanging fruits.
This is where a type of digital signature certificate, known as a client authentication certificate, can come in handy. A client authentication certificate enables you to authenticate without having to type in a username or password. Instead, you have a PKI certificate installed on your device, enabling you to authenticate automatically.
Why is this necessary? ForgeRock reports that 50% of cyber attacks they studied were due to unauthorized access through various account compromises. Of course, there are many ways accounts can become compromised. One of the most common methods is phishing, which involves an attacker stealing a user’s login information using social engineering tactics.
Using PKI-based authentication instead of a username-password combination means you no longer have a password that can be phished or stolen via malware. You simply go to the web app or system you have permission to access, and the authentication “magic” happens on the backend automatically. No muss, no fuss.
Final Takeaways on Digital Signature Certificates
It’s now more important than ever to secure your organization’s digital identity and data. Choosing to use a digital signature certificate to secure your digital assets is the difference between sending or receiving authenticated communications or files instead of unauthenticated (and potentially dangerous) ones.
To get a digital signature certificate for your website, emails, documents, or software:
- Evaluate what you need to secure and authenticate.
- Go to your favorite CA or authorized reseller’s website.
- Choose the certificate(s) based on the type(s) of coverage and validation type.
- Purchase your certificate(s).
- Generate a certificate signing request (CSR) for domain validation (DV) and organization validation (OV) certificates, if applicable.
- Provide the CA with the necessary organizational information to complete validation.
- Collect your digital signature certificate and install it on your server, device, or client.
- Start using your certificate right away!






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown